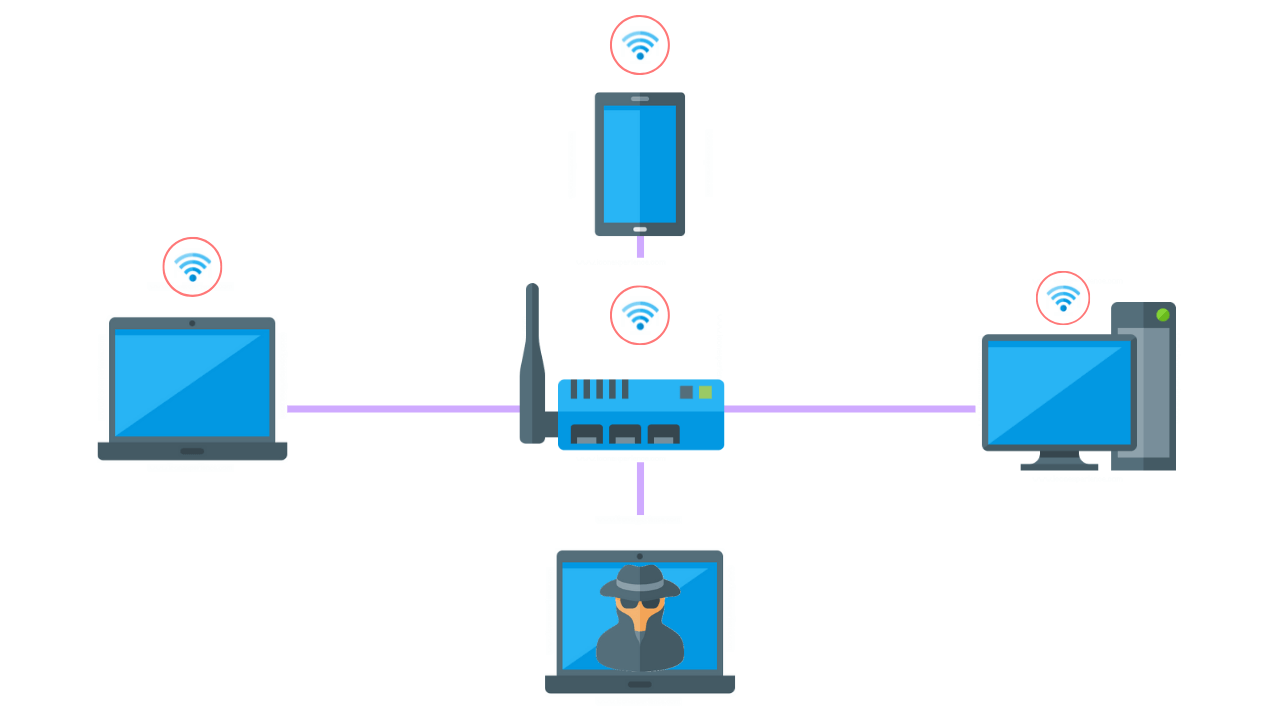
How To Perform A Wireless Penetration Test
Test & Validate Your Security Posture
Our penetration testing services deliver immediate ROI with an agile and efficient solution testing resilience against the latest attacks and APT techniques.
The term WiFi refers to wireless network technology that uses radio waves to establish wireless network connections. Due to the nature of WiFi and its methods for providing network access, malicious hackers often choose to penetrate a company by compromising its WiFi network and corresponding infrastructure devices. Homes are also at risk, especially due to the rise of IoT connected devices and appliances.
Wireless penetration testing is comprised of six main steps including reconnaissance, identifying wireless networks, vulnerability research, exploitation, reporting, and remediation. These tests are performed primarily to maintain secure software code development throughout its lifecycle. Coding mistakes, specific requirements, or lack of knowledge in cyber attack vectors are the main purpose of performing this type of penetration test.
In this article, we will focus our efforts on Wi-Fi penetration testing steps, methods and most popular tools used in the Wi-Fi penetration testing process.
Article Navigation
- What Is A Wireless Penetration Test?
- What Are The Goals Of A Wireless Pen Test?
- Steps To Performing A Wireless Penetration Test
Types Of Penetration Tests |
||
|---|---|---|
 |
 |
 |
External VS Internal |
Network |
Social Engineering |
 |
 |
 |
Physical |
Firewall |
Web Application |
What Is A Wireless Penetration Test?
