There are 6 strategies you can implement to reduce your attack surface including:
- Assuming zero trust.
- Decreasing complexity.
- Monitoring vulnerabilities.
- Segmenting your network.
- Using strong encryption policies.
- Training your employees.
Free Security Policy Templates
Get a step ahead of your cybersecurity goals with our comprehensive templates.

Understanding the attack surface of your business is an important step to properly securing your organization’s business architecture.
Any hardware asset, software system, business application, or mobile device that is indirectly or directly connected to the internet makes up what is known as the attack surface.
Threat actors today are continuously refining their techniques to exploit weaknesses within these systems through human interaction or digital for financial gain and notoriety.
One of the primary goals of an effective cybersecurity program is to create as small of an attack surface as possible without impacting business operations.
Once this goal is satisfied, it must be continuously monitored for effectiveness, since the global threat landscape is constantly changing.
What Is An Attack Surface?
 The attack surface is the total of all possible points, or attack vectors, where an attacker can access a system and extract data.
The attack surface is the total of all possible points, or attack vectors, where an attacker can access a system and extract data.
Every access point that allows unauthorized access or actions adds to the total attack surface.
The assets and devices that comprise the attack surface can be in the form of digital or physical attack surfaces.
- Digital Attack Surface: Includes vulnerabilities found in connected hardware and software code, or applications. Threat actors thrive on this surface because they can easily scan public-facing websites for open ports remotely, crawling internet-exposed systems for weaknesses to exploit.
- Human Attack Surface: The human attack surface is the sum of all exploitable security holes or gaps created by humans within your organization. Examples include the employee’s susceptibility to a phishing attack and unintentional or intentional activities that expose corporate information to an unauthorized recipient.
