What Is Vulnerability Prioritization?
(& How To Do It Effectively)
Learn about PurpleSec’s fully managed vulnerability management services.
Author: Jason Firch, MBA / Last Updated: 03/24/2023
Reviewed By: Josh Allen & Michael Swanagan, CISSP, CISA, CISM
View Our: Editorial Process
Table Of Contents
You can prioritize vulnerabilities by identifying and assessing them based on factors like severity, exploitability, and potential impact, considering the organization’s unique context and goals. Then, develop a risk-based remediation plan focusing on high-risk vulnerabilities while continuously monitoring and retesting to ensure effective vulnerability management.
What You’ll Learn
- Understand the concept of vulnerability prioritization and its importance in cyber security.
- How to consider factors like severity, exploitability, impact, and business context in prioritization.
- How to adapt prioritization techniques to align with organizational goals and risk tolerance.
- Insight into the process of identifying, categorizing, and remediating vulnerabilities effectively.
- How AI and ML is enhancing risk-based automation tools for improved vulnerability management.
- How PurpleSec is improving the vulnerability management process.
What Is Vulnerability Prioritization?
Vulnerability prioritization is the process of identifying and ranking vulnerabilities based on their potential impact, exploitability, and other contextual factors such as asset Information, severity, exploitability, impact, and threat Intelligence.
The goal of vulnerability prioritization is to ensure that high-risk vulnerabilities are addressed first, while lower-risk vulnerabilities are addressed later.
Effective vulnerability prioritization requires a comprehensive understanding of the vulnerabilities present in an organization’s systems and applications.
This involves identifying and assessing vulnerabilities based on their:
- Severity
- Exploitability
- Potential impact
It also involves considering contextual factors such as asset information, threat intelligence, and business requirements.
The prioritization process involves ranking vulnerabilities based on their risk level and assigning resources based on the level of risk.
This ensures that vulnerabilities that carry the most business impact and risk are remediated first.
Importance Of Vulnerability Prioritization
Prioritizing vulnerabilities is crucial in managing a large number of vulnerabilities.
Without prioritization, organizations may waste resources addressing lower-risk vulnerabilities while higher-risk vulnerabilities remain unaddressed.
Vulnerability prioritization provides a systematic approach to managing vulnerabilities based on:
- The organization’s goals
- Business context
- Risk appetite
It enables organizations to protect sensitive data and critical systems, efficiently allocate resources to address threats, and minimize the attack surface.
Contextual Information In Vulnerability Prioritization
- Asset Information
- Severity
- Exploitability
- Impact
- Threat Intelligence
Asset Information
Understanding the importance of assets within an organization will help you to determine the potential impact of a vulnerability and help organizations prioritize remediation efforts accordingly.
These factors include:
- Asset owners: Who is responsible for the asset?
- Asset function: What role does the asset play within the organization?
- Asset value: What is the financial or operational worth of the asset?
Severity
The severity of a vulnerability reflects its potential impact on the system or application.
It is usually measured using the Common Vulnerability Scoring System (CVSS), which provides a standardized way to assess and rate the severity of vulnerabilities.
CVSS scores range from 0 to 10, with higher scores indicating a higher severity level.
Keep in mind that CVSS scores should be just one aspect of your vulnerability prioritization process. Low-rated vulnerabilities can often be chained together to compromise a network or application.
While they provide a useful starting point, other factors also play a role in determining the overall risk associated with a vulnerability.
Exploitability
Exploitability refers to the likelihood that a vulnerability will be exploited by an attacker.
This can depend on factors such as the availability of exploit code, the skills and resources required to exploit the vulnerability, and the potential rewards for the attacker.
When prioritizing vulnerabilities, consider how likely it is that an attacker would exploit them.
Vulnerabilities with known exploits or those that are easy to exploit should be prioritized higher, as they pose a greater risk to your organization.
Impact
The impact of a vulnerability refers to the potential damage that could be caused if it were exploited.
This might include data loss, system downtime, reputational damage, or financial loss.
The impact of a vulnerability can vary depending on the specific systems and data affected, as well as the organization’s overall security posture.
To properly prioritize vulnerabilities, evaluate the potential impact of each one on your organization.
This can help you focus on addressing the vulnerabilities that could cause the most damage if exploited.
Threat Intelligence
Incorporating threat intelligence into vulnerability prioritization allows organizations to identify vulnerabilities that are actively being exploited in the wild.
This information can help businesses focus their efforts on vulnerabilities that pose an immediate threat, ensuring resources are allocated effectively to address the most pressing risks.
Business Context
The business context of a vulnerability refers to how it might affect the organization’s objectives and regulatory compliance requirements.
This includes considering factors such as the importance of the affected systems or data to the business, the potential for regulatory fines or penalties, and the potential impact on customer trust.
When prioritizing vulnerabilities, it’s essential to understand their potential impact on your organization’s business goals and compliance requirements.