Wireless penetration testing involves identifying and examining the connections between all devices connected to the business’s wifi. These devices include laptops, tablets, smartphones, and any other internet of things (IoT) devices.
Wireless penetration tests are typically performed on the client’s site as the pen tester needs to be in range of the wireless signal to access it.
Read More: 10 Cyber Security Trends You Can’t Ignore In 2021
What Are The Goals Of A Wireless Pen Test?
Every official penetration test should primarily focus on the vulnerabilities most easily exploited.
This is often referred to as going for the “low-hanging fruit” as these identified vulnerabilities represent the highest risk and are most easily exploitable.
In the case of wifi networks, these vulnerabilities are most often found in wifi access points.
A common reason for this is due to insufficient Network Access Controls and due to the lack of MAC filtering.
If these security controls are not used to effectively increase the security of a WiFi network, malicious hackers gain a significant advantage over the company and can use various techniques and WiFi hacking tools to gain unauthorized access in the network.
Steps To Performing A Wireless Penetration Test
As previously stated, we will focus on the methodology and steps for testing the WiFi network and give examples of certain attacks and tools that will accomplish our goal.
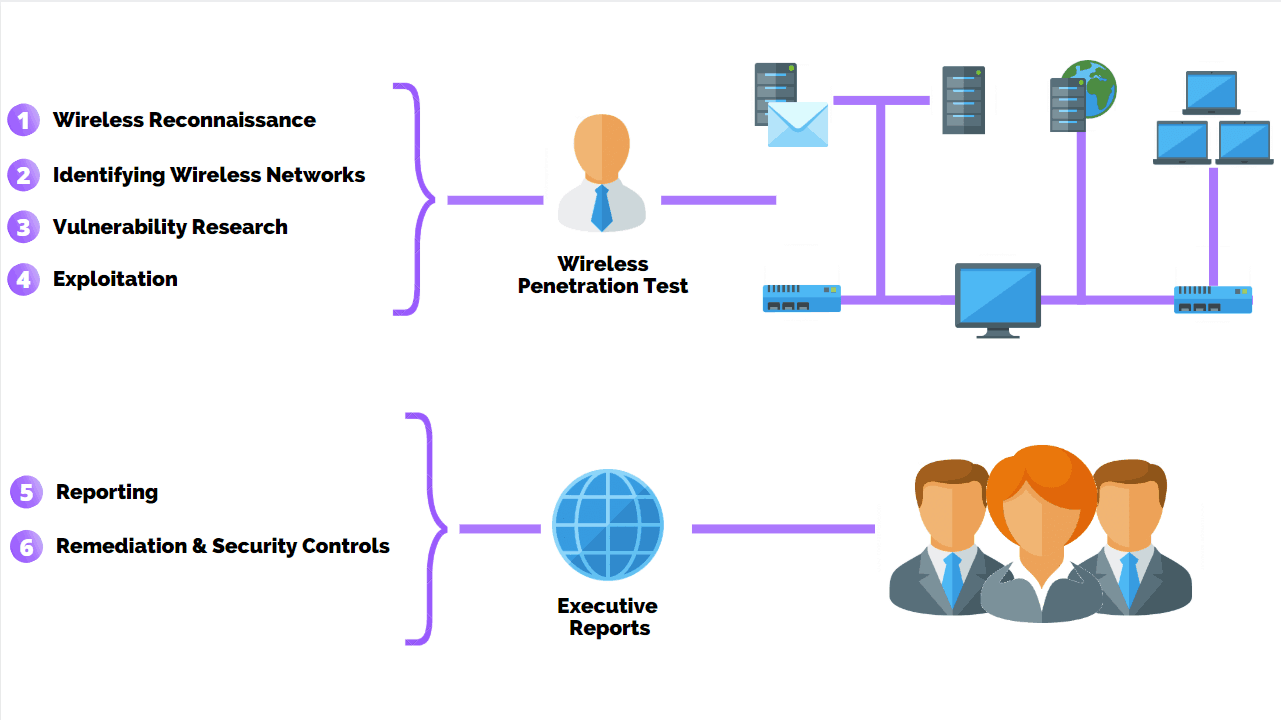
Below is a list of steps that can be sorted in 6 different areas of the penetration test.
