Previous
How To Implement Social Engineering Awareness Training
Reduce your attack surface with PurpleSec’s social engineering services.
Author: Michael Swanagan, CISSP, CISA, CISM / Last Updated: 10/23/22
Reviewed By: Seth Kimmel, OSCP & Jason Firch, MBA
View Our: Editorial Process
Table Of Contents
You can implement security awareness training by developing policies, defining resources and toolsets, creating phishing campaigns, reporting on findings, and following up with online or in-person training.
What You’ll Learn
- What security awareness training is and why it’s important.
- Why social engineering continues to be the #1 cyber threat.
- Actionable steps you can take to build a security awareness program for your organization.
- How you can report on findings and gain buy-in from senior leadership.
Chances are at some point in time you’ve seen an email from HR asking you to complete security awareness training.
That’s because social engineering has quickly become standard practice for security and IT professionals as they seek to harden security controls.
Establishing a security awareness training program is one of these controls.
In this article, I’m going to show you how to build and implement a security awareness program for your organization step-by-step.
We’ll discuss what security awareness is, why it’s important, how to measure the success of your program, and what actions you need to take to remediate vulnerabilities.
What Is Security Awareness?
Security awareness is the knowledge and understanding members of an organization possess regarding the protection of corporate assets and information.
Security awareness also promotes a heightened level of attention to the subtle activities performed by a threat actor, who has the objective of illegally obtaining your data or to damage your corporate resources.
What Is Security Awareness Training?
Security awareness training is a formal process that seeks to educate its members about security practices as outlined in the organization’s corporate policies and procedures.
The goal of security awareness training is to help the employee recognize threats and to provide guidance on how to respond appropriately when presented with a situation that may compromise the security of your organization.
Why Is Security Awareness Training Important?
Security awareness training is a critical component of a comprehensive information security program. The shortest and simplest reason why this training is important is that social engineering works.
Failure to implement a security awareness program for your organization may lead to negative consequences or unwanted public exposure.
We oftentimes hear reports of publicized data breaches of large organizations.
When a data breach is made public, this typically means that a large amount of sensitive data was leaked outside of the network, and the organization is legally required to make it public.
Read More: 9 Data Security StrategiesYou Need To Implement In 2023
This negative exposure may result in the potential loss of revenue and damages the reputation of the business, which may take years to earn back the trust of its consumers or business partners.
Social Engineering Is The #1 Cyber Threat
Recent statistics reveal that social engineering is one of the primary techniques threat actors use to infiltrate an organization.
