There are 9 strategies and best practices to follow when implementing a data security strategy including:
- Identifying data security risks.
- Conducting an asset inventory.
- Implementing a data security policy.
- Mobile data security.
- Securing your database.
- Securing data in the cloud.
- Tracking user behavior.
- Respecting data privacy.
- Enforcing and maintaining least privilege.
Free Security Policy Templates
Get a step ahead of your cybersecurity goals with our comprehensive templates.

Data is integral to every aspect of life. It allows us to analyze financial trends, informs us on our health, it even helps to suggest new purchases we didn’t know we needed.
As one of the core assets used by businesses today, data helps to make informed decisions and generate continuous streams of revenue…making its security a top priority.
Securing data is and can be a significant challenge for enterprise and SMB organizations alike. In this article, I’ll explain what data security is and why it’s important.
Next, I’ll highlight the steps necessary for an organization should take to reduce its risk. Lastly, I’ll provide actionable tips on what you can do to secure your data.
Why Is Data Security Important?
In the wrong hands, lack of a good data security framework can lead to data loss or data leakage, which can l lead to negative consequences for the business.
An organization can be extorted for large sums of money by a threat actor, unintentional error can be made by an employee, or an attack from a disgruntled employee can compromise the business.
An organization’s reputation can also be damaged, either from the content exposed in the data leakage or data loss itself or by the negative public image earned from the security failure.
Either scenario has the potential to impact the business standing in the eyes of customers, vendors, stakeholders, and possibly government regulators, depending on the type of data that was leaked.
Data Security Strategies To Implement In 2024
For an organization to be properly secure it must have a clear roadmap on how it will achieve its security goals. The purpose of this section is to introduce the top strategic components that will aid in the build out of a mature data security program.
Following these best practices will help enable an organization to be more aware, hardened, compliant, and proactive about data security.
Once data is secured, it can then be tracked and monitored for assurance. Awareness and training programs can also follow at this point.
Regardless of where an organization proceeds, executing these key strategies will help the organization reduce the risk of data loss and improve its data security program.
1. Identify Data Security Risks
A security risk assessment is performed for organizations to assess, identify, and modify their overall security posture. A complete assessment brings any and all security gaps to light.

In doing so, management can determine the next steps to remediate the weaknesses, often requiring greater resources such as funding, new tools, or more personnel.
With a detailed assessment in hand, it can be used to justify these improvements to organization stakeholders for support. An organization can conduct a data risk assessment in-house, using their own teams and resources, or pay for a service that specializes in risk assessments.
If a data risk assessment is conducted by a third party, there are many legal steps involved to make sure the access and handling of data is protected. To begin a risk assessment, an organization needs to identify all valuable data assets to test their security risk.
Once all testing and evaluation is complete, the best way to deliver an assessment is in a report format.
Technical aspects can be included in either appendixes or supplied as a supplemental document, but the goal is to have a readable source that can be easily referenced and understood by all parties.
2. Conduct An Asset Inventory
 An asset inventory for data security is the identification of your most valuable assets in order to determine an associated level of risk.
An asset inventory for data security is the identification of your most valuable assets in order to determine an associated level of risk.
A proper inventory is accomplished by first understanding the various classifications your organization has placed on its data.
After determining classifications, you can begin to map your assets to organize their structure and flow.
Once you have a full view of all assets you can then look to what potential threats exist in the context of your organization’s own data.
By classifying, mapping, and identifying the threat landscape you can prioritize risks and act on reducing your business’s attack surface.
3. Implement A Data Security Policy
An effective aspect of a good data strategy is for an organization to develop its data security policy. This helps set controls, expectations, and enforcement of the human element in securing data.
Without policies, users would have no direction or understanding of how to properly collect, leverage, or share data.
Some common policies that can be implemented to protect your data include:
- Workstation security.
- Acceptable use.
- Remote access.
- Bring your own device (BYOD).
