5 Proven Network Security Tips For Small Business
While it’s true that enterprise companies are targeted by cyber attacks daily it’s actually small businesses that face the most risk of loss.
This is because threat actors view small businesses as easy targets as they often do not invest in network security in ways that financial institutions or technology companies do.
In this article, I’m going to share 5 ways to protect your small business from the most common cyber attacks. When it comes down to securing your business these are the bare minimum steps you should be taking.
Article Navigation
What Steps Can You Take To Protect Your Business From Cyber Attacks?
In short, small businesses can protect themselves from most cyber attacks by developing and enforcing security policies, implementing security awareness training, installing spam filters and anti-malware software, performing routine network vulnerability scans, and conducting penetration tests.
What Is Security Worth To You?
Some of the most robust systems employ hundreds of security professionals to maintain their network security. These organizations can afford to deploy host-based network intrusion prevention/detection systems and SSL decryption servers.
Security at all costs, right? Unfortunately, security costs something and depending on the solution the resource costs scale quickly.
Another point worth mentioning is that by adding some layers of security, such as encrypting all data fields in a database, you slow down an employee’s access to that data because it requires additional resources and time to decrypt.
While network security is an ever evolving discipline the following 5 methods below will help mitigate exposure to the most common types of network vulnerabilities.
1. Develop Cyber Security Policies
Cyber security policies provide a road map to employees of what to do and when to do it, and who gets access to systems or information. Policies are also required for compliance, regulations, or laws.
A few examples of cyber security policies include:
- Password recovery policy – The purpose of the password recovery policy is to establish a standard for creation of strong passwords and the protection of those passwords.
- Security response plan policy – The purpose of the security response plan policy is to establish the requirement that all business units supported by the Infosec team develop and maintain a security response plan.
- Server audit policy – The purpose of the server audit policy is to ensure all servers deployed at the company are configured according to the company security policies.
You can access our library of 50 cyber security policy templates for free to develop policies to protect your business from cyber attacks.
Start With A Vulnerability Risk Assessment
Protecting your business from a cyber attack comes down to your tolerance for risk. In other words, what are you trying to protect and what are you willing to spend to protect it?
Performing a vulnerability risk assessment is a critical first step in determining the level of investment that should be made into cyber security.
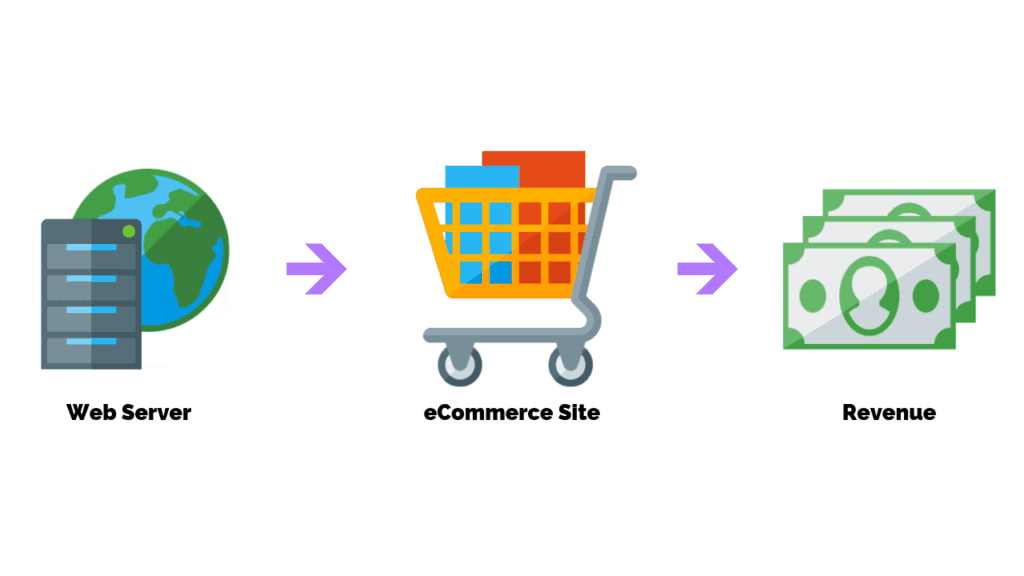
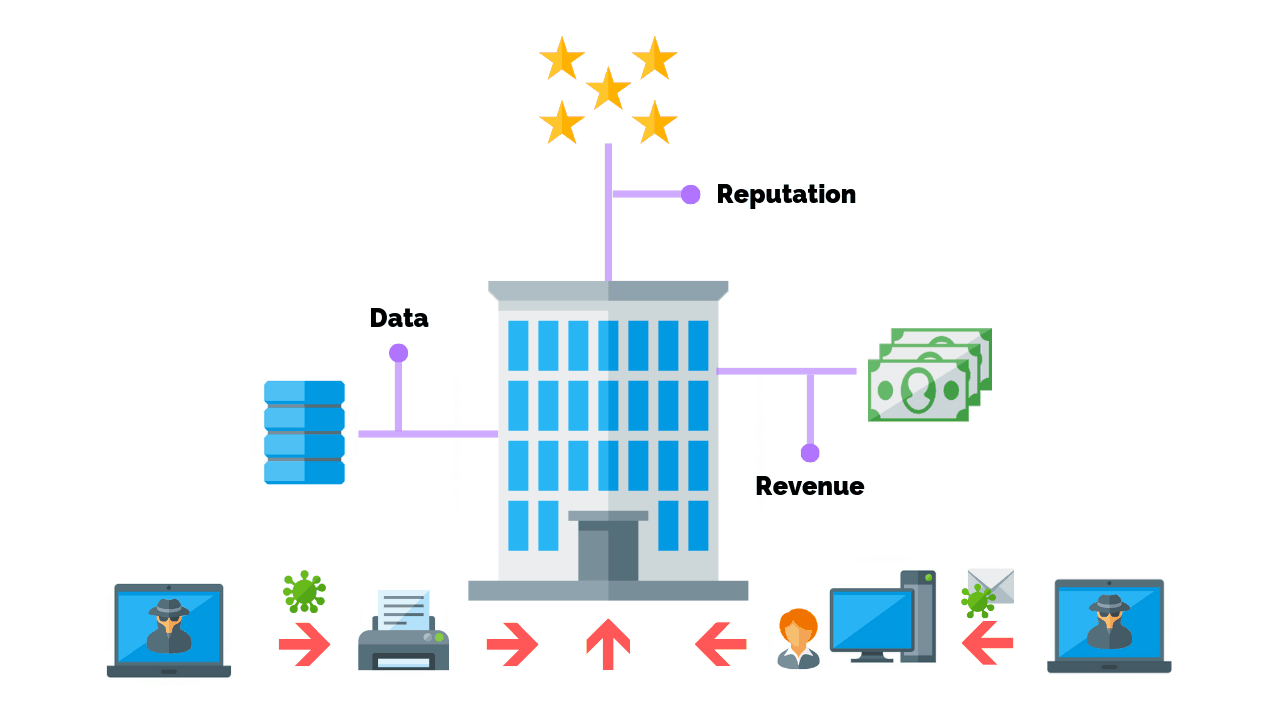
Imagine you have web server that hosts one of your eCommerce sites that earns $1 million in revenue per month.
Now, picture the worst case scenario.
