What Is A Phishing Attack? (And How To Prevent Them)
Users are often the “weakest link in the chain” when it comes to a company’s network because social engineering attacks are designed to exploit human vulnerabilities.
Phishing is a type of social engineering attack that targets individuals in an attempt to gain access to a network or system for malicious purposes. Phishing attacks are most commonly sent via email. However, this attack may also be delivered via SMS texts or phone calls. You can prevent a phishing attack by never clicking links, not publishing PII online, avoid emails that fake urgency, verifying email addresses are authentic, check for spelling and grammatical mistakes, and implement security awareness training.
Article Navigation
- What Is Phishing?
- What Are The Types Of Phishing?
- What Is Spear Phishing?
- What Is A Whaling Attack?
- How Do You Prevent Phishing Attacks?
What Is Phishing?
![]()
Phishing is a form of social engineering where threat actors attempt to retrieve sensitive information by manipulating people into clicking links, downloading attachments, or providing access over the phone.
Threat actors track our digital footprint to gather as much information as they can about an organization, its employees, and its vendors.
They then craft general or targeted phishing campaigns by preying on our emotions or by impersonating authority figures to gain our credentials and personal information.
Phishing attacks are often directed toward recipients who have access to financial information, data, or systems to which the attacker wishes to gain access.
What Are The Types Of Phishing?
There are three types of phishing which include:
- Email phishing
- Vishing (Voice Phishing)
- Smishing (SMS Phishing)
The main difference between each type of phishing attack is the method of delivery.
Email Phishing
 An email attack that attempts to convince a user that the originator is genuine, but with the intention of obtaining information for use with malicious intent is called email phishing.
An email attack that attempts to convince a user that the originator is genuine, but with the intention of obtaining information for use with malicious intent is called email phishing.
Cybercriminals use emails as a mode to gain access to our sensitive information such as credit card numbers, login credentials for bank accounts, or other sensitive information.
Vishing (Voice Phishing)
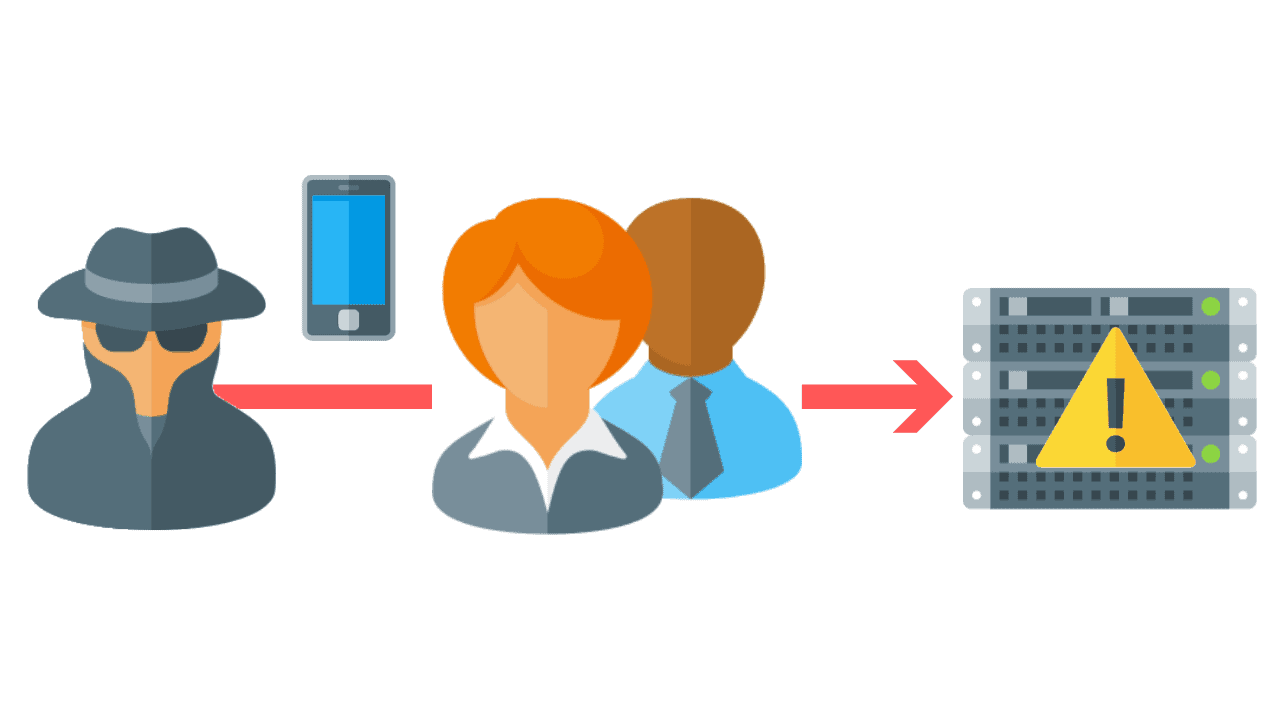 Vishing attempts to trick victims into giving up sensitive information over the phone.
Vishing attempts to trick victims into giving up sensitive information over the phone.
In most cases, the attacker strategically manipulates human emotions, such as fear, sympathy, and greed in order to accomplish their goals.
Smishing (SMS Phishing)
