The different types of penetration tests include network services, applications, client side, wireless, social engineering, and physical.
A penetration test may be performed externally or internally to simulate different attack vectors.
Depending on the goals of each test, a penetration tester may or may not have prior knowledge of the environment and systems they’re attempting to breach.
This is categorized as black box, white box, and gray box penetration testing.
In this article, I’m going to explain the different types of penetration tests, how they work, and why they should be performed. By the end, you will have a better understanding of why penetration tests are an effective layer of defense for any successful cyber security program.
Before we dive into the different types of penetration testing let’s define what a penetration test is.
Sample Network Pen Test Report
What should a penetration test report include? Download our sample report to learn.
What Is Penetration Testing?
A penetration test involves a team of security professionals who actively attempt to break into your company’s network by exploiting weaknesses and vulnerabilities in your systems.
Penetration tests may include any of the following methods:
- Using social engineering techniques to access systems and related databases.
- Sending of phishing emails to access critical accounts.
- Using unencrypted passwords shared in the network to access sensitive databases.
These attempts can be far more intrusive than a vulnerability scan and may cause a denial of service or increased system utilization, which may reduce productivity, and corrupt the machines.
In some cases, you may schedule penetration tests and inform staff in advance of the exercise.
However, this wouldn’t be applicable if you want to test how your internal security team responds to a “live” threat.
For example, red team exercises are often performed without informing staff to test real-world threat scenarios.
In this case, it’s important to inform the blue team lead, CISO, or upper-level management of the exercise.
This ensures the response scenario is still tested, but with tighter control when/if the situation is escalated.
Regardless of the scenario, you should conduct a penetration test with a specific intent and clearly define your wants and needs with the penetration testing team.
For example, you may just finish rolling out a new security program for your business and want to test its effectiveness.
A penetration test can determine if certain objectives of the program have been achieved such as maintaining 99.99% availability during an attack, or ensuring data loss prevention (DLP) systems are blocking would-be attackers from exfiltrating data.
Why Are Penetration Tests Performed?
Penetration testing has become a widely adopted security practice by organizations in recent years.
This is especially true for industries, such as banks or healthcare providers, that store and access sensitive or private information.
While the primary purpose is to expose vulnerabilities or exploit weaknesses, it’s important to note that the main goal of a pen test is often tied to a business objective with an overarching strategy.
For example, Department of Defense contractors must have adequate processes in place to protect Controlled Unclassified Information (CUI) as part of the Cyber Security Maturity Certification (CMMC).
A penetration test is one of many security controls needed to pass auditor requirements depending on the level that the contractor must attain.
On the other hand, a software company’s security goals may vary greatly.
For example, application penetration testing helps to identify flaws and weaknesses within code that could be susceptible to an attack.
Developers then work to create fixes to update the codebase.
Ultimately, the business goals determine the types of penetration testing performed, which we will cover shortly.
Reporting On Findings
Upon completion of the testing phase, a report is created and presented to executive leadership and business owners.
This is the real value of any penetration testing engagement.
This report should provide direction and guidance for reducing exposure to risk while also providing actionable steps toward a resolution.
It’s important to mention that penetration testing reports are customized and tailored to meet a company’s cyber security needs based on:
- How their network is set up.
- Business objectives for performing a pen test.
- What is being tested – software, servers, endpoints, physical controls, etc.
- The value of tangible or intangible assets being secured.
- And much more!