This means that no matter how well your organization invests in technology to protect the perimeter of the network, in most cases, the weakest link in most cases is the human element, the person behind the keyboard and phone.
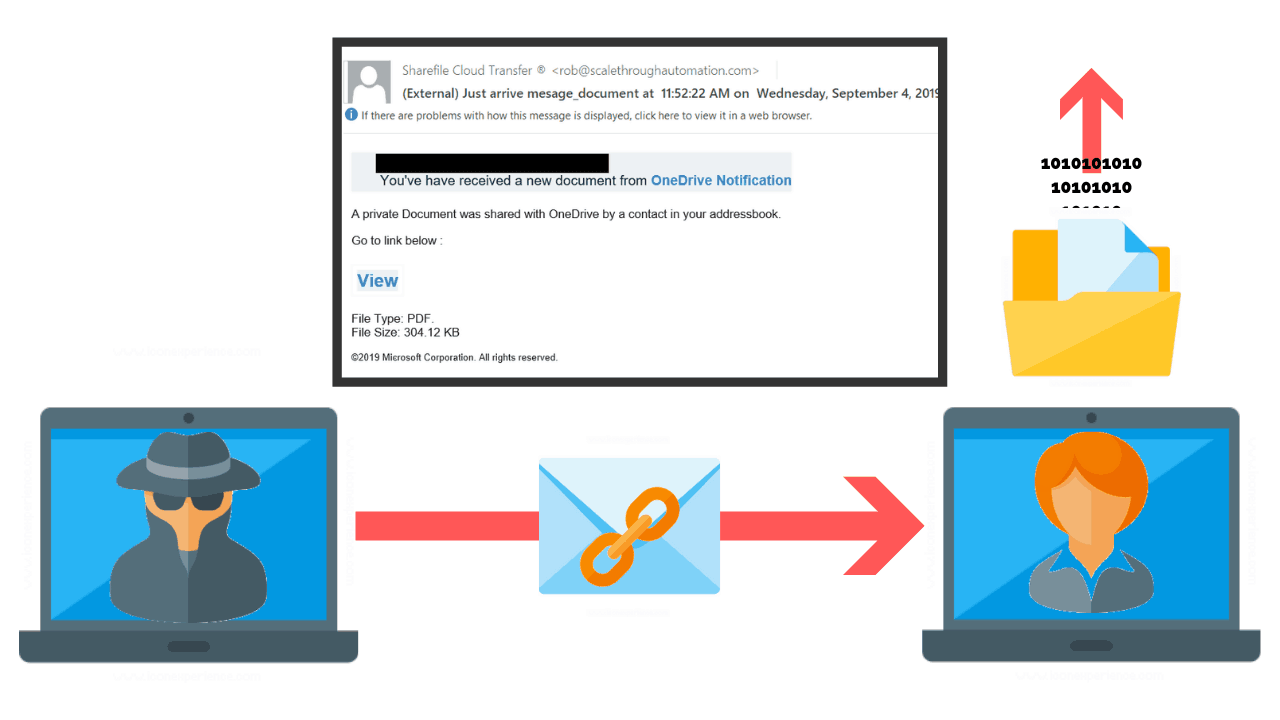
Referring to end users as the weakest link is not to minimize their value in the organization, but to shed light on the critical role each employee has in protecting the organization.
All employees regardless of their role in your organization require routine training that focuses on recognizing the various social engineering schemes used by threat actors today.
The recent security trends also emphasize the importance of security awareness and why it should be viewed as an essential component of the overall security program of your organization.
This program can help reduce the risk of unwanted public exposure resulting from data breaches caused by phishing attacks.
How To Build A Security Awareness Program
Now that we have established the need for a Security Awareness Program for your organization, how do you build it? Where should we start?
There are 5 main steps to implementing a security awareness program including:
Step 1: Implement A Social Engineering Awareness Policy
Without proper awareness of how to identify a social engineering attack, the employees of an organization will be susceptible and may be the next victim.
To reduce the risk of employees falling for social engineering attacks, the organization should have a written document in place which provides directions.
This written set of instructions is your Social Engineering Awareness Policy.
A well-defined policy will typically contain the following:
- Purpose – Sets the tone of the policy, includes the goals of why the policy is created and its purpose.
- Scope – Defines the intended audience and identifies what resources the policy applies to.
- Policy – Provides the basic objectives of the organization and a description of the general guiding principles or rules.
- Accountability – Describes the specific responsibilities of all employees as it related to information assurance.
- Contacts – Information on who to contact in case of an incident or general question regarding the policy content.
- References – Included in case the policy statement(s) references an existing policy or supplemental information.
- Version History – Informs the reader that they are viewing current and relevant information.
Step 2: Define Resource & Toolset Requirements
Once you have a clearly defined security awareness policy in place, the next step is to enforce the policy.
Now that does not mean demanding each user to recite the policy verbatim and punish them if they misquote. Policy enforcement are the activities that reinforce the policy statements.
The tools used to implement and enforce the plan should be engaging and interactive.
The tool should demonstrate real workplace situations and challenge the employee to decide based on several options.
The tool should also congratulate the employee for making the right decision and will provide guidance on an incorrect choice that may impact the entire organization.
Remember, a hacker only needs one person to make a mistake in judgement.
A few of the well-known security awareness tools are listed in the Forrester 2020 Security Awareness and Training Solutions report below.
I would suggest clicking through a few of them to get an idea of the features.
