How To Conduct Vulnerability Assessment In 8 Steps
Learn about PurpleSec’s fully managed vulnerability management services.
Let’s be honest, no business wants to expose itself to risk. Or, worse yet, be the headline story of the latest cyber attacks.
According to one survey from the Ponemon Institute, 60% of breaches in 2019 involved unpatched vulnerabilities.
One way to mitigate this risk is by performing routine vulnerability assessments.
There are 8 steps to performing a network security vulnerability assessment, which includes: conducting risk identification and analysis, developing vulnerability scanning policies and procedures, identifying the type of vulnerability scan, configuring the scan, performing the scan, evaluating risks, interpreting the scan results, and creating a remediation and mitigation plan.
In this article, I’m going to break down each of these steps to show you exactly how to perform a vulnerability test for your organization. By the end, you will have a better understanding of the complete vulnerability assessment process and what you need to do in order to lay the foundation for a successful cyber security program.
Article Navigation
- What Is A Vulnerability Assessment?
- What Are The Benefits Of Vulnerability Assessments?
- Steps To Performing A Vulnerability Assessment
- Step 1: Conduct Risk Identification And Analysis
- Step 2: Vulnerability Scanning Policies and Procedures
- Step 3: Identify The Types Of Vulnerability Scans
- Step 4: Configure The Scan
- Step 5: Perform The Scan
- Step 6: Evaluate And Consider Possible Risks
- Step 7: Interpret The Scan Results
- Step 8: Create A Remediation Process And Mitigation Plan
What Is A Vulnerability Assessment?
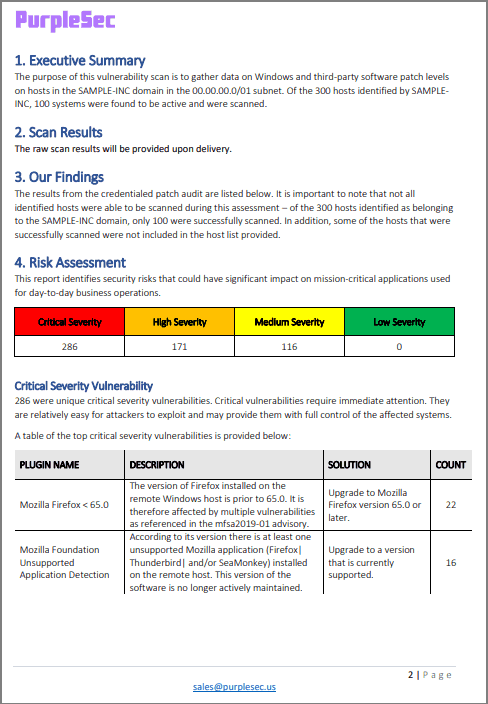
A vulnerability assessment is a process of identifying security vulnerabilities in systems, quantifying and analyzing them, and remediating those vulnerabilities based on predefined risks. Assessments are an essential part of a holistic security program and is cited by many industry standards and compliance regulations.
The vulnerability assessment example below identifies and categorizes vulnerabilities found on a network.
A security expert conducts vulnerability analysis of the network scans to prioritize threats identified. From this, an action plan can be created with steps to remediate vulnerabilities. For example, maintaining up to date patches and implementing a patch management procedure may be a valid recommendation.
Read More: How To Develop & Implement A Network Security Plan
Vulnerability Assessment Pricing & Frequency
Vulnerability assessment costs vary, but you can expect to pay between $2,000 – $4,000 per report. The complexity of the network and the goals of the assessment often determine the cost of a scan.
Many security professionals consider it best practice to perform vulnerability assessments at least quarterly, however, there are a number of factors to consider including compliance, changes in infrastructure, and business needs.
With the growing threat landscape, it is not uncommon for organizations to adopt a continuous vulnerability management solution.
What Are The Benefits Of Performing A Vulnerability Assessment?
