Vulnerability Scanning VS Penetration Testing
Learn about PurpleSec’s fully managed vulnerability management services.
As cyber attacks continue to become more sophisticated, businesses are required to invest in more robust security solutions like vulnerability assessments and penetration testing to protect their data, reputation, and revenues.
Vulnerability scanning identifies known vulnerabilities, lack of security controls, and common misconfigurations within systems on a network. Penetration testing simulates an attack to exploit weaknesses in order to prove the effectiveness of your network’s security. The main difference is that vulnerability scanning is used for both defensive and offensive cyber security strategies while penetration testing is offensive in nature.
Article Navigation
- What Is Vulnerability Scanning?
- How Much Does A Vulnerability Scan Cost?
- How Often Should You Get A Vulnerability Scan?
- How Long Does It Take To Perform A Vulnerability Scan?
- Vulnerability Scanning Tools
- What Is A Penetration Test?
- What Type Of Penetration Do You Need?
- How Long Does It Take To Perform A Penetration Test?
- How Much Does A Penetration Test Cost?
- Penetration Testing Tools
What Is Vulnerability Scanning?
With vulnerability scans, tools are used to log into your systems via credentials or defaults providing a map of the entire system. During this process, the scan builds inventories then compares all the items listed against possible weaknesses.
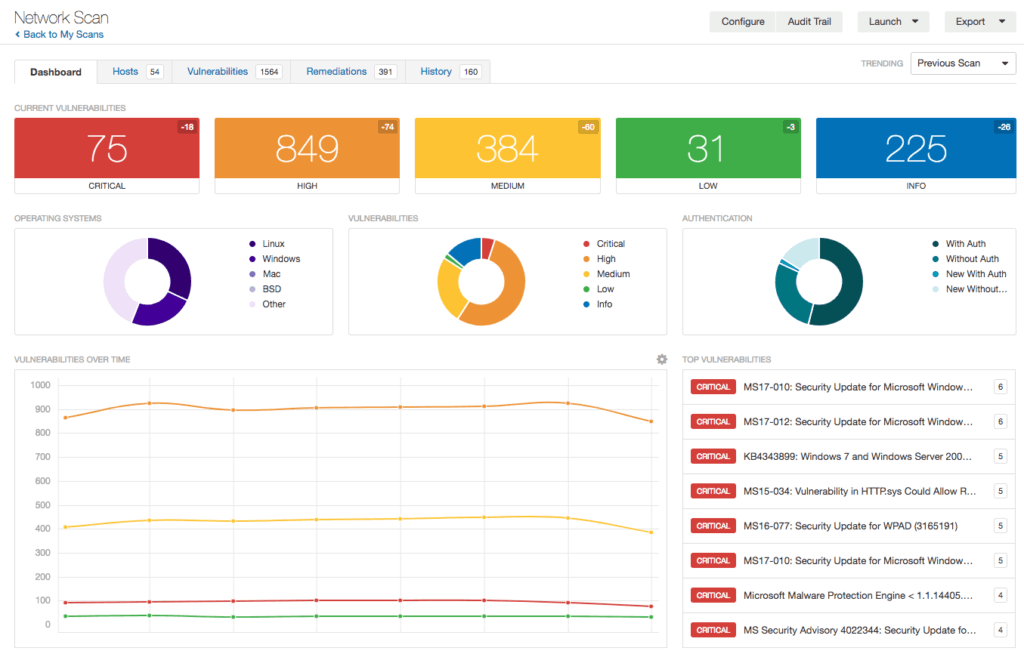
The goal of a vulnerability scan is to identify and categorize vulnerabilities found on your network. Scans on their own don’t provide much information for businesses. The real value is in the vulnerability assessment report.
In order to conduct this assessment, a security expert reviews the raw scan results and compiles a report, which contains a summary of findings along with a remediation plan.
You will need to plan ahead prior to scanning your network, as it may impact system performance and cause bandwidth issues. This is especially true depending on the type of vulnerability scan being performed. Because of the potential impact on operations, it’s recommended that vulnerability scans be performed outside of standard business hours.
Employees should also be instructed to leave their workstations at the office, powered on, and connected to the network if you want a complete scan. Alternatively, you can install an endpoint agent on each workstation.
Read More: How To Develop & Implement A Network Security Plan
How Much Does A Vulnerability Scan Cost?
There are a number of factors that affect the cost of a vulnerability scan including the environment being scanned such as an internal network or web application.
On average, vulnerability assessment costs can range between $2,000 – $2,500 depending on the number of IPs, servers, or applications scanned.
IP Based Pricing Model
There are a variety of pricing models used for vulnerability scans. For network scans it’s not uncommon for security vendors to price the solution based on the number of IPs scanned.
| IPs | Annually | Quarterly | Monthly |
|---|---|---|---|
| 100 | $2.500 | $1,900 | $500 |
| 200 | $4,800 | $3,600 | $1,100 |
| 300 | $6,900 | $5,100 | $1,600 |
| 400 | $8,400 | $6,000 | $1,900 |
| 500 | $10,000 | $7,000 | $2,200 |
How Often Should You Get A Vulnerability Scan?
While every business need is different, it’s best practice to perform network vulnerability scans at least once per quarter. However, vulnerability scans may be required monthly or weekly based on compliance, major changes to infrastructure, and internal network security capabilities.
How Long Does It Take To Perform A Vulnerability Scan?
A vulnerability scan will take 20 – 60 minutes, depending on the number of IPs, while web scans may take up to 2 – 4 hours to complete. Scans can be automated and maintained by a network administrator or an internal security team.