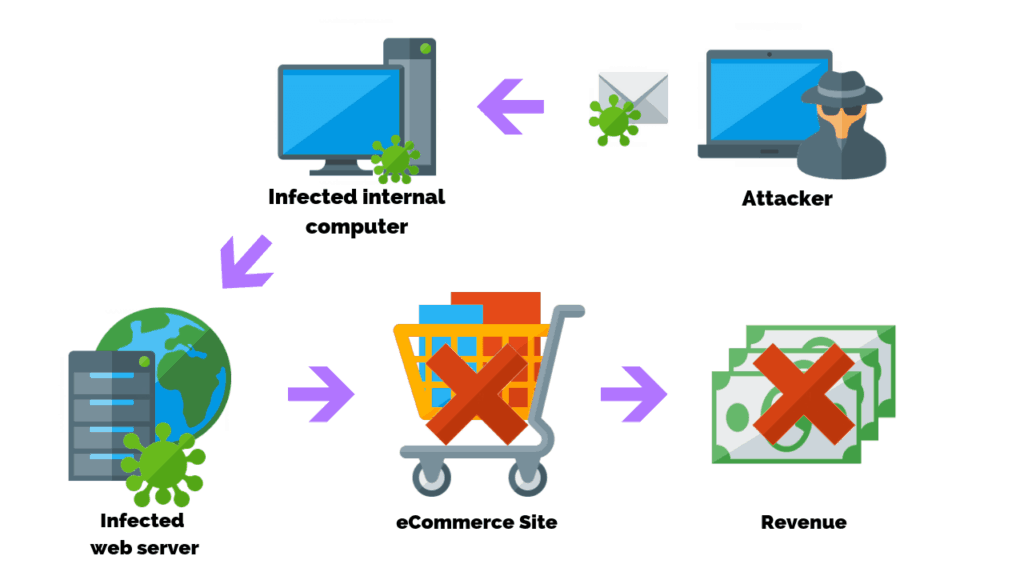
A hacker sends infected malware to an internal computer that has access to the web server. The attacker then deploys the malicious code taking the site down.
- What would be the impact to your business if the site was down for 1 week?
- What would the cost be to recover your systems and get the site operational again?
- What is the cost to your business’s reputation?
- Was the attack on the web server a distraction and the main goal your customer’s data?
Cyber risk assessments and security policies cover these scenarios to clearly define the actions your business will take in the event of a security breach. When well defined, these policies can reduce costs associated to cyber attacks as well as mitigate or prevent them altogether.
2. Implement Security Awareness Training
Internal users are the single biggest threat to a company’s network security, which is why it’s not surprising that 98% of cyber attacks rely on social engineering.
Fortunately, security awareness training and education has proved to be one of the most effective tools to mitigate against social engineer attacks. Awareness training informs and educates users on how to identify and report cyber attacks or threats.
It’s often recommended that this training be done in person and should be conducted at least once per year. While this may sound expensive to gather everyone, consider the alternative of losing all of your data to be more costly.
Security awareness training software, like KnowBe4, is a popular solution used to send phishing email simulation tests. Email campaigns are designed to mimic a socially engineered attack and delivered randomly to users within the network.
If a user clicks on a link or enters their credentials (username and password) they’re redirected to a page notifying them of the phishing exercise.
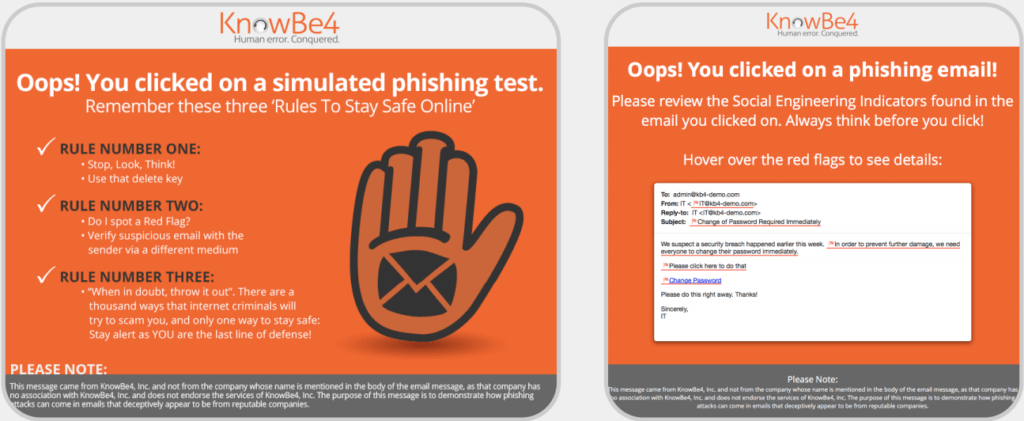
The user is then required to take remedial training to prevent the action from happening again. Dashboards graphically display the data from the tests for system administrators to report on. It’s important to note that physical security should also be evaluated as social engineering attacks are not always delivered remotely.
