Previous
Maui Ransomware Attacking Healthcare And Public Health Sector
Learn how PurpleSec’s experts can protect your business against the latest cyber attacks.
Author: Dušan Trojanović / Last Updated: 7/26/2022
Reviewed By: Dalibor Gašić, & Michael Swanagan, CISSP, CISA, CISM
View Our: Editorial Process
Table Of Contents
Summary Of The Attack
- North Korean state-sponsored cyber actors are attacking U.S. Healthcare and Public Health (HPH) Sector organizations since at least May 2021.
- These incidents disrupted the services provided by the targeted HPH Sector organizations for prolonged periods.
- Compared to other ransomware attacks Maui ransomware is believed to be designed for manual execution by attackers.
- The attack can be prevented by maintaining off-site offline backups, keeping operating systems, and applications, keeping firmware up to date, and having a proper cybersecurity response plan.
What Happened?
The Federal Bureau of Investigation (FBI), Cybersecurity and Infrastructure Security Agency (CISA), and the Department of the Treasury released a joint Cybersecurity Advisory (CSA) to provide information on Maui ransomware, which is claimed to have been used by North Korean state-sponsored cyber actors since at least May 2021 to target Healthcare and Public Health (HPH) Sector organizations.
In June 2022, the Stairwell research team investigated one of lesser-known ecosystems of Ransomware-as-a-Service, the Maui ransomware.
Maui has been shown to have a lack of several key features which are commonly seen with tooling from RaaS providers, such as an embedded ransom note to provide recovery instructions or automated means of transmitting encryption keys to attackers.
Instead, Stairwell research team believe that Maui is manually operated, in which operators will specify which files to encrypt when executing it and then exfiltrate the resulting runtime artifacts.
Security awareness training also promotes a heightened level of attention to the subtle activities performed by a threat actor, who has the objective of illegally obtaining your data or to damage your corporate resources.
How PurpleSec Helps To Secure Your Organization
Our vulnerability management services and penetration testing services provide a holistic approach to securing what’s most important to you.
What Is Maui Ransomware?
Since May 2021, the FBI has observed and responded to multiple Maui ransomware incidents at HPH Sector organizations.
North Korean state-sponsored cyber actors used Maui ransomware in these incidents to encrypt servers responsible for healthcare services, including electronic health records services, diagnostics services, imaging services, and intranet services.
In some cases, these incidents disrupted the services provided by the targeted HPH Sector organizations for prolonged periods.
The initial access vector(s) for these incidents is unknown.
The earliest identified copy of Maui…
(SHA256 hash: 5b7ecf7e9d0715f1122baf4ce745c5fcd769dee48150616753fec4d6da16e99e)
…was first collected by Stairwell’s inception platform on 3 April 2022.
Maui is believed to be designed for manual execution by attackers.
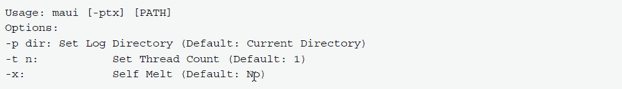
When executed at the command line without any arguments, Maui prints usage information, detailing supported command-line parameters.
The only required argument is a folder path, which Maui will parse and encrypt identified files.
Maui command line usage details:
How Does Maui Ransomware Work?
Instead of relying upon external infrastructure to receive encryption keys, Maui creates three files in the same directory it was executed from (unless a custom log directory is passed using the -p command line argument) containing the results of its execution.
These files are likely exfiltrated by Maui operators and processed by private tooling to generate associated decryption tooling.