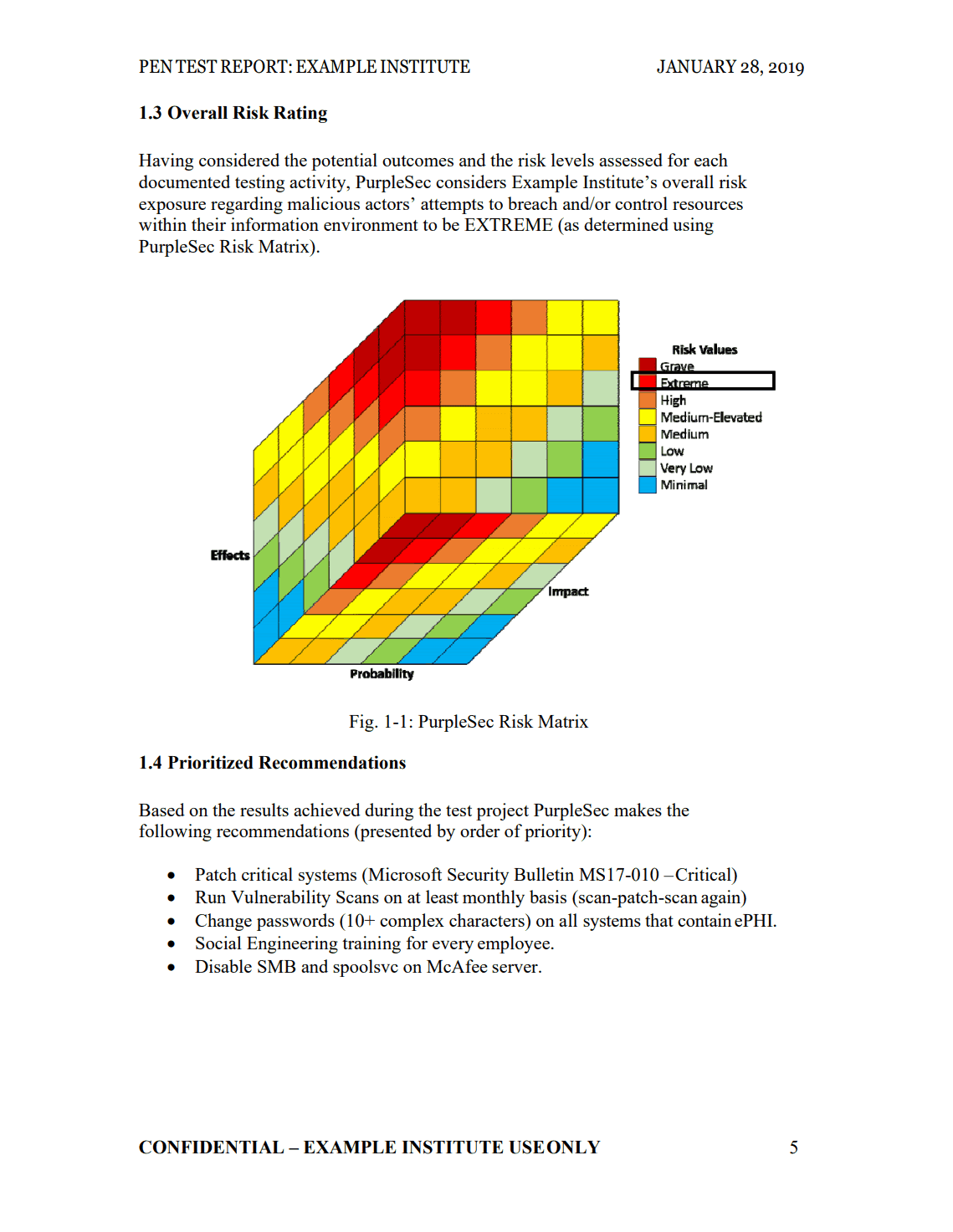
When consulting with vendors, be sure to ask how they plan to present their findings.
The last thing you want is to pay a company $10,000 for a PDF document with no explanation.
At PurpleSec, we tell clients to set aside at least 1 hour with our technical team, encourage them to ask questions, and to challenge our findings.
As a result, they clearly understand every aspect of the report, their risk rating, and the pathway to remediating their exposure.
Free Penetration Testing Policy
Skip the policy-writing hassle with our ready-to-use penetration testing policy template.

What Are The Different Approaches To Penetration Testing?
Penetration tests differ both in their approach and in the weaknesses they attempt to exploit.
The level of information provided to the pen tester will determine their approach as well as the scope of the project.
For example, will the penetration tester have knowledge of how a network is mapped, or are they required to uncover this information on their own?
The different approaches to penetration testing include:
- Black Box
- White Box
- Gray Box
Black Box Penetration Testing
During a black box penetration test (also known as external penetration testing) the pen tester is given little to no information regarding the IT infrastructure of a business.
The main benefit of this method of testing is to simulate a real-world cyber attack, whereby the pen tester assumes the role of an uninformed attacker.
