External VS Internal Penetration Test: What’s The Difference?
Penetration testing, also known as ethical hacking, is the practice of checking the security weaknesses of application software, networks, computers and devices, wireless systems, and employees. Penetration tests can be either external or internal depending on the goal of the project.
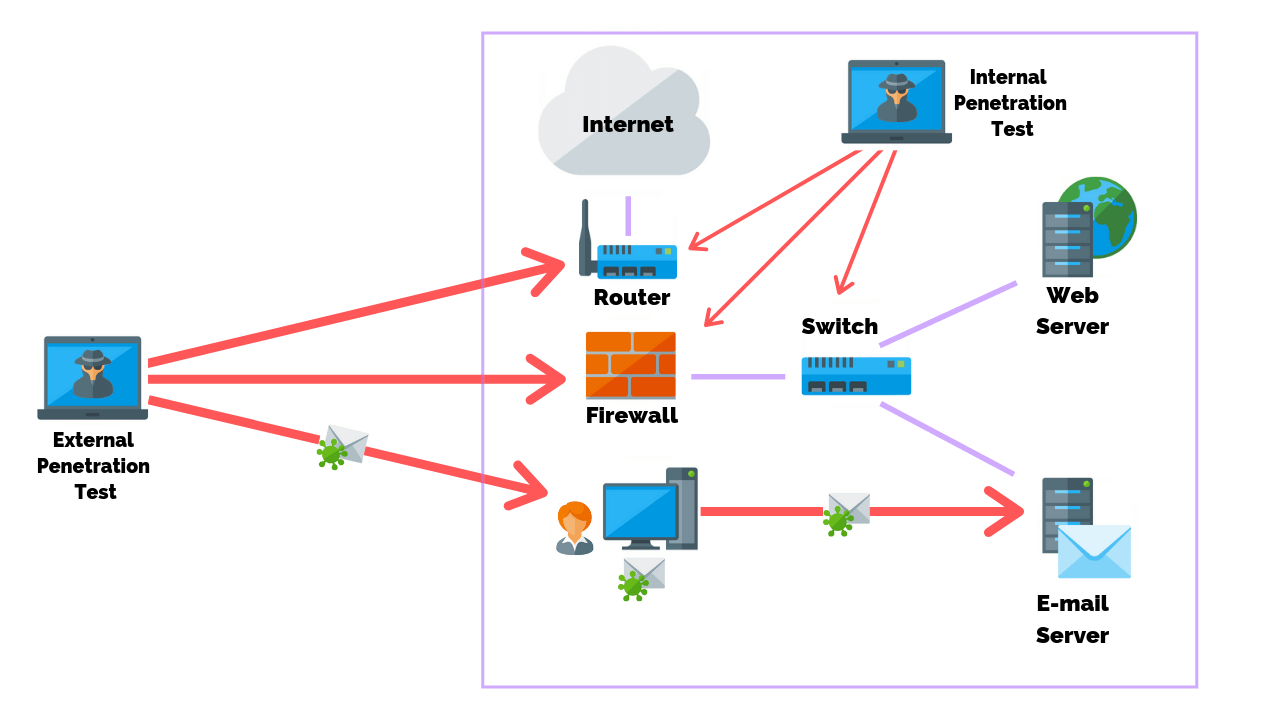
An external penetration test researches and attempts to exploit vulnerabilities that could be performed by an external user without proper access and permissions. An internal penetration test is similar to a vulnerability assessment, however, it takes a scan one step further by attempting to exploit the vulnerabilities and determine what information is actually exposed.
Article Navigation
Types Of Penetration Tests |
||
|---|---|---|
 |
 |
 |
External VS Internal |
Network |
Social Engineering |
 |
 |
 |
Physical |
Firewall |
Web Application |
External Penetration Test
External penetration testing consists of testing vulnerabilities to review the chances of being attacked by any remote attacker. By exploiting the found vulnerabilities it identifies the information being exposed to outsiders.