3. Install Spam Filters And Anti-Malware Software On Mail Gateways
Emails are the primary method for delivering malware and socially engineered attacks. While employees do have anti-virus and anti-malware software installed on their workstations, adding them to your mail servers is recommended as part of a defense in depth approach.
Setting up a spam filter is a balancing act. On one hand the network administrator wants to block all malicious traffic. On the other hand if the filters are too aggressive then legitimate traffic gets blocked and end users start to complain.
After 2-3 weeks of use a baseline for the network can be established and further adjustments are made.
How Do Spam Filters And Anti-Malware Software Work?
Spam filters block traffic at the source by using global threat dictionaries that lists known malware signatures. If a known signature is detected as an attachment in an email, then the threat is block transparently from the user’s perspective.
The idea is the less spam traffic that gets through to the end user then the less likely the chances are malicious links will be clicked.
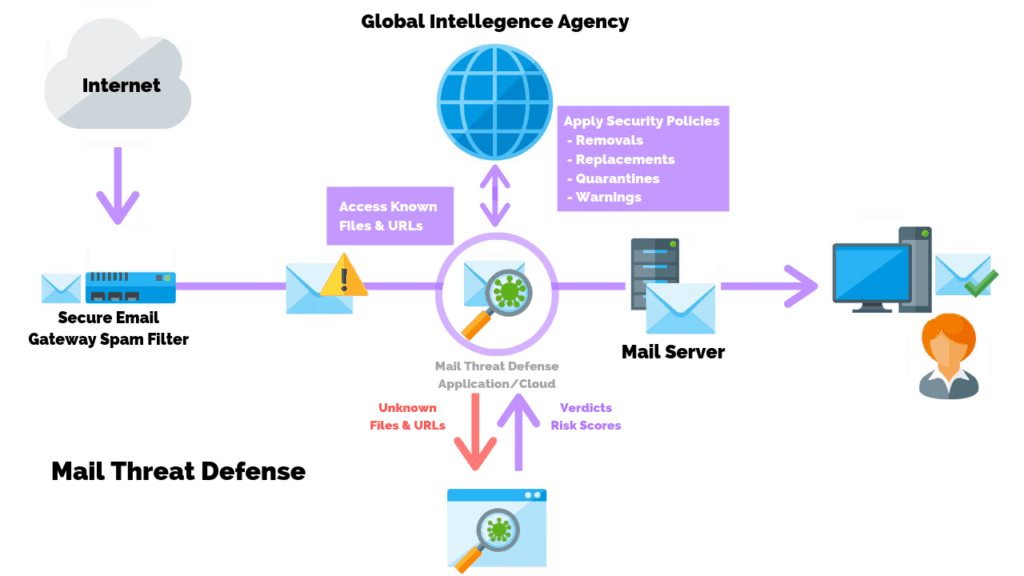
The picture above shows how a spam filter might be set up on your mail server.
- An external request sends, passes through a web server’s firewall, and reaches the filter.
- The spam filter detects a suspicious file or URL attached and flags the email.
- The attachment is scanned and compared against a threat dictionary of known threats.
- The email is then opened in a sandbox environment to confirm its safety to the user.
- The email is forwarded to the mail server and then to the end user’s mailbox.
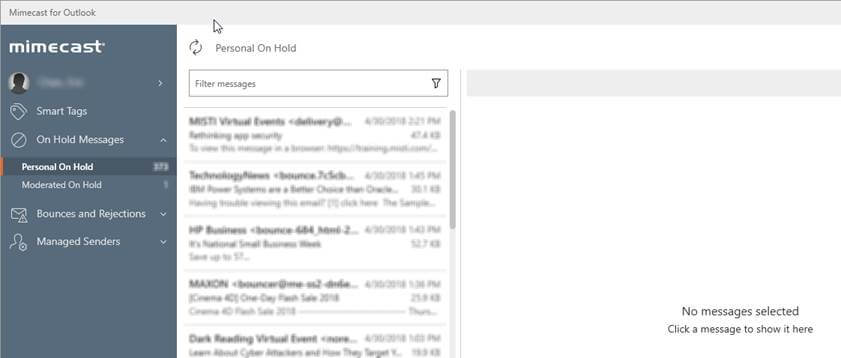
Systems like Mimecast provide spam filtering and anti-malware capabilities. Users are given a “digest” of emails that have been sent to their account. Users can then choose to block, confirm, or always allow an individual email or an entire domain.
