Preventing a breach of your network and its systems requires protection against a variety of cyber attacks. For each attack, the appropriate countermeasure must be deployed/used to deter it from exploiting a vulnerability or weakness.
There are many tools and solutions that can be implemented, which is why small and mid-sized businesses can get easily overwhelmed.
One of the first steps you should take is to assess and implement the appropriate security controls based on it’s impact to the business and your security goals.
$35/MO PER DEVICE
Enterprise Security Built For Small Business
Defy your attackers with Defiance XDR™, a fully managed security solution delivered in one affordable subscription plan.
Solutions For Cybersecurity
Some of the best practices and solutions to prevent cyber attacks include:
- Creating a cybersecurity strategy.
- Developing cybersecurity policies.
- Conducting a security risk assessment.
- Building a cybersecurity program.
- Hiring a virtual CISO.
- Performing vulnerability assessments.
- Building a vulnerability management program.
- Penetration testing networks and applications.
- Conducting employee phishing campaigns.
- Implementing security awareness training.
- Using multi-factor authentication.
- Create an incident response plan.
- Implement a managed XDR solution.
- Microsegmenting systems and users.
- Installing spam filters and anti-malware software.
- Deploying Next-Generation Firewalls (NGFW).
- Installing endpoint detection & response (EDR).
- Using a VPN or SD-WAN solution.
- Implementing a Virtual desktop infrastructure (VDI) solution.
- Implementing security information and event management (SIEM)
- Deploying intrusion detection & prevention software (IDS and IPS)
- Creating a data loss prevention (DLP) program
- Performing static code analysis
- Performing red and blue team exercises
- Hiring a virtual Security Operations Center (SOC)
- Investing in a Managed Detection And Response (MDR) service.
- Implementing active threat-hunting.
- Using web application firewalls (WAFs).
- Deploying a zero-trust security architecture.
- Building security automation into processes.
Implementing some, or all of these cyber attack prevention methods, will help to protect your business from the latest cyber attacks.
While this list may seem overwhelming the goal is to focus on areas of most risk. That’s why creating a strategy and working with a risk management expert to narrow down the solutions of the most value is important.
What Is A Cyber Attack?
A cyber attack is performed with malicious intent when a threat actor attempts to exploit a vulnerability or weakness in a system or individuals of an organization.
These attacks threaten to steal, alter, destroy, disable or gain access to or make use of an unauthorized asset.
Cyber attacks, threats, and vandalism are a dangerous and increasing problem for businesses. Nearly all modern-day companies require a network of computers, servers, printers, switches, access points, and routers to operate.
Businesses also deploy software tools to streamline functions, like QuickBooks for handling bookkeeping.
Unfortunately, while these devices and applications provide a huge benefit to the company, they also represent a risk.
All it takes is one employee to click on a malicious link that then gains access to your network and infects your systems.
The Breach Report
PurpleSec’s security researchers provide expert analysis on the latest cyber attacks.

Types Of Cyber Attacks & How To Prevent Them
The different types of cyber attacks are:
- Network attacks
- Wireless attacks
- Malware attacks
- Social engineering attacks
It’s important to note that no system is 100% vulnerability free or “hacker-proof”. If a threat actor has enough time, resources, and manpower to launch an attack then chances are they will find a way in.
This is especially true of advanced persistent threat groups.
Cyber attacks come in all shapes and sizes from deploying an application-specific attack against a database server to sending phishing emails with malicious attachments or URLs.
While knowing the purpose of a cyber attack can be helpful it isn’t the main priority. What takes priority is knowing how the attack occurred and how to prevent them from succeeding in the future.