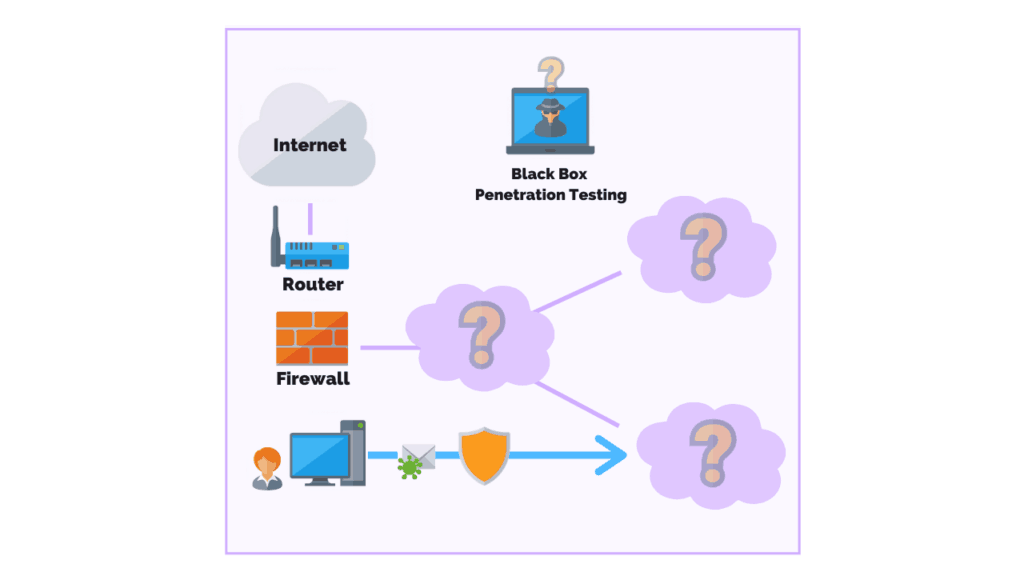
A black box penetration test can take up to six weeks to complete making it one of the longest types of penetration tests.
Businesses can expect to pay between $10,000 – $25,000 due to the level of effort involved in planning, performing, testing, and completing the report.
This, of course, all depends on the scope of the project.
One of the easiest ways for pen testers to break into a system during a black box test is by deploying a series of exploits known to work, such as Kerberoasting.
This method of testing is also referred to as the “trial and error” approach, however, there is a high degree of technical skill involved in this process.
White Box Penetration Testing
White box penetration testing (also called clear box testing, glass box testing, or internal penetration testing) is when the pen tester has full knowledge and access to the source code and environment.
The goal of a white box penetration test is to conduct an in-depth security audit of a business’s systems and to provide the pen tester with as much detail as possible.
As a result, the tests are more thorough because the pen tester has access to areas where a black box test cannot, such as quality of code and application design.
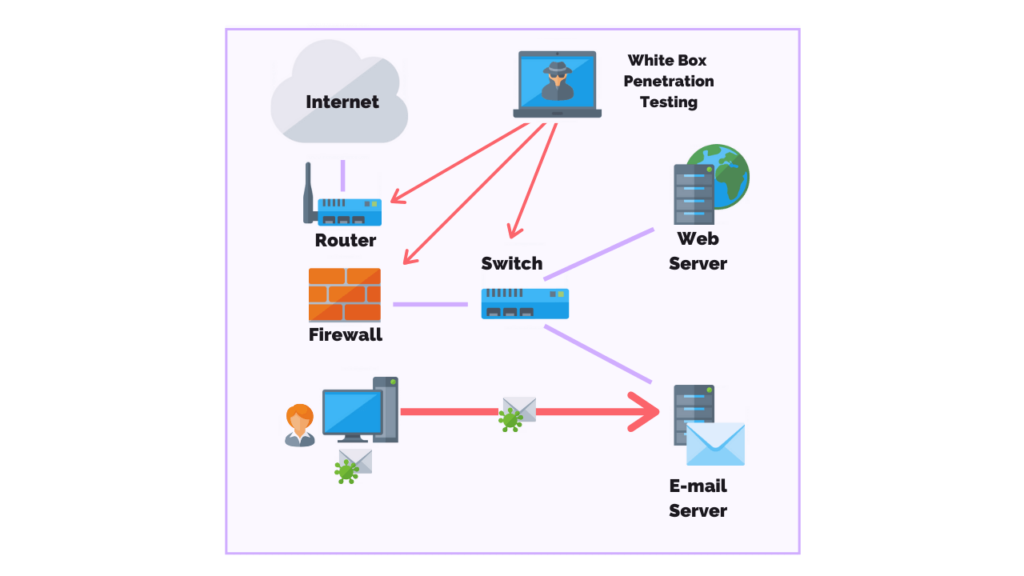
White box tests do have their disadvantages.