At this point you might be asking yourself:
“Why are network vulnerability assessments important?”
There is a wide range of benefits associated with performing vulnerability assessments, especially considering the rise in cyber attacks occurring in the past few years. Only by facilitating identification, analysis, and remediation of risks and vulnerabilities, can a business realize the full value the vulnerability assessment process can provide.
The benefits of performing a network vulnerability assessment are:
Closing Down Security Gaps
Closing gaps in your network’s security is most commonly referred to as system hardening. This is a process of creating more secure systems by decreasing the attack vector that a malicious actor can exploit.
Some of the main steps of system hardening include closing down unnecessary ports and services, updating outdated OS and software and dedicating a separate server for every major service. Vulnerability assessments, more specifically vulnerability scans, help you to efficiently identify possible vectors of attack and help you close them down.
Getting Compliant
Something that every company strives for is becoming compliant with certain standards and regulations because it makes it more competitive in the market. Depending on the geographical location and the industry a certain company operates in, the following are some of the main compliance standards that companies strive to achieve:
- HIPAA – Health Insurance Portability and Accountability Act
- PCI DSS – Payment Card Industry Data Security Standard
- GDPR – General Data Protection Regulation
- ISO 27001 – information security standard from the International Organization for Standardization
- SOX – Sarbanes-Oxley Act
- FISMA – Federal Information Security Management Act of 2002
- GLBA – Gramm–Leach–Bliley Act
To add, not all of the above compliance standards require the existence of a vulnerability assessment process. However, the process of becoming compliant is almost impossible without an assessment.
Maintaining Strong Security
Decreasing the likelihood of a successful cyber attack is something that most companies struggle with. Finding ways to keep security defenses efficient in preventing cyber attacks that result in a compromised system or a breach is a daunting task.
Performing routine vulnerability assessments provide the best bang for your buck in terms of value in identifying and mitigating attacks. Considering that most companies have tight cyber security budgets, implementing assessments into your security policies should be a no brainer.
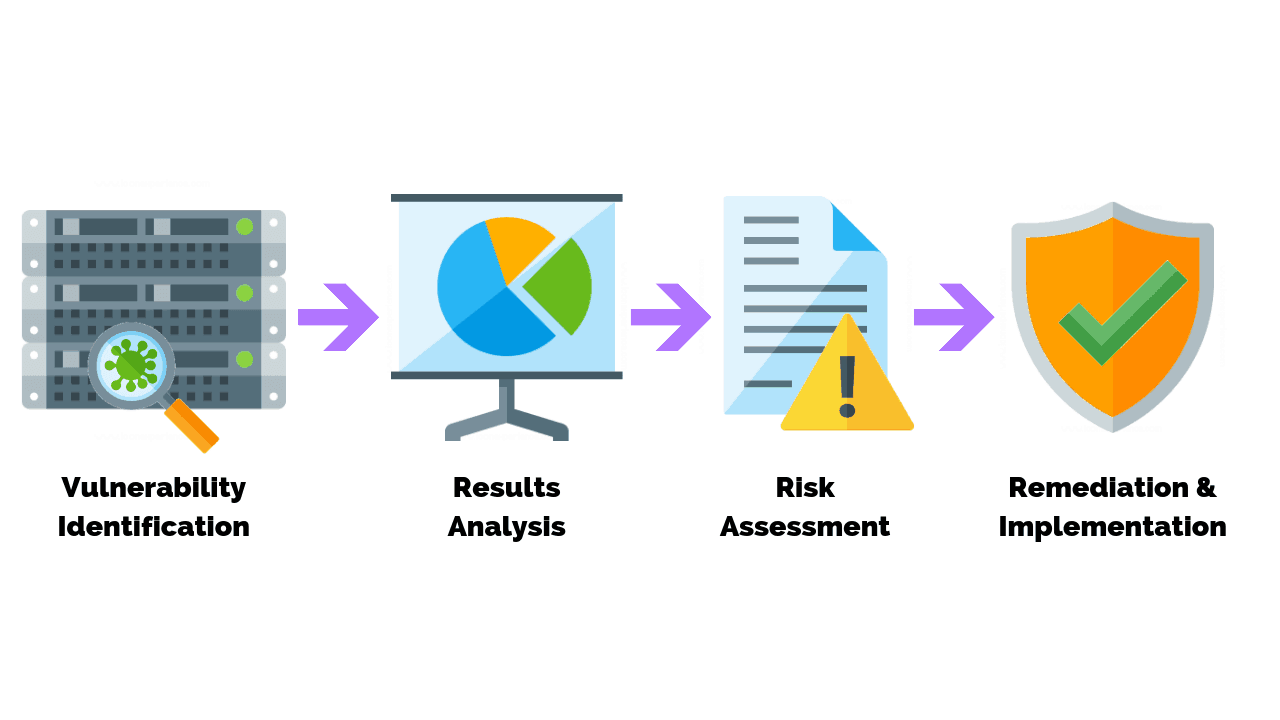
What Are The Steps In The Vulnerability Assessment Process?
