There are 10 steps to building a cybersecurity program including:
- Conducting a security risk assessment.
- Selecting a cybersecurity framework.
- Developing a cybersecurity strategy.
- Developing a risk management plan.
- Creating security policies and procedures.
- Securing your network.
- Securing your data
- Securing your applications.
- Testing your security posture.
- Evaluating/improving program effectiveness.
Free Security Policy Templates
Get a step ahead of your cybersecurity goals with our comprehensive templates.

Small businesses looking to grow may overlook the importance of cybersecurity in their day-to-day operations, and even if they do recognize its importance they can be quickly overwhelmed with the complex task of managing a cyber security program.
Digital transformation increases the complexity of business operations and requires specialized knowledge, skills, and resources that an SMB might rather spend on growth, but the risks associated with ignoring cyber security are high.
To mitigate the risk of a cyber attack, organizations including start-ups and SMBs need to get proactive concerning developing a cyber security program, create cyber awareness in their workforce, and establish effective IT security policies and controls to protect themselves.
What Is A Cybersecurity Program?
A cybersecurity program is a set of activities, security policies, and security controls that are designed to prevent a successful cyber attack against an organization and recover from it quickly and completely.
The most fundamental way to define the technical goals of a cyber program is that it should provide Confidentiality, Integrity, and Availability (CIA) assurances for the systems and data that comprise an organization’s IT assets.
The specific details of a cyber security program depend on each organization’s unique business operations, technology environment, and risks.
Many reputable industry standards and advisories such as NIST, ISO, and OWASP serve to consolidate information and make it available to those tasked with designing and managing a program.
Who Is Responsible For Managing This Program?
The ultimate responsibility for implementing and managing a cyber security program starts with C-level executives such as the CEO, CIO, CISO, and IT management.
Policies and awareness training can be used to delegate some degree of responsibility to all employees across an organization, and IT security controls are implemented, monitored, and reported on by an IT team or dedicated security team.
Why Is Developing A Cybersecurity Program Important?
Cybercrime is becoming increasingly prevalent, persistent, and costly.
Companies incurred approximately $6 trillion in losses due to cybercrime in 2021, and the average cost of a data breach was $4.45M per incident in 2023 according to an IBM report.
The consequences of cyber-attacks include downtime, a tarnished brand reputation leading to fewer business relationships, and potentially large fines or class action lawsuits.
In one example, 3rd party software vendor Kaseya experienced a ransomware attack that leveraged a supply chain attack that installed ransomware on client victim’s systems.
The group responsible, REvil, demanded a $70M demand in exchange for decrypting the impacted data.
The Kaseya ransomware attack demonstrates the importance of developing controls to detect cyber breaches and having plans in place to respond quickly and effectively to reduce the negative impact they cause.
Ad Hoc Security Isn’t a Strategy
Ignoring the threat of cyber attacks won’t make them go away.
When an organization puts its head in the sand and deals with cybersecurity incidents reactively, the risk and potential costs are often much greater.
Any claims of ignorance will likely fall on deaf ears since cybercrime has been grabbing major headlines for some time now.
However, if properly prepared, an SMB could walk away from a cyber attack with minimal damages and have a proper policy-driven response ready for customers and clients whose data has been impacted.
View Security As An Investment
ROI is an important security metric used by decision-makers to calculate the value of an investment. It’s difficult to calculate the return on a security investment because they generally generate no positive return.
However, considering the veracity of today’s cyber-threat environment, businesses that implement cyber security programs are likely to benefit from costs prevented.
So, instead of a traditional ROI calculation, the Return on Security Investment (ROSI) equation should be used, which incorporates the savings of security events avoided.
ROSI = (Security expense avoided – prevention cost) / prevention cost
By realistically calculating the benefit of avoided costs, investment in a cyber security program can be more clearly justified and an organization can reap the rewards of being prepared to weather the storm of a cyber breach.
Creating A Cybersecurity Program
Developing and maintaining a cybersecurity program enables operational resilience.
But organizations need to calculate and apply relative risk and focus efforts in an organized strategic way, rather than relying on an ad-hoc reactive approach.
For SMBs, a cyber security program should begin with an appropriate scope to ensure manageability. As a business grows, it can expand its program’s scope to meet the evolving risk requirements.
