What Is Endpoint Detection And Response? (And Why It’s Important)
Endpoints today pose a significant security risk to businesses.
One reason is that hackers have learned how to inject code into the operating system and its underlying applications.
Endpoint detection and response (EDR) provides an additional layer of endpoint protection that is lacking with traditional anti-virus software. The intent of most hackers today is to secretly install malware onto the endpoint in order to steal passwords, encrypt and hold your files ransom, record your keystrokes, or stealthily perform malicious activity. To counter the hidden threats aimed at exploiting the endpoint, a layer of endpoint protection is needed.
In this article, we will define EDR, explain how it works, explore when it is needed, and find out which solutions are leading the pack in the EDR market today.
Article Navigation
- What Is An Endpoint?
- Endpoint Detection and Response (EDR)
- How Does EDR Work?
- When Do You Need An EDR Solution?
- What Are The Best EDR Tools?
What Is An Endpoint?
The endpoint is the communication entry and exit point of an organization’s network.
The most common endpoints for an organization are:
- Laptops
- Workstations
- Servers
- Tablets
- Smartphones
The endpoint device contains the operating system and applications that allow us to connect to the Internet.
Once that connection is made, the endpoint device can send and receive email, process financial transactions, and perform many other related activities in a matter of seconds. This is an awesome technology, however, it comes with a major drawback.
Read more: 10 Cyber Security Trends You Can’t Ignore In 2021
Endpoint Detection and Response (EDR)
Endpoint detection and response technology is defined as a solution that continuously records system activities and events taking place on endpoints and provide security teams with the visibility, they need to uncover incidents that would otherwise remain invisible.
A Gartner researcher coined the term in 2013 to distinguish its capabilities from traditional anti-malware tools.
Is Anti-Virus The Same As EDR?
Is advanced threat protection the same as EDR? Well, like most scenarios in cyber security – it depends. The multiplicity of terms and products used to protect the endpoint can be challenging and confusing.
The reason being is that EDR may be the component of a software vendor’s product suite. The vendor may use the terms interchangeably or distinctly list it as a standalone product. We will get into the details of the various vendors later in this article, but for now, we’ll look at the differences between EDR and anti-virus solutions.
EDR complements traditional anti-virus.
The objective of anti-virus is to prevent malware by matching a specific signature or pattern. Once the signature of the malware is matched, the file in question is usually deleted or quarantined to another folder on the endpoint.
The activity is logged on the endpoint and that’s the end of it. But what if the malware is not totally cleaned, and continues to run under a new process. This time, files are damaged or corrupted. The desktop support analyst is now tasked with locating logs and trying to perform analysis which may take a significant amount of time.
What is the usual course of action? Remove the device from the network and wipe it clean. This approach will indeed save time and man-hours, but what if the same malware appears again, or better yet on different endpoints on the corporate network. The issue is obvious, another method of alerting and analysis is needed to complement the existing solution.
This is where EDR comes into the picture.
EDR provides a graphical view of how the attacker gained access to the system and what they did once they were inside. EDR can detect malicious activity on an endpoint as a result of zero-day exploits, advanced persistent threats, fileless or malware-free attacks, which don’t leave signatures and can, therefore, evade legacy anti-virus.
How Does EDR Work?
In order for EDR to learn and monitor an endpoint, it must first be installed on the endpoint. This installation is usually in the form of an agent or software package that is deployed to the endpoint. The agent resides on the endpoint which gathers data and reports to a back-end database system on-premise on the organization’s network or to a cloud instance.
Although each vendor has their own specific agent that performs the detection, the core functionality of EDR is similar across all vendors.
