Vulnerability & Patch Management Metrics: Top 10 KPIs to Measure Success
Learn about PurpleSec’s fully managed vulnerability management services.
Author: Michael Swanagan, CISSP, CISA, CISM / Last Updated: 04/23/2023
Featuring: Walter Haydock
Reviewed By: Josh Allen & Rich Selvidge, CISSP
View Our: Editorial Process
Table Of Contents
The top 10 vulnerability management metrics you should be measuring include Average Time To Action, Mean Time To Remediation, Risk Score, Acceptance Risk Score, Average Vulnerability Age, Internal Vs External Exposure, Rate Of Recurrence, Total Risk Remediated, Asset Inventory/Coverage, and Service Level Agreement (SLA).
What You’ll Learn
- Why tracking vulnerability and patch management metrics are essential for any security program.
- The top metrics you need to track along with lesser important metrics that are “nice to have.”
- How to better measure successful outcomes of your vulnerability management program.
- How PurpleSec is improving the vulnerability reporting process.
Reporting the results from vulnerability scanning without a set of clearly defined metrics is an issue many organizations face today.
Presenting vulnerability reports to senior management without key metrics will also limit your ability to effectively communicate the overall risk of your organization.
Faulty reporting of vulnerability metrics not only creates blind spots for your security and infrastructure team, but your executive leadership and stakeholders will not understand the true value of the vulnerability program and will question the return on this security investment.
In this article, we will help you identify and define the top key metrics that your organization can implement to track the progress and state of your vulnerability and patch management programs.
We will also discuss the differences in KPI’s and demonstrate how PurpleSec can help you measure and report on successes.
Let’s now take a look at why vulnerability metrics are critical to your program.
Why Vulnerability Metrics Are Critical to Program Success
Vulnerability metrics are critical to the successful measurement of your vulnerability management program. They measure the status of your remediation strategy and patching effectiveness.
Without a consistent system of reporting the status of your program, the likelihood of exposure to a data breach increases as reported in recent breach statistics of 2022.
When considering which metrics to report, the approach should not be to simply gather statistics and charts, but it should focus on prioritizing remediation efforts on of your most critical systems and applications.
The steps to gather the right metrics for your organization will take care planning by your IT and security teams. This can be accomplished by understanding the importance of gathering metrics.
Note the following four areas that can help you get started:
Risk Awareness
Metrics quantify the state of risk of your organization into a format your teams and stakeholders can understand.
The right metrics can also elevate risk awareness and understanding for your business leaders to support the vulnerability management program.
Planning
A consistent program for gathering metrics can help your organization plan for reducing risk each time a new application or system is introduced into the environment.
This approach can also evaluate if business objectives are met and if additional resources are required.
Audits
If metric reporting is already an established process of your vulnerability program, your internal or third-party audits will more than likely result in success.
NIST and CMCC compliance requirements can help you identify weaknesses in your vulnerability program.
Resource Allocation
Metrics can help pinpoint areas of risk within key business applications or at the development stage.
Once identified, your leadership teams can determine where and if additional resources are needed to reduce risk or close gaps within the system.
Top 10 Vulnerability And Patch Management Metrics
The following 10 metrics can apply to either vulnerability or patch management reporting:
- Average Time To Action
- Mean Time To Remediation
- Risk Score
- Accepted Risk Score
- Average Vulnerability Age
- Internal Vs External Exposure
- Rate Of Recurrence
- Total Risk Remediated
- Asset Inventory/Coverage
- Service Level Agreement (SLA)
Depending on the type of vulnerability scanner, a few of these metrcis may already be pre-built into the reporting engine.
If you choose to customize your report, review the context of each metric and select as needed to fit your organization’s needs.
1. Average Time To Action
This important metric reveals how responsive your team reacts to the results of the reported vulnerabilities.
This metric should be consistently low since the security team is accountable for delivering the message and action plans for remediation to business owners.
3. Risk Score
This value is usually automatically calculated from the vulnerability report. This score illustrates the cumulative risk of your vulnerabilities per severity level, i.e. Critical, High, or Medium.