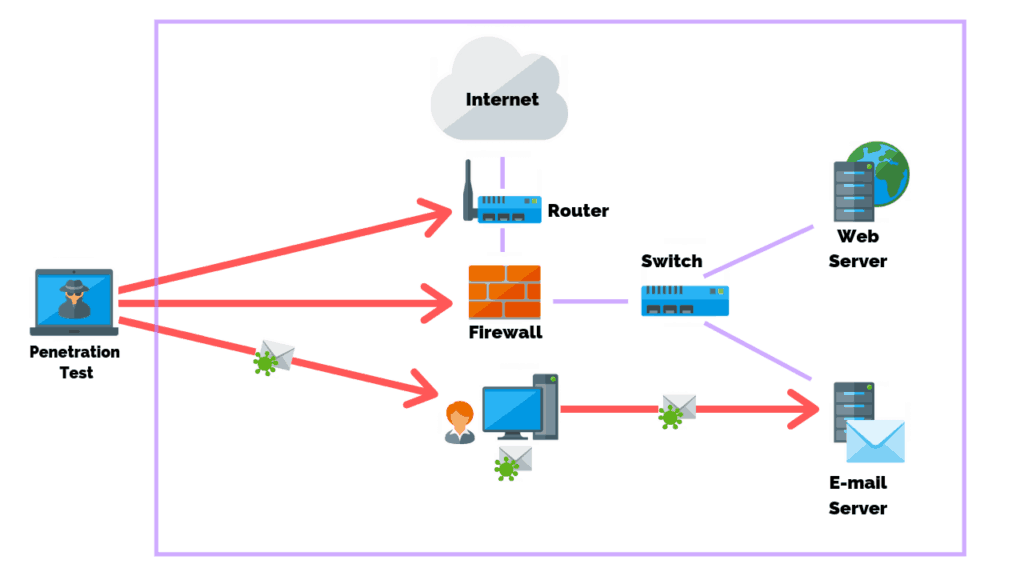
A network attack is an attempt to exploit a vulnerability or weakness in a network or its systems including servers, firewalls, computers, routers, switches, and printers.
Common network attacks include:
- Denial of Service (DoS)
- Distributed Denial of Service (DDoS)
- Buffer Overflow Attacks
- Ping Attacks
- SYN Flood
- DNS Amplification
- Back Door
- Spoofing
- Smurf Attack
- TCP/IP Hijacking
- Man In The Middle Attacks
- Replay Attacks
- DNS Poisoning
- ARP Poisoning
- Domain Kiting
- Typosquatting
- Client Side Attacks
- Watering Hole Attacks
- Zero Day Attacks
The goal of a network attack can be to steal, modify, or remove access to valuable data. Or, it could be to bring down a network.
Attacks on networks have become more common in recent years in part because small and mid-sized businesses are not making investments into securing their systems fast enough.
As a result, hackers target businesses because their systems are often easier to compromise. Other reasons include a rise in hacktivism, bring your own device (BYOD) use, and cloud-based applications.
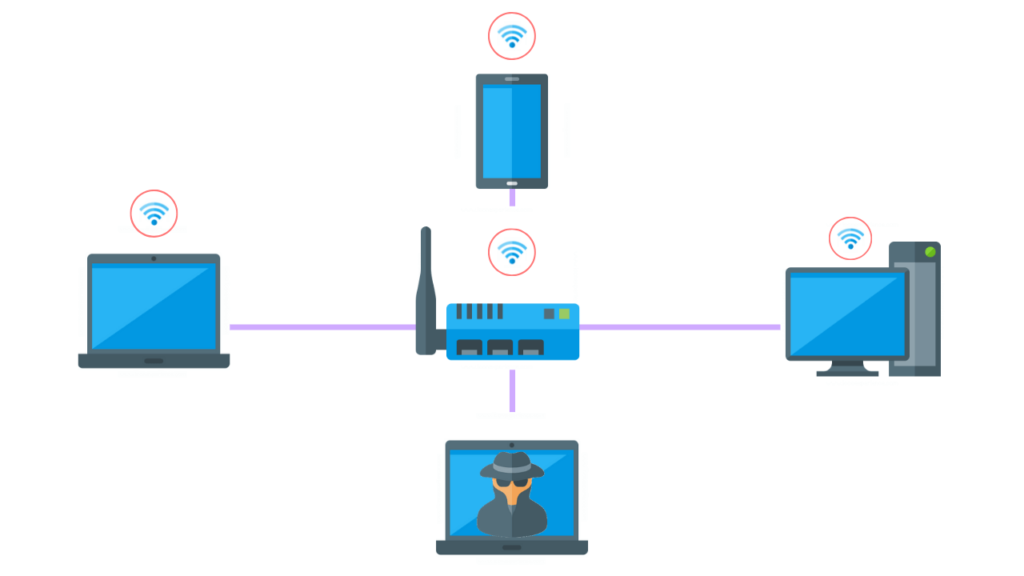
Wireless Attacks
A wireless attack involves identifying and examining the connections between all devices connected to the business’s WiFi.