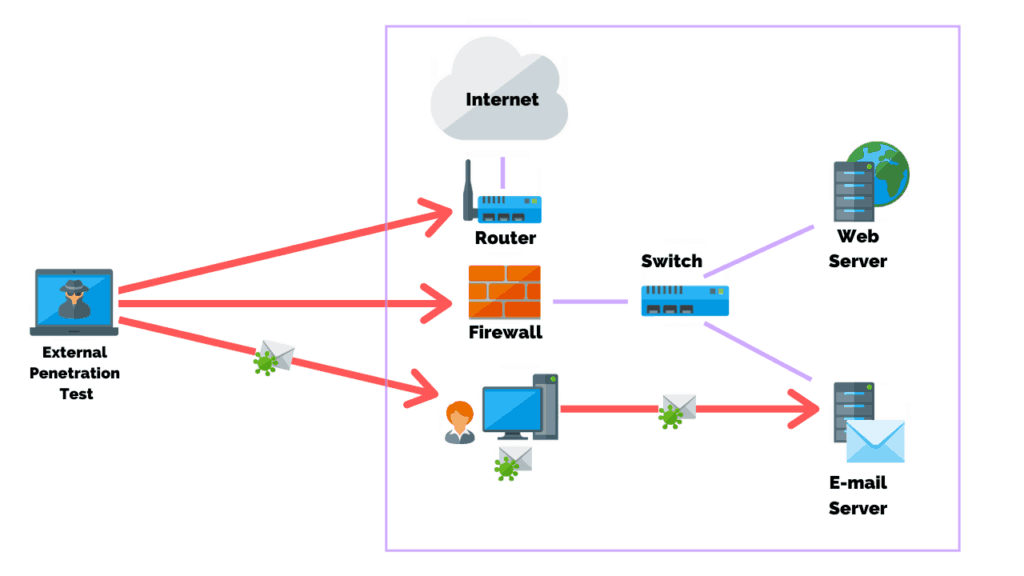 The main objective of this test is to simulate an attack on the internal network by mimicking the actions of an actual threat actor.
The main objective of this test is to simulate an attack on the internal network by mimicking the actions of an actual threat actor.
This type of penetration testing attempts to find and exploit vulnerabilities of a system to steal or compromise the organization’s information. As a result, the test will show whether the implemented security measures are enough to secure an organization and to assess its capability to defend against any external attack.
On average, an external penetration test will take 2-3 weeks to complete. However, this depends on the complexity of the system, the size of the network, and the goals of the test itself.
Examples of external penetration tests include:
- Configuration & Deployment Management Testing
- Identity Management Testing
- Authentication Testing
- Authorization Testing
- Session Management Testing, Input Validation Testing
- Testing for weak Cryptography
- Business Logic Testing
- Client Side Testing
- Testing for Error Handling.
Testing methodologies include:
- Footprinting
- Checking for public information and other information leakages.
- System Scanning/Port Scanning/Service Scanning for vulnerabilities
- Manual testing identified vulnerabilities.
- IDS/IPS Testing
- Password Strength Testing
Popular tools used in external penetration tests are:
- Nessus
- Metasploit
- Burp Suite Pro
- Dirbuster/Dirb/GoBuster
- Nikto
- Sqlmap
- Recon-ng
- Nmap
- Hydra
- GHDB
- theHarvester
Internal Penetration Test
An internal penetration test uses a different way of dealing with the attacks and comes into the picture after completion of an external penetration test. In this test, the main focus is to identify what could be accomplished by an attacker who has internal access to your network.
Prior to engaging with a vendor consider having the following checklist of items available:
- Your goals for performing a pen test.
- The number of internal workstations on the network.
- The number of servers.
- The total number of internal and external IPs.