Step: 1 Wireless Reconnaissance
Before jumping straight into hacking, the first step in every penetration testing process is the information gathering phase.
Due to the nature of Wi-Fi, the information you gather is going to occur via War Driving. This is an information gathering method that includes driving around a premise to sniff out Wi-Fi signals.
To do this you will require the following equipment:
- A car or any other transportation vehicle.
- A laptop and a Wi-Fi antenna.
- Wireless network adapter.
- Packet capture and analysis software.
Most of the information you gather here will be useful but encrypted as most if not all companies use the latest Wi-Fi protocol: WPA2.
This Wi-Fi protocol protects the access point by utilizing encryption and uses EAPOL authentication.
Step 2: Identify Wireless Networks
The next step in Wi-Fi penetration testing is scanning or identifying wireless networks.
Prior to this phase, you must set your wireless card in “monitor” mode in order to enable packet capture and specify your wlan interface.

After your wireless card starts listening to wireless traffic, you can start the scanning process with airodump in order to scan traffic on different channels.

An important step in decreasing your workload during the scanning process is to force the airodump to capture traffic only on a specific channel.
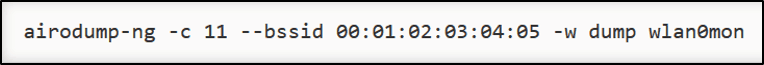
Step 3: Vulnerability Research
After finding wifi access points through scanning, the next phase of the test will focus on identifying vulnerabilities on that access point. Most common vulnerability is in the 4-way handshake process where an encrypted key is exchanged via between the WiFi access point and the authenticating client.
When a user tries to authenticate to a Wi-Fi access point, a pre-shared key is generated and transmitted.
During the key transmission, a malicious hacker can sniff out the key and brute force it offline to try and extract the password.
In order to clarify this most commonly exploited vulnerability, the next section of the article will focus on the pre-shared key sniffing attack and tools used to successfully accomplish the task.
Step 4: Exploitation
We will use the Airplay NG suite tool to accomplish our exploitation efforts by:
- De-authenticating a legitimate client.
- Capturing the initial 4-way handshake when the legitimate client reconnects.
- Running an offline dictionary attack to crack the captured key.
Since we already started capturing the traffic on a specific channel, we will now proceed with the next step.
De-authenticating A Legitimate Client
Since we want to capture the 4-way handshake that occurs when every client authenticates to an access point, we must try and de-authenticate a legitimate client that is already connected.

By doing this, we are effectively disconnecting the legitimate client from the access point and waiting for our previous Airodump -ng commands that we ran, to sniff out the 4-way handshake once the legitimate client starts reconnecting automatically.
Capturing The Initial Handshake
During the process of capturing traffic after the “de-auth” packets you’ve sent, you will be able to see lots of live information regarding the “de-auth” attack running.
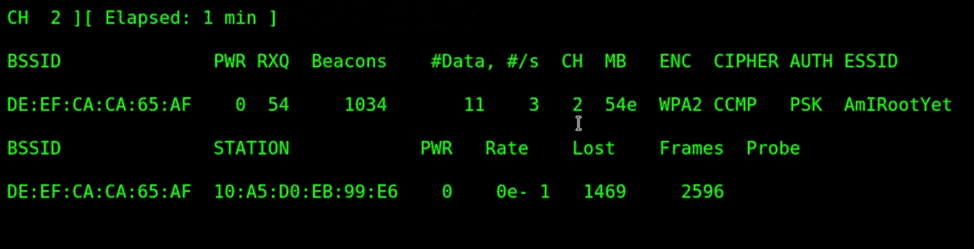
We can see the channel number, time elapsed, BSSID (MAC address), number of beacons and a lot more information.
The time it takes to successfully perform this depends on the distance between the hacker, the access point and the client we are trying to disconnect.
Once the 4-way handshake has been captured, you can save the capture to a “.cap” file.
By saving all of this captured traffic into a “.cap” file, we can quickly input the file in Wireshark – a popular network protocol analyzer tool to confirm that we have indeed captured all 4 stages of the handshake.