- Physical Attack Surface: Includes vulnerabilities that an attacker can exploit if they have gained access to your network equipment, mobile devices, laptops, servers, USB devices, or any assets located within your server room or data center.
Strategies To Minimize Your Attack Surface
1. Assume Zero Trust
The Zero Trust Architecture security model assumes that a breach is inevitable or has likely already occurred.
Zero Trust constantly limits access to only what is needed and looks for anomalous or malicious activity.
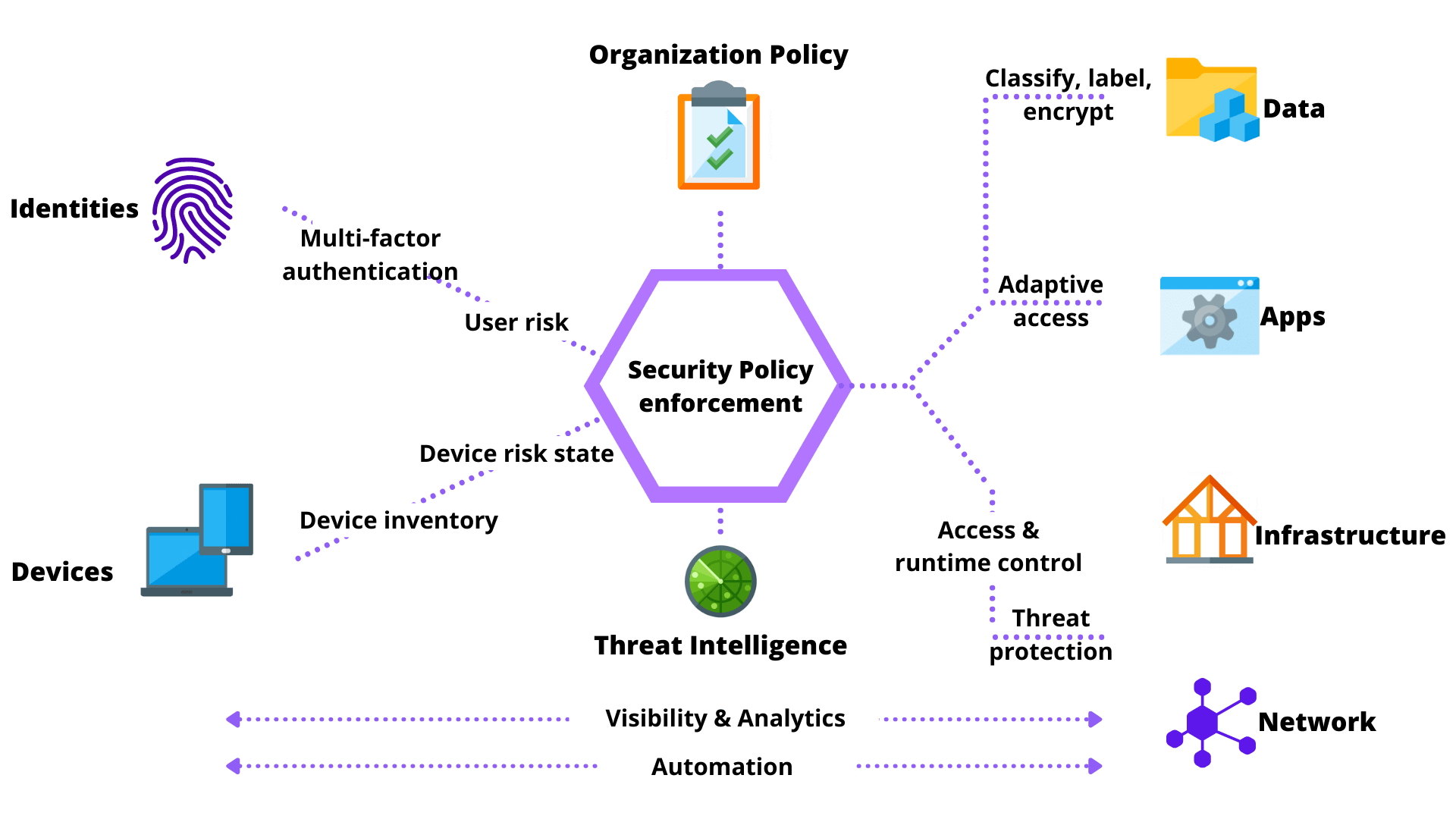
The items below are reference points that can be used to build a zero-trust system for your organization.
Identify and maintain an inventory of all assets within infrastructure:
- Understand how the network is structured, i.e., network architecture diagrams.
- Document existing security tools or applications, and determine feasibility and purpose.
- Create perimeters around every system and user (i.e., network firewalls, VPN technology).
- Maintain strict access control based on identifying access types – understand your data, where it is, and who can access, based on data classifications.
- Use multifactor authentication or MFA.
- Enroll devices into a system for identification and verification before accessing internal resources.
2. Decrease Complexity
To reduce the attack surface successfully, it bears repeating that you can’t protect what you don’t know.
It’s imperative that a complete inventory of all accounts, assets, and systems is up to date and documented accurately.
This inventory will identity out of date operating systems, legacy applications, and who and what access is required to access systems within the organization.
Note the items below that should be considered to reduce complexity within the environment and simplify controls.
- Reduce redundant or legacy software systems – ensure no end-of-life systems are on the network unless approved by senior leadership to retain.
- Assign systems and users to groups.
- Use “Least Privileged Access” principle:
- Users are only given access to a minimum of systems/software needed to complete the job.
- Applies to system and software access controls.
- Requires centralized user access management and secured secrets for access (password vaults).
- Centralize access control management with an application or an Identity Access Management system.