Having a policy that is laid out clearly and accessible for everyone will allow for a more consistent data security.
4. Mobile Data Security
 With technology becoming increasingly more mobile, our data is constantly moving in and out of new environments.
With technology becoming increasingly more mobile, our data is constantly moving in and out of new environments.
This of course opens many potential risks. Mobile data security, whether it be a smartphone or tablet, involves securing the data located on or accessed from a mobile device.
Without a security process in place, a device that is stolen, damaged, or lost can become at risk of compromising corporate data by potentially infecting an organization’s wider network.
Setting proper access controls such as multi-factor authentication (MFA), avoiding untrusted and public WiFi networks, and centralizing native device and operating software (OS) security tools are some of the easiest and most effective ways of implementing mobile data security.
5. Secure Your Database
 Database security requires the necessary tools, controls, and measures to properly maintain a database’s overall integrity.
Database security requires the necessary tools, controls, and measures to properly maintain a database’s overall integrity.
Attempted unauthorized access, purging, downloading, and sharing of data are potential risks of an unsecured database.
There are several considerations in determining a database’s integrity, including:
- Its physical or virtual server.
- The database management system.
- Third-party applications.
- The network infrastructure in which the database is accessed.
- The data itself.
Compromised databases can result in data breaches, intellectual property theft, or fines and penalties for non-compliance.
The best way to secure your database is to set basic administrative (backend) network access controls, always update database software to its latest version, encrypt the stored data, apply multi-factor authentication (MFA) for user access, back up and segment all data, and routinely audit.
These procedures are integral to strengthening your database security.
6. Data Security In The Cloud
![]() Data that’s located in the cloud is a particular area of security based on the data’s location.
Data that’s located in the cloud is a particular area of security based on the data’s location.
By its very nature, the cloud is designed to incorporate a wider network and range of accessibility.
Related Article: Best Practices For Cloud Vulnerability Management
Data can be accessed in virtually any location, which allows for greater efficiency and productivity. But from a security perspective, these qualities open a unique set of entry points and attack vectors.
There are a couple of key stakeholders when it comes to the responsibility of protecting data in the cloud; private and public cloud.
The first is private cloud, where the enterprise organization is entirely responsible for maintaining their own data centers.
Second is the public cloud, in which cloud vendors like Microsoft Azure or Amazon Web Services (AWS) own and operate the infrastructure and the enterprise organization is responsible for areas such as the virtual network, applications, and the data.
Implementing access control policies, devising encryption solutions, providing regular employee training, and securing endpoints are some of the best ways to begin securing data in the cloud from unauthorized access.
Compliance, monitoring, and auditing are added steps to make sure your security measures are effective or need the necessary improvements.
7. Track User Behavior
Tracking and analyzing user behavior is a form of security that recognizes individuals’ approaches to how data on a network is leveraged.
This could be to satisfy compliance factors, abuse done by public users, or even to determine the potential of insider threats, or malicious activity done by employees.
Having this perspective allows for data to be intelligently monitored.
A common intelligence tool that can be applied to tracking user behavior is a Security Incident and Event Management (SIEM).