From there, organizations need to continue to monitor and improve their cybersecurity program to achieve true continuous cyber resilience.
Step 1: Conduct A Security Risk Assessment
Risk does not exist uniformly throughout an organization. Every business has critical processes and assets essential to its operations.
The goal of conducting a security risk assessment is to identify critical processes and assets and assess the contextual risk of each.
This map of contextual risk is used in subsequent stages of the cyber security program development process to allocate resources and develop appropriate security policies and controls that ensure operational resilience.
An organization’s contextual risk landscape may also depend on relevant national regulations such as:
- GDPR for companies that store Personally Identifiable Information (PII).
- HIPPA for those who store Personal Health Information (PHI).
- Industry standards such as PCI-DSS for companies that directly handle payment card data.
Violating regulations and industry standards have consequences such as fines or other restrictions, which should be included in a risk assessment.
Step 2: Select A Cybersecurity Framework
After an organization has conducted a risk assessment, it can select the most appropriate cybersecurity framework to mitigate cyber risk in concordance with the findings of the risk assessment.
The cyber security framework will serve as an advisory for best practices during the design and implementation of policies and controls.
In many cases, following the CIS top 18 controls is a low-cost and attainable framework for small businesses to follow.
Other common cyber security standards are:
- ISO-27001 / ISO-27002
- NIST Cybersecurity Framework (CSF)
- Center for Internet Security Critical Security Controls (CIS-CSC)
In some cases, businesses must conform to a particular standard such as PCI-DSS for companies that directly handle payment card data, or the Cybersecurity Maturity Model Certification (CMMC) for those that interact with the US Department of Defense (DoD).
National regulations may also require businesses to take proactive measures to protect customer data such as GDPR for organizations based in the EU, and HIPPA for US organizations that handle Personal Health Information (PHI).

Step 3: Develop A Cybersecurity Strategy
A cybersecurity program is a continuous and iterative process.
A cybersecurity strategy is a formalized plan or roadmap that establishes a baseline for a company’s security program and plans activities over the next 2-3 years.
Developing a cyber security strategy involves:
- Creating teams.
- Assigning roles and responsibilities.
- Allocating resources.
- Creating target milestones.
- Planning core activities.
Core activities, in this case, include:
- Policy and security control development.
- Testing.
- Monitoring.
- Review strategies.
- Vulnerability scanning.
- Penetration testing.
- Security awareness training.
By planning the program’s road, an organization can ensure that defensive security remains consistently resilient to emerging threats and risks over time.
Without a well-organized and long-term strategy, an enterprise is more likely to fall back into an ad hoc approach to security.
Step 4: Develop A Security Risk Management Plan
Each organization’s risk landscape is unique and evolves.
A security risk management plan is an iterative process that periodically reassesses where the relative risk lies within an organization.
This allows the prioritization of assets and processes so that resources can be allocated appropriately, and risk can be mitigated with contextual cyber security policies and controls that address each business’s unique requirements.
An SMB may want to apply a full-fledged IT Risk Management Framework (RMF) to ensure they are following a best-practices approach to managing risk.
Some common IT Risk Management Frameworks include:
Free Security Policy Templates
Get a step ahead of your cybersecurity goals with our comprehensive templates.

Step 5: Create Security Policies And Procedures
Policies and procedures help to define the standard operating procedures (SOP) that will ultimately ensure IT security best practices of the selected cyber security framework are applied and remain active.
The most fundamental way to describe the key function of IT security policies and controls is to protect the:
- Confidentiality – Data cannot be accessed by unauthorized individuals or systems.
- Integrity – Data cannot be modified by unauthorized individuals or systems.
- Availability – Systems that are always online can be accessed when they are needed, of data-at-rest (as it is stored on medium such as hard drives, removable drives, or on cloud resources), data-in-transit (as it is transferred across a network), and data-in-use (as it is being processed by a CPU and RAM).
Protecting these critical elements should include:
- Administrative controls.
- Technical controls.
- Physical controls.
These controls are designed to detect, prevent, and recover from all incidents that could otherwise negatively impact the organization’s IT infrastructure and business operations.
Step 6: Secure Your Network
Creating a plan to secure your network includes protecting data as it travels across the network, and also protecting each endpoint on the network.
