Managed
Assess your security and discover your true risk:
- Assess your network, application(s), or wireless security
- Get actionable results in 2 weeks
- Remote presentation of findings and recommendations
- Save up to 50% annually with quarterly penetration testing
Starting At
$4000
One time fee
- Following MITRE’s ATT&CK framework
- Offensive security expert analysis with CISSP review
- Ransomware simulation (available upon request)
Why Managed Penetration Testing?
Bring agility and automation into your penetration testing

Cost Effective
Deliver immediate ROI with an agile, efficient, and inexpensive solution
Certified Assessors
Skilled pen testers are equipped with tools up to date with the latest exploits
Actionable Results In 2 Weeks
Simple exploits or high/critical findings can be quickly reported and remediated
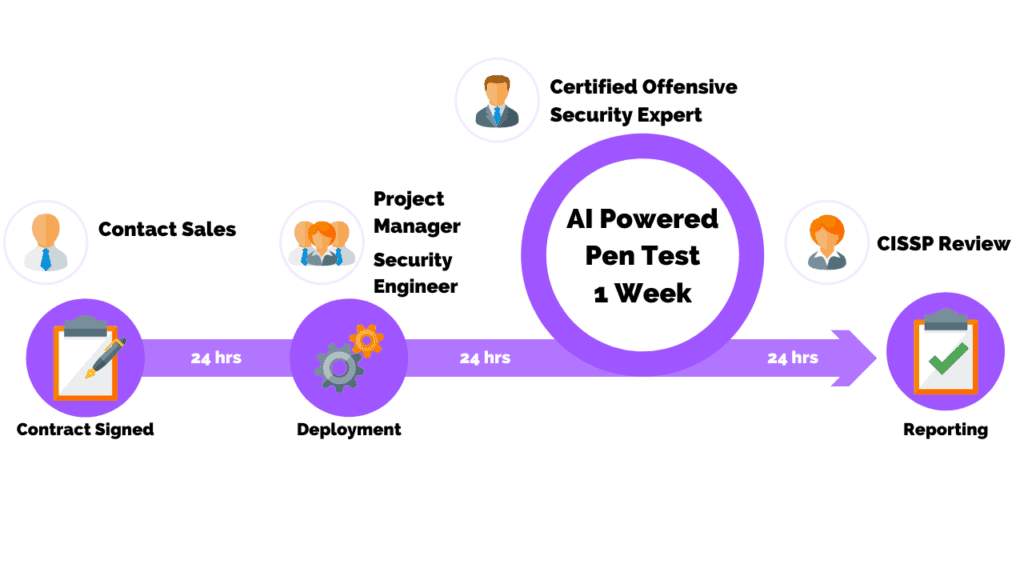
Penetration Testing As A Service
Assess your security posture and reduce your cyber risk with confidence
ONE TIME PROJECT
 What You Get
What You Get
- Assess your network, application(s), or wireless security.
- Single penetration test with an option for retesting.
- A certified offensive security expert with CISSP review.
- Remote presentation of findings and recommendations.
- The project is billed 50% down and 50% due on delivery.
No Contracts. No Setup Fees.
STARTING AT
$4,000
MONTHLY SUBSCRIPTION
What You Get
- Assess your network, application(s), or wireless security.
- Quarterly penetration testing (save 50% annually!).
- A certified offensive security expert with CISSP review.
- Remote presentation of findings and recommendations.
- The project is billed on a monthly basis.
No Contracts. No Setup Fees.
STARTING AT
$500/month
One Platform For All Your Cyber Security Validation Needs
The PurpleSec platform continuously discovers enterprises’ internal and external attack surfaces and safely validates its readiness against the latest advanced threats.
The platform proves the potential impact of exploiting each security gap and prioritizes remediation accordingly.
Why Choose PurpleSec’s
Penetration Testing Services?
At PurpleSec, our offensive security experts will establish a framework to proactively identify and classify vulnerabilities in applications or an IT infrastructure with the goal of reducing risk.
This approach ensures that we prioritize work on the areas of greatest risk by identifying the strengths and weaknesses of your penetration testing program; thereby maximizing the ROI of your security initiatives.
- Direct experience working for the Defense Information Systems Agency, U.S. Cyber Command, and other government agencies.
- Have an average of 20 years of security experience from the C-level to technical implementation and controls.
- Hold numerous certifications including CISSP, CRISC, CISM, CISA, GCED, OSCP, GWAPT, MCSE, MCP, CCNA, and more.
![]()
Project Management
Get actionable results within 2 weeks of a signed contract
Project Deliverables
Analysis and reporting delivered by an offensive security certified professional
What Type Of Penetration Testing Services Do You Need?
Learn pen test best practices and protect yourself from advanced cyber attacks
External VS Internal Test >
An external test attempts to exploit vulnerabilities by an external user. An internal test assumes an attacker has already breached your systems.
White Box Penetration Testing >
White box penetration testing is where the penetration tester has full access and complete knowledge of the target that is being tested and its features.
Black Box Penetration Testing >
A black box penetration test is a security test performed by an external party that is completely unfamiliar with the target.
Continuous Pen Testing >
Efficient & effective security. Learn how continuous penetration testing can drive down costs and improve your security posture.
Network Penetration Testing >
A network test identifies security vulnerabilities in applications and systems by using malicious techniques to evaluate the network’s posture.
Web Application Testing >
Application testing is a series of steps aimed at compromising web applications by researching, identifying, and exploiting vulnerabilities.
Wireless Penetration Testing >
Wireless testing examines all devices connected to the business’s WiFi including laptops, tablets, smartphones, and IoT devices.
Social Engineering >
Social engineering focuses on people and processes and the vulnerabilities associated with them such as phishing, USB drops, or impersonation.
Physical Penetration Testing >
Physical testing exposes weaknesses in a business’s overall physical defenses including physical infrastructure, buildings, systems, and employees.