How Often Penetration Testing Be Done?
Test & Validate Your Security Posture
Our penetration testing services deliver immediate ROI with an agile and efficient solution testing resilience against the latest attacks and APT techniques.
While every business need is different, it’s best practice to perform penetration tests regularly, 1 – 2 times per year. However, compliance, installation of new networking infrastructure, changes in cyber policies and tolerance to cyber risk all play a role in how often penetration tests need to be performed. Some penetration testing services also offer continuous testing.
In this article, I’ve put together a simple 3 point checklist you can follow to determine how often you should perform a penetration test for your business.
Article Navigation
- Why Should You Perform A Penetration Test?
- What Determines How Often You Should You Perform A Penetration Test?
Why Should You Perform A Penetration Test?
Penetration tests simulate an attack against your network in order to test every aspect of your IT security management system. Through gathering information about a certain target, finding common network vulnerabilities in systems, exploiting them to the fullest and documenting the results is what encompasses every penetration test.
The benefits of performing a penetration test are huge as it provides a unique insight from an attacker’s perspective on the robustness of your system. Depending on the extent of knowledge that a company provides to the penetration tester, they are categorized in multiple ways that define the methodology for each test.
Considering the high costs of certified penetration tests, along with the man hours needed to choose the right vendor, set up plans, and in certain cases, configure internal access for the penetration tester, most companies perform 1 to 2 tests annually.
What Determines How Often You Should You Perform A Penetration Test?
Here’s a 3 point checklist that will help you narrow down you penetration testing requirements:
- Assess your business’s risk to cyber attacks by performing a cyber risk assessment. Focusing on cyber risk assessment will help you identify weak spots, or vulnerabilities, that need to be worked upon.
- Compliance, another huge factor for a penetration test, is the requirements certain certification and standards have that qualify your company to operate legally. These standards are usually industry specific.
- Most companies have a fluid environment and often make changes to critical infrastructure, software, and policies. Depending on the change, a new penetration test may need to be performed to reassess your network’s security and ensure unintended vulnerabilities are identified and resolved.
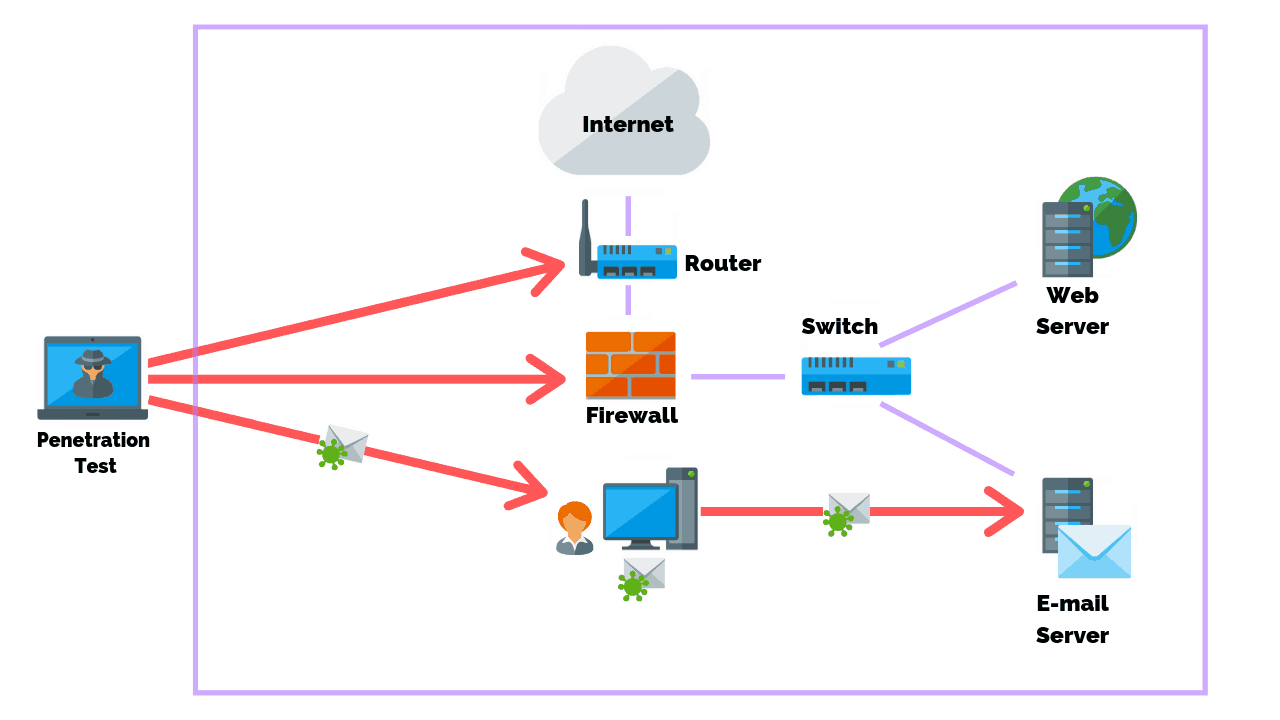
You may also want to consider the type of attack that most aligns with your goals. For example, you would perform an external penetration test when evaluating the defense of your network to an outside attacker. However, if your goal is to test how an attacker would proceed once inside your network, then you would conduct an internal penetration test.