For instance, given the level of access the pen tester has it can take longer to decide what areas to focus on.
In addition, this method of testing often requires sophisticated and expensive tools such as code analyzers and debuggers.
White box tests can take two to three weeks to complete and cost between $4,000 – $20,000.
In the end, it doesn’t matter whether you perform a black box or a white box penetration test so long as the primary goal of the test is being met.
Gray Box Penetration Testing
During a gray box penetration test, the pen tester has partial knowledge or access to an internal network or web application.
A pen tester may begin with user privileges on a host and be told to escalate their privileges to a domain admin. Or, they could be asked to get access to software code and system architecture diagrams.
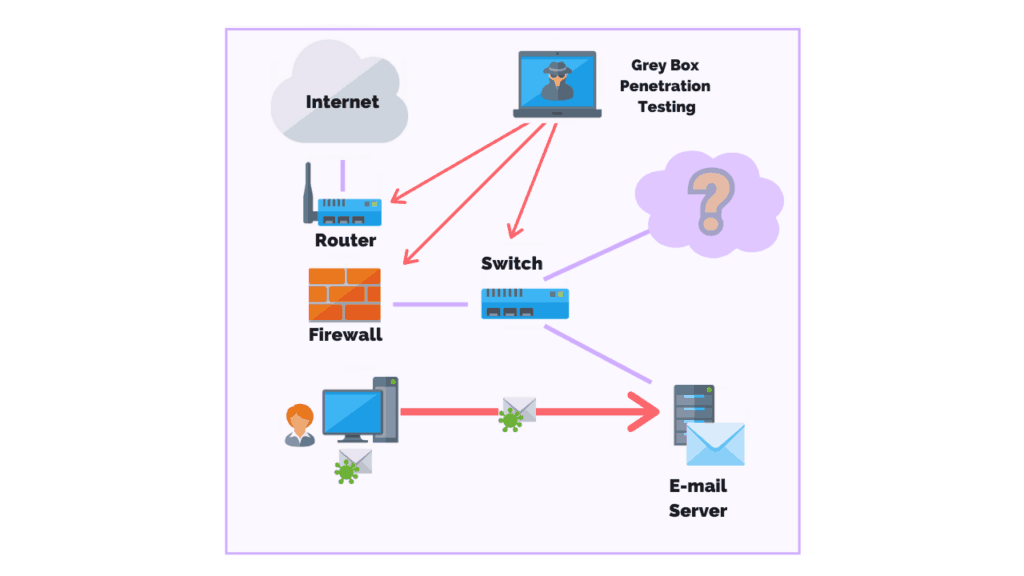
One main advantage of a gray box penetration test is that the reporting provides a more focused and efficient assessment of your network’s security.
For instance, instead of spending time with the “trial and error” approach, pen testers performing a gray box penetration test are able to review the network diagrams to identify areas of greatest risk.
From there, the proper countermeasures can be recommended to fill the gaps.
$35/MO PER DEVICE
Enterprise Security Built For Small Business
Defy your attackers with Defiance XDR™, a fully managed security solution delivered in one affordable subscription plan.
Types Of Penetration Testing
The different types of penetration testing include:
- Network
- Web Application
- Client Side
- Wireless
- Social Engineering
- Physical Penetration Testing
Each type of penetration test requires specific knowledge, methodologies, and tools to perform and should align with a specific business goal.
These goals could range from improving awareness of social engineering attacks to employees company-wide, to implementing secure code development to identify flaws in software code in real-time, or meeting regulatory or compliance obligations.