4. Accepted Risk Score
If your organizations decide not patch a specific or group of vulnerabilities within a specified time period, this is an acceptance of risk.
Acceptance of risk should be tracked, scored, and reported to help the organization understand the potential for exposure and the risk that has been accepted.
5. Average Vulnerability Age
The vulnerability age is the number of days since a vulnerability was publicly disclosed. Tracking this metric will help your organization create remediation plans that aligns with your SLA.
6. Internal Vs External Exposure
Your external internet facing applications inherently are at highest exposure to outside threats compared to internal. An organization should have separate scanners for each environment.
Although an external scan has high priority, internal scans should be prioritized as well due to the potential of a threat actor entering your network and exploiting a threat is always probable.
7. Rate Of Recurrence
A remediated vulnerability that returns on the same or different asset may indicate a problem with the baseline configuration or lack thereof.
Tracking this metric continuously will enable your infrastructure teams to closely review process errors or system configuration issues.
8. Total Risk Remediated
Total risk remediated is a key metric that illustrates the effectiveness of your vulnerability management program to your IT and executive management teams.
When your total risk remediation is trending upward continuously, this may demonstrate to your business stakeholders the effectiveness of your security investment.
9. Asset Inventory/Coverage
This metric identifies the number of assets that should be patched. The vulnerability management tool should have auto discovery functionality to detect new systems on the network.
Tracking this metric will help you identify how your environment is trending, or if new assets are added and serviced by a ticketing or inventory system.
10. Service Level Agreement (SLA)
The Service Level Agreement determines when a patch is expected to be remediated. This value should be documented within your vulnerability management policy.
This metric is the baseline tracker for remediation – i.e., Zero-day attacks may require immediate remediation, a Critical Severity finding may have a duration of 7 days.
SLA values may also be dependent on the priority of the asset as well, per your organization’s needs.
Less Important KPIs
The following metrics provide useful data on detection times, severity detail, and quantity of vulnerabilities.
They are considered less important due to their lack of direct impact on risk reduction.
Mean Time To Detect
Mean Time to Detect is the average amount of time between the beginning of a vulnerability and the discovery of the vulnerability by your IT or security team.
Although this is a useful metric, the most important takeaway from this vulnerability is the action to be performed after it’s detected.
In addition, when deploying a continuous vulnerability solution, your mean time to detect should be days or hours – not weeks or months.
Average CVSS Scores
Common Vulnerability Scoring System (CVSS) provides a numerical representation of the severity of a vulnerability to help incident responders prioritize remediation efforts.
Although CVSS scoring does not directly indicate risk, it can provide valuable insight into software or systems that may be at risk.
Open Vulnerabilities
Tracking open vulnerabilities is a useful metric that illustrates your current technical debt across all of your systems. The numerical value of open vulnerabilities is not a risk rating.
The value of the metric is realized when combined with other metrics to prioritize a vulnerability remediation process for critical systems.
How To Measure Successful Vulnerabilities
Management Outcomes
So far, we’ve defined why metrics are important for reporting and identified top metrics that should be included in your reports.
In this section, the goal is to ensure you are capturing data from all sources within your network.
Once this data is consumed into your reports, you will be in a position to tell the story with your results.
Obtain Reports From All Sources
It is important to understand the type and whereabouts of all assets connected to your network. Assets not accounted for may result in unpatched systems and inaccurate reporting of your risk posture in network vulnerability reports.
Include reporting from your blue and red team tools to provide comprehensive insights into your vulnerability management lifecycle.
The outcome will result in better prioritization of remediation plans of your most critical systems through validation.
This inclusive reporting approach will enable your teams to identify targets for further testing.
