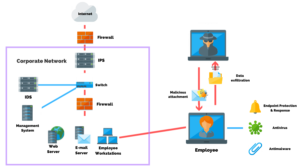
Social engineering is the number one method used by threat actors to collect sensitive data or gain access to systems and networks.
According to some security professionals Voice Phishing (Vishing), has a success rate of 37%, but this increases to 75% when combined with email phishing.
Further, a recent spearvishing attack, or targeted attack, against Twitter highlights the growing concern. Threat actors were able to gain access by manipulating a Twitter employee into providing access to internal tools. With this access, the threat actor was able to control thousands of prominent accounts such as Bill Gates, Joe Biden, and Beyonce.
In this article, I’m going to explain what vishing attacks are, the common types of scams used by threat actors, how you can identify a vishing attack, and steps your business can take to prevent an attack.
Free IT Security Policies
Get a step ahead of your goals with our comprehensive templates.

What Is Vishing?
Vishing is a social engineering attack that attempts to trick victims into giving up sensitive information over the phone. In most cases, the attacker strategically manipulates human emotions, such as fear, sympathy, and greed to accomplish their goals.
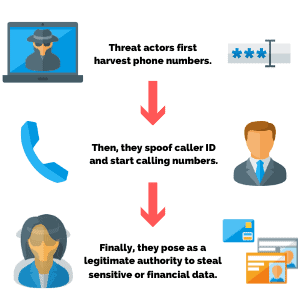
This form of attack has been around since the early 2000’s, but has become increasingly prevalent in part due to the upward trend in the amount of people working remotely today.
Vishing sounds like another social engineering attack that is common in corporate environments, phishing. Vishing is a combination of two words, voice and phishing.
So what’s the difference between vishing and phishing?
Why Are Vishing Attacks Performed?
According to recent reports, the primary motivation behind vishing attacks is to obtain sensitive financial data from an organization or the personal data of the person taking the call.
The NSA reported recently in a COVID-19 article that a foreign country was allegedly attempting to gather COVID-19 vaccination formulas. The foreign country denied the accusation, however, it’s noteworthy that cyber-attacks usually originate outside the borders of a country.
The NPR article did not specifically state if the attack was phishing or vishing, but the motivation would have been to compromise sensitive documents or data for financial gain.
What Are The Most Common Vishing Scams?
Scammers today are master opportunists. As noted in the vishing attack examples, thieves want something you have of value, i.e. your banking information, credit cards, or social security numbers.
If they are unable to entice their victims with something tangible, they will prey on your emotions by focusing on a current world event or natural disaster. At this point in history, the COVID-19 pandemic, fires, storms, and social unrest are the major topics today and are used by attackers to carry out vishing schemes.
A popular Security Magazine recently published information regarding the COVID-19 pandemic and vishing attacks.
They reported that the FTC from January 2020 until mid-April, received 18,235 reports related to COVID-19, and people reported losing $13.44 million dollars to fraud.
Another common vishing scheme happens once a year around tax filing time.
You guessed it, IRS phone or vishing scams.
IRS vishing scams are usually aggressive in nature and prey on unsuspecting taxpayers’ fear that they are in tax payment trouble and need to rectify the situation immediately with the caller.
As noted at the outset of this article, attackers are taking advantage of remote teleworkers.
Since many workers are not within the physical workplace environment, this makes the remote employer susceptible to phony callers disguising themselves as technical support looking to help you fix a problem that doesn’t exist.
In the state of Georgia, a vishing attack made the local news that involved law enforcement. The spokesman for law enforcement revealed this information to the public:
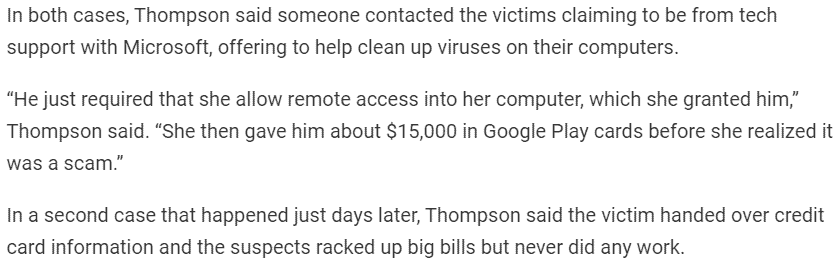
This case sounds eerily similar to an incident a colleague revealed at their business. A corporate user received a phone call from someone claiming to be from IT support.