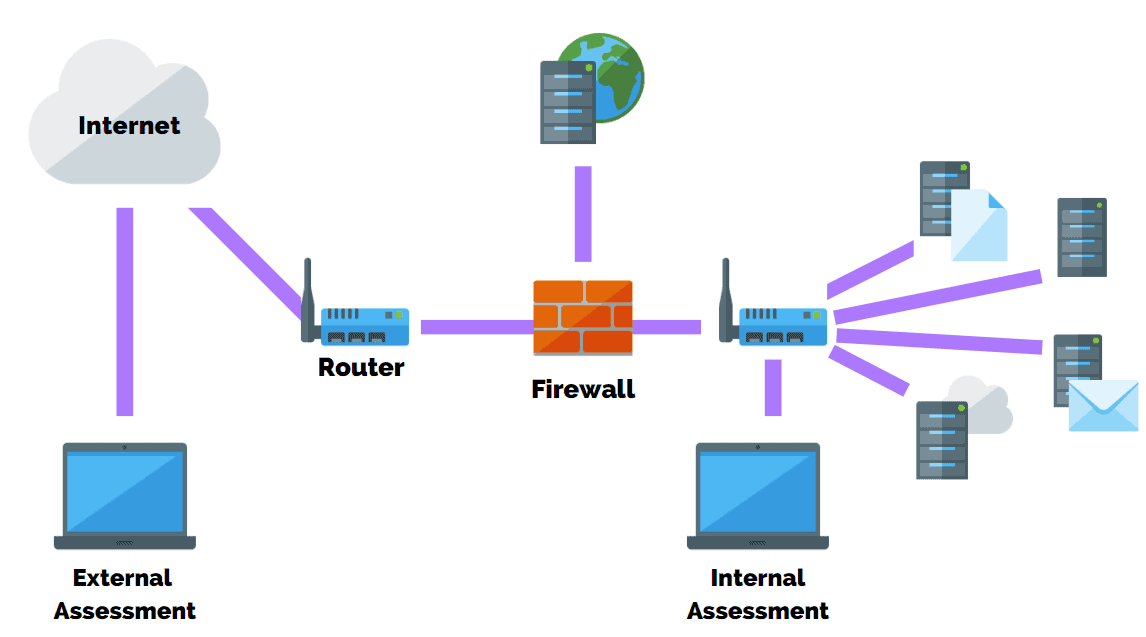
Network Penetration Testing
Network penetration testing, or infrastructure testing, is one of the most common types of penetration testing performed.

The main purpose is to identify the most exposed vulnerabilities and security weaknesses in the network infrastructure (servers, firewalls, switches, routers, printers, workstations, and more) of an organization before they can be exploited.
Why Should You Perform A Network Penetration Test?
Network penetration tests should be performed to protect your business from common network-based attacks including:
- Firewall Misconfiguration And Firewall Bypass
- IPS/IDS Evasion Attacks
- Router Attacks
- DNS Level Attacks:
- Zone Transfer Attacks
- Switching Or Routing Based Attacks
- SSH Attacks
- Proxy Server Attacks
- Unnecessary Open Ports Attacks
- Database Attacks
- Man In The Middle (MITM) Attacks
- FTP/SMTP Based Attacks
Given that a network provides mission-critical services to a business, it is recommended that both internal and external network penetration tests be performed at least annually.
This will provide your business with adequate coverage to protect against these attack vectors.
Web Application Penetration Testing
Web application penetration testing is used to discover vulnerabilities or security weaknesses in web-based applications.
It uses different penetration techniques and attacks with aims to break into the web application itself.
The typical scope for a web application penetration test includes web based applications, browsers, and their components such as ActiveX, Plugins, Silverlight, Scriptlets, and Applets.
These types of tests are far more detailed and targeted and therefore are considered to be a more complex test.
In order to complete a successful test, the endpoints of every web-based application that interacts with the user on a regular basis must be identified.
This requires a fair amount of effort and time from planning to executing the test, and finally compiling a useful report.
The techniques of web application penetration testing are continuously evolving with time due to the increase in threats coming from web applications day by day.
This threat has expanded greatly since the outbreak of COVID-19, resulting a 600% increase in cybercrime.
Why Should You Perform A Web Application Penetration Test?
A key reason to perform a web application penetration test is to identify security weaknesses or vulnerabilities within the web based applications and its components like Database, Source Code, and the back-end network.