The following are action points divided into three main stages that define a mature vulnerability assessment process:
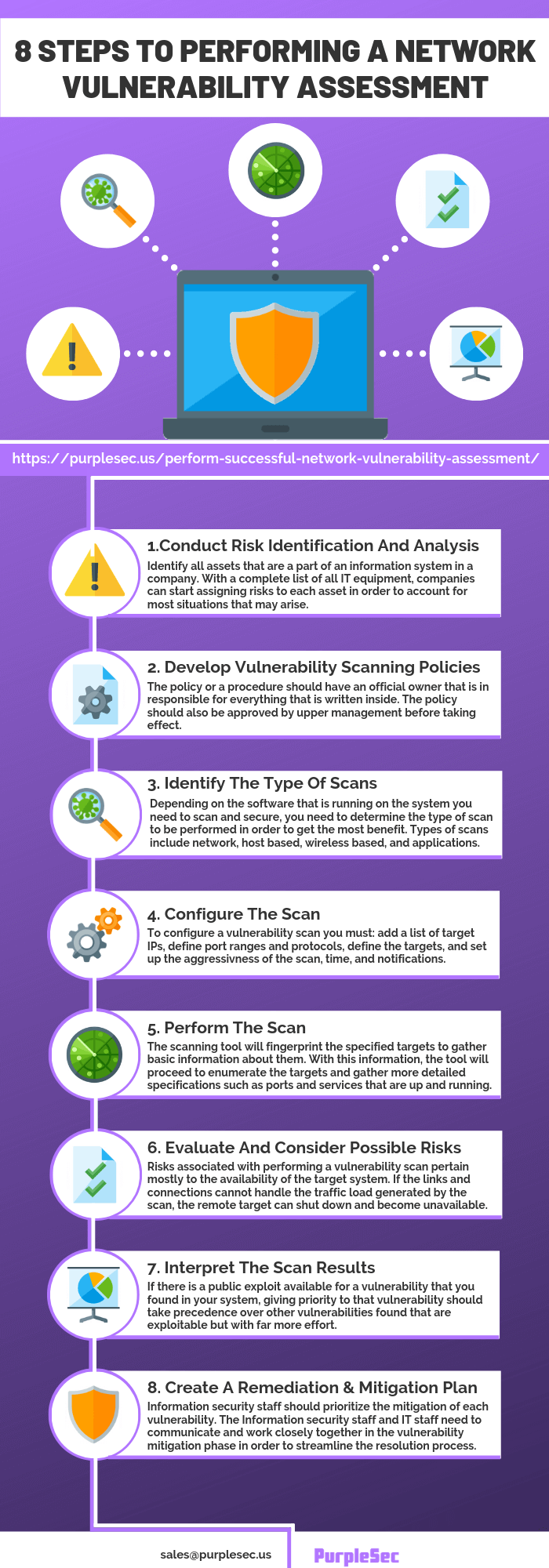
Share this Image On Your Site
Risk Identification and Analysis – The risk identification and analysis process starts with identifying all assets that are a part of an information system in a company. With a complete list of all IT equipment, companies can start assigning risks to each asset in order to account for most situations that may arise.