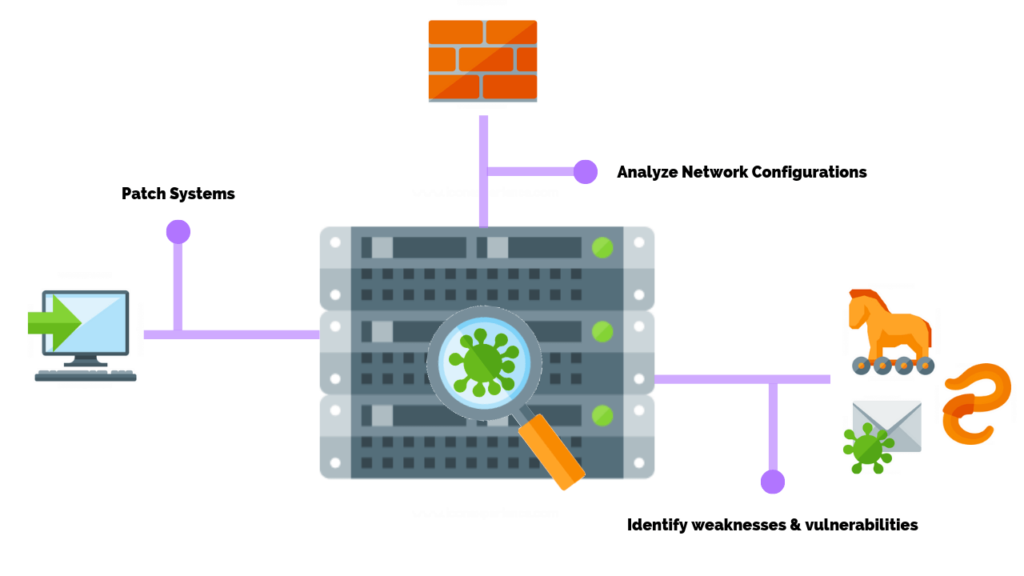
3. Monitor Vulnerabilities
The most important aspect of a zero-trust architecture is to be able to continuously monitor your attack surface.
The tools used to support the management of your attack surface must be able to alert on exposed assets and allow you to verify the successful remediation of a detected risk.
The items below provide direction on how to monitor the attack surface for vulnerabilities.
- Perform continuous vulnerability monitoring – Implement a solution that allows for scheduling or ad-hoc scans of internal and internet-exposed assets with complete reporting of severity grades and recommended remediation.
- Ensure full network visibility – Understand the layout of the network, including all ingress/egress points.
- Prioritize based on risk – This goes back to the asset inventory. Servers and the applications that reside on them should be prioritized according to business impact. Vulnerability scans can be created based on the pre-defined priority.
- Remediation – Create a vulnerability remediation plan or ensure the expectations are documented and approved in a policy.
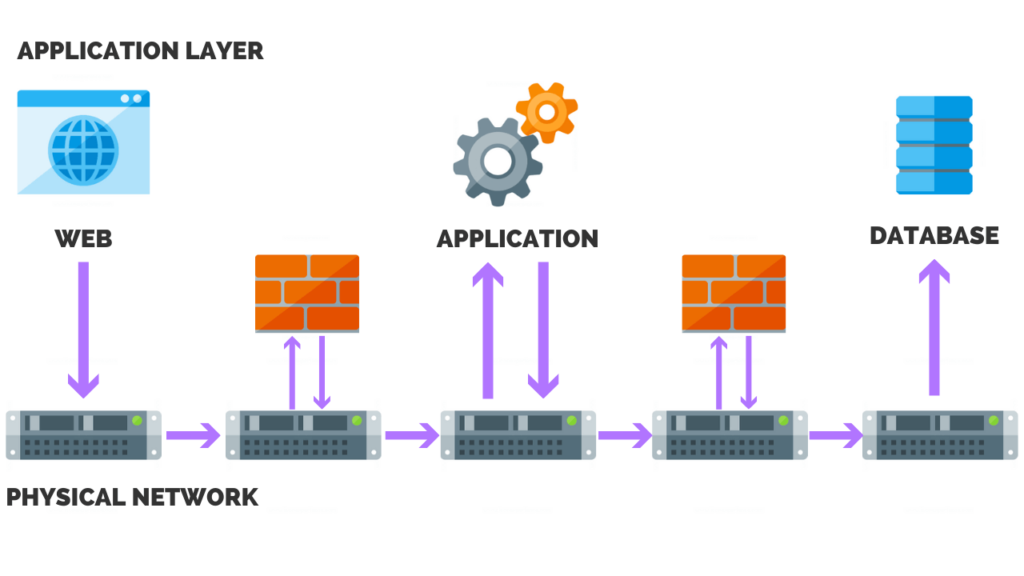
4. Segment Your Network
The term network segmentation has become a household name recently due to the prevalence of ransomware attacks spreading across an organization’s network, crippling their enter network infrastructure.