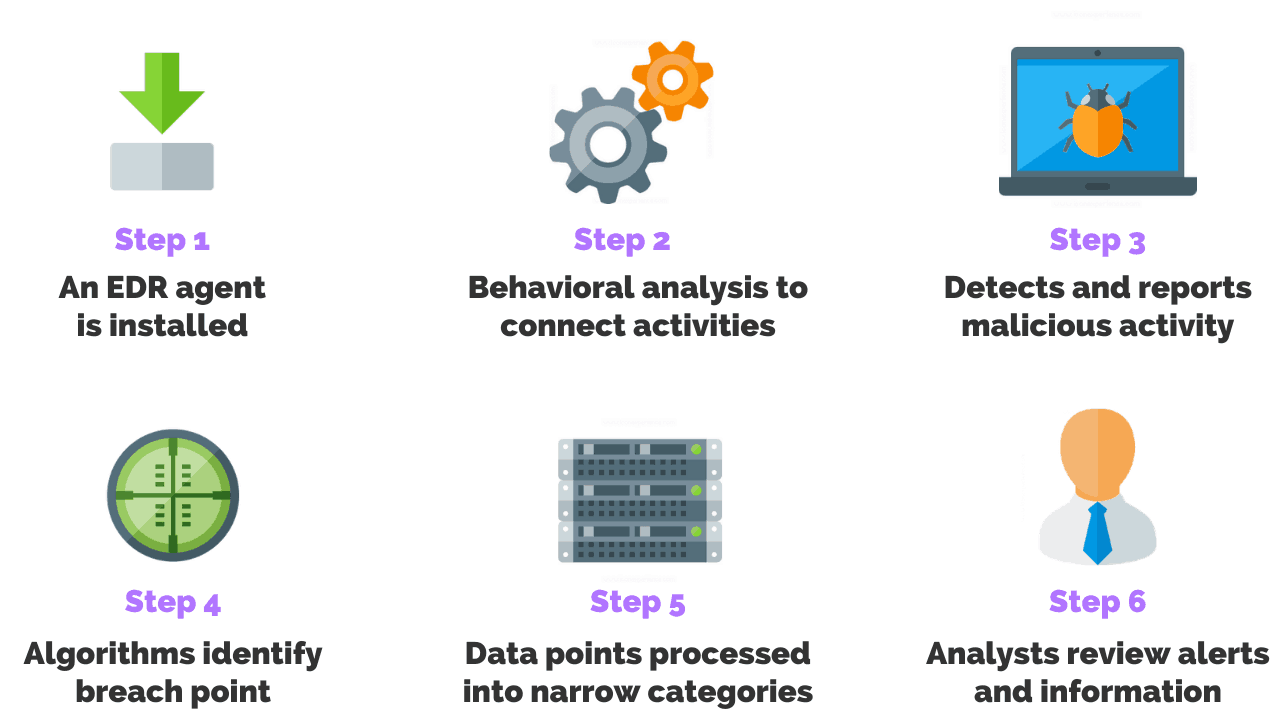
Let’s now take a deeper dive and examine how EDR works:
- An agent is installed on the endpoint device. The agent monitors the computer and archives all of its actions.
- The user and entity behavior analytics (UEBA) is a type of cyber security process that takes note of the normal conduct of users. In turn, they detect any anomalous behavior or instances when there are deviations from these “normal” patterns. For example, if a particular user regularly downloads 10 MB of files every day but suddenly downloads gigabytes of files, the system would be able to detect this anomaly and alert them immediately.
- The agent continuously monitors and analyzes activities on the endpoint and reports information directly to a console dashboard via a notification alert.
- The agent detects occurrence of abnormal behavior on the endpoint, potentially malicious. Advanced algorithms map a path of services and processes that were sequentially executed during the attack
- A visualization or process map is created to illustrate the process or processes that triggered the event. The capability to drill down to the defending executable or program is provided and where it came from.
- A security analyst or Engineer receives a notification alert message via email. The analyst reviews the alerts in order to create a plan of remediation.
As previously stated, the core functionality of EDR solutions on the market today are similar in how they perform. The major differentiator amongst the vendors is how they visually present the information to the console. Regardless of the dashboard or console view, the end goal of EDR is to provide a real-time and historical analysis of a malicious attack.
When Do You Need An EDR Solution?
When a new endpoint is powered up and connected to the local corporate network or the internet, it is susceptible to an attack.
It’s not uncommon for new or existing computers to automatically connect to the website of your anti-virus product in order to download the latest anti-malware virus definitions. In a corporate environment, IT support teams may point all endpoints to a repository server to retrieve anti-virus software packages.
If an organization fails to have a process in place to update its endpoints immediately with some form of anti-malware protection, it’s a matter of time before the endpoint is attacked.
Today, with the influx of hackers and innovative malware techniques, executive decision-makers are faced with the challenge of whether to purchase and add more endpoint security solutions to stay ahead of the hackers.
Depending on the nature of the organization, a business may handle PII, PHI, and PCI data. The risk of data loss in either of these standards is high.
Therefore, security analysts must have endpoint tools that provide visibility on the behavior of system processes in real-time, along with the ability to perform post reconnaissance on an endpoint that has been exploited.
EDR can provide this level of visibility.
Anti-virus software historically is the most common component for securing the endpoint. Security experts suggest that anti-virus applications are not enough, while others say it’s not necessary at all.
