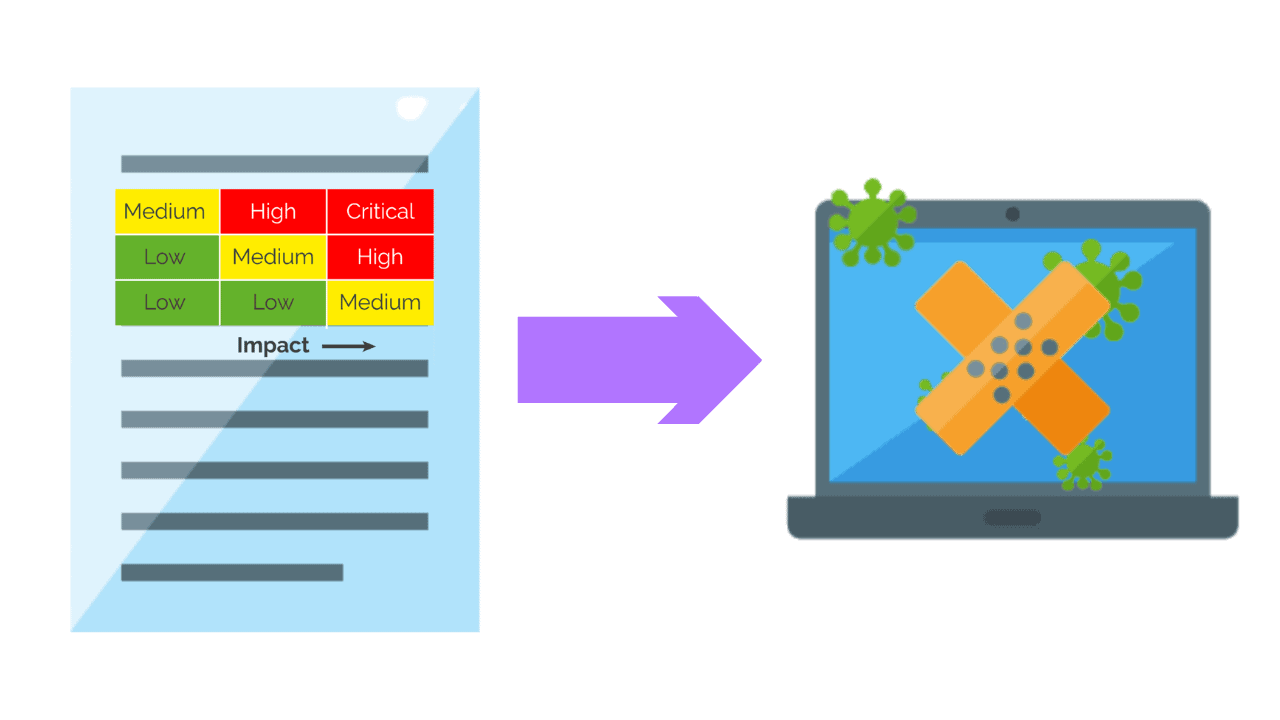
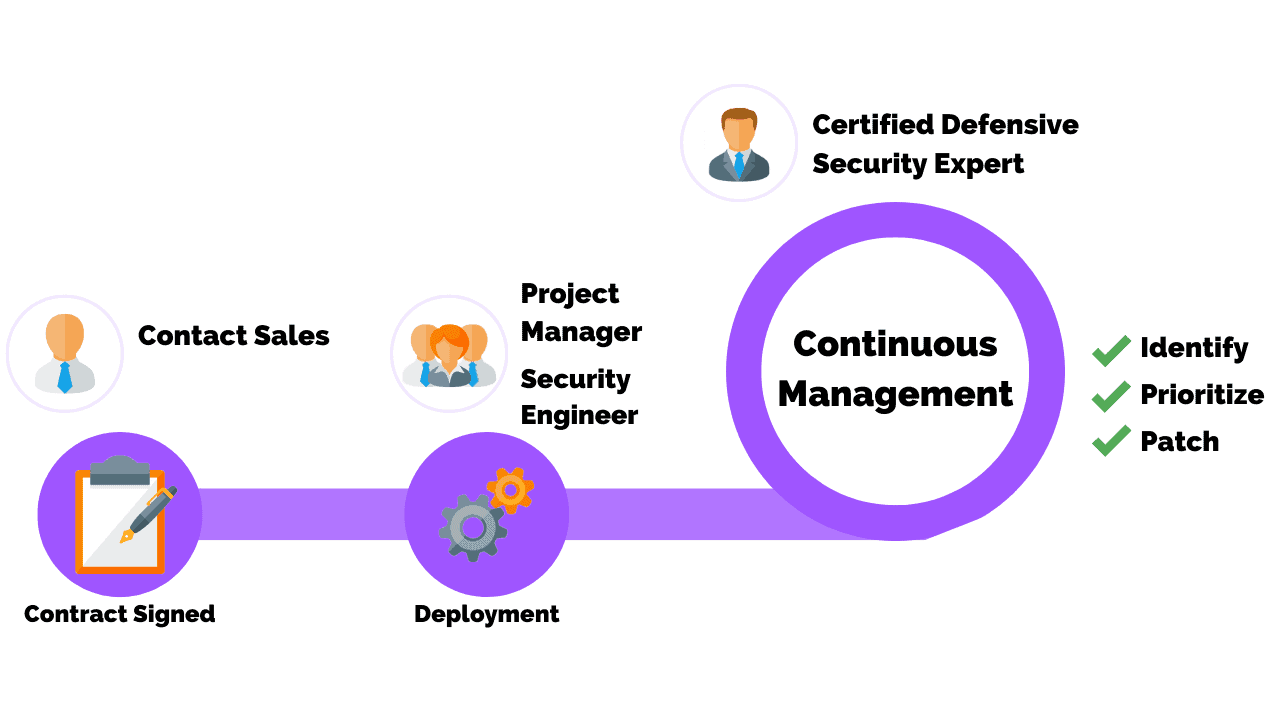
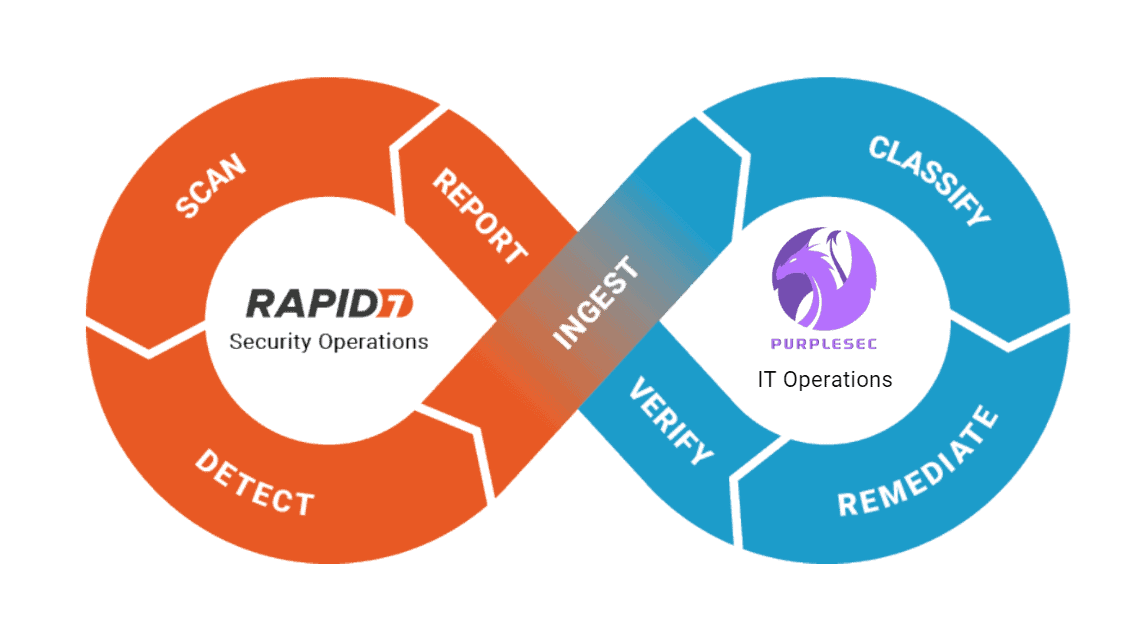
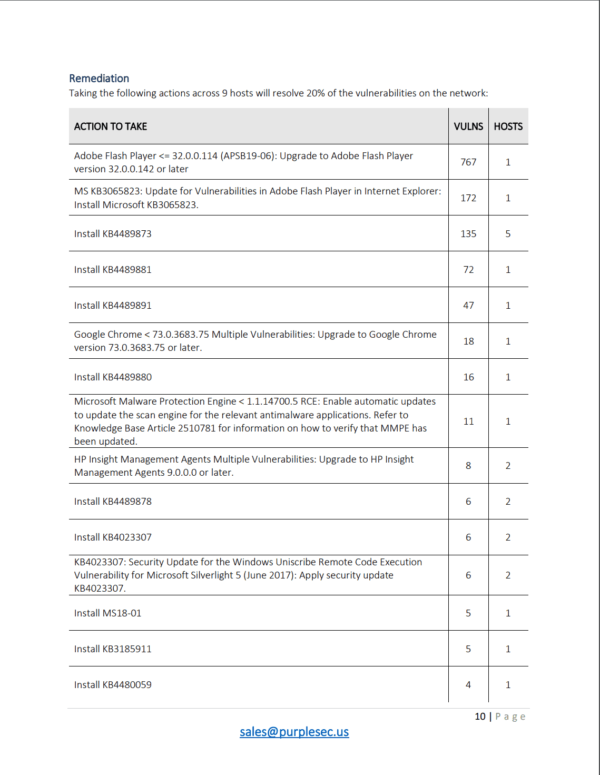
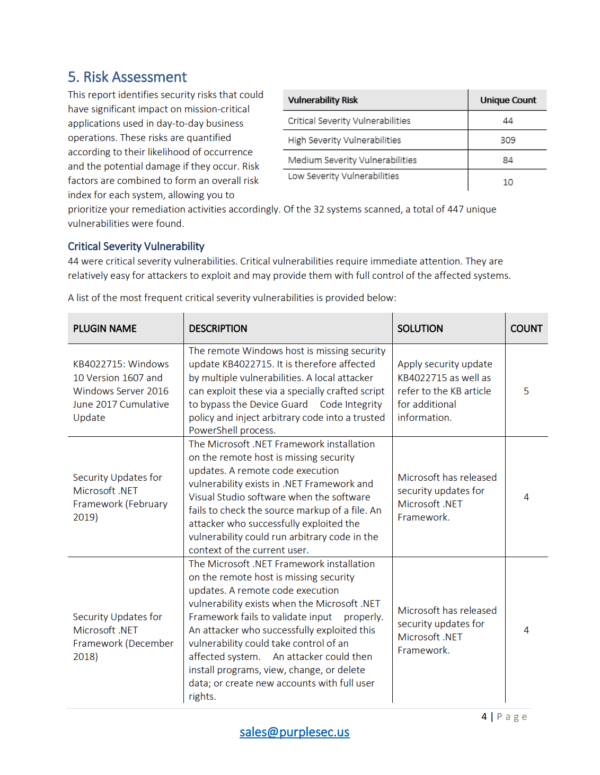
Managed Vulnerability
Automagically patch vulnerabilities with features that:
- Saves time and resources
- Improves performance and reliability
- Maintains consistency and compliance
- Reduces downtime
Helios Auto Patching
$20
Monthly subscription
(per device)
Why Vulnerability Management As A Service?
Manage and analyze vulnerabilities and risk in one place

A rapid time-to-value solution that’s easy to use and has minimal requirements for implementation, configuration or training.

Expert-defined Remediation library that immediately delivers the right fix for any vulnerability to speed up risk remediation.

Easy to configure with the ability to automate as much or as little of the vulnerability management lifecycle as you need.
The Challenges Of
Vulnerability Management
As IT environments become more complex and the attack surface expands the potential for risk grows. Organizations at all sizes struggle to prioritize and mitigate vulnerabilities at scale across highly distributed architectures.
And entire vulnerability and risk management programs are now responsible for everything from hybrid and multi-cloud environments to container images and code repositories, and as well as traditional storage and network infrastructure.
