There are 8 best practices when planning your vulnerability remediation including:
- Prioritization of vulnerabilities.
- Setting timelines.
- Defining a SLO.
- Developing a remediation policy.
- Automating your vulnerability management processes.
- Adopting continuous remediation.
- Deploying compensating controls.
- Building a vulnerability management program.
Free Security Policy Templates
Get a step ahead of your cybersecurity goals with our comprehensive templates.

Cyber attacks are quickly increasing every year.
While some attacks require sophisticated knowledge of networking or well-funded campaigns, the vast majority are carried out in the simplest of ways. How?
There are a number of reasons:
- Low technical barrier of entry
- More open-source tools are available
- Poor cyber hygiene from organizations and individuals
Organizations, especially SMBs, are being required by clients, vendors, and insurance providers to prove security best practices are being followed.
However, many take an ad hoc or relaxed approach to their vulnerability management and remediation requirements.
In this article, we will lay out a template for a vulnerability remediation plan your organization can follow that will streamline processes, lower costs, and immediately mitigate risk.
Vulnerability Scanning
Reduce your exposure and meet
compliance and vendor requirements
Monthly Subscription
(per device)
-
Continuous scanning
-
Web and network scans
-
Weekly reporting
-
Vulnerability assessment
-
Advisory services
*Requires a minimum of 5 devices. Subscription will automatically renew for 1 month from the date of purchase unless you cancel.
Vulnerability Mgmt
Complete management of vulnerabilities
across all assets and applications
Monthly Subscription
(per device)
-
Continuous scanning
-
Automatic patching
-
Web and network scans
-
Weekly reporting
-
Vulnerability assessment
-
Advisory services
*Requires a minimum of 5 devices. Subscription will automatically renew for 1 month from the date of purchase unless you cancel.
What Is Vulnerability Remediation?
Vulnerability remediation is a process of eliminating detected weaknesses in your network. This process includes the discovery, prioritization, remediation, and monitoring of a vulnerability to ensure a successful long-term fix.
It’s also one of the many benefits of vulnerability management that delivers an actionable outcome for enhanced security.
What Tools Are Required?
Determining the software and other tools you use can impact how you roll out and manage vulnerability remediation.
A defensive security engineer on a blue team might use several tools to scan, analyze, and patch vulnerabilities to complete their remediation tasks.
Nessus may be used to scan and identify exposures during a vulnerability assessment, whereas other platforms could be leveraged for vulnerability prioritization and asset management.
With Rapid7, a security engineer could test with changes to the code and re-run to see whether the fix works.
Once you’ve decided on the right vulnerability remediation tool for your needs, the next important build to your arsenal is managing an effective team.
Managing The Remediation Team
Managing a vulnerability remediation team requires a multilevel effort with a clear set of roles and responsibilities.
Without the correct roles and organizational structure defined for your organization, a vulnerability remediation plan will not have the support to achieve its goals.
The C-Suite
Starting at the top includes the Chief Technology Officer (CTO) or Chief Information Security Officer, (CISO).
These roles are charged with delivering a security outcome for the business, reporting results to senior leadership and stakeholders. These roles are focused on long-term strategy and securing funding for their programs.
The Security Manager
Operationally, a vulnerability remediation team relies on a Security Manager to assign and drive the rest of the team in reaching its objectives.
Depending on the size of the organization and maturity of the program, a Security Architect will build a design for the process and development of the project.
The Security Architect
Sometimes the Security Architect will report to the Security Manager, but in many cases both the Security Architect and Security Manager will report to the Senior Manager or Security Program Director.
The Security Engineers & Analysts
The team members deploying the tasks determined by management (the “hands on keyboard”) are the security engineers, responsible for scanner configuration and other technical aspects, and security analysts, who monitor and report on vulnerabilities within the context of the organization’s asset management.
Together, the duties of the engineer and analyst will result in the delivery of a vulnerability remediation report.
These roles commonly report to a team lead, who then reports to the Security Manager, but it’s common for security engineers and analysts to report directly to the Security Manager, especially within small organizations.
The Vulnerability Remediation Lifecycle Explained
Now that you have identified which tools to use and how to organize your team, we can begin to address what is involved in the remediation of a vulnerability.
The vulnerability remediation process is broken down into 4 key steps:
- Find
- Prioritize
- Fix
- Monitor
Step 1: Find
The most straightforward way to find a vulnerability is to scan your network and conduct a vulnerability assessment.
Read More: How To Conduct A Vulnerability Assessment
These will help to discover misconfigurations or coding flaws that can be used to compromise or exploit an application or system.