Let’s examine some of the most important aspects of network security.
Related Content: How To Manage Your Network Security In 8 Steps
Install And Configure Next-Generation Firewalls
To properly protect a network and endpoints, next-gen firewalls should be installed in strategic locations within the network topography.
Next-gen firewalls extend the capabilities of traditional firewalls and are capable of advanced network security functions such as:
- Intrusion detection and prevention.
- Content filtering to examine incoming files and quarantine those with detected malware.
- URL filtering to restrict which websites may be accessed from inside a network.
- Performing traditional firewall activities such as restricting which ports may be accessed across the network.
Implement A Continuous Vulnerability Management Strategy
To mitigate vulnerabilities that could be exploited by an attacker, organizations should take a continuous approach to their vulnerability management.
Another fundamental component of vulnerability management is the timely installation of software patches to ensure that updates are applied in order to remediate vulnerabilities in operating systems and software applications that have been discovered by the vendors themselves.
In more advanced vulnerability management programs, penetration testing can ensure strong network defenses are effectively protecting, and cannot be circumvented by an attacker.
It’s also important to note that periodic scanning, vulnerability remediation, and penetration testing may be required by industry standards such as PCI-DSS and SOC-2.
Install Endpoint Security Products
Since a network infrastructure includes both the medium that enables data to travel between systems and the systems themselves, good network security requires protecting both.
A variety of endpoint security products such as traditional malware scanners, and more modern and advanced endpoint detection and response (EDR) solutions are available and should be installed on endpoints to reduce the risk of infection.
The main advantage of an EDR solution is that it can continuously monitor a system for indicators of compromise (IOC), rather than merely scanning files for malware as they enter an endpoint.
It’s also important to configure security products to push alerts to pre-designated IT team members in order to monitor, investigate, and take further action when required.
Step 7: Secure Your Data
Data is a critical asset for business operations, and failure to properly protect data can leave an organization vulnerable to ransomware attacks and/or result in important trade secrets being stolen.
After identifying and classifying data according to its sensitivity level, decision-makers can determine which forms of protection should be applied.
Free Resource: Sample Data Security Policy Template
Implement Data Loss Prevention Strategies
Data Loss Prevention (DLP) combines a group of strategic approaches to prevent sensitive data from being stolen from an organization.
Related Content: 9 Data Security Strategies You Need To Implement
A few data loss prevention strategies include:
- Encrypting data-at-rest
- Enabling remote-wipe capabilities on mobile devices (laptops, phones, and tablets).
- Implementing removable media restrictions (banning or monitoring the use of removable USB drives and optical media).
In terms of internal network DLP, Next-Gen firewalls can be configured to scan for and block sensitive files from being exfiltrated from the network.
DLP strategy can also include administrative policies such as a “least privilege” policy that ensures access to data is only given to individuals and systems that require it, and “segregation of duties” that make sure that operations are broken into small tasks ensuring that responsibility and authority are not concentrated into one individual or a single small group.
Implement A Backup Solution
Strong and effective backup solutions are critical to ensure that a business’s operations can be continued indefinitely.
This should include backups that store data in various formats and at various stages of its lifecycle such as:
- Full-disk images of endpoints.
- Servers.
- Cloud-based resources such as Virtual Private Servers (VPSs).
- Separate backups of databases, applications, and other files.
The process of recovering from backup should be tested to ensure that acceptable recovery time objectives (RTO) and recovery point objectives (RPO) can be met.
This allows an organization the ability to adjust its backup strategy and make sure it can perform when needed.
Finally, backups should be stored in multiple locations including at least one backup off-premises with advanced technologies such as RAID to mitigate data-loss due to drive failure.
Create A Data Recovery / Disaster Recovery Plan
Designing a disaster recovery plan, and knowing how to implement it can be the difference between a minor downtime incident and an extended interruption that can leave a lasting financial impact.
Ransomware attacks continue to be more sophisticated every day, but a well-designed recovery plan ensures that critical IT staff know how to fully and quickly recover ransomware-encrypted files and systems from backups.
Recovery exercises serve to train IT teams and build confidence that recovering from an incident can happen quickly and effectively, thus reducing potential missteps caused by stress during a real cyber breach incident.