Afterward, assigning value and performing the analysis will determine the actual risk each asset faces. With risks identified and analyzed, the vulnerability assessment process begins to take shape and the focus slowly shifts to assets with the most amount of risk.
Vulnerability Scanning Policies and Procedures – Written policies and procedures are a backbone of every major action that is planned to be taken. Thus, all activities performed should be within the boundaries of those policies and procedures.
Vulnerability scanning isn’t any different. By structuring the whole process within a policy or a procedure, you will have a determined set of rules and steps that need to be taken and points that specify forbidden behavior.
Needless to say, prior to initiating any vulnerability scan, there should be existing policies and procedures that address the entire process of the scan.
Vulnerability Scanning – Depending on the part of the system you wish to scan, vulnerability scans are divided into two categories, external and internal. External scans encompass all publicly available resources, while internal scans target all internal assets that are inaccessible from the internet.
To add, depending on who is conducting the vulnerability scan, it can be classified as an in-house scan or as a 3rd party scan. Vulnerability scans are typically performed by qualified security staff and configured in various tools that are available as a paid software solution or in an open-source form.
Step 1: Conduct Risk Identification And Analysis
 Identifying risks for each asset and possible threats they face is a complex task. The most important thing is to structure the process well so that nothing important slips through the cracks. Companies can accomplish this by structuring their asset registers with added columns for threats and vulnerabilities.
Identifying risks for each asset and possible threats they face is a complex task. The most important thing is to structure the process well so that nothing important slips through the cracks. Companies can accomplish this by structuring their asset registers with added columns for threats and vulnerabilities.
This way, you will have a centralized document with all the necessary information needed. After you assign threats and vulnerabilities to your assets, you can begin the analysis phase where you assign risks to assets by determining the impact and likelihood of each threat materializing.
Once complete, you can finally focus on prioritizing assets that have the highest risk assigned and those most critically affected by known weaknesses or vulnerabilities.
Step 2: Vulnerability Scanning Policies and Procedures
 In order to have a structured and successful scanning methodology, policies and procedures must exist in order to have a pre-determined course of action needed to be taken. This includes all aspects of vulnerability scanning.
In order to have a structured and successful scanning methodology, policies and procedures must exist in order to have a pre-determined course of action needed to be taken. This includes all aspects of vulnerability scanning.
For starters, the policy or a procedure should have an official owner that is in responsible for everything that is written inside. The policy should also be approved by upper management before taking effect. Defining the frequency of scanning is also important due to compliance adherence.
From a technical perspective, everything regarding the vulnerability scan configuration and functionality should be emphasized and written down. The document should also include steps to be taken after the scan is complete.
The most important factors are the types of scans that will be conducted, the ways the scans will be performed, software solutions used, which vulnerabilities take precedence over others, and steps that need to be taken after the scan is complete.
Step 3: Identify The Types Of Vulnerability Scans
 Vulnerability scanning is a process where vulnerability scanning software is used to identify security weaknesses in information systems. Vulnerability scanning can be performed by network administrators, information security analysts and all technical IT staff that are trained and assigned the function of conducting a vulnerability scan.
Vulnerability scanning is a process where vulnerability scanning software is used to identify security weaknesses in information systems. Vulnerability scanning can be performed by network administrators, information security analysts and all technical IT staff that are trained and assigned the function of conducting a vulnerability scan.
Most malicious hackers attempt to map a network by scanning the system and trying to find possible vulnerabilities to gain unauthorized access to information systems. If malicious hackers you are trying to defend against use vulnerability scanning techniques, you have no choice but to employ them as well in order to stay ahead of their game.