With these vulnerabilities now known, you can move on to the next step.
Step 2: Prioritize
Not every vulnerability is the same, meaning not every vulnerability requires the same treatment.
The most critical vulnerabilities could include ones that are backlogged, not just newly discovered ones.
To map out the severity levels facing your organization you can assign a risk scoring card or matrix to prioritize which vulnerabilities to remediate.
Step 3: Fix
Once you have prioritized your vulnerabilities you can begin addressing the ones at the top of your list.
By implementing a patch management process, your security infrastructure or engineering team will repair and test each vulnerability at a time.
These could be short-term or long-term fixes.
Step 4: Monitor
To ensure the reliability of patches and to keep updated on any irregularities or changes to the vulnerability, it’s important to maintain continuous monitoring.
This step can be done either manually with the aid of a security analyst or more commonly now with the use of automated tools.
These steps are an ongoing process designed to organize and continually strengthen your cyber defense.
Remember, the bad guys don’t sleep, and neither should your security monitoring.
Vulnerability Remediation Best Practices
To bring added value to your organization, understanding a few industry best practices for vulnerability remediation will go a long way to help further mitigate risk, streamline processes, and reduce costs.
1. Prioritize Vulnerability Remediation
Prioritization is a central feature for organizations to address when building up their defenses. A successful practice is to follow the alignment of vulnerability management to risk appetite.
A risk-based vulnerability management approach is accomplished by examining the attack surface of the organization and prioritizing the remediation of vulnerabilities based on associated risks.
This is a preferred method because the results improve visibility and awareness of which systems are most at risk if exploited.
It’s important for organizations to follow this risk-based approach when aiming to remediate vulnerabilities, rather than trying to tackle vulnerabilities based on severity.
An organization should not just target critical and high vulnerabilities but consider the specific business impact all vulnerabilities may have if exploited.
It’s possible for a high severity vulnerability to be less impactful to a specific organization. Instead, there could be a less severe vulnerability, but one that yields a higher overall risk to the organization due to it being a key component of operations or relation to assets.
With this approach, you should identify critical business systems that should be prioritized, then prioritize your vulnerability remediation to these at-risk systems.
2. Set Vulnerability Remediation Timelines
The heightened intensity of vulnerabilities being exploited has caused greater attention and formal processes to be required by organizations to prove their compliance with set standards.
Establishing service level agreements (SLA) for vulnerability remediation is a way in which an organization can set a course for achieving remediation goals on a fixed timeline.
Partnering with a vendor for vulnerability management can help to ensure remediation is completed in days or months.
Achieving these goals is critical for organizations that must maintain compliance.
Something to keep in mind is how a specific framework aligns to your organization’s goals because frameworks that establish compliance have their own definitions and remediation timelines.
For instance, under the Payment Card Industry Data Security Standard (PCI DSS), any vulnerability with a CVSS score (Common Vulnerability Scoring System) of 4 or higher must be remediated within 30 days of notification.
In contrast, the Cybersecurity Maturity Model Certification (CMMC) requires remediation within 3-12 months, depending on an organization’s resources to implement repairs.
Having this documentation will not only help to prove compliance to clients and regulators but will support a more organized and efficient operation when fixing vulnerabilities.
A remediation timeline does not need to be overly complex. It just needs to be clear.
3. Determine Your Service Level Objective (SLO)
Properly defining your organization’s objectives will help to establish goals.
A service level objective (SLO) is a method designed to benchmark and track performance as it adheres to policy.
This method is especially helpful when remediating vulnerabilities because it can help to confirm your organization’s alignment with compliance frameworks.
You may have weekly, monthly, or quarterly goals, such as maintaining 95% compliance for all workstations and servers.
Or, you may have longer-term objectives such as reaching 99% compliance across all systems by 2025.
Using an SLO as a metric for charting vulnerability remediation will lay out a clear path for you and your stakeholders to see where the organization is and where it’s going to reach its goals.
4. Develop A Vulnerability Remediation Policy
So far, we’ve discussed compliance frameworks and service-level agreements, but what about your vulnerability policy?
Developing an internal policy will help to streamline operations and reduce risk.
Vulnerability Assessment Policy
A regularly implemented vulnerability assessment is a common requirement for most organizations. To create your policy, you’ll want to start with building your vulnerability assessment policy.
Every assessment is different and will require multiple parts of the organization to contribute to its formation.
Legal, finance, IT, and other departments will help to shape a holistic approach when identifying all the possible avenues of risk associated with your organization.