4. Perform Network Vulnerability Scans And Assessments
Performing routine network vulnerability scans are a great way to test security controls in your network, and may be performed internally or externally.
The goal of a network scan is to identify known vulnerabilities, lack of security controls, and common misconfigurations.
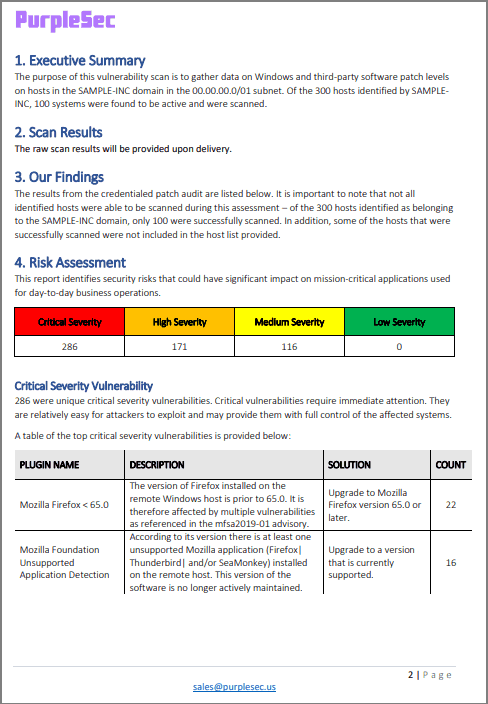
Network vulnerability scanners, like Nessus, are used to scan ports, analyze protocols, and map a network. This provides network administrators with detailed information about which hosts on a network are running what services.
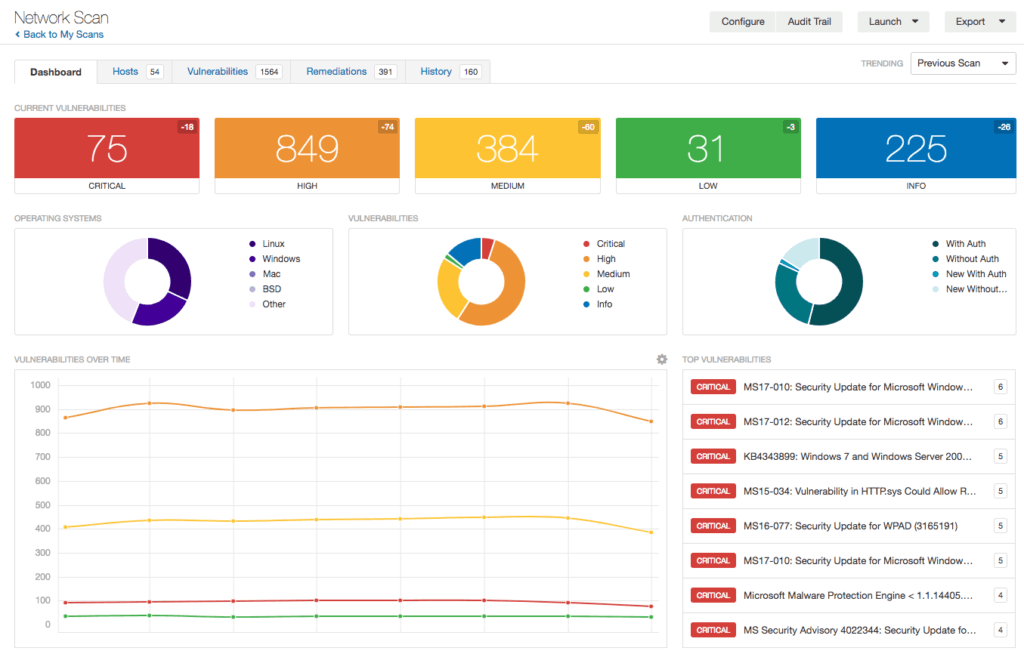
Most scanners will display the information collected in a dashboard listing each vulnerability found and it’s severity. In addition to providing the raw scan results, most vulnerability scanning services include an assessment report consisting of a remediation plan to resolve at risk systems.