Effective mitigation processes now need to span diverse teams (security operations, DevOps, application development, etc.), each with its own business mandates, unique processes, and preferred operating technologies.


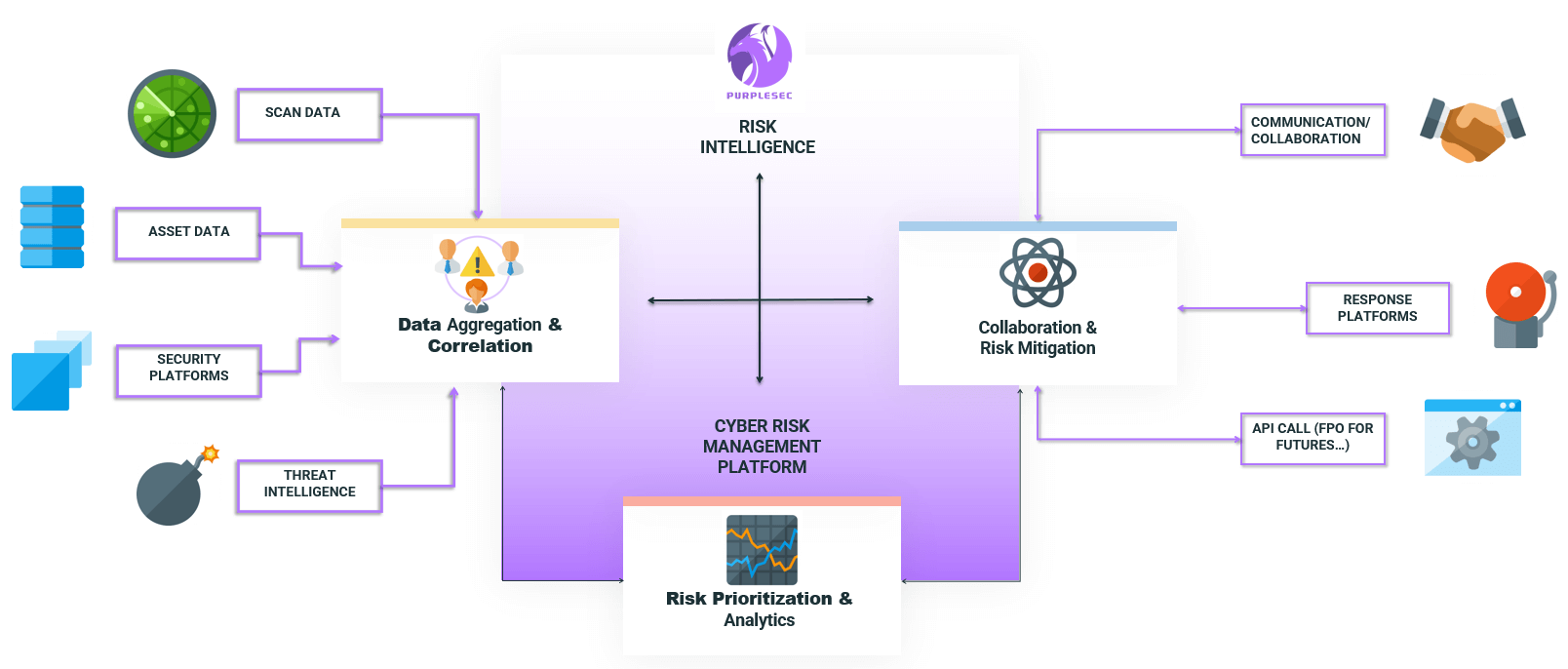
Aggregation And Correlation Of All Data
PurpleSec integrates with any vulnerability and risk detection solution, covering servers, workstations, containers, cloud workloads, code, applications, and more. It consolidates risk analysis across infrastructure, code, applications, and cloud assets, delivering full risk visibility across every potential attack surface.
Customizable Risk Analytics And Reporting
PurpleSec delivers extensive analytics and lets you create custom reports to serve different audiences and purposes, such as executive-level dashboards to track KPIs or detailed views into critical vulnerabilities and high priority tasks.
Content-Aware Vulnerability Prioritization
PurpleSec analyzes relevant data from a wide range of sources, including organizational context specific to each enterprise, and delivers expert vulnerability assessment intelligence to deliver more information and better prioritization so that you understand the actual risks to your environment and how they might impact your organization.
Communication And Collaboration With All Departments
