Penetration Testing Best Practices
Test the effectiveness of your security controls against a real world threat.
Test the effectiveness of your security controls against a real world threat.
Overview
In this guide, you’ll learn everything you need to know about penetration testing.
This section features articles that will help guide your business towards selecting a vendor to ensure penetration testing best practices are followed.
Recent Articles
Categories
Policy Templates
Recent Articles:
Automated penetration testing is a vulnerability scanning technique that uses software to find security vulnerabilities in networks, cloud infrastructure, websites, and web and mobile applications.
There are many definitions of continuous penetration testing. At PurpleSec, we believe conducting a penetration test at least quarterly means you’re continuously assessing your security posture.

Cloud Penetration Testing is the process of detecting and exploiting security vulnerabilities by simulating a controlled cyber attack on cloud-native systems, where the cloud infrastructure’s security posture is assessed.
A penetration testing policy is a set of formalized guidelines, requirements, and standard operating procedures that serve to define the overall goals, expectations, limits, and methods.
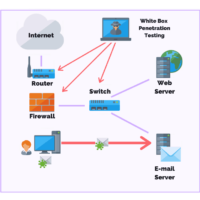
You may need to conduct a white box penetration test if you want to evaluate your application security, wireless security, infrastructure, network security, or physical security in an assumed breach scenario.
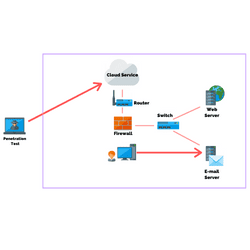
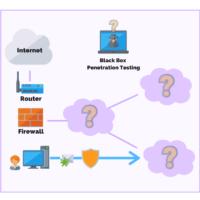
You may need to conduct a black box penetration test if you want to evaluate your application security, wireless security, infrastructure, network security, or physical security in a scenario closest to a real-life attack.
There are a number of types of pen tests that can be performed and understanding the type is critical to a business’s security success.
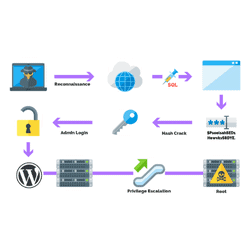
Privilege escalation attacks exploit weaknesses and security vulnerabilities with the goal of elevating access to a network, applications, and mission-critical systems.
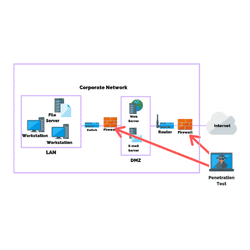
There are 13 steps to firewall penetration testing, which include locating the firewall, conducting tracerroute, scanning ports, banner grabbing…
The 4 main steps in the penetration testing methodology include planning and preparation, scan / assessment, exploitation and data exfiltration, and reporting, cleanup, and destruction of artifacts.
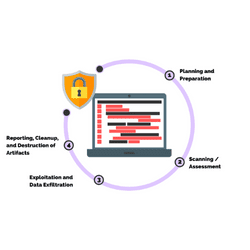
Performing a successful network penetration test includes information gathering and understanding client expectations, reconnaissance and discovery, performing the penetration test, and reporting on recommendations and remediation.
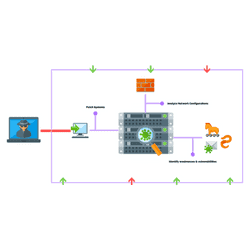
Social engineering penetration testing focuses on people and processes and the vulnerabilities associated with them.
Wireless penetration testing is comprised of six main steps including reconnaissance, identifying wireless networks, vulnerability research, exploitation, reporting, and remediation.
Physical penetration testing exposes weaknesses in physical security controls with the goal of strengthening a business’s security posture.

Web application penetration tests are performed primarily to maintain secure software code development throughout its lifecycle.
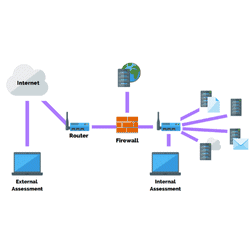
What’s an internet and external pen test? Which one do I need and what’s more important? We explain.