By doing so, you can ensure that your vulnerability prioritization process aligns with your organization’s overall risk management strategy.
Balancing Key Factors For Effective Vulnerability Prioritization
To effectively prioritize security risks, it’s important to strike a balance between these key factors.
Relying too heavily on one factor (e.g., CVSS scores) can lead to an incomplete view of the risk associated with a vulnerability.
Instead, consider all these factors together to develop a comprehensive understanding of the risk landscape and prioritize vulnerabilities accordingly.
You’ll be better equipped to allocate resources effectively to focus on the most mission critical vulnerabilities.
Adapting Prioritization Techniques
Every organization has its priorities, goals, and risk tolerance levels.
As a result, vulnerability prioritization techniques must be tailored to meet these unique requirements.
To adapt prioritization techniques, consider the following steps:
- Identify organizational goals and risk tolerance: Understand the organization’s objectives and its appetite for risk. This will serve as a foundation for developing a prioritization strategy that balances security efforts with business needs.
- Assess the importance of assets: Determine the criticality of different assets within the organization, such as data, applications, and infrastructure. This assessment should take into account factors such as asset value, asset function, and the potential impact of a breach on the organization’s operations.
- Incorporate contextual information: Leverage information such as CVSS scores, threat intelligence, and regulatory compliance requirements to better understand the risk landscape and prioritize vulnerabilities accordingly.
- Develop a risk-based remediation plan: Create a plan that focuses on addressing high-risk vulnerabilities first, while also considering the organization’s unique requirements and goals.
Examples Of Adapting Prioritization Techniques
Healthcare Organization
A healthcare organization must protect sensitive patient data, ensure the availability of medical systems, and meet regulatory compliance requirements (e.g., HIPAA).
Learn More: How To Perform A HIPAA Risk Assessment
In this case, the organization should focus on:
- Prioritizing vulnerabilities affecting systems that store, process, or transmit patient data, as a breach of this data can have severe consequences for patients and the organization.
- Addressing vulnerabilities that could disrupt the availability of critical medical systems, as downtime in these systems can directly impact patient care.
- Ensuring compliance with HIPAA and other relevant regulations by prioritizing vulnerabilities that could lead to non-compliance and potential fines.
By adapting its prioritization techniques to align with these specific goals and requirements, the healthcare organization can better protect its sensitive data, maintain the availability of critical systems, and meet regulatory requirements.
Financial Organization
A financial organization will place a high priority on protecting sensitive financial data, ensuring the integrity and availability of transaction processing systems, and meeting regulatory compliance requirements (e.g., PCI DSS, SOX).
For this industry prioritization should focus on:
- Prioritizing vulnerabilities affecting systems handling sensitive financial data.
- Addressing vulnerabilities that could disrupt the integrity and availability of transaction processing systems.
How To Prioritize Vulnerabilities
To prioritize vulnerabilities effectively, organizations should follow a risk-based approach that takes into account the severity of the vulnerability, exploitability, impact, and business context.
Step 1: Identify Vulnerabilities
First, let’s find the vulnerabilities in your system or application.
Use a mix of tools to spot issues in your codebase, third-party libraries, or APIs. For web apps, tools like static code analysis and web application scanners are great.
For network vulnerabilities, consider using network vulnerability scanners and intrusion detection systems.
These tools can help you find problems like input validation, authentication, and authorization.
They can also detect coding errors that may cause vulnerabilities, such as buffer overflows and integer overflows.
Related Articles:
Step 2: Categorize & Prioritize Vulnerabilities

Once you’ve identified vulnerabilities in your application, the next step is to categorize and rank them.
You can use a standardized scoring system, such as a CVSS to rank vulnerabilities based on their severity.
Risk-based vulnerability management is an approach that incorporates risk assessments into vulnerability management processes.
By identifying and prioritizing vulnerabilities based on risk, organizations can allocate resources more efficiently and reduce process times.
Other factors to consider when categorizing vulnerabilities include impact, exploitability, and business context.
Create a risk-based plan that considers the effort needed for fixing and the timeline for addressing vulnerabilities.
This approach lets you focus on the vulnerabilities that are the biggest threat to your organization thereby balancing security efforts with business objectives.
Step 3: Implement Fixes & Mitigations

The next step is to apply solutions and mitigations for the prioritized vulnerabilities.
Conventional wisdom will tell you to fix critical and high vulnerabilities first.
Conventional wisdom is wrong.
Instead, your assessment and remediation plan should focus on areas of the greatest business impact.
For example, two low vulnerabilities can be chained into an attack path that provides a threat actor a foothold into your network just enough to ransom your data.
For vulnerabilities that can’t be fixed right away, apply mitigations to reduce the risk.
In the case the vulnerability creates more work than is worth fixing you can choose to accept the risk for a few months or even a year.
Just be sure to set a reminder to revisit the accepted risk and reevaluate whether or not it should continue to be accepted.
