Top 10 Benefits Of Vulnerability Management
Learn about PurpleSec’s fully managed vulnerability management services.
Author: Eryk Waligora / Last Updated: 9/05/22
Reviewed by: Michael Swanagan, CISSP, CISA, CISM, Rich Selvidge, CISSP, & Josh Allen
View our: Editorial Process
Table Of Contents
There are 10 benefits of vulnerability management including cost effectiveness, maturing your security program, rapidly responding to threats, gaining operational efficiencies, enhancing visibility and reporting, maintaining compliance requirements, integrating with patching program, helping to burn down backlogs, establishing trust with clients, and automating scanning and patching.
What You’ll Learn
- What risk-based vulnerability management is and why it’s important.
- The vulnerability management lifecycle explained.
- How an effective vulnerability management process works.
- The top benefits gained from implementing vulnerability management.
- How PurpleSec manages vulnerabilities
Cyber attacks have skyrocketed in recent years due to an attack surface expansion.
Many organizations are dependent on interconnected technologies, this surface includes a higher volume of internet-connected devices and increased integration of networks and systems.
New devices typically have default settings and credentials, but many people fail to change them. Armed with the same default login and password, a threat actor looking to exploit a device could easily gain access.
This means cybercriminals can steal your personal data, lock you out of your device, invade your privacy, and even cause physical harm when in control of IoT and operational technology (OT) machinery.
But it’s not always fresh out of the box items. Vulnerabilities can become exposed with existing technology.
After reading this article you will be able to clearly see what makes vulnerability management effective and how to communicate these benefits to stakeholders.
We’ll begin by defining Vulnerability Management.
What Is Vulnerability Management?
Vulnerability Management is a management process designed to proactively identify, classify, remediate, and mitigate vulnerabilities in an IT infrastructure with the goal of reducing overall risk to an organization. It’s an important feature of a cyber security strategy and helps to drive the first lines of defense.
The goal of an effective Vulnerability Management Program is to understand the threat landscape in order to reduce attack surface and mitigate risk.
This is achieved with cross functional teams working on projects and utilizing tools to gain greater insights for remediation.
Vulnerability Management Vs Vulnerability Assessment
A vulnerability assessment is part of the vulnerability management lifecycle. The assessment is the step of identifying vulnerabilities and understanding what risk they may pose to your organization.
The vulnerability management lifecycle is designed to take that assessment and create projects and prioritization around assessing and remediating those vulnerabilities.
The Vulnerability Management Lifecycle
The Vulnerability Management Lifecycle is designed as a continuous management process for an organization to actively address vulnerabilities to their systems through discovery, prioritization, assessment, action, re-assessment, and improvement.
- Discovery – Discover and target the assets that are to be included in the vulnerability assessment.
- Prioritize – Assign a value to each asset based on its impact or criticality to business operations.
- Assess – Conduct the vulnerability scan based on the asset discovery. Create reports to ensure each asset is properly scanned and provides results.
- Act – Review the vulnerability report with appropriate stakeholders. Establish a strategy for remediation or acceptance of risk.
- Reassess – Ensure threats are eliminated and prove mitigation efforts are actually working.
- Improve – Routinely review the state of your vulnerability program. Look for ways to improve and protect your network against evolving threats.
Why Vulnerability Management Is Important
From neglected software security updates to misconfigurations, to weak identity and access management, and other instances, there is an entire ecosystem ripe with weaknesses.
These vulnerability factors increase the overall risk to an organization.
Attackers can steal data and damage critical systems, which opens the door to potential legal, financial, and public relations challenges.
Many organizations suffer colossal payouts every year due to ransomware and the fallout associated. They lose millions over a vulnerability that was not properly managed.
To avoid this outcome, organizations have begun to take a proactive approach to their vulnerability management.
Some go as far as to implement a continuous process for managing and remediating these threats.
How Does Vulnerability Management Work?
Vulnerability Management is a continuous process designed to proactively identify, classify, remediate, and mitigate vulnerabilities in an IT infrastructure.
The goal is to reduce overall risk to an organization.
There are multiple methods and tools to operate successful vulnerability management.
How and where should your organization start in developing its vulnerability management program?
Let’s take a deeper look at one of the first and most important resources to include as part of your organization’s vulnerability management, a vulnerability assessment.
Perform A Vulnerability Assessment
Since the goal of vulnerability management is to reduce risk, a formal vulnerability assessment should be included to encompass input from various teams within the business to carefully identify and prioritize assets that are most critical from an exposure perspective.