Common wireless attacks include:
- Explore All Wireless Attacks
- Data Emanation
- Jamming
- Bluetooth Vulnerabilities
- Near-Field Communication
- War Driving
- Evil Twin
- Deauthentication and Disassociation
- War Chalking
- Packet Sniffing and Eavesdropping
- Replay Attacks (Wireless)
- WPS Attacks
- WEP/WPA Attacks
- IV Attack
- TKIP Attack
- WPA2 Attacks
Due to the nature of WiFi and its methods for providing network access, malicious hackers often choose to penetrate a company by compromising its WiFi network and corresponding infrastructure devices.
Homes are also at risk, especially due to the rise of IoT-connected devices and appliances.
Malware & Ransomware Attacks
Malware, or malicious software, is any piece of software that was written with the intent of harming data, devices, or people.
Learn More: How To Prevent Malware Attacks
Systems infected with malware will present with symptoms such as running slower, sending emails without user action, randomly rebooting, or starting unknown processes.
There are thousands of malware variants and different types of malware including:
- Viruses
- Keyloggers
- Worms
- Trojans
- Ransomware / Crypto-Malware
- Logic Bombs
- Bots/Botnets
- Adware & Spyware
- Rootkits
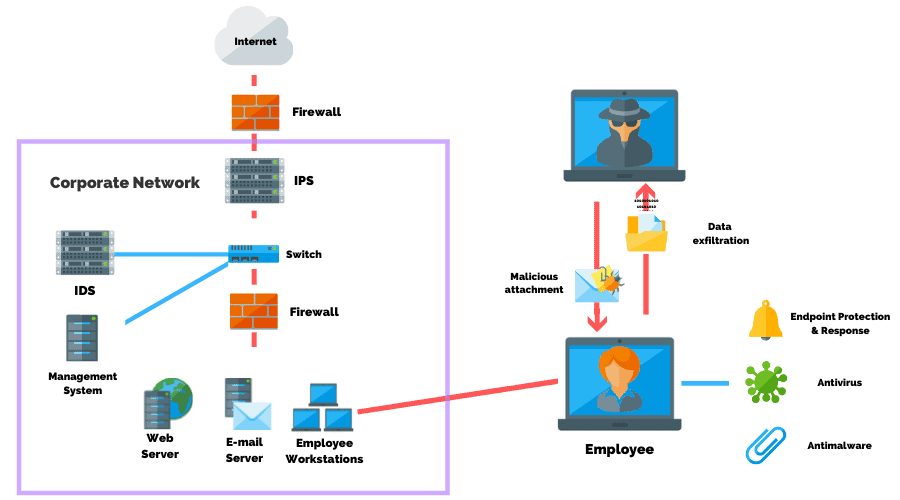
Social Engineering Attacks
Social engineering is the attempt to manipulate a user into giving up sensitive information such as user account credentials, wiring funds, or personal customer information.
Learn More: How To Prevent Social Engineering Attacks
This form of cyber attack is one of the most popular for deploying malicious code on to a network. According to recent data, 98% of cyber attacks rely on social engineering.
Most are familiar with email phishing and whaling techniques as it has become an essential component of any cybersecurity program and is often bundled into other IT solutions.
Common types of social engineering attacks include:
- Email Phishing
- Vishing
- Smishing
- Watering Hole Attacks
- Pretexting
- Whaling
- Tailgating
Article by