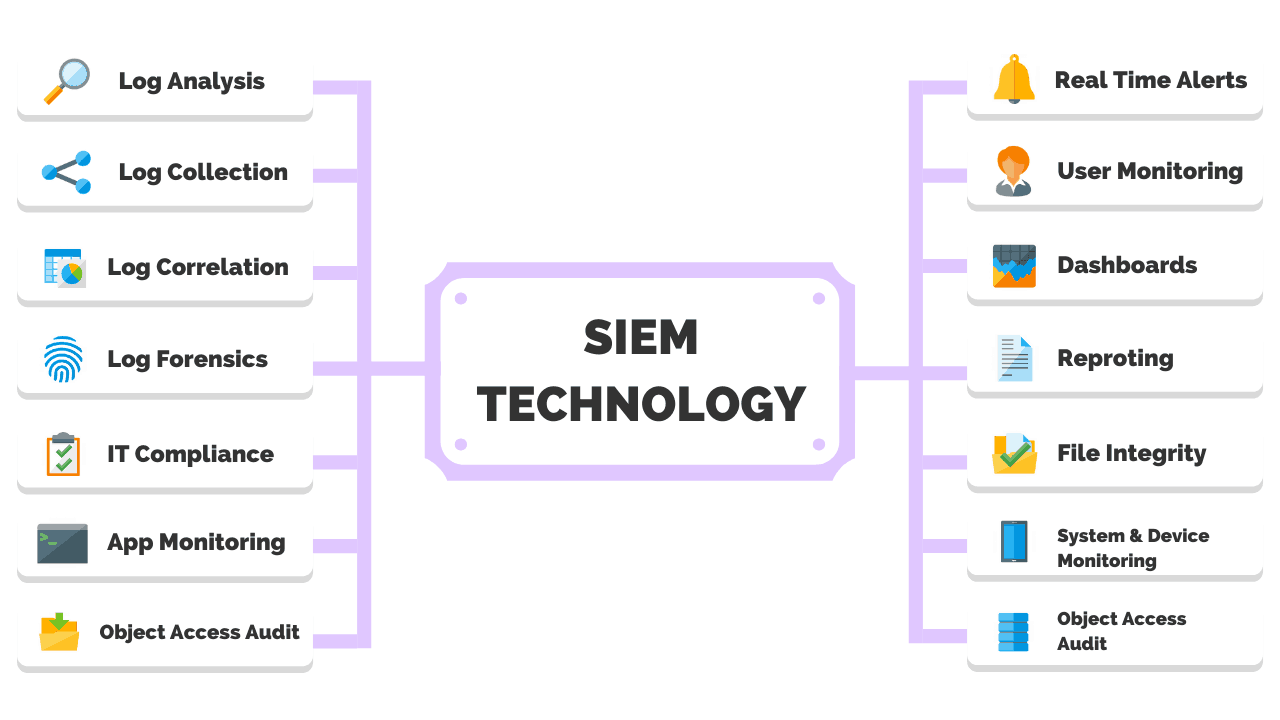
A SIEM logs behavior and analytics, providing insights used to make strategic decisions.
In addition to specific tooling, speed and adaptability are key to tracking user behavior.
Creating a custom-built architect to instantly answer relevant queries is an important function for timely results.
Having analytics scalable for any team to leverage as needed is also a desirable feature.
8. Respect Data Privacy
Respecting data privacy is not only an ethical consideration for an organization to adhere to but a legal and financial one.
With the massive amounts of data being generated, maintained, and shared, there comes a certain level of delicateness required to preserve the privacy of users.
Failing to ensure privacy could mean failing to comply to laws and regulations, which puts an organization at risk of penalties, lawsuits, and even breaches.
Developing a policy is the first step in respecting data privacy.
Having a policy as a framework, controls can be securely put in place to make sure access and usage are properly aligned with an organization’s operational structure.
Finally, ongoing security awareness training is important to keep employees up to date and knowledgeable on the need for handling private data with care and within organization policy.
9. Enforce And Maintain Least-Privilege
Least-privilege access is exactly what it sounds like a process in which the minimum level of access is granted to a user.
This model of “less is more” restricts users and applications from gaining administrative access to sensitive data.
Having full access granted to everyone would be a bad idea. So, only specific users can leverage data.
A user can request access, but that decision is left to administrative control and is typically based on a policy of who may or may not gain access.
This is the essential gatekeeping process that helps to track and reduce over-access, and by default, greater inherent risk.
Maintaining a clear least-privilege policy and assigning administrative governance are the first steps in creating proper enforcement.
How And Why Are Data Breaches Still Happening Today?