The frequency of performing scans depends on the scope of the site to be scanned, network latency, and system services you need to be examined. However, unless there are specific compliance, regulation, legal, or specific industry factors, it’s typical to conduct vulnerability scans monthly, quarterly, or annually.
Vulnerability Scanning Tools
Software tools for vulnerability scans will vary depending on the goals of the exercise. The type of exercise will also influence the tools used.
Examples of vulnerability scanning tools include:
- Nessus – is a super easy to use vulnerability scanning tool that was designed to reduce the overall time and efforts you may need for scanning, prioritizing, and remediating issues. It works by testing all the ports in a device individually to define its operating system. It then examines the operating system to check for any known vulnerability.
- OpenVas – is cleverly engineered to help perform in-depth vulnerability scanning and management packaging by scanning all the network devices, and servers. It works by picking the target, e.g., a specified IP address then launching the scans according to the preferred scanning type to diagnose weaknesses.
- Netspark – is a security scanner testing tool used to automate website application tests. The software is able to identify cross-site scripting and SQL injection attacks. This is particularly important for developers as they can use Netspark on their websites, web services, and web applications.
What Is A Penetration Test?
A penetration test involves a team of security professionals who actively attempt to break into your company’s network by exploiting weaknesses and vulnerabilities in your systems.
Penetration tests may include any of the following methods:
- Using social engineering hacking techniques to access system and related databases.
- Sending of phishing emails to access critical accounts.
- Using unencrypted passwords shared in the network to access sensitive databases.
These attempts can be far more intrusive than a vulnerability scan and may cause a denial of service, increased system utilization, which may reduce productivity, and corrupt the machines. In some cases, you may schedule penetration tests and inform staff in advance of the exercise.
However, this wouldn’t be applicable if you want to test how your internal security team responds to a “live” threat.
What’s important is that you’re conducting a penetration test with a specific intent and clearly defining your wants and needs with the penetration testing team.
For example, you may just finish rolling out a new cyber security program for your business and want to test its effectiveness. A penetration test can determine if certain objectives of the program have been achieved such as maintaining 99.99% availability during an attack, or ensuring data loss prevention (DLP) systems are blocking would-be attackers from exfiltrating data.
What Type Of Penetration Do You Need?
There’s a number of factors to consider before conducting a penetration test.
The first step is to clearly define the goals and purpose of the test. Are you trying to simulate an attack against your safeguards? Do you want to simulate an internal attack to see what level of access an attacker could get into your network? Is there a compliance requirement? If so, do they have specifications?
Next, what type of penetration test do you need to be performed? Network, web application, client side, wireless, social engineering, or physical? Additional information may be required such as credentials to a user account, number of devices, user count, or an estimate of how large the systems are in order to provide an accurate scope of work (SOW).
Finally, you’ll need to specify whether you want an external or internal test. Most industry compliance requirements test both externally and internally as it best simulates the various attack vectors used by attackers.
How Long Does It Take To Perform A Penetration Test?
Depending on the type of penetration test performed, the number of systems tested, and possible constraints, it may take around 1-3 weeks to complete a penetration test. If you’re testing individual processes, applications, or systems, it may take less than one week.
It’s recommended that you perform penetration tests at least 1 – 2 times per year. However, this depends on your business needs, the type of data you store, and compliance factors.
How Much Does A Penetration Test Cost?
A penetration test can cost between $4,000 – $100,000 on average due to how involved the process is, the resources required to execute a successful penetration test, and the duration of time required to complete the report.
The complexity of your network, the type of test being performed (network, web, application), and the tools used will also determine the price.
If you’re performing penetration tests internally you can expect to pay $80,000 – $130,000 per year for each security position along with $3,000 – $8,000+ in costs associated with software purchases.
Penetration Testing Tools
Penetration tests will vary depending on the goals of the exercise. The type of exercise will also influence the tools used.
For example, a penetration test involving a social engineering attack might use software to clone an access card. This would allow the “attacker” access into areas of the building that they’re not authorized to be in. On the other hand, the testers might use John The Ripper to crack a password hash.
You may be surprised to learn that many of the software tools used in vulnerability scanning also doubles as penetration testing tools. Likewise, many penetration tools such as Metasploit are used by security professionals to identify flaws and set up proper defenses.
Examples of penetration testing tools include:
- Kali Linux– is a popular Linux distribution penetration testing tools used mainly in high-end security auditing and penetration testing. It works by combining a set of powerful built-in tools which are excellent in reverse engineering security research to execute its operations.
- Metasploit – can be used to discover vulnerabilities, manage security evaluations, and also to formulate defense methodologies. It works by writing, testing, and executing the exploited code. It comes with a set of powerful tools, which are excellent in evading destruction, running attacks, enumerating networks, and testing vulnerabilities on target networks.
- Wireshark – captures and interprets network packs and provides both offline and live-capture options. The capture feature enables security professionals to analyze the source and destination protocols. The tool is open source and available for various systems including Windows, Solaris, FreeBSD, and Linux.
- Burp Suite – is capable of automatically crawling web-based applications. This tool would be used when attempting to gather information on web-based applications to analyze requests between a browser and its destination. The paid version provides the essentials features required for advanced penetration testing.
Conclusion
Both vulnerability scanning and penetration testing perform one significant role; helping you spot weaknesses in your network before the hackers can do it for you. In comparing the differences, one thing that remains clear is that penetration testing is more aggressive, more intrusive, and a fair bit more expensive.
That should not rule it from your plans of making your system secure and safe. When the resources are available, it’s equally recommendable to perform vulnerability scans and penetration tests.
Are you ready to work together? Get a no-obligation consultation to meet your penetration testing needs.
Related Articles