Implement Security Awareness Training
Communication channels such as email, social media, and other private messaging systems are an easy way for attackers to introduce malicious files or links into an organization’s network.
Employees can be tricked into executing files or clicking links by attackers employing sophisticated social engineering tactics known as phishing or spear-phishing attacks that use context gained through extensive reconnaissance of an organization.
Proper training can give staff the knowledge and awareness they need to discern between real business communication and phishing attacks, and take policy driven action when they suspect being targeted.
Step 8: Secure Your Applications
Software applications are the tools that fundamentally underpin an organization’s operations.
It’s also true that exploiting applications is the most common vector that external attackers exploit to gain initial access to an organization’s network.
Let’s take a look at some fundamental ways SMBs should secure their applications.
Have A Provider Host Critical Business Applications
Digital transformation has unquestionably increased the complexity of business operations and comes with increased costs and risks.
However, both costs and risks can be reduced then SMBs choose to outsource critical functions to an IT provider.
The business model allows companies to take advantage of outsourced specialized talent including increased security capabilities.
For example, managing an email server is a complex task with dire consequences.
If an organization’s email server is breached, a company may lose the ability to communicate with customers, have its email encrypted by ransomware, destroyed, or stolen; resulting in the loss of business secrets.
Therefore, many SMBs choose to outsource the management of their email to a provider.
In addition, by shifting office applications to a provider’s cloud environment, the files conveniently become available from anywhere, easily shared and used in team collaboration, and backups are automatically managed by the vendor.
Use Multi-Factor Authentication
There are several ways that attackers can try to exploit a user account to gain access. Stolen passwords and brute force password spraying are a couple of the most used tricks.
The best defense against user account attacks is Multi-Factor Authentication (MFA).
MFA ensures strong authentication by requiring the user to verify a one-time-passcode (OTP) delivered to their mobile device, or probing a USB hardware token.
YubiKeys are by far our favorite hardware token on the market today.
Limit The Installation Of Applications To Those Required
Attackers can only exploit software that is available to be exploited.
Application whitelisting is the practice of specifying a list of approved software applications that are permitted to be installed on each system and verifying that no other applications are present.
Application whitelisting serves to reduce the attack surface by limiting the number of ways that an attacker can gain initial access to a network.
Application whitelisting can also serve to limit the options an attacker has after initial access has been gained since many attackers employ a live-off-the-land (LOTL) approach.
Using tools that come pre-installed with an operating system, instead of importing their exploit toolkits, potentially triggering security alerts.
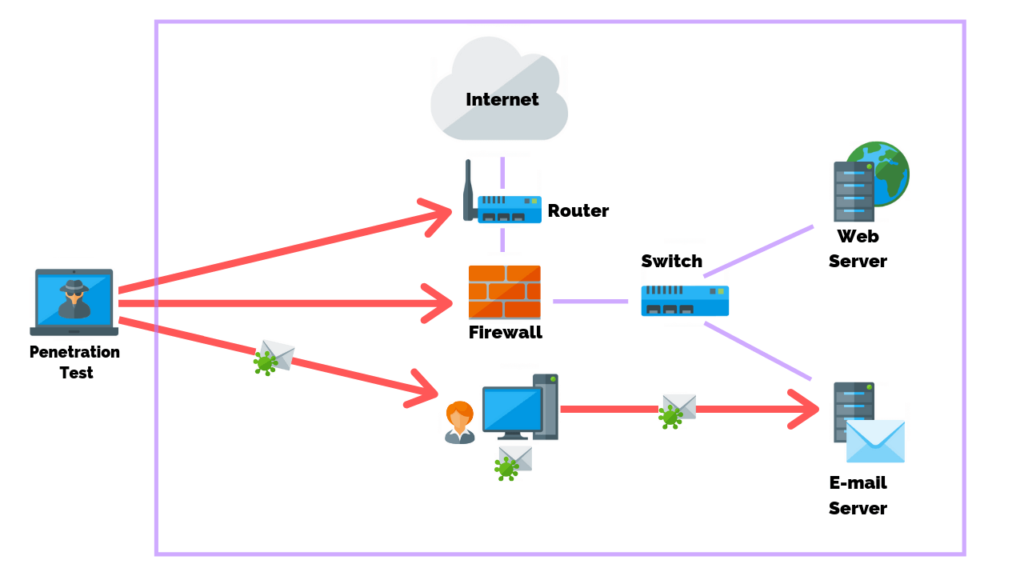
Step 9: Test Your Security Posture
Designing and implementing policies and controls is the heart and soul of a cybersecurity program. However, all that hard work is pointless if you do not monitor for adherence and test for effectiveness.