- Low barrier of entry for attackers – You don’t have to be a highly skilled hacker to breach an organization’s data. Most times, the capabilities required can be easily learned online and deployed without many additional resources. This is one of the primary reasons why social engineering is so effective as a point of entry to a network.
- Increased attack surfaces – While technology has become more connected to make our lives easier, it has also opened the flood gates to greater potential points of entry for attacks or data leaks.
- Reporting and response failures – Because businesses don’t want to suffer poor public relations and retain their integrity, many organizations do not publicly notify a breach to their data, which makes response and downstream remediation difficult. We can’t learn from what we don’t know.
- Geopolitical turmoil – The ongoing rivalries and tensions between countries across the globe embolden politically motivated nation-state threat actors.
- Not enough cyber security professionals – Simply put, there are far more open roles than there are cyber security professionals. This causes heavy workloads for some employees and strain on an organization to sufficiently operate its security objectives.
The growing number of new threats and attack vectors are constantly changing.
Cybercriminals are making fortunes off exploiting individuals and organizations due to a lack of knowledge or weak security practices.
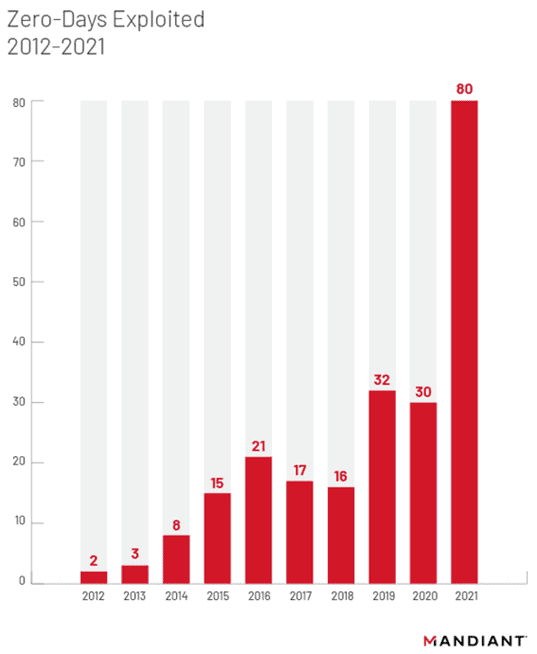
Zero-day vulnerabilities have been increasingly taking advantage of this lucrative opportunity to exploit and steal data.
The graph below shows the rise between 2012 and 2021.
Who are what is the motivation behind the uptick in the attacks over the last decade?
This is sometimes a difficult answer because threat actors and motivations vary.
Some are in it for the money, seeking financial gain from sensitive data theft or ransomware.
Others can be politically based, infiltrating an opposing party or government across ideological lines with the goal of impacting an election or economy.
Many of these attacks aren’t done by lone amateurs but are sponsored by nation-state actors, such as China, Russia, and North Korea.
Seeking to cause chaos and fear by disrupting systems and supply chains is another, more direct, motivation carried out by attackers.
As the saying goes, “An attacker has to only be right once. Everyone else has to be right every time”.
But with the attack surface being so widespread and the bar for skills required to initiate an attack so low, being right every time can seem daunting.
So, what to do?
While there are no guarantee attacks can be completely eliminated, an organization can significantly reduce risk and improve its data security without a heavy lift.
This includes strategically implementing a framework to identify risks and deploying solutions to monitor, alert, and recover data loss.
These actions go a long way in closing the door on potential attackers attempting to exploit vulnerabilities.
Wrapping Up
The world is more data driven than ever before, and new technology has allowed for greater ease of integration and distribution of data for users. This has its advantages and its concerns.
With evermore attack surfaces available for advantageous threat actors seeking to steal key assets, new laws and regulations requiring strict compliance, and privacy expectations, data security is the foundation for every security program.
This article has walked through the importance of properly securing data and how to do it.
Your organization now has the necessary information to develop and implement a strategy for a successful data security protection program.
Article by