It also helps by prioritizing the determined weaknesses or vulnerabilities and provides possible solutions to mitigate them.
In software application development it’s considered best practice to continuously improve the codebase.
Deploying a secure and agile code is the phrase often used to describe this practice.
Agile code deployment is the preferred method over large batch deployments, as the more variables introduced into the code in a single deployment, the more opportunities there are to create bugs or errors leading to security vulnerabilities.
As a result, technical debt forms, where developers gradually spend more time implementing fixes to problems then they do develop new features or updates.
In contrast, agile methodologies use a sandbox environment (a duplicate copy of the codebase) to test code functionality and usability prior to launching into production.
If the deployment is unsuccessful, developers can easily single out the change and roll the code back to previous version history.
The trick is balancing daily code deployment with security in mind.
It’s not uncommon for enterprise software companies to employ pen testers to continuously test their code. Google, as well as other tech giants, offer a reward for finding and reporting on vulnerabilities within their applications.
Client Side Penetration Testing
Client side penetration testing is used to discover vulnerabilities or security weaknesses in client side applications.
These could be a program or applications such as Putty, email clients, web browsers (i.e. Chrome, Firefox, Safari, etc.), Macromedia Flash, and others. Programs like Adobe Photoshop and the Microsoft Office Suite are also subject to testing.
Why Should You Perform A Client-Side Penetration Test?
Client-side tests are performed to identify specific cyber attacks including:
- Cross-Site Scripting Attacks
- Clickjacking Attacks
- Cross-Origin Resource Sharing (CORS)
- Form Hijacking
- HTML Injection
- Open Redirection
- Malware Infection
Wireless Penetration Testing
Wireless penetration testing involves identifying and examining the connections between all devices connected to the business’s wifi.
These devices include laptops, tablets, smartphones, and any other internet of things (IoT) devices.
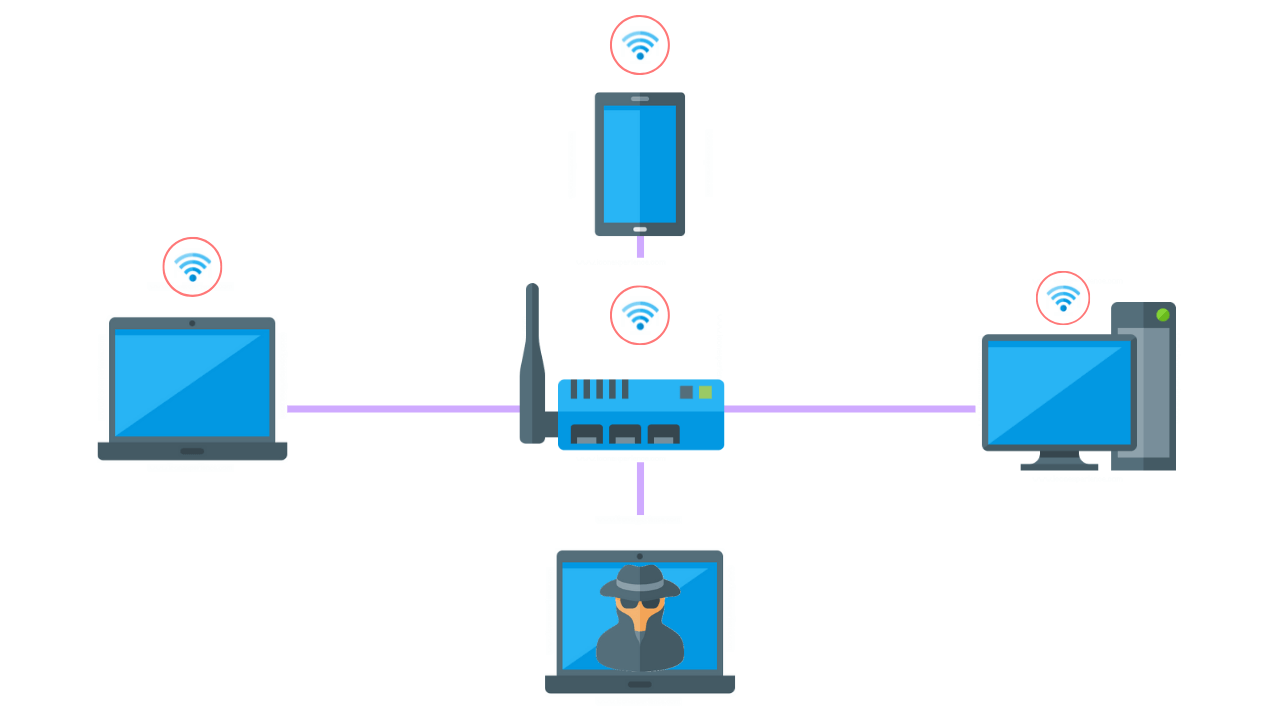
Wireless penetration tests are typically performed onsite as the pen tester needs to be in range of the wireless signal to access it.