We’ll walk through the phases of an assessment, starting with remediation planning.
Plan Remediation
First, you need to inventory and prioritize your vulnerabilities.
This can be done by applying a value or classification metric to help determine which vulnerabilities are a priority to a given asset or group of assets critical to business operations.
To carry out a successful remediation plan, you need to understand the role of each team member involved in the project.
This includes not only the vulnerability team, but other security teams, IT, legal, finance, public relations, and business operations.
This alignment is necessary because you want to make sure you are prepared in every aspect vital to the health of the organization.
A holistic approach also includes getting buy-in from clients and internal stakeholders.
Obtaining approval on which vulnerabilities to prioritize often comes at the determination of these asset holders or asset owners
Once you have your plan in place, also make sure to follow Change Management procedures for your organization.
Knowing how to adapt to changes in scope, process, and responsibility hand-off are important to document ahead of time.
Manage The Project
Once your vulnerabilities have been prioritized with a remediation plan, you’re ready to begin deploying your project.
To do so, you will need a dedicated project manager to oversee all aspects of the project plan.
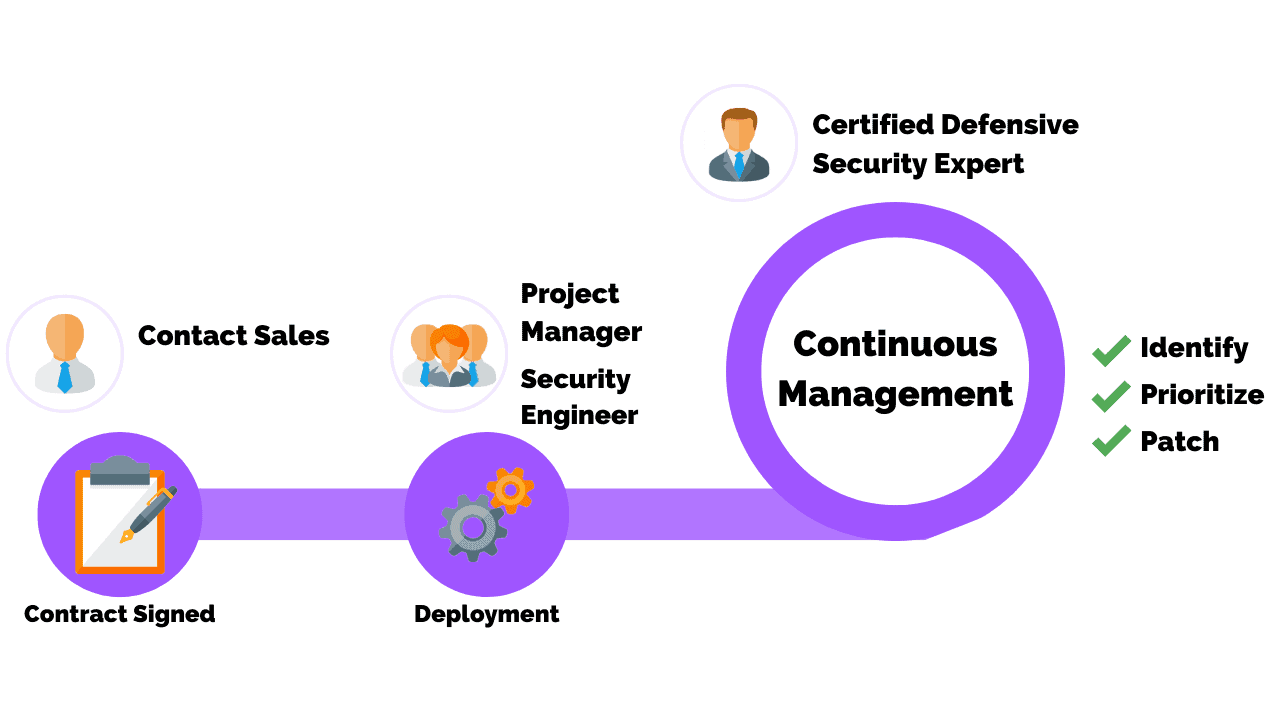
Depending on the size and maturity of the organization’s cyber security program, either a full-time project manager or other project lead will be responsible for planning sprints and reviewing the work after it’s complete.
To ensure all teams are working together on the flow of the project and understand their objectives, it is recommended that the project manager have their team use a centralized platform to communicate, assign tasks, and keep track of deadlines.