Defenders are tasked with protecting every aspect of the potential attack surface, while cyber attackers only need to find one security gap for success.
Testing the effectiveness of security controls includes testing production systems for misconfigurations and monitoring to ensure that secure configurations are persistent.
More advanced testing strategies include penetration testing and red team exercises where cyber-attacks are simulated against a network to test the implemented security controls.
Penetration testing and red team exercises also serve to test a security team’s ability to detect and properly mitigate malicious behavior on the network and its endpoints.
Free Resource: Sample Penetration Test Report
Step 10: Evaluate And Improve Program Effectiveness
The cyber threat landscape and business operations are both evolving environments that create the need for adjustments to a cyber security program.
Therefore, a cyber security program needs to be an iterative process to maintain its resiliency.
The evaluation process allows an organization to:
- Assess the effectiveness of the program as it stands.
- Identify potential ways to streamline the program.
- Improve the program in areas that have been identified as lacking appropriate security.
For example, monitoring can show that cyber-attacks are concentrated, or where the level of risk has changed.
The evaluation phase is a good time to take note of strategic victories and generate progress reports that can serve to inform top-level managers about the cyber security programs’ effectiveness and areas where more resources may be needed.
Common Pitfalls To Avoid When Building A Cyber Security Program
Now that we have established the key steps of implementing a cyber security program, let’s take a look at some common mistakes that get made and how you can avoid them.
Not Effectively Sharing Your ‘Success’ Stories
Executives want to see results. Generally, broad-scoped bullet points and high-level details are the most effective ways to relay progress to management, but regardless, it’s important to show how the implemented policies and controls have reduced risk for the business.
Recognizing a security team’s successes can go a long way toward maintaining the morale and motivation of the team.
Lack Of Documentation
The difficulty of implementing a cyber security program is increased exponentially when proper documentation is lacking or not easily accessible to security team members and managers.
Good documentation prevents misconfigurations, violations of policies, missing steps of critical processes, and ensures that reviews and reporting are done reliably.
Allowing Out-Dated Systems Or Software
The IT environment is fast-changing. New vulnerabilities are found and patched on a day-to-day basis, so it’s important that your business effectively keeps pace with change.
Unless legacy infrastructure absolutely cannot be updated, it must be updated regularly. Turn on automatic updates whenever feasible.
Insufficient Budget To Support The Program
A cybersecurity program may seem like just a cost with no return, but when you consider the costs saved by preventing one or more cyber breaches, it makes sense to allocate enough resources toward cybersecurity.
A good cyber security program will reduce the chances of suffering a breach, and allow an organization to recover from a breach quickly and completely.
Thinking You Can Do It Alone
Many organizations lack the funds and expertise to build a full-time in-house security team and to develop an effective cybersecurity program on their own.
Partnering with a Managed Security Service Provider (MSSP) or a virtual CISO is a cost-effective and convenient way to gain access to professional dedicated security knowledge and skills and can streamline the process of gaining strong security assurances and lower costs.
Wrapping Up
In the modern digital age, cyber security is a must-have. SMBs are squarely on the radar of cybercriminals.
Those who are unprepared run a high risk of indefinite operational downtime, loss of access to critical data, reduced customer base as clients flee, fines if they violate regional regulations and even potential class action lawsuits on behalf of users who had their data stolen.
Building a cybersecurity program starts with a risk assessment and selecting the appropriate cyber security Framework.
From there the managers and IT team need to build policies and controls that will implement cybersecurity industry best practices to secure the organization’s:
- Network
- Endpoints
- Data
- Software applications
Although the development and deployment of a cybersecurity program can feel overwhelming, stakeholders need to begin the process of understanding cybersecurity, and how an organized approach to initializing a manageable program can measurably reduce risk, and evolve as a business grows.
Article by