Alternatively, a NUC and WiFi Pineapple can be deployed onsite to remotely perform the test.
Why Should You Perform A Wireless Penetration Test?
Wireless communications are an invisibly running service that allows data to flow in and out of the network.
Therefore, this wireless network must be secured from any weaknesses like unauthorized access or data leakage.
Before performing a wireless penetration test you should consider the following:
- Have all access points been identified and how many use poor encryption methods?
- Is the data flowing in and out of the network encrypted and if so, how?
- Are there monitoring systems in place to identify unauthorized users?
- Is there any possibility the IT team could have misconfigured or duplicated a wireless network?
- What are the current measures in place to protect the wireless network?
- Are all wireless access points using WPA protocol?
Social Engineering Penetration Testing
Social engineering penetration testing is where a malicious actor attempts to persuade or trick users into giving them sensitive information, such as a username and password.
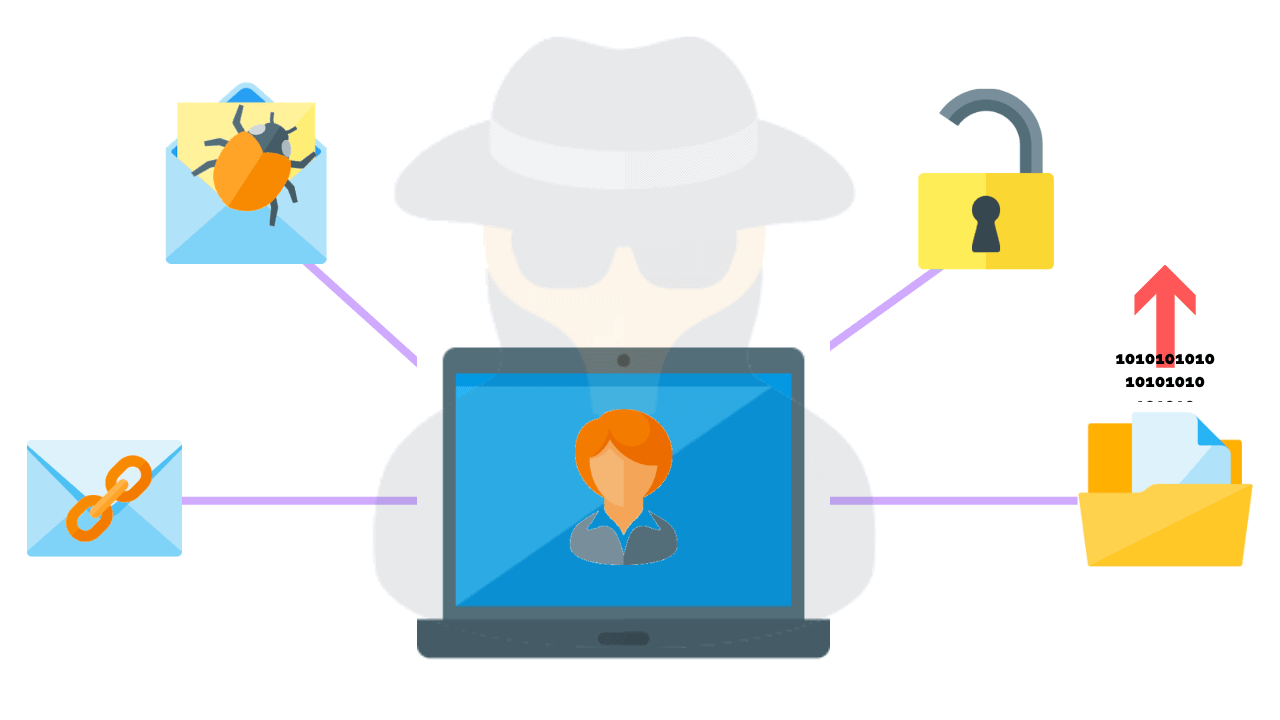
Common types of social engineering attacks used by pen testers include:
- Phishing Attacks
- Vishing
- Smishing
- Tailgating
- Imposters (i.e. Fellow Employees, External Vendors, or Contractors)
- Name Dropping
- Pre-texting
- Dumpster Diving
- Eavesdropping
- Gifts
Why Should You Perform Social Engineering Tests?