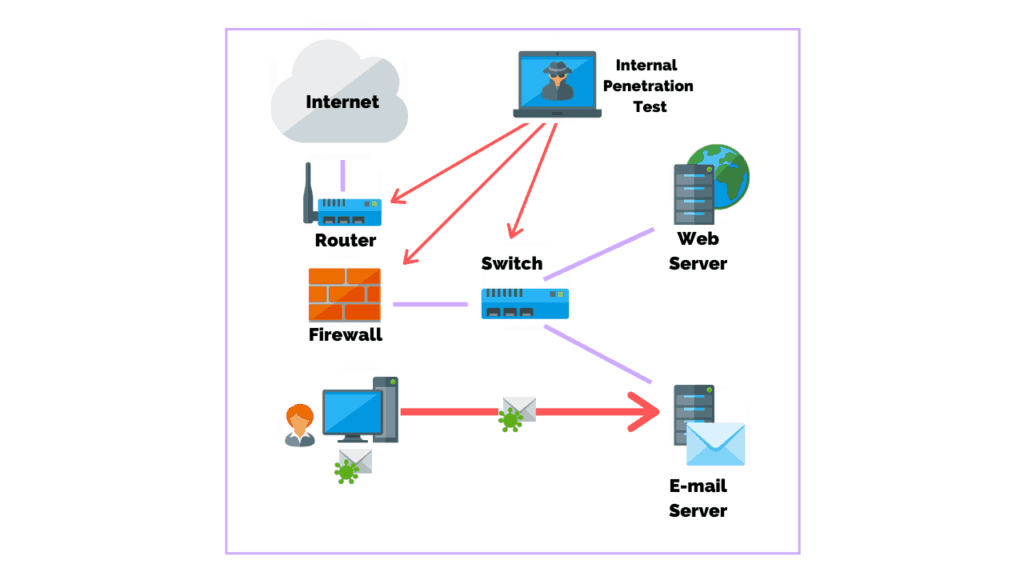
This can be a threat actor who penetrated the organization’s external defense systems or it can be an employee, contractor, or other staff with internal access.
Internal penetration tests include using:
- Computer Systems
- Access Points
- WiFi Networks
- Firewalls
- IDS/IPS
- Local Servers
- Employees
Once those vulnerabilities are identified, testers exploit them to discover the impact of an attack and show the weakness/entry points to the organization.
Internal penetration testing is not just limited to exploiting internal network vulnerabilities, but it also includes privilege escalation, malware spreading, man in the middle attacks (MITM), credential stealing, monitoring, information leakage or any other malicious activity.
You might be wondering why you would conduct an internal penetration test, to begin with, given your systems are supposedly secure from any external threats.
However, internal tests provide the results to an organization that should an attacker manage to gain access equivalent to an insider, or if any malicious internal user tries to break the security, what impactful it could have in terms of disclosure, misuse, alteration, or destruction of organization’s confidential information.
Testing methodologies include:
- Internal Network Scanning
- Port Scanning and System Fingerprinting
- Finding vulnerabilities
- Exploiting
- Manual Vulnerability Testing and Verification
- Firewall and ACL Testing
- Administrator Privileges Escalation Testing
- Password Strength Testing
- Network Equipment Security Controls Testing
- Database Security Controls Testing
- Internal Network Scan for Known Trojans
- Third-Party/Vendor Security Configuration Testing
Popular tools used in internal penetration testing:
- Nmap
- Wireshark
- Burp Suite Pro
- Dirbuster/Dirb/GoBuster
- Nikto
- Sqlmap
- Nessus
- Responder
- Metasploit Framework
- Nmap
- Hydra
- Bettercap/Ettercap
- Hashcat/John the Ripper
- Custom Scripts
Conclusion
For every organization, it’s best practice to perform an external and internal penetration test along with regular security audits to ensure the security of their IT System and determine what information can be exposed to the attackers. It is also necessary because of IT Security Rules & Regulations and Guidelines like GLBA, FFIEC, NCUA, HIPAA, and etc.
Are you ready to work together? Get a no-obligation consultation to meet your penetration testing needs.
Related Articles
- 5 Ways To Protect Your Business From Most Cyber Attacks
- How Often Should You Perform A Network Vulnerability Scan?
- Social Engineering Penetration Testing: Attacks, Methods, And Steps
- Vulnerability Scans VS Penetration Tests: What’s The Main Difference?
- What Is A Red Team VS A Blue Team In Cyber Security?


Ted Jordan
why do the external test before the internal test?
Jason Firch, MBA
Hi Ted. It really depends on what you’re trying to accomplish. However, generally speaking external tests don’t require as much effort and time to complete vs. internal tests.
An external test ultimately may end being checking configurations on a firewall. Getting the easy stuff out of the way helps to work towards that baseline more quickly.