The facts show that standalone anti-virus protection is not the silver bullet to detect advanced malware today, such as, ransomware. The approach that many security experts in the field suggest is that defense in depth is the best solution.
When an organization is compromised by malicious malware, such as ransomware, it is usually discovered that that anti-malware software was installed and running. This occurrence is a strong indicator that a robust complementary tool is needed, namely EDR.
The best time to consider an EDR solution is before the attack.
This isn’t unlike protecting your home. It’s standard for a new home to have doors and windows that lock. For added protection though, most new homeowners immediately purchase an alarm system to complement the traditional security of the door and window locks.
Similar to the protection of your endpoints, more than just traditional anti-virus is needed. EDR complements anti-virus.
The good news is that many anti-virus vendors have developed EDR software that integrates with their existing anti-virus agent or is a separate product that can be managed from the same console. In the next section, we will review top leaders in the EDR market.
What Are The Best EDR Tools?
According to an independent market research report by Forrester, three companies lead the pack in Enterprise Detection Response (another name for EDR) solutions.
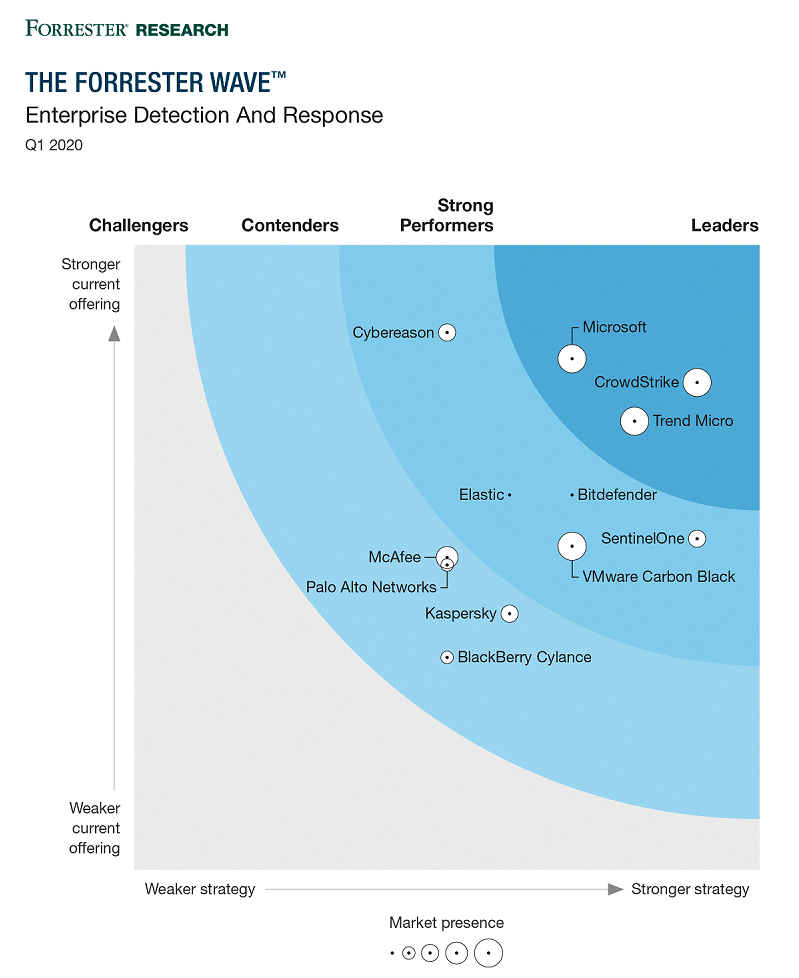
The top EDR solutions on the market today include:
- Microsoft’s Advanced Threat Prevention
- CrowdStrike’s Falcon Insight
- Trend Micro
- VMware Carbon Black
- Bitdefender
- Cybereason
- Elastic
- SentinelOne
- McAfee
- Cybereason
- Palo Alto Networks
- Kaspersky
- BlackBerry Cylance
Interestingly, Microsoft is one of the top leaders in the first quarter of 2020 based on a current Forrester report. When you think of Microsoft, their free anti-virus solution named Windows Defender comes to mind. Not any longer, Microsoft has introduced EDR capabilities within their Advanced Threat Prevention product.
VMWare Carbon Black is another popular EDR product that gives the security analyst a visualization of an endpoint under attack and provides the recording capabilities to look back at the process flow of the threat.