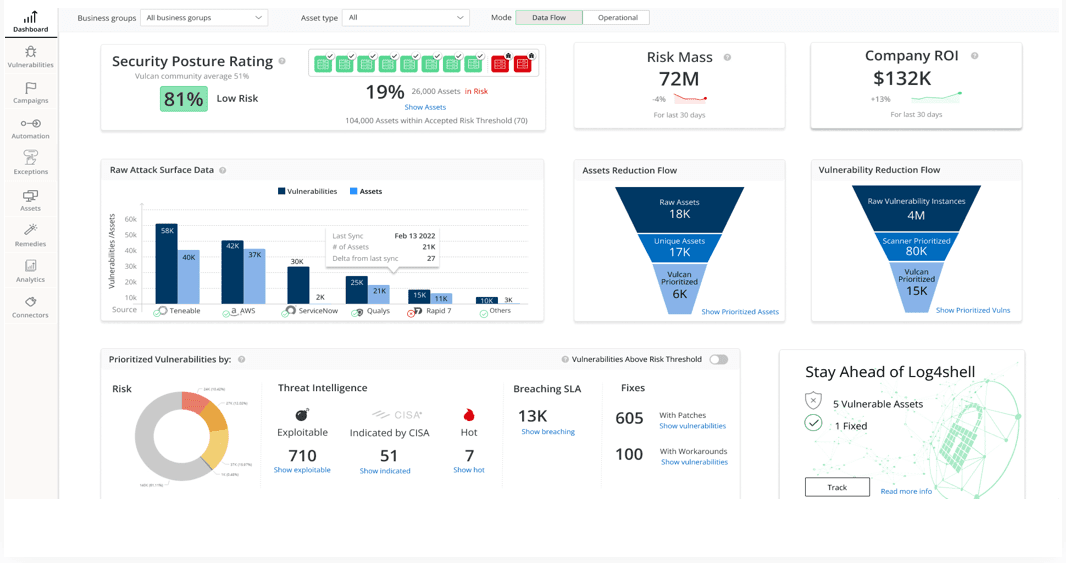
Centralize Metrics With Dashboard Reporting
Multiple reporting dashboards for each tool can make demonstrating results difficult to manage.
Centralizing your reporting into a single pane makes it easier for your organization to observe the positive impact your vulnerability program, which leads to more success.
Present Metrics Based on The Story You Need to Tell
Present the most important KPIs first based on your organization’s needs.
Your stakeholders need to know what the risk impact is to the business. Present the metrics that focus on the priority of critical systems and risk that have been accepted.
Present metrics that match the SLA’s documented in your vulnerability management policy. This will demonstrate the timeliness of patching systems to reduce your overall risk profile.
Let’s now take a look at how PurpleSec can help improve your reporting capabilities with automation.
How PurpleSec Improves Reporting With Automation
PurpleSec’s Vulnerability Management platform can help your organization improve your reporting capabilities. Note the following features of this platform and how it can complement your existing framework.
Orchestrates & Automates Reporting
PurpleSec can help you deliver and customize reports that measure the state of your vulnerability program.
Let’s examine the key components of the reporting engine that will supercharge and enhance the value of your vulnerability management program.
You can create an executive dashboard for managers or a general view for infrastructure teams or business units for up-to-date statistics.
Dashboards generally provide an export feature which allows the generation of instant reports.
Fully Managed Solution
PurpleSec’s security experts will partner with your teams to understand your objectives and setup everything you need to make informed decisions about your security posture based off reported metrics.
Our teams are made up of certified information security professionals who can consult, manage, and approve security processes by automating vulnerability management reporting.
Wrapping Up
In this article, we have reviewed the value of reporting key vulnerability and patch management metrics.
As your organization manages its vulnerability management program, it is critical to provide the right metrics that clearly demonstrate risk to your high priority systems along with the tracking of risks that have been accepted.
By following the recommendations of measuring risk through metrics reporting, your IT teams and stakeholders will be able to clearly observe the outcomes and successes of the vulnerability management program.
Your organization will also improve its security posture by having a continuous vulnerability management program to reduce risk.
If you would like to learn more about PurpleSec’s Vulnerability Management platform, please schedule a demo by clicking the link below and one of our security experts will be in touch.
Ready to speak with one of our experts? We want to help you with your next project. Schedule a demo.

Michael Swanagan, CISSP, CISA, CISM
Michael is an IT security expert with 15 years of proven experience. He has experience leading and supporting security projects and initiatives in the healthcare, finance, and advertising industry.
Recent Articles
Categories
Policy Templates
Most Popular