Patch Management Policy
You will also want to develop a patch management policy.
This type of policy is especially important because it involves the action that goes along with fixing the identified vulnerabilities from your assessment.
Knowing who will be responsible for patches, timelines, and priorities will help focus the effort toward remediation.
The major goal here is to create a policy where everyone is on the same page and processes are continuous.
5. Automate Your Vulnerability Remediation
As systems become increasingly complex and integrated, it’s desirable to move away from manual processes where possible.
This is especially true for a vulnerability remediation plan.
To make work more efficient, you’ll want to use technologies to automate vulnerability management.
However, it’s recommended you do so in a controlled fashion that limits disruptions to business systems. To do this you can automate your testing workflows and triage process.
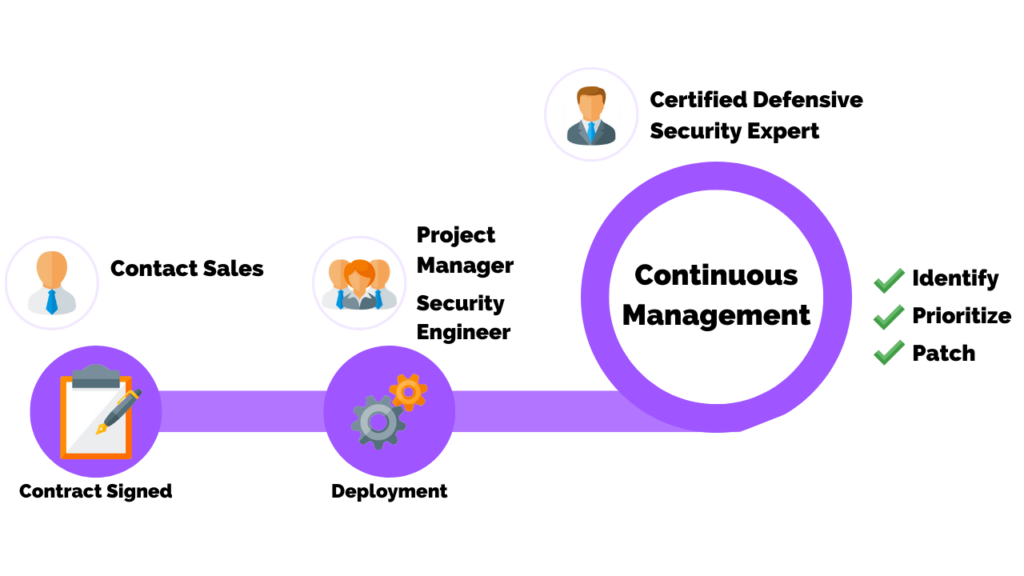
6. Continuous Vulnerability Remediation
This article has expressed the importance of continuous processes to harden cyber defenses.
It cannot be overstated…continuous vulnerability management is a must!
Scanning just once per month means you’re vulnerable the other 29 days of the month. It’s not just a one-and-done task – it must be continuous to truly reduce risk, especially against zero-day attacks and ransomware.
7. Provide Compensating Controls
To reduce risk, appropriate compensating controls are recommended.
While this could mean including some of the features previously discussed, such as assessments and patch management, remediation efforts often go beyond discovery or deploying a patch.
Defining and enforcing baseline configurations and implementing a threat monitoring process are other controls that may apply.
You may find a weakness or flaw in your application’s code that requires your software developers to re-write, test, and push it into production.
Or there may be a way to bypass your default Windows security controls that require configurations to be updated.
Regardless of which controls your organization decides to use, it’s important to understand that going above and beyond what is sufficient will provide a greater security value.
8. Build A Vulnerability Management Program
So, you now have tools, a team, policies, controls, and a process to continuously roll out remediation. This seems like a lot.
And each of these items on their own certainly are. So how do you centralize all these efforts to become more effective?
Establishing a formal vulnerability management program will strengthen your organization’s security posture by ensuring an ongoing process of discovering, investigating, and mitigating vulnerabilities on an enterprise network.
Additionally, it will help to identify ways to improve current processes to deliver more efficiency on dollars spent on security and will support a pipeline for planning your cybersecurity strategy 2-3 years down the road.
Reporting On Vulnerability Remediation
To keep goals in check and to fulfill requirements from leadership or stakeholders, having consistent reporting on vulnerability remediation is vital.
There are several ways to report the status of remediations, and depending on your organization, more than one type could be required.
- Dashboard Reporting – A highly efficient means of reporting is to be able to generate instant reports. As a means of automation, dashboards provide real-time data that can be pulled at any time! Dashboards for each business unit provide up-to-date statistics and campaign tracking.