I can personally attest to the capability of this product. Our team was called upon to investigate a possible data leakage event from an unknown source that occurred several hours earlier.
Since we owned Carbon Black’s Threat Hunter product along with agents deployed to our laptops, the analyst logged into the console and located the asset that was suspected to be compromised.
Utilizing the Process Analysis example below, we were able to drill down on all of the children processes to locate a program executable on the endpoint.
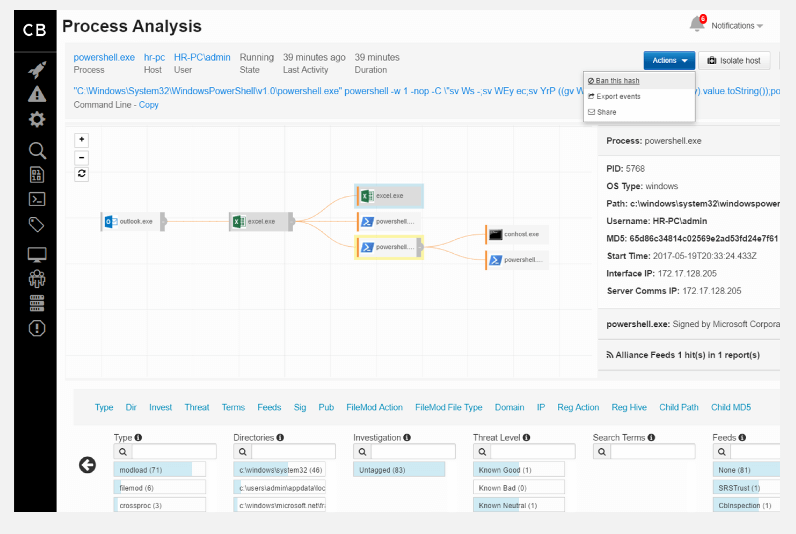
Within minutes, we were able to locate the remote process that attempted to access the device and the IP address of the source. The activity aligned with the time of the suspected attack which confirmed that we had located the source of the issue.
Fortunately, we determined that this was not a malicious attack, but was an inadvertent attempt to remote control the device by an internal support analyst. Based on the result of the analysis with Carbon Black Threat Hunter, we experienced first-hand the capabilities and value of an EDR solution.
How Much Does an EDR Solution Cost?
Since many vendors do not fully disclose their rates on their public website, the annual cost per user below are estimates:
| Vendor | Est. Cost Per User/ Annual |
| Microsoft Advanced Threat Prevent Standalone | $62.40 |
| CrowdStrike Falcon Insight | $59.99 |
| BitDefender Gravity UltraZone | $59.50 |
| Blackberry Cylance Protect | $45.00 |
| SentinelOne Endpoint Protection Platform | $45.00 |
The vendor, in most cases, will direct you to their recommended Value Added Reseller or Managed Service Provider for an accurate quote.
Other factors that influence the cost of EDR solutions include:
- Number of users
- Maintenance
- Support
Like any other complex security application, internal operations staff will need to fully understand the features of the tool in order to recognize and respond to attacks. If your organization decides to move forward with the purchase of an EDR solution, it is prudent to include training.
This will increase the overall cost, however, it is necessary in order to optimally receive a return on the investment.
Many vendors also offer professional services to assist in implementing the application as well as providing post support.
Adding this level of service will more than likely increase the overall annual cost, however, the additional cost is well worth it if the expertise and resources are limited in-house.
Conclusion
They say in the sports world, that the best defense is a good offense. Many organizations today are focused on adding security layers to defend their corporate infrastructure on-premise or in the cloud.
An EDR solution not only adds a defensive layer, but it also provides an offensive component by proactively uncovering threat events before they can impact the network.
In this article, we have defined the term Endpoint Detection and Response (EDR) solution and how it complements existing malware and threat prevention tools.
An effective EDR solution can extend and provide much-needed visibility for security support teams to quickly investigate threats as they occur in real-time or from an archived backup.
Adding an EDR solution will definitely enhance the security posture of your organization. Once implemented, you will be on your way to protecting your endpoints from attacks in order to keep your business operations moving safely and securely.
Related Articles
- Vulnerability Scans VS Penetration Tests: What’s The Main Difference?
- How To Perform A Successful Network Vulnerability Assessment
- What Is A Red Team VS A Blue Team In Cyber Security?
- How Often Should You Perform A Penetration Test?
- Network Security Types: Expert Explains The Basics Of Cyber Security