How Often Should You Perform A Network Vulnerability Scan?
Learn about PurpleSec’s fully managed vulnerability management services.
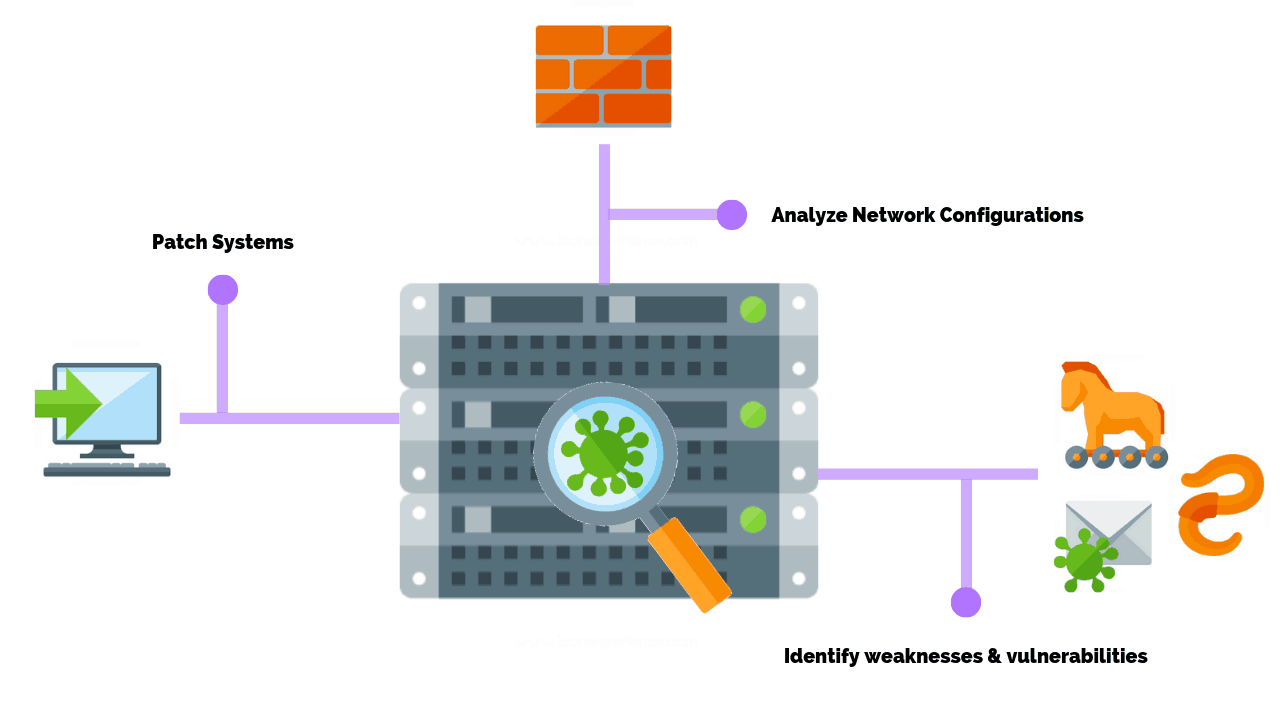
A network vulnerability scan is part of the vulnerability assessment process where the main focus is placed on finding and identifying security vulnerabilities in systems hosted on specific IP addresses.
While every business need is different, it’s best practice to perform network vulnerability scans at least once per quarter. However, vulnerability scans may be required monthly or weekly based on compliance, major changes to infrastructure, and internal network security capabilities. One way to narrow down scanning frequency is to identify and categorize the type of data your company stores such as credit card and social security numbers as well as the average length of time data is retained.
Vulnerability scans help with identifying and closing down vectors of attack by providing details regarding found vulnerabilities, possible exploits and recommendations for mitigation.
Article Navigation
- What Factors Determine Scanning Frequency?
- Network Vulnerability Assessments
- Compliance
- Major Infrastructure Changes
What Factors Determine Scanning Frequency?
Reasons and needs for vulnerability scans can vary greatly depending on the seriousness of the company and its willingness to commit to cyber security best practices.
Some of the major factors that determine the frequency of vulnerability scans include the need to achieve and maintain:
- Successful Vulnerability Assessment Processes – A vulnerability assessment is an integral part of every successful cyber security program. Thus conducting vulnerability scans and mitigating found vulnerabilities contribute to the overall efforts to keep the company’s systems and network safe.
- Compliance – Many compliance standards require vulnerability scanning to be performed on a regular basis. Presenting auditors with quarterly reports and remediation efforts is part of most audit processes.
- Adequate Security After A Major Infrastructure Change – It is a common practice to conduct vulnerability scans on parts of the infrastructure that undergone a major change in order to ensure the security of newly modified systems. Scans should also be performed after major software and patch deployments.
I’ve broken down these factors below to expand on the different types of ways a vulnerability scan can be conducted.
Read More: 10 Cyber Security Trends You Can’t Ignore In 2021
Network Vulnerability Assessments
In order to perform a security vulnerability assessment, you have to start with the identification of your assets and with the identification of each asset’s risk appetite and value. The very least you should do is identify how important each asset or network device is for your company.
By understanding the importance and by defining your risk appetite, you can move forward with the strategic components that will shape your vulnerability assessment process.
After your initial assessment of devices and with a firm strategic vulnerability assessment process in place, you must determine which devices will be publicly available on the internet and which will stay hidden from the internet, or in other words, be only accessible from inside your network.