Depending on the software that is running on the system you need to scan and secure, you need to determine the type of scan to be performed in order to get the most benefits.
The most common types of vulnerability scans include:
Network Vulnerability Scans
The most common type of vulnerability scan is a network based scan. This scan includes networks, their communication channels and the networking equipment used in an environment.
Some of the major software and hardware devices that are in the scope of a network scan are hubs, switches, routers, firewalls, clusters, and servers. A network scan will detect and classify all vulnerabilities that it finds on these devices.
Host Based Vulnerability Scans
Host based scan is often misunderstood as being the same as a network scan. Far from the truth, host-based scans address vulnerabilities related to hosts on the network including computers, laptops and servers.
More specifically, this scan investigates the host configuration, its user directories, file systems, memory settings and other information that can be found on a host. This scan focuses more on the endpoints and their internal system setup and functionality.
The importance of a host-based scan is also often overlooked. If neglected, misconfigurations and dormant vulnerabilities that lie in endpoints can mean disaster for your company if a malicious hacker manages to penetrate past your perimeter. By neglecting host-based scans malicious actors are able to move laterally through the system with far more ease.
Wireless Based Vulnerability Scans
In order to conduct a successful wireless vulnerability scan you need to know all the wireless devices that are in your network. Additionally, you need to map out the attributes for each device in order to know how to properly configure the scan.
The next step is to identify any rouge access points that might be in your network and isolate those unknown devices. It is important to remove these devices from your network as they might be listening in on your wireless traffic.
After all of the above, you can start testing your wireless access points and your wireless LAN infrastructure.
Application Based Vulnerability Scans
This type of vulnerability scan is often forgotten and is in the shadows of an application penetration test. Nevertheless, if you are not conducting an application penetration test, scanning your applications for vulnerabilities should be very high on your priority list.
By choosing from a variety of application vulnerability scanning tools, you can automate your security tasks and increase the security of your applications. There is are a variety of tools that you can use, both open-source and commercial in order to conduct a true application vulnerability scan.
Step 4: Configure The Scan
 Even though there are many vulnerability scanning vendors to choose from, the configuration of any scan can still be addressed by identifying general objectives and the type of system you want to scan.
Even though there are many vulnerability scanning vendors to choose from, the configuration of any scan can still be addressed by identifying general objectives and the type of system you want to scan.
To configure a vulnerability scan you must:
- Add A List Of Target IPs – The IP addresses where the target systems are hosted need to be inputted into the vulnerability scanning software in order for a scan to be performed.
- Defining Port Range And Protocols – After adding the target IPs it is important to specify the port range you want to scan and which protocol you wish to use in the process.
- Defining The Targets – In this step, you need to specify if your target IPs are databases, windows servers, applications, wireless devices etc. By making your scan more specific, you will get more accurate results.
- Setting Up The Aggressiveness Of The Scan, Time And Notifications – Defining how aggressive your scan will be can influence the performance of the devices you are going to scan. To avoid any downtime on the target systems, it is recommended to set up a scan to be executed at a certain time, usually non-business hours. Additionally, you can also setup to receive a notification when the scan is complete.
Step 5: Perform The Scan
 After determining the type of scan you want to conduct, and after setting up the configuration of the scan, you can save the configuration and run as desired. Depending on the size of the target set and the intrusiveness of the scan, it can take minutes to hours for it to complete.
After determining the type of scan you want to conduct, and after setting up the configuration of the scan, you can save the configuration and run as desired. Depending on the size of the target set and the intrusiveness of the scan, it can take minutes to hours for it to complete.
Each vulnerability scan can be divided into three phases:
- Scanning
- Enumeration
- Vulnerability Detection
In the scanning phase, the tool you are using will fingerprint the specified targets to gather basic information about them.