Try to determine which resource is a good fit for your organization if you do not currently have one in place today.
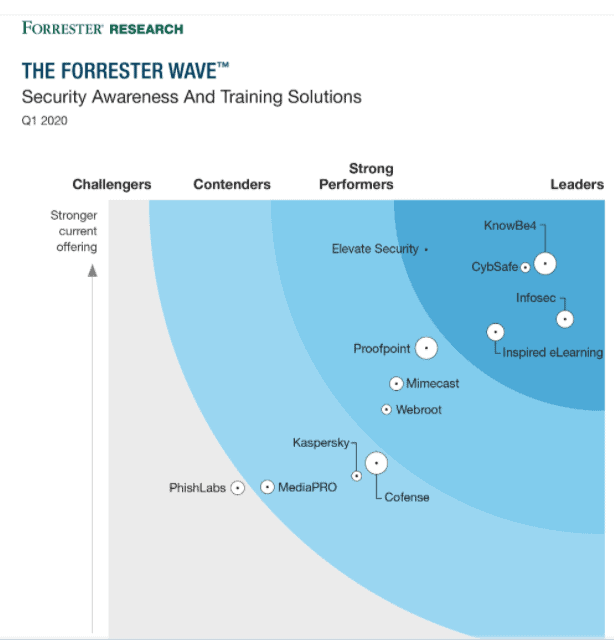
The leaders in the space last year were:
If your organization is in the market for a new product, I would recommend conducting a proof of concept on a few of the tools listed to determine if they align with your organization’s requirements and provides the interactive capabilities to influence your organization members to always make the right decision.
Now that you have developed your Social Engineering Awareness Policy, and a hopefully a tool of choice, it is now time to create a plan of action to test user responses.
Step 3: Create A Phishing Campaign
Phishing campaigns are designed to help you customize and manage simulated phishing emails.
When you are ready to create a phishing campaign, you have the option to select which group(s) to target, which type of email template to use, and the frequency of the testing.
In most cases, only a select few of individuals are aware of the phishing campaign.
It would be difficult to ascertain user behavior if the campaign is announced to all employees, therefore, a small group with knowledge of the campaign is typical.
One of the groups that have knowledge of the campaigns is senior leadership.
Senior leadership should be aware of the campaign and authorize the test.
The compliance team may oversee the management of the tool and work with the product vendor to create the email template and reporting.
Build Templates & Scenarios Email templates
If your organization is building a secure awareness for the first time, I recommend that you work directly with the vendor to assist in designing your phishing campaign template.
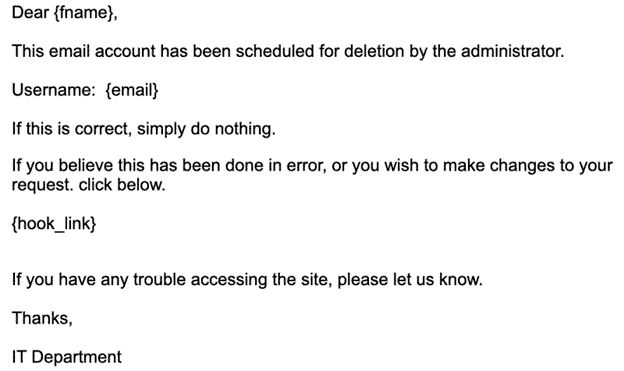
The basic template example below illustrates the fields and options used to create the content of the phish message.
General Campaign VS Spear Phishing
The targets for the phishing email exercise are controlled by the administrators of the tool.
Senior leadership should have input as to which group(s) should receive the test or configure the tool to target a specific user or group, such as the Finance team.
This form of attack is also known as spear phishing, a highly effective technique hackers use to trick victims into clicking on malicious links.
Vishing Campaign
A vishing campaign tests how the employers react to a phone call by a malicious actor. A social engineer may pose as someone having authority outside, or within the organization, such as an IT manager. The unsuspecting employee may be lured into giving out sensitive information to the caller.