Learn More: How To Automate Patch Management
Step 4: Monitor & Retest For Vulnerabilities
Lastly, always monitor and test for vulnerabilities.
For web applications, integrate security testing into your development pipeline, update third-party libraries and dependencies regularly, and carry out periodic security reviews and audits.
For network systems, use continuous monitoring tools and conduct regular vulnerability assessments.
By always keeping an eye on vulnerabilities, you can find and fix new ones before they’re exploited.
In the case of Log4j, PurpleSec was able to immediately identify and patch the vulnerability the same day it was released.
Learn More: How To Conduct A Vulnerability Assessment
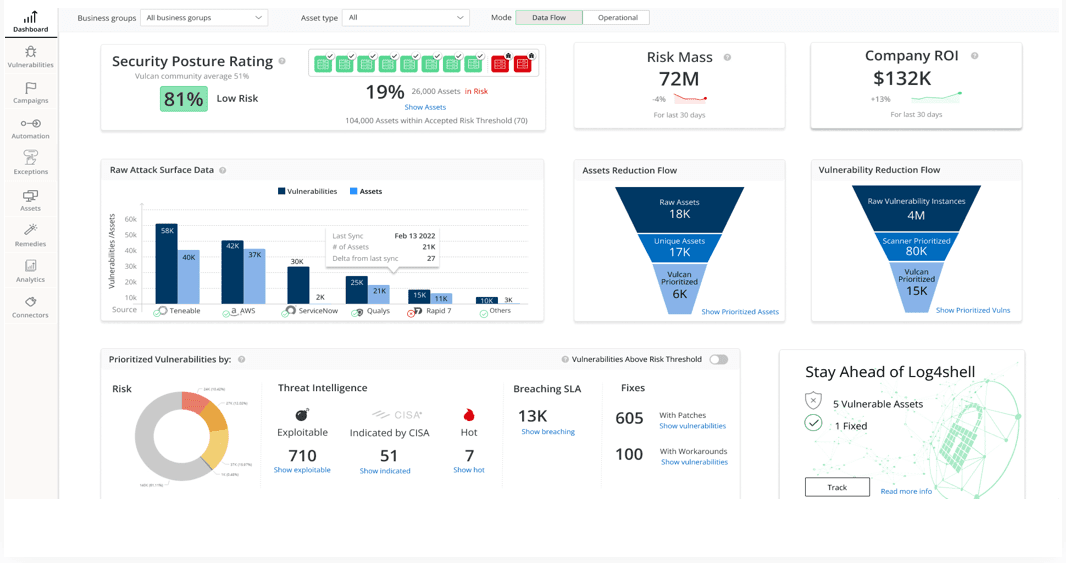
Risk-Based Automation Tools Enhanced By AI
Risk-based automation tools enable organizations to intelligently prioritize vulnerabilities based on their potential impact on the business.
AI and ML algorithms can analyze vast amounts of data, identifying patterns and correlations that might be missed by traditional vulnerability management approaches.
This enables a more accurate and efficient prioritization of vulnerabilities.
For example, AI and ML can help improve risk-based automation tools by:
- Predicting Exploitability: Analyze historical data on vulnerabilities and exploits, identifying patterns that suggest which vulnerabilities are more likely to be exploited.
- Context-Aware Prioritization: Incorporate contextual factors into vulnerability prioritization, such as the criticality of affected assets, the potential impact on the organization’s operations, and the presence of mitigating controls.
- Automating Remediation Efforts: Automate the remediation process by identifying the most effective solutions for each vulnerability and automatically applying patches or other mitigating actions when possible. This reduces the time and effort required for manual intervention and speeds up the overall vulnerability management process.
How PurpleSec Prioritizes Vulnerabilities
At PurpleSec, we provide an automated vulnerability patching solution that prioritizes vulnerabilities based on their severity and impact on your organization.
Our solution leverages cutting-edge automation and AI-powered technologies to deliver end-to-end detection and remediation, making it easy for SecOps and ITOps to coordinate from the moment a vulnerability is discovered until it’s remediated – all without uncertainty or confusion.
With our cloud-native design, organizations can get faster implementation and limitless scalability, while our single, lightweight agent provides control over all endpoints with minimal overhead and virtually no impact on the end-user.
By using PurpleSec’s automated vulnerability patching solution, organizations can significantly reduce process times, eliminate threats, and manage exposed endpoints.
Our solution provides full-spectrum resolution with remediation coverage for all vulnerability types, delivering continuous, rapid risk reduction.
Organizations can also gain a single view of their full remediation cycle, removing costly, time-consuming

Jason Firch, MBA
Jason is a proven marketing leader, veteran IT operations manager, and cyber security enthusiast with 10 years of experience. He is the co-founder and CEO/CMO of PurpleSec.
Recent Articles
Categories
Policy Templates
Most Popular