This will help reduce inconsistencies and drive the project forward.
Having transparent communication is also important between the project team and the stakeholders.
You’ll want to confirm they are involved throughout the entire process, often needing approval to complete work or required to provide tracking and reporting.
Set Reporting Cadence
To provide stakeholders with the best reporting on your project, outcomes should be assessed by having continuous touchpoints with your team to review vulnerability reports.
The best way to analyze outcomes is to deliver activity reports in the form of weekly, bi-weekly or monthly updates.
This will help to determine where the project is in achieving its goals.
If a project is highly sensitive or designed for the short term, it’s recommended to establish daily updates.
But remember, to reduce meeting fatigue, updates and touchpoints can be made over email or other centralized platforms.
It’s important to create meaningful metrics around the project data and to hold people accountable.
Failure to execute certain tasks could cause setbacks or even derail the entire project.
Benefits Of Vulnerability Management
Now that we understand what vulnerability management is, how it works, and how a vulnerability assessment is structured, we have the context for what all this means for you and your organization.
To help get right to the point, we’ve identified the top 10 benefits of vulnerability management:
- Is Cost Effective
- Matures Your Security Program
- Quickly Respond To Threats
- Gain Operational Efficiencies
- Enhances Visibility And Reporting
- Maintains Compliance Requirements
- Integrates with Patching Program
- Helps Burn Down Backlogs
- Establishes Trust With Clients
- Automates Scanning And Patching
Being able to communicate these key values are essential to gaining stakeholder support and charting goals.
1. Is Cost Effective
Certainly, one of the top benefits to any organization is cost effectiveness, and a vulnerability management possesses multiple cost saving advantages.
It eliminates ad hoc patching which can lead to missed patches and compound costs.
It also reduces technical debt by helping the organization set focus and prioritization around assets that present the highest risk if exploited.
Plain and simple, vulnerability management helps to bring structure and precision to an organization’s security posture, bolstering its justification to stakeholders who will then be more likely support vulnerability initiatives.
2. Matures Your Security Program
Growth is an important component of any organization, but especially in and around its
cyber security program.
Vulnerability management enhances the overall security posture of your organization by recognizing key assets and where to prioritize efforts in order to reduce risk.
Working together with other security teams, it helps prevent access and data exploitation by threat actors.
But not all risks are due to outward attacks. Vulnerability management also achieves specific goals for security frameworks or compliance requirements.
Related Content: How To Conduct A Security Risk Assessment
3. Quickly Respond to Threats
Bad guys don’t sleep or take holidays! New vulnerabilities are found daily when we least expect it.
For instance, the Log4j vulnerability was identified a day before Thanksgiving in 2021, sending all organizations on high alert.
Vulnerability management helps to move organizations from a reactive response to a proactive one.
Having a continuous patch management process in place ensures immediate identification, prioritization, and has the resources to remediate critical vulnerabilities.
In doing so it lays the groundwork for a quicker and more effective response to threats that emerge.
4. Gain Operational Efficiencies
Keeping teams and systems aligned to project goals and outcomes is important – especially when involving highly sensitive security for an organization.
To maintain alignment, vulnerability management aims to define the process for identifying vulnerabilities and remediating them.
It also has the potential to reduce manual workflows and provide automation with continuous monitoring, alerting, and remediation solutions.
This not only adds to operational efficiency but has very much become a standard security practice.
5. Enhances Visibility And Reporting
As mentioned previously, when deploying a vulnerability assessment, vulnerability management helps to build a system of tracking and reporting.
Having visibility into a project explains the return on investment in security to stakeholders and can help to support other projects.
Vulnerability reporting also helps to uplift the team by providing actionable dashboards and trend reports to quickly measure performance and state of the program.
In turn, these contextualized reports provide key metrics and indicators for senior management to make informed decisions on key initiatives.
6. Maintains Compliance Requirements
Effective vulnerability management will help to achieve regulatory requirements.
This can be done by reviewing and implementing compliances from various frameworks, such as the Payment Card Industry (PCI) and the Health Insurance Portability and Accountability Act (HIPPA).
PCI has a list of compliances that range from the more general, as in, “provide a patch audit report”, to the more specific, such as, “deploy patches on systems for both internal and external applications only after testing them in separate test environments”.
A robust set of patch management policies and procedures are required for a healthcare organization to meet HIPAA compliance.
This includes proper inventory management, testing, documentation and configurations around automatic software updates, unmanaged hosts, firmware, and more.