Smishing Campaign
The word Smishing comes from the combination of phishing and SMS or text messaging.
Instead of a fraudulent e-mail, the attacker sends a text message containing malicious links.
This is effective because the average person may pay less attention to what they receive on their device, since the links are not easily discerned as malicious.
Stakeholder Approval
As noted previously in Step 3, prior to activating the templates into production, ensure that Senior Leadership approves the details of the campaign, such as, when it starts, individuals or specific involved, and the duration of the test.
The most highly anticipated aspect of the campaign are the test results.
How did the end users respond, who clicked the malicious link, who gave up their password? How is this information reported? Step 4 will provide the details.
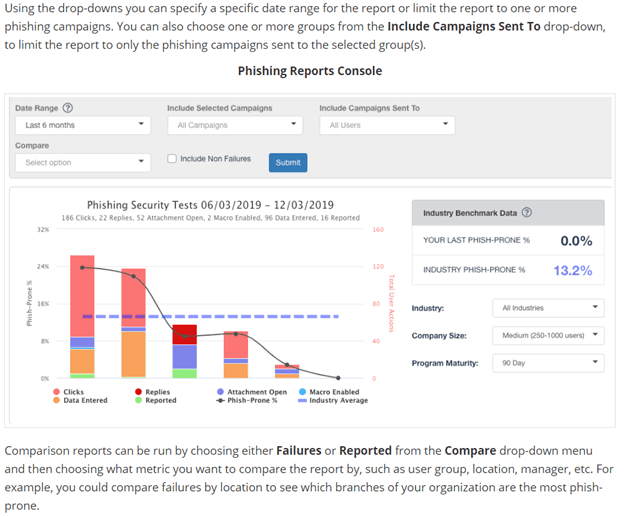
Step 4: Report Findings
The report delivered to Senior Leadership depends on the tool of choice.
Each product has its unique reporting methods; however, they generally log user behavior in an easy-to-read executive report, or they may provide your team with access to the reporting console to create your own reports.
Step 5: Security Awareness Training
Another key component to the Security Awareness Program is to implement security awareness training.
Like a phishing campaign, the primary goal of security awareness is for the end-user to recognize vulnerabilities or threat scenarios and respond to them appropriately.
Security awareness training can be implemented in various forms. One organization may utilize flyers or post boards placed in high traffic areas for employees to regularly view.
Note the two sample posters below. The language of each bullet item is simple and concise.
Posters are good security awareness tools since they are portable. If a poster is strategically posted in a high traffic area, it can provide daily reminders for all employees to be security aware.

Another effective method to establish security awareness is to provide training videos.
Videos are simple in content, with real life scenarios that informs the end user of basic security practices.
At the conclusion of the training module, there may be test your knowledge with question and answers, allowing the end user to retake the test until all questions are answered correctly.
If you are looking for a presentation, choose one that fits your business culture. Animation type videos may fit an organization with a young culture, whereas a seasoned employee base appeals to a presentation that has human actors.
Regardless of which type of presentation is used, it should be fun, engaging, memorable, and challenges the end user to think critically and understand the correct response for the scenario presented.
Sample Security Awareness Videos
There are a ton of videos available for security awareness on the web, particularly YouTube.
Your organization may opt to use a formalized presentation for security awareness.
The primary objective of the video is to influence the end-user to have the right attitude towards security and make the right decision.
Security awareness videos are great resources to include in your annual security awareness program
Wrapping Up
In this article, we addressed the key components of a successful security awareness program.
The most important asset in your organization is not the investment in the latest and greatest hardware appliance or security tool, it is the employees.
A well-trained employee who can quickly identify and respond properly to a security threat is a critical ally within your Information Security program.
By following the steps listed in this article, all employees will have a share in the ongoing support and continuous success of your security awareness program.

Michael Swanagan, CISSP, CISA, CISM
Michael is an IT security expert with 15 years of proven experience. He has experience leading and supporting security projects and initiatives in the healthcare, finance, and advertising industry.