According to recent statistics, 98% of all cyber attacks rely on social engineering.
This is because internal users are one of the biggest threats to a networks security and due to how lucrative the scams are.
Social engineering tests and awareness programs have proven to be one of the most effective methods of mitigating an attack.
For example, KnowBe4, the popular email phishing platform, simulates an email phishing attack.
When the user clicks on the link they’re taken to a page that informs them that it was a phishing test.
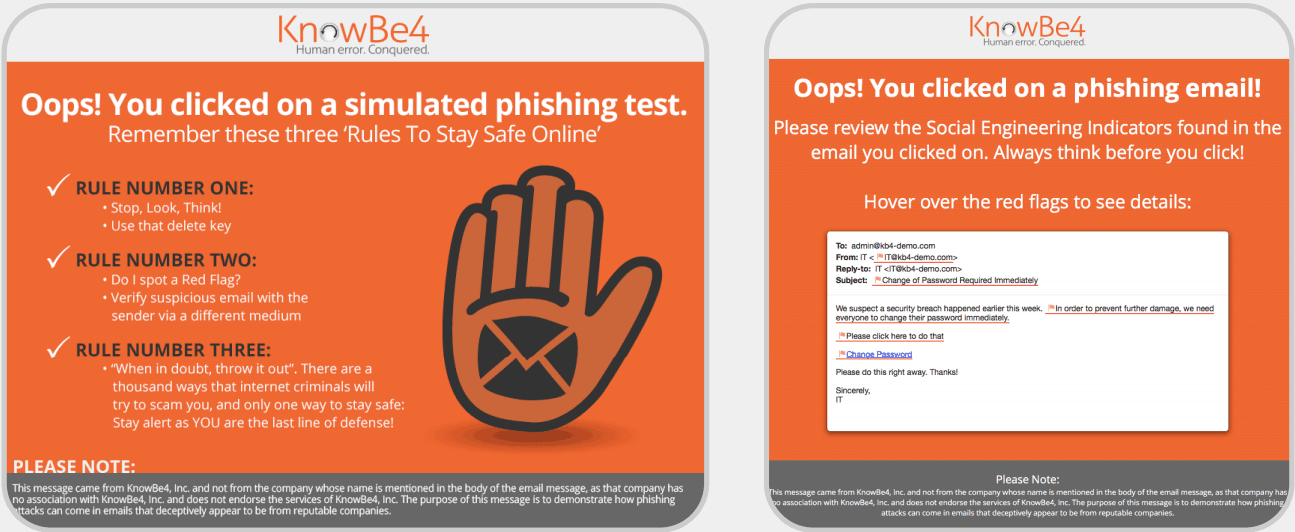
Remediation training is then provided to help educate and inform users on the most current cyber attacks and how to avoid them.
Physical Penetration Testing
Physical penetration testing simulates a real-world threat whereby a pen tester attempts to compromise physical barriers to access a business’s infrastructure, building, systems, or employees.
Why Should You Perform A Physical Penetration Test?
Physical barriers are often an afterthought for most businesses, however, if a malicious actor is able to gain physical access to your server room then they could own your network.
Imagine the impact that might have on your business, on your customers, as well as business partnerships.
The primary benefit of a physical penetration test is to expose weaknesses and vulnerabilities in physical controls (locks, barriers, cameras, or sensors) so that flaws can be quickly addressed.
Through identifying these weaknesses proper mitigations can be put in place to strengthen the physical security posture.
Article by