PurpleSec enables Security, IT, DevOps, and Application Developt teams to manage risk together in the most effective way for their operating requirements, using their preferred toolsets. It is tightly integrated with ITSM, application development, DevOps, and deployment tools, as well as communication and collaboration platforms to orchestrate remediation processes more effectively.
Expert-Defined Remediation Intelligence
PurpleSec automatically enriches vulnerability and risk data using our own machine learning and expert-driven engine to deliver proprietary threat intelligence* (exploits, running campaigns, threats, and usage in the world) as well as Remediation Intelligence (recommended patches, workarounds, configuration changes and mitigations).
Automated Mitigation Playbooks
PurpleSec has an intuitive playbook builder for automating previously manual cyber risk lifecycle management and vulnerability remediation activities and tasks, reducing operating overhead and accelerating mean-time-resolution (MTTR).
What’s Inside The Report?





Learn Vulnerability Management Best Practices
Mature your vulnerability management and increase your security ROI
What Is Vulnerability Management? >
The process of identifying, prioritizing, and mitigating vulnerabilities in an organization’s systems and networks to reduce the risk.
What Is A Vulnerability Assessment? >
A vulnerability assessment is the process of identifying vulnerabilities and classifying risk in an infrastructure.
What Is Patch Management? >
Patch management refers to the process of identifying, acquiring, testing, and installing software updates (also known as patches) to an organization’s systems
Build A Vulnerability Management Program >
What makes for a successful vulnerability management program and what common pitfalls should you avoid? Our security experts explain.
Vulnerability Remediation
Plan >
Follow this step by step vulnerability remediation plan to streamline your processes, lower costs, and immediately mitigate risk.
Vulnerability Management
Automation >
Automating vulnerability management eliminates repetitive tasks prone to human error and replaces them with data-driven vulnerability prioritization.
Continuous Vulnerability
Management >
Continuous vulnerability management supports real-time visibility of vulnerabilities and risk across an organization’s network.
Risk-Based Vulnerability
Management >
Risk-based Vulnerability Management is an improvement on traditional vulnerability management because it prioritizes each vulnerability’s risk score.
Vulnerability Management
Reporting >
Streamline your vulnerability reporting and gain buy-in with all levels of management and leadership.
Ready To Hire A Vulnerability Management Expert?
Get ahead of your 2023 goals with a turnkey solution