In basic terms, segmentation refers to setting boundaries around certain areas and limiting access from one section to another, to prevent lateral movement in case of an attack.
This method isolates the attack to one area of the network, which in turn minimizes the attack surface.
The bullet points below provide additional information on why network segmentation is critical in managing the attack surface of your network.
Encapsulate systems and users based on data classification:
- Ensure application traffic is encrypted between highly classified systems – including database systems.
- Build network segmentation based on business roles and functions.
- Encrypt traffic between on-premises data sources and cloud systems, i.e., Office365, Salesforce, Azure, and AWS.
Simplify access controls with centralized management:
- Requires having robust network controls between segments.
- This should include network IPS and IDS to monitor outgoing and incoming data for malware
- Utilize a centralized tool to manage, log, and report metrics.
Articulate the purpose of network segmentation to peer teams and organization leadership:
- Helps contain attacks.
- If one environment is compromised it can’t impact others.
- Stops the spread of malware.
- Prevents elevation of access.
- Easier to recover one segment than the entire infrastructure.
- Create perimeters around groups of systems and data.
- Access controls and monitoring between each segment.
5. Use Strong Encryption Policies
Encryption policies provide the strategy that determines:
- What data should be considered classified or sensitive.
- Its whereabouts on the network.
- How it is accessed.
- Address compliance requirements.
- How the encryption is applied.
- Other relevant information related to the data in its resting state on a server or database.
Encryption is a powerful method that can be used to manage the attack surface especially if the data is leaked, lost, or moved outside of the organization.
The following items are basic steps that support a strong encryption policy:
- Enforce strong encryption based on data classifications – Know your business vertical.
- Healthcare, the Payment Card Industry (PCI), and the Federal Government classify different and will have different encryption requirements.
- Use modern versions of cipher suites.
- Replace legacy devices that don’t support modern encryption.
6. Train Your Employees
You may have heard it mentioned that the weakest link in an organization’s cybersecurity program is the person behind the keyboard.
That may be true to an extent, but their weakness and what they do behind the keyboard may be indicative of their security awareness – which points back to who?
It’s the responsibility of the compliance and security teams to instruct their employees on how to quickly identify and react to phishing or social engineering attack.
The employees should follow through as well on their security awareness training, so the accountability is two-fold.
Let’s see what can be done to prepare your employees for the attack that is referred to as the “human or physical attack surface.”
- Schedule and implement regular phishing simulations.
- Provide security awareness videos to all employees.
- Post security awareness tips in high-traffic areas or internal web communications.
Frequently Asked Questions
How Do You Measure Your Attack Surface?
The final measurement to reduce the attack surface is analysis.
Security configuration assessments, traffic flow analysis, and quantitative risk scores are three common methods of analysis that can be extremely effective in reducing the attack surface.
What Is The Difference Between An Attack Vector An An Attack Surface?
An attack vector is the path or route that malware or malicious actor may use to compromise your network and access your data and services.
The attack surface encompasses all your company’s attack vectors.
In other words, your attack surface is the set of all possible methods an attackers may employ to compromise your network.
Attack vectors may include the following:
- Weak passwords
- Shared passwords
- Software vulnerabilities
- Software misconfigurations
- Denial of service
- Stolen credentials
- Phishing
What Is The Human Attack Surface?
Simply defined, the human attack surface is the sum of all exploitable security holes or gaps created by humans within your organization.
Examples include the employee’s susceptibility to a phishing attack and unintentional or intentional activities that expose corporate information to an unauthorized recipient.
What Is The Digital Attack Surface?
The digital attack surface area encompasses all the hardware and software that connect to an organization’s network. These include applications, software code, network ports, servers, and websites, as well as Shadow IT.
How Often Should You Assess Your Attack Surface?
The frequency of assessing your attack surface depends on the identification of the attack vectors that exist within your organization.
The vulnerabilities associated with the attack vectors are continuously under attack, therefore, the assessment of the attack surface should be continuous as well to counter the constant flow of attacks from threat actors.
Many organizations incorporate real-time monitoring and scheduled vulnerability scans to protect the infrastructure.
The main objective for any organization would be to continuously assess their attack surface.
Article by