With this information, the tool will proceed to enumerate the targets and gather more detailed specifications such as ports and services that are up and running. Finally, after determining the service versions and configuration of each target IP, the network vulnerability scanning tool will proceed to map out vulnerabilities in the targets, if any are present.
Step 6: Evaluate And Consider Possible Risks
 Risks associated with performing a vulnerability scan pertain mostly to the availability of the target system. If the links and connections cannot handle the traffic load generated by the scan, the remote target can shut down and become unavailable.
Risks associated with performing a vulnerability scan pertain mostly to the availability of the target system. If the links and connections cannot handle the traffic load generated by the scan, the remote target can shut down and become unavailable.
When performing a scan on critical systems and production systems, extra caution should be exercised, and the scan should be performed after hours when the traffic to the target is minimal, in order to avoid overload.
Step 7: Interpret The Scan Results
 Having qualified staff members configuring, performing and analyzing the results of a vulnerability scan is most important. Knowledge of the scanned system is also important in order to properly prioritize remediation efforts. Even though each vulnerability scanning tool will prioritize vulnerabilities automatically, certain types of vulnerabilities should be given a priority.
Having qualified staff members configuring, performing and analyzing the results of a vulnerability scan is most important. Knowledge of the scanned system is also important in order to properly prioritize remediation efforts. Even though each vulnerability scanning tool will prioritize vulnerabilities automatically, certain types of vulnerabilities should be given a priority.
For example, remote code execution vulnerabilities should take precedence over possible DDOS and encryption vulnerabilities. It’s important to consider the likelihood and the effort needed in order for a hacker to exploit the found vulnerability.
If there is a public exploit available for a vulnerability that you found in your system, giving priority to that vulnerability should take precedence over other vulnerabilities found that are exploitable but with far more effort.
Step 8: Create A Remediation Process And Mitigation Plan
 After interpreting the results, information security staff should prioritize the mitigation of each vulnerability detected and work with IT staff in order to communicate mitigation actions. The Information security staff and IT staff need to communicate and work closely together in the vulnerability mitigation phase in order to make the process successful and fast.
After interpreting the results, information security staff should prioritize the mitigation of each vulnerability detected and work with IT staff in order to communicate mitigation actions. The Information security staff and IT staff need to communicate and work closely together in the vulnerability mitigation phase in order to make the process successful and fast.
Numerous follow-up scans are usually performed during the back and forth problem-solving between teams until all vulnerabilities that need to be mitigated no longer appear in the reports.
CVSS Database (Common Vulnerability Scoring System)
As mentioned, during the interpretation phase of vulnerability scanning results, qualified staff will read the report that the vulnerability scan produced and decide on the most critical actions to be taken first. The CVSS database can help staff in their decision as it helps with assessing the severity of each vulnerability.
CVSS database is an industry standard for assessing security vulnerabilities that assigns a scoring number to each vulnerability found. It contributes to the prioritization of vulnerabilities and speeds up the remediation process.
Based on a scale of 0 to 10, the CVSS database assigns a number value to each vulnerability depending on various factors such as severity, part of security system affected, public exploit available for a given vulnerability and the complexity of a possible attack.
Conclusion
Vulnerability Assessments are a complex process that is always ongoing. Due to the constant changes in technology in the modern era and with the increased number of successful attacks being launched at all major companies, these assessments have become the backbone for a successful defense of any information system.
It is a process that is heavily based on previously determined assets and their assigned risk due to the need of prioritizing security issues in order to deflect the most damage that could arise from a successful cyber-attack.
The benefits associated with performing regular vulnerability assessments are enormous. From serving as an aid in the process of system hardening to being an integral requirement of most compliance standards, vulnerability assessments also allow you to maintain good security posture and contribute to the success of your company’s cyber security program.
The complex vulnerability scanning tools allow you to build your own configurations and run scans on a vast number of different devices. This gives your business the ability to assess its infrastructure in a sound and complete way, covering all fronts, for network, host, wireless and application level vulnerabilities.
Related Articles