Vulnerability scans can be performed weekly, monthly, quarterly, or annually depending on the type of data you store as well as compliance factors.
5. Conduct Penetration Testing
Your business can develop the best policies, scan the network every week, and patch systems daily, but you will never be 100% vulnerability free. Unless your system is truly stress tested there’s no way for you to determine if the security measures in place are adequate.
Penetration testing is a simulated attack against a network designed to test an IT security system. These pen tests are typically conducted by 3rd parties who search for vulnerabilities to exploit and provide recommendations on improving security measures.
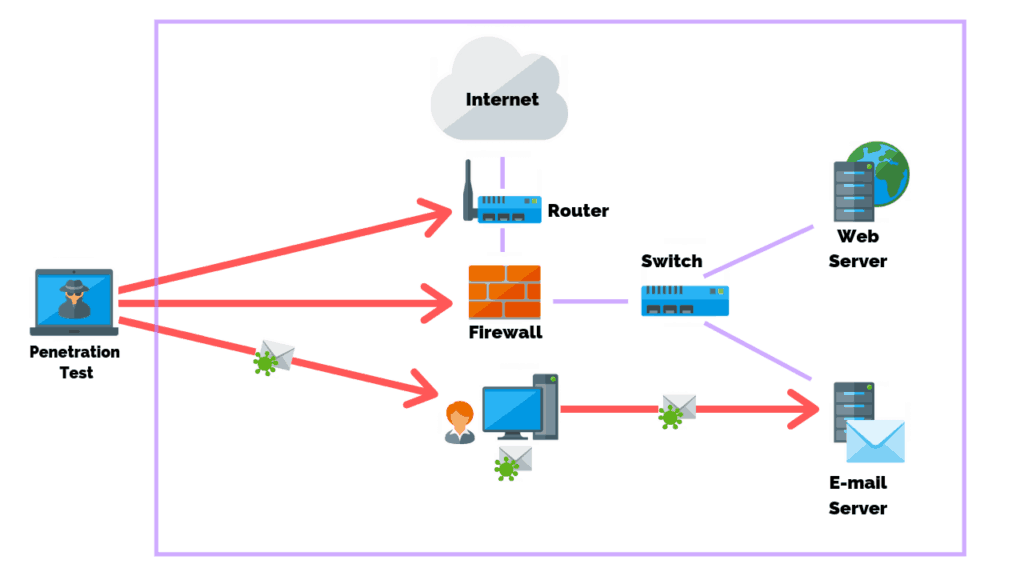
Penetration tests are typically performed 1-2 times per year. This is in part due to cost, but also the potential impact to the business due to how intrusive penetration tests can be. However, certain compliance adherence, industries, regulations, and laws clearly define their requirements for penetration testing.
In most cases are penetration test is a step beyond what is expected for small and mid-sized businesses. If the basics above haven’t been covered then your network will be torn to shreds. The end result will be you paying $20,000 for information you already knew.
Conclusion
Network vulnerabilities are always at threat of being compromised as malicious actors seek to find new ways to exploit and gain access into your business’s system. Fortunately, there are a number of steps you can take to protect your business from a cyber attack including: Developing and enforcing cyber security policies, implementing security awareness training, adding an email spam filter and anti-malware software to your mail server, performing routine vulnerability scans, and conducting penetration tests.
Related Articles
- How Often Should You Perform A Network Vulnerability Scan?
- 19 Cyber Security Healthcare Statistics You Need To Know
- Vulnerability Scans VS Penetration Tests: What’s The Main Difference?
- What Are The Most Common Types Of Network Vulnerabilities?
- Privilege Escalation Attacks: Everything You Need To Know