7. Integrates with Patching Program
It’s common within an organization structure for a vulnerability management team to function under the ownership of IT or security.
Regardless of where your team is placed, both IT and security teams need to work together to achieve the goal of patching vulnerable systems.
Having open communication and regular cadences will help with integration of priorities and projects.
8. Helps Burn Down Backlogs
Planning to burn down existing vulnerabilities is much easier to strategize and execute than patching new vulnerabilities, and often more important.
Not every organization operates the same way or has the same type of assets or users.
Because of this, many vulnerabilities that may pose a greater risk to one organization don’t necessarily pose the same level of risk to another.
A patching plan to reduce the backlog of vulnerable systems helps save time, organizes priorities, and can prevent unnecessary costs to low level vulnerability remediation.
9. Build Trust With Clients
The rise of ransomware and supply chain attacks, like the Kaseya ransomware attack, has forced organizations to audit 3rd party vendors, forcing stakeholders to become more aware of the dangers of insecure systems.
Executive level reporting and key metric indicators provide stakeholders and clients with visibility into the state of the program.
This is an important feature of modern business practice, where many stakeholders increasingly assess the risk of doing business based on an organization’s security posture.
Having the data and resources in place to report on the health of the organization adds to credibility and heightens the chance of doing business.
Establishing security policies is a great first step if you’ve not already begun to build a cyber security program.
10. Automates Scanning And Patching
We touched on how automation improves operational efficiency, but it also has the opportunity to further reduce costs on headspace.
Instead of hiring employees to manually scan or patch a system, it makes more sense for them to be analyzing the results and proving to management for decision making.
This relieves the burden of time-consuming tactical work and allows for better planning and strategy.
How PurpleSec Manages Vulnerabilities
Our biggest focus at PurpleSec is automation and AI enhancement. Our current solution is called AI Powered Vulnerability Management.
The traditional ways of throwing resources and technology at it is tedious and time consuming. There are many great toolsets available nowadays, but you’re still relying on human involvement, which is extremely resource intensive.
We take a large portion of repetitive tasks out of human hands and automate them. This allows the human resource time to validate the machine and help organize and report on the risk for the organization.
Talented security professionals are also extremely valuable and patching isn’t quite a glamorous job in of itself.
By automating those tasks it enables your team to spend their time on more value-added work like building new processes or programs to further enhance your security efforts.
With our solution, we’ve built out a process for managing the automation of identifying, prioritizing, assigning risk to, and setting up all the patching processes and mitigation.
- We know the risk.
- We know the priority to patch.
- We can take action immediately.
It can take a few days to get our system to talk to your scanners, patch management systems, and ticketing systems.
Once set up, we can have our experts remediating and creating risk acceptance plans and mitigating those risks withing 48 hours.
There’s a quick setup period and highly configurable to work with your technology stack and business processes. As a result, your 14-30 day risk windows become a 2-5 day risk window.
Risk-Based Vulnerability Management
Effective risk-based vulnerability management is accomplished by examining the attack surface of the organization and prioritizing the remediation of vulnerabilities based on associated risks.
It focuses on the prioritization and orchestration of where you’re putting in your vulnerability management efforts.
The traditional way of running vulnerability management is in a cycle where we’re patching what’s coming in – first in first out coming in from our systems.
In contrast, risk-based vulnerability management is assessing the entire threat landscape continuously.
This identifies vulnerabilities and:
- Determines if they are exploitable.
- Assesses the impact if they were exploited.
- How likely they are to be exploited.
It’s also assessing where that system is, for example, internally vs externally facing.
You’re able to assign data classifications as well. This is helpful for sensitive data such as a bank storing customer PCI data.
Wrapping Up
Technology helps improve business processes and goals by creating a more efficient and productive work environment.
But technology can also hinder an organization from reaching its goals if its critical business systems and applications are left unmanaged within the organization’s infrastructure.
Vulnerability management creates a healthier ecosystem by identifying and remediating vulnerabilities that may cause severe harm, resulting in legal, financial, and reputational consequences to your business operations.
By laying out its top 10 benefits, this article has shown the value vulnerability management brings to an organization.
You can now easily communicate and justify to stakeholders and project teams why this area of security is vital to reaching shared goals.

Eryk Waligora
Eryk has a multi-perspective experience from his over 10 years of professional work in the media/entertainment, technology, and cyber security industries. He is currently serving as a cyber threat intelligence manager as well as a technical writer for PurpleSec.
Recent Articles
Categories
Policy Templates
Most Popular