Network Security Best Practices
Learn what steps businesses need to take to secure their networks.
Learn what steps businesses need to take to secure their networks.
Resources
Overview
In this guide, you’ll learn everything you need to know about network security.
This section features 7 articles that will help guide your business towards implementing network security best practices.
How PurpleSec Helps To Secure Your Network
Our vulnerability management services and penetration testing services provide a holistic approach to securing what’s most important to your organization.
Who Will Benefit From This Guide?
Protect the confidentiality of corporate information, the integrity of data, and ensure access to resources.

Learn the complete network assessment process and begin laying the foundation of your security program.
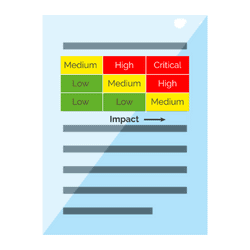
Download our FREE vulnerability assessment template today! Written by experienced security experts.
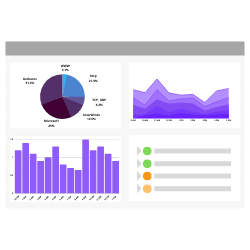
The key to an effective security program is real-time monitoring of events and how to respond to them.
Coming Soon
Develop and implement a successful network security plan for your business from start to finish.

Identify and categorize vulnerabilities found on your network with routine network scans.

The goal of managing your network’s security is to define and streamline your processes.