The user provided the caller access to her PC. The fake support person remoted into the PC and downloaded malware.
The user quickly came to her senses after noticing strange applications installed on the machine. They ended the call and the employer immediately called their real corporate tech support to inform them of the activity.
In the news article and this case, the attacker used the phone to perform their nefarious activity, under the guise of a technical support representative.
How To Identify A Vishing Attack
Recently, I received an urgent recorded call from someone claiming to be from a government entity.
The recording stated that law enforcement was notifying me that my Social Security number had been stolen. The message paused briefly and placed me on hold with an option to continue the support call.
This call ended during the pause.
Last year, a support person claiming to be from a well-known Cable Provider called to offer me free services. All I needed to do was to go purchase a gift card and give them the card number to receive free services for 6 months.
I was caught off guard for a moment because I did use the cable service and it did sound like the call was from a real support center since they knew my name.
I thought for a minute, why would my cable provider request me to purchase a gift card.
Well, because they would never do this.
I was almost a victim of a prepaid card scam, which is a known vishing attack.
To avoid becoming a vishing attack victim, understand the characteristics of the attacker and their behavior.
Be leery of threatening callers from local numbers that call repeatedly during the day, or robotic voice calls that leave unsolicited messages.
Preventing Vishing Attack
If the identity of a person on the other end of the phone call sounds mysterious and has an offer too good to be true, proverbial red flags should start waving in your mind immediately.
Attackers also use auto-dialers to randomly call their potential victims. One tip of an autodialer is to listen for a two-second delay before a live person speaks.
When the person comes on the phone, they usually offer to either sell or offer you something if you surrender something personal about yourself or your company.
If you own a mobile phone, check with your provider to determine if they offer call blocking for unsolicited phone calls. If you own a landline, caller blocking is offered by most of the well-known carriers.
Another option to block unsolicited calls is to purchase a device known as Call Blockers or register your phone numbers with the National Do Not Call Registry.
In summary, below are a few steps that you can implement to prevent yourself from becoming victimized by a vishing attack:
- Use mobile apps to block callers
- Don’t pick up the phone
- Hang up immediately if the caller sounds suspicious
- Verify the caller’s identity – obtain name and organization web address
- Establish strict security policies for wiring money or updating payment information
- E.g. require offline confirmation before sending money requests
- Conduct regular vishing exercises
- Follow-up with security awareness training for staff
- Enroll in an Identity Theft Protection service
How Do You Recover From A Vishing Attack?
Recovering from a vishing attack depends on the nature of the attack and what was compromised.
If you are a remote teleworker who logs into a corporate environment from a company-issued device, notify your Security Department immediately of the activity.
They will request a detailed summary of the interaction between you and the attacker and advise on what to do next.
In most corporate environments, there may be a dedicated Incident Response team that will guide the next step in the process, particularly in the case if corporate-sensitive data involved.
If the attack occurred on your personal computer, ensure your anti-virus is up to date and change your password.
If you mistakenly gave the attacker your financial information, contact the institution for guidance on how to protect your data.
If you suspect your credit information has been compromised, immediately contact the credit bureaus to freeze your credit or request their guidance on recovery steps.
Conclusion
Vishing attacks, like phishing attacks, will continue as long as the opportunity for compromise is available and financial gain is the motivation for the cybercriminal.
The best attack for a criminal desiring to exploit sensitive information that belongs to you or your company is to understand the attacker and method of attack.
This article has provided details and statistics on the tactics used by cybercriminals. Their main ploy is the development of schemes used to exploit basic human tendencies and emotions for their financial gain.
Remain vigilant in protecting your personal information and that of your employer.
By following the simple precautionary steps and recommendations outlined in this article, you will be in a position to recognize and prevent becoming the next victim of a vishing attack.
Article by