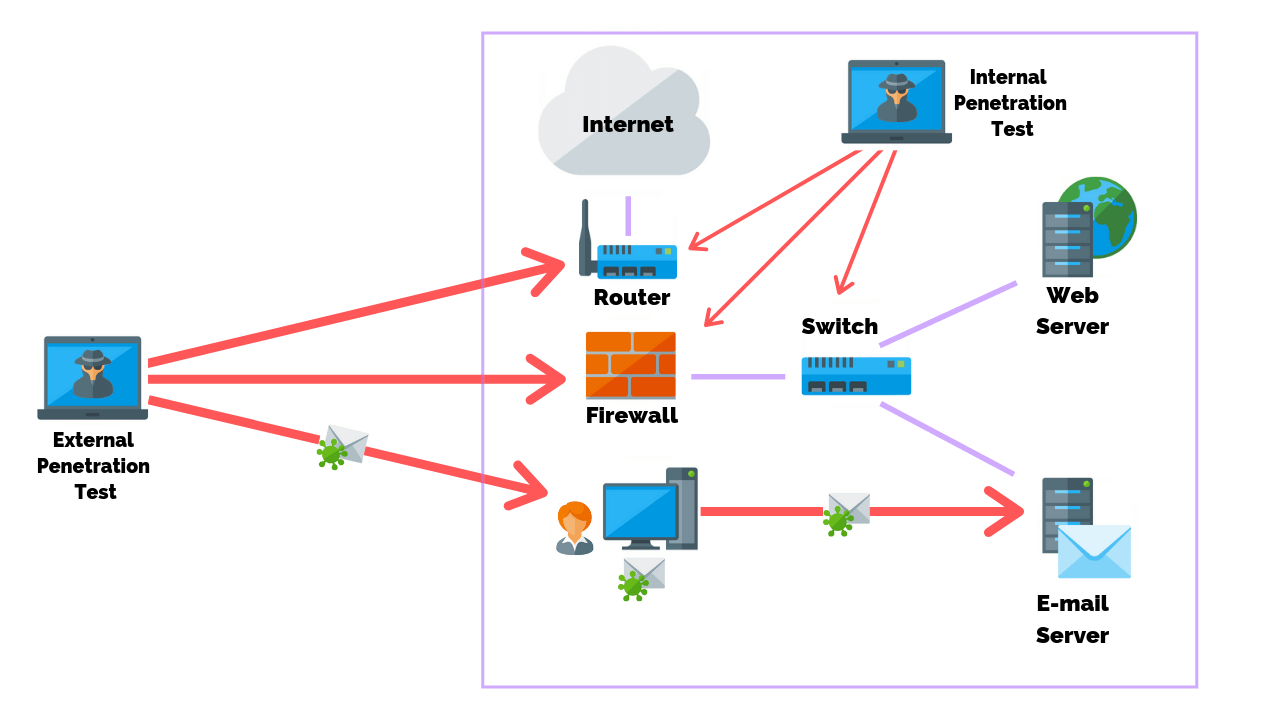
Performing both tests semi-regularly provides the best way to stress test your security defenses and the readiness and responsiveness of your internal security team.
Assess Your Business’s Risk To Cyber Attacks
A cyber risk assessment is part of every company’s risk management strategy, or at least it should be. This is because almost every company relies on some sort of technology or information system to operate.
What Is A Cyber Risk Assessment?
Cyber risk assessment is focused on identification, estimation and prioritization of risks in order to allow safe operation and use of Information systems. The outcome for each type of cyber risk is measured in terms of likelihood and impact matrix.
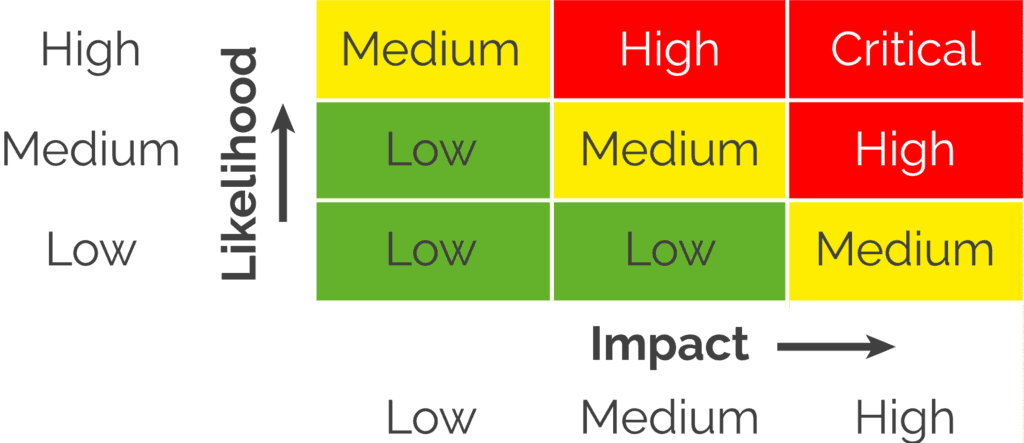
Depending on each company’s structure, business goal and day to day operations, the likelihood of high certainty attacks that would have a high impact on the business should be classified as a critical risk.
This cyber risk assessment matrix should be your go-to guide in helping you prioritize the risks you find.
What Is Your Budget?
Determining your budget for the cyber risk assessment will be crucial for your prioritization of cyber risks and should not be taken lightly. If a company doesn’t invest in proper cyber risk assessment, you cannot expect your defenses to be proper.
Many companies view cyber attacks as an afterthought to running numerous profitable projects, which is a mistake. By planning for cyber safety from day one, and taking into account cyber risk, security and privacy by design will be an achievable term that will significantly contribute to the future success of your company.
What Is The Monetary Impact?
To make things easier, you should prioritize each risk by calculating the potential monetary impact that could arise if that risk becomes a reality.
For example, imagine you have a web server hosting an eCommerce site that generates $1 million in monthly revenue. What would be the impact to your business if a threat actor exploited a vulnerability to the web server and shut it down for 1 week?
Of course, this isn’t always the scenario. If mitigating a certain risk would cost a lot more than the actual damage of a realized risk, mitigating it would be a waste of prioritization. Planning for risks by determining the frequency of attacks and allocating money towards mitigation is the key.
Compliance Requirements
Most companies strive to achieve regulatory compliance in order to show due diligence, attract new customers and retain the old ones. Some compliance standards require companies to be certified in order to allow them to operate, as a successful cyber attack can cause real-life damage to individuals.
Here is a short list of most common compliance standards that require or recommend performing a penetration test:

The Payment Card Industry Data Security Standard (PCI DSS)
Both network and application penetration tests are required by PCI DSS and any other part of a system that can affect the mechanism of the cardholder data. This compliance mandates annual frequency of tests.

Federal Information Security Management (FISMA)
FISMA is a compliance standard relating to government institutions and does not require a penetration test, but puts heavy emphasis on it.

Health Insurance Portability and Accountability Act (HIPAA)
Strictly speaking, a penetration test is not required in order to be compliant, however, a cyber risk assessment is required.

International Organization for Standardization (ISO) 27001
ISO 27001 requires a penetration test to be performed at least annually.

Gramm-Leach-Bliley Act (GLBA)
GLBA act dictates that effective mitigation controls must be in place in order to meet the requirements. Arguably, conducting a penetration test annually will help tremendously in order to achieve this objective.
Changes To Critical Infrastructure, Software, And Policies
Companies make changes to their systems and architecture for a number of reasons.
New cloud vendors are chosen because they offer a better service, old software is decommissioned due to being ineffective and old systems are decommissioned due to 3rd party vendors ending development support.
Some changes are critical to standard business operations such as phones and emails, which is required for reliable communication. In practice, network equipment changes along with new network security software change the environment. Software solutions that deal with access control processes and user management are often changed as well.
Information security policies are one of the core requirements for any functional security system. They define the scope and most of the activities around an information security management system.
Major changes in policy lead to major changes on the information systems which requires a thorough security check. Thus, performing a penetration test around any major changes is highly recommended as it provides you with the most helpful insight into the newly defined system.
Conclusion
Penetration testing strengthens your security posture by providing you with valuable information about what outside malicious actors can see. It is highly recommended to perform penetration tests at least once a year and up to twice a year if any major infrastructure or policy change occurs.
It is very likely that your company is also subject to compliance standards that require a penetration test to be conducted. In this case, you shouldn’t just focus on ticking the box but rather use the opportunity to excel the company in the right direction.
If you happen to be a victim of a security breach, waving a paper of some cheap and basic penetration test will not save you from upset clients. As the saying goes, better safe than sorry.
Related Articles
- How Often Should You Perform A Network Vulnerability Scan?
- Vulnerability Scans VS Penetration Tests: What’s The Main Difference?
- What Are The Different Types Of Penetration Testing?
- What Are The Most Common Types Of Network Vulnerabilities?
- 13 Physical Penetration Testing Methods (That Actually Work)


