Social Engineering Testing Services
Go Beyond Basic Phishing To Discover Your True Risk
Our Social Engineering Testing Services
We model activities of real-world attackers by manipulating employees into giving up confidential information.
Basic Phishing
Intermediate Phishing
Advanced Phishing
Why Is Social Engineering Such A Successful Form Of Cyber Attack?
Social engineering is involved in over 98% of all cyber attacks. One answer for its growing popularity is that social engineering is easier and less expensive for threat actors.
Instead of developing or purchasing a zero day exploit threat actors simply trick a company’s employees into providing credentials. This is why social engineering attacks are so effective and a crowd favorite as it doesn’t require nearly as much effort or technical skillset to penetrate into an environment.
Ultimately, social engineering attacks work because they prey on human vulnerabilities.
Authority
People will tend to obey authority figures, even if they’re asked by those figures to perform objectionable acts.
Social Proof
People will do things they see others do and bad guys use this to their advantage.
Scarcity
Perceived scarcity will generate demand. For example, by saying offers are available for a “limited time only,” retailers encourage sales.
Consistency
If people commit to an idea or goal they are more likely to honor that commitment because it’s now congruent with self-image.
Reciprocity
People tend to return a favor, hence the pervasiveness of free samples in marketing.
Likability
People are easily persuaded by others that they like.
How Our Social Engineering Testing Services Work
End to end solution to test employee’s security awareness.
We begin every engagement understanding your company’s cybersecurity goals.
A security engineer will be assigned to assist in crafting phishing campaigns.
Carry out social engineering testing via email phishing, spear phishing, and vishing scenarios.
Recommendations are collected into an executive report including steps toward remediation.
“We partnered with PurpleSec to test various functions in our Finance department via vishing and phishing. We couldn’t be happier with the results! We were able to meet our compliance requirements while gaining a clear picture of our risk.“
– Christie N., CISO
Global Private Equity Firm
End-To-End Project Management
Get actionable results within 4 weeks of a signed contract and immediate insights on critical vulnerabilities.
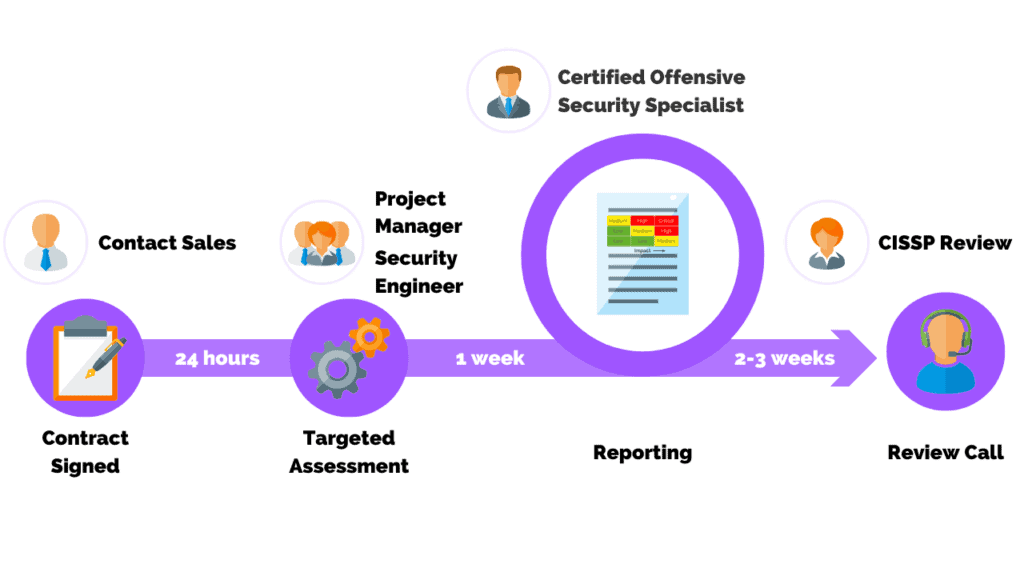
Social Engineering Testing Deliverables
Analysis and reporting delivered by an offensive security certified professional.



Basic Campaigns
The basic phishing campaign uses a pre-created phishing template modified to suit customer needs. A single email will be delivered to target users.
Intermediate Campaigns
Custom email templates and social engineering scenarios with a final report on clicks/opens of phishing emails.
Advanced Campaigns
This option will expose this risk and keep clear documentation of why each risk matters to the business’s security, brand, and bottom line. PurpleSec will utilize Credential Theft as a means of collecting employee login information.
PurpleSec will employ analysts to utilize the same techniques that malicious actors use every day. Activities here include using impostor accounts and credentials, assessment of IT and other support systems, and public information leaks.
Why Choose PurpleSec's Social Engineering Testing Services?
At PurpleSec, our offensive security experts will establish a framework to proactively identify and classify vulnerabilities.
This approach ensures that we prioritize work on the areas of greatest risk by identifying the strengths and weaknesses of your penetration testing program; thereby maximizing the ROI of your security initiatives.

What Is A Phishing Attack? (And How To Prevent Them)
What Is A Social Engineering Attack? (& How To Prevent Them)
What Is A Smishing Attack? (& How To Prevent It)
Why Is Social Engineering Effective?
Our Services Work Better Together
Ready To Get Secure?
Reach Your Security Goals With Affordable Solutions Built For Small Business