This will clearly separate the kind of network vulnerability scan you will be performing on each device.
Before performing the vulnerability scan, you should close all unnecessary ports and services that are running on each device and go over the configuration settings. Performing basic hardening of each device early on in the process will allow you to focus on more complex issues that may arise later during the scanning process.
Finally, configure your network vulnerability scan in such a way that it corresponds with the type of device you wish to scan. It is very important to have a security specialist perform the scan in order to make sure you don’t miss any present vulnerability due to poor configuration of the scan.
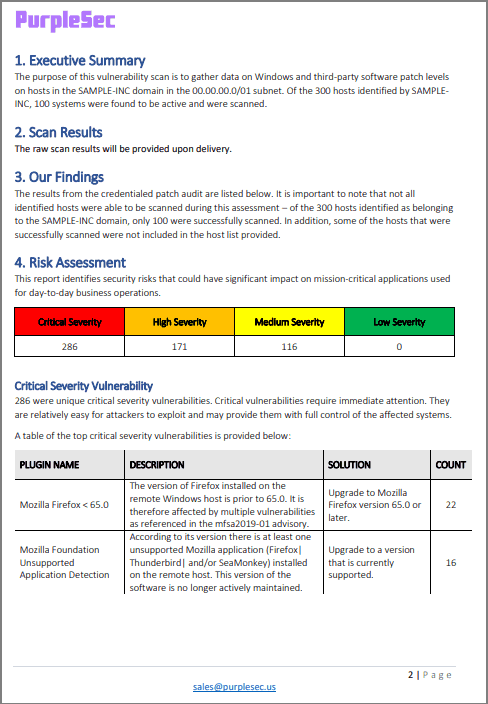
After the scan is complete, a report needs to be generated and examined.
The results should be interpreted and summarized in such a way that your IT department can easily grasp the vulnerabilities at hand and properly mitigate them.
Depending on the severity of found vulnerabilities, it might take 1-2 weeks to apply a proper fix to address all issues. A follow-up scan using the same configurations should be performed after applying the fix in order to confirm the success of the vulnerability mitigation actions.
Compliance
Compliance plays a big role in pushing companies to perform network vulnerability scans on a regular basis.
The following are some of the most well-known compliance standards and their requirements around vulnerability scans:
- ISO27001 – One of the most appreciated certification standards in cyber security recommends performing both external and internal vulnerability scans on a quarterly basis.
- Health Insurance Portability and Accountability Act (HIPAA) – places heavy emphasis on the risk assessment process. Even though HIPAA doesn’t require a network vulnerability scan, it places heavy emphasis on a detailed assessment of vulnerabilities and potential risks, which are more easily identified with a vulnerability scan in your arsenal.
- Payment Card Industry Security Standards Council (PCI DSS) – Most strict in its requirements regarding network vulnerability scanning. Quarterly external and internal scans are required to be performed by qualified personnel. On top of that, the vulnerability scans must be conducted by an approved scanning vendor.
- Federal Information Security Management Act (FISMA) – All federal agencies in the United States must be FISMA compliant. That being said, FISMA requires an implemented and well-documented program that protects the availability, confidentiality and integrity of IT systems. It goes without saying that a network vulnerability scan helps tremendously with identifying and closing down vulnerability gaps.
- National Institute of Standards and Technology (NIST) – NIST is not a regulated compliance but instead a framework for companies to follow in order to develop and mature their cyber security programs. As such, many CISOs choose to incorporate the NIST framework into their own programs to strengthen security controls. Vulnerability scans are typically required quarterly or monthly depending on the NIST framework being followed: 800-171, 800-53, etc.
- Cyber Security Maturity Model Certification (CMMC) – A new standard set by the US government, the CMMC will require all Department of Defense (DoD) contractors and it’s vendors to meet and maintain a set of cyber security processes and standards by 2021. The model is still being revised, however, it vulnerability scans may be required weekly up to quarterly depending on auditor requirements.
Major Infrastructure Changes, Software Deployment, Or Patches
Ensuring adequate security after any major infrastructure, software, or patch deployment is not easy. Whether it be transitioning to another email provider, implementing a new CRM, or purchasing new networking equipment, there’s a lot of diligent work to be done without corrupting the everyday flow of business activities.
Not only will the new implementation need to be functional, but it also must be secure. Performing a network vulnerability scan will ensure that nothing is missed in the new implementation.
Conclusion
Companies perform network vulnerability scans on a weekly, monthly, quarterly, biannual, or annual basis. This continual evaluation of your business’ intellectual assets, applications, connectivity, servers, and users, allows the cyber security team to focus on patching any risk profiles in the network. They also provide a summarized picture of your security posture.
Each scan should be performed by a qualified security professional who is capable of properly configuring scans and identifying vulnerabilities during the assessment phase. Finally, network vulnerability scans will help you will your compliance efforts and ensure that any major changes in your infrastructure, software, and unpatched systems are done safely and responsibly.
Now you’ll be well on your way in showing auditors and clients that your company is not just ticking checkboxes along the way, but that you are actually staying proactive about your security measures. The safer you are, the more reliable your business becomes, and of course, you will make those auditors very happy.
Related Articles
- How Often Should You Perform A Penetration Test?
- 5 Ways To Protect Your Business From Most Cyber Attacks
- Vulnerability Scans VS Penetration Tests: What’s The Main Difference?
- External VS Internal Network Penetration Tests: What’s The Difference?
- 50 Free Cyber Security Policy Templates To Secure Your Network