Indicators of Compromise (IOCs) obtained from FBI incident response activities since May 2021 provided below:
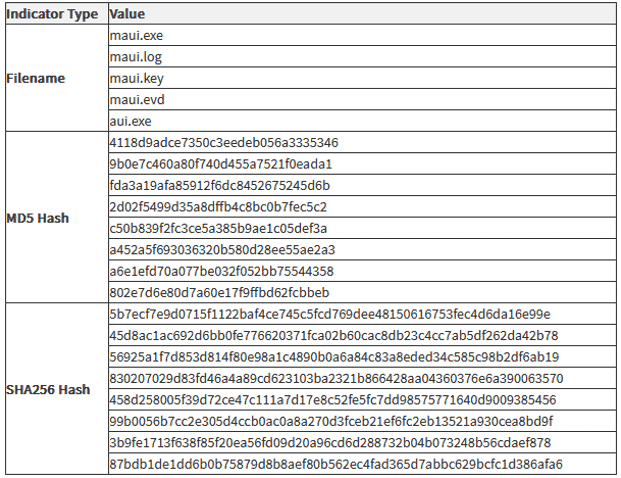
How Maui Encrypts Data
Maui uses a combination of Advanced Encryption Standard (AES), RSA, and XOR encryption to encrypt [T1486] target files:
- Maui encrypts target files with AES 128-bit encryption. Each encrypted file has a unique AES key, and each file contains a custom header with the file’s original path, allowing Maui to identify previously encrypted files. The header also contains encrypted copies of the AES key.
- Maui encrypts each AES key with RSA encryption. Maui loads the RSA public (maui.key) and private (maui.evd) keys in the same directory as itself.
- Maui encodes the RSA public key (maui.key) using XOR encryption. The XOR key is generated from hard drive information (\\.\PhysicalDrive0).
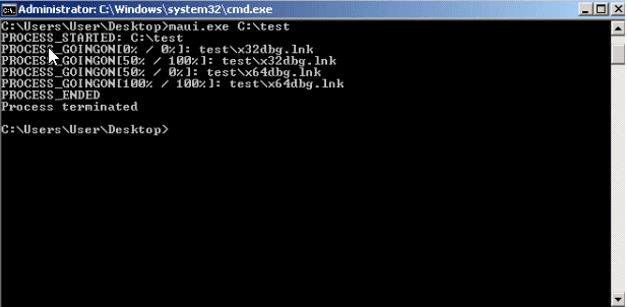
While Maui is encrypting files, it outputs status information back to operators. Command line output during execution:
How To Mitigate Maui Ransomware
The advisory also provides mitigation steps organizations can to prepare for, or deal with attacks using Maui ransomware.
Thankfully, although Maui may be a little different from run-of-the-mill ransomware, the steps to protect against it are not:
- Maintain off-site, offline backups of data and test them regularly.
- Create a cyber security response plan.
- Keep operating systems, applications, and firmware up to date.
- Disable or harden remote desktop protocol (RDP).
- Require multi-factor authentication (MFA) for as many services as possible.
- Require administrator credentials to install software.
- Report ransomware incidents to your local FBI field office.
We hope that this article will guide you to this recent attack and give you good advice on how to protect yourself and your organization.
The best advice that can be given is always to keep your systems and service updated as soon as they are available.
Related Articles:

Dušan Trojanović
Dušan is a Senior Security Engineer actively working as a penetration tester in DevSecOps projects. He is also an avid security researcher bringing forward analysis on the latest attacks and techniques.
Related Articles
- Top 10 Cyber Attacks In 2022
- Top 10 Vulnerabilities In 2022
- Rackspace Ransomware Attack
- Dropbox Suffers Data Breach
- Iranian APT Uses Log4j
- Google SEO Poisoning Campaign
- Killnet DDoS Target Airports
- Advocate Aurora Health Data Leak
- Microsoft 2.4 TB Data Leak
- Optus Exposes 2.1M Customers
- $570M Binance Coin Hack
- TikTok Denies Cyber Attack
- NATO Data Leak
- Uber’s Systems Compromised
- Cisco Cyber Attack
- Samsung Exposes PII
Popular Articles
Ransomware Attacks
Preventing Attacks



 HEALTHCARE
HEALTHCARE GOVERNMENT
GOVERNMENT CRYPTO
CRYPTO