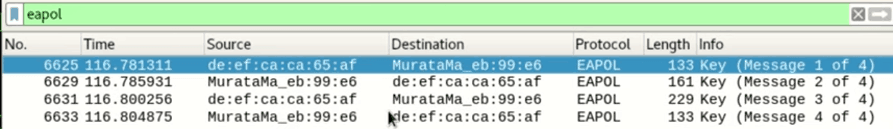
Since we have now confirmed the 4-way handshake packet capture, we can go ahead and stop the packet capturing by typing the following airodump command: “Airmon-ng stop wlan0mon”.
Dictionary Attack On The Captured Key
Our final step in the exploitation phase is to crack the captured 4-way handshake key and extract the password. To do this, we do not even have to use additional password cracking tools such as JohntheRipper or Hydra. We can simply use the Aircrack-ng module of the aireplay-ng suite.
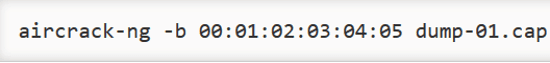
Additionally, you must identify the dictionary you want to use for cracking the key by specifying the file path after the “dump-01.cap” part of the above command.
This command will run the cracking process on target MAC address of the access point utilizing the captured traffic in the .cap file and a specified dictionary.
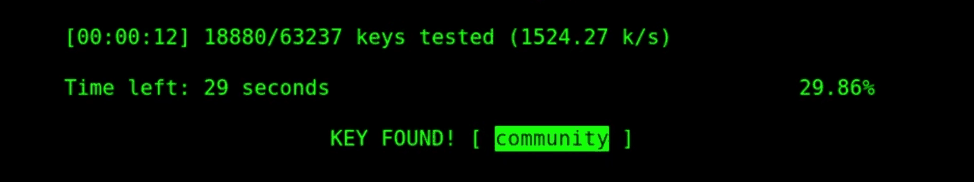
As the end result, we successfully found the password phrase “community.
Other Wireless Attacks
Since capturing keys from the 4-way handshake and brute forcing it offline is one of the most effective ways to gain unauthorized access, we placed the emphasis on this one practical attack.
Other practical attacks on wireless networks include the deployment of a rogue access point within the company.
This attack leverages the use of an unauthorized Wi-Fi access point deployed inside the company buildings.
The main idea is to overpower the signals of a legitimate access point in the company’s network (or use Wi-Fi signal jammers to render the authorized access point inaccessible) and force the employees to connect to the unauthorized access point.
If this runs successfully, an attacker will have control over all the traffic that is passing through that access point.
Step 5: Reporting
Structuring all of your steps, methods and findings into a comprehensive document is the most important step in the work of a penetration tester.
It is highly suggested to document every step of your work, including every detailed finding, so you can have all the necessary details to make your report complete.
Make sure to include an executive summary, detailed technical risks, vulnerabilities you found along with the complete process of how you found them, exploits that were successful and recommendations for mitigation.
Step 6: Remediation And Security Controls
We’ve demonstrated one practical exploit regarding Wireless networks that involves capturing Wi-Fi traffic and the pre-shared key. The attack was successful for many reasons including the lack of MAC filtering controls.
With this control turned on, the malicious hacker wouldn’t have been able to authenticate himself with the same password the legitimate user did.
Since anything can be hacked, the attacker would have to spoof his MAC address that is on the MAC list of approved addresses in order to successfully break in the wireless network.
Having Network Access Control (NAC) solutions in place will mitigate the possibility of having rouge access points in your network.
Additionally, company may consider deploying wireless honeypots – simulated wireless networks that are used for detecting intrusions and analyzing the behavior of malicious hackers.
Conclusion
Wireless networks need just as much security consideration when being deployed and configured in order to keep them secure. Wireless penetration testing is therefore a popular way to determine the realistic security posture of your wireless networks.
Even though it requires a bit more hardware equipment than your usual penetration test, wireless penetration testing Is still performed with software tools often present in the Kali Linux OS with the industry’s most infamous tool for it being Airplay -NG.
We demonstrated a practical way of utilizing Airplay -NG and the results it can give with its powerful set of sub-tools. All that is left for you to do now is try it out on your own (make sure you have consent for whatever and however small of a test you plan to do) and mitigate those vulnerabilities!
Are you ready to work together? Get a no-obligation consultation to meet your penetration testing needs.
Related Articles