- Monthly Reports – Summary report of compliance and remediation statistics available by system types and business unit. These reports are tactical in nature and will include the internal team, project, leads, and 3rd party vendors.
- Quarterly Reports – Higher level overview of progress towards milestones and objectives. Often includes internal team members, project leads, 3rd party vendors, and key executive stakeholders.
- Annual Reports – Annual review of the remediation process to reassess objectives and set new goals.
- Executive Reports – Include vulnerability metrics that visualize the state of the remediation process over time.
Top Vulnerability Remediation Challenges
Now that we’ve discussed best practices and reporting, let’s address a few challenges that organizations commonly face when implementing a vulnerability remediation plan including:
- Lack Of Defined Remediation Process
- Lack Of Communication
- Supporting End Of Life Systems
- No Testing Environment(s)
- Bypassing Change Management
- Data Overload
- Decentralized Asset Management Database
Lack Of A Defined Remediation Process
Stopping before you even get going. The lack of definition or structure behind business processes, in general, is doomed to failure.
The same is true for a weak remediation plan.
It’s unsettling, but many take an ad hoc approach to vulnerability remediation. Without a policy that defines the remediation process, it will be difficult to prioritize and sustain remediation efforts over time.
Communication
One of the most understated and important soft skills of all time! Having clear, open communication is required, and valued, when working with multiple people across multiple teams.
This includes working with 3rd party vendors that need to be managed.
You’ll need to provide resources on your team’s end including providing access to systems, services, and employees and assigning a project manager to keep workflow moving.
Each of these depends on a high volume of in and out communication to make sure everything runs smoothly.
A way to construct a more communicable work environment is to support your teams with the use of the rights tools.
Centralized communication and use of project management software, such as Trello, Slack, WorkBoard, or Jira, can help to assign tasks and manage milestones and objectives.
Consider implementing workflow automation that generates tickets or notifications to support teams.
Remediation impacts multiple teams and business applications. Lack of communication may result in unplanned downtime or disruption of service.
Supporting End Of Life Systems
Patches do not always successfully deploy, even when tested. This is especially true of legacy systems that may not be properly maintained.
Unfortunately, many organizations fail to update their systems due to inconvenience or costs.
However, ignoring end-of-life systems or repeatedly trying to apply short-term fixes that ultimately fail only heightens the security risk, potentially adding a lot more in long term costs.
Lack Of A Test Environment
Having an adequate test environment for security engineers to perform various tasks to remediate a vulnerability while a system or application is running is incredibly important.
Applying patches directly to a production system may lead to unplanned outages and impact operations and users.
To avoid this headache, ensure test systems are available to test patches before applying production systems to gauge performance.
Bypassing Change Management
Similar to the need for good communication is the need for proper change management.
Whereas having general good communication across all parts of the business is necessary for an even flow of operations, change management is critical to remediation efforts.
Failure to notify teams, data owners, or stakeholders of remediation can lead to distrust and system failure.
To ensure backout plans are in place in case remediation effort fails, having change management to communicate improves overall productivity and helps to reduce any security gaps.
Data Overload
Improperly tuned vulnerability tools generate large amounts of data. It can be overwhelming! That’s why these tools should be tuned to detect confirmed vulnerabilities.
The last thing you want is to create more work for your team, having to sift through irrelevant data and vulnerabilities presenting a very low risk to the organization.
This is also true for reporting, where leadership and stakeholders will want to see a precise view of remediation outcomes.
To drown out the noise, target and prioritize scans on your highest-risk systems.
Lack Of Centralized Asset Management
Your asset inventory should be tightly integrated with your vulnerability tool in order to properly identify systems and understand the scope of your programs.
Having access to an asset manager throughout each step of the vulnerability remediation process is important because it will help you to:
- Understand and find the vulnerabilities most impactful to your organization.
- Prioritize those vulnerabilities based on the assets in your inventory.
- Fix the weak points in those systems.
- Keep track and monitor their progress.
Wrapping Up
A vulnerability remediation plan can help uplift your organization by clearly defining the path to eliminate weaknesses in your system.
To reach this goal, there are several critical steps you need to take in order to gain the right tools, team, compliance, controls, reporting and so much more. Having a plan matters.
This article has defined vulnerability remediation and delivered a number of best practices and common pitfalls that can be used to help form your own successful plan.
Now that you are equipped with what you need to know about vulnerability remediation, you can provide greater benefit to your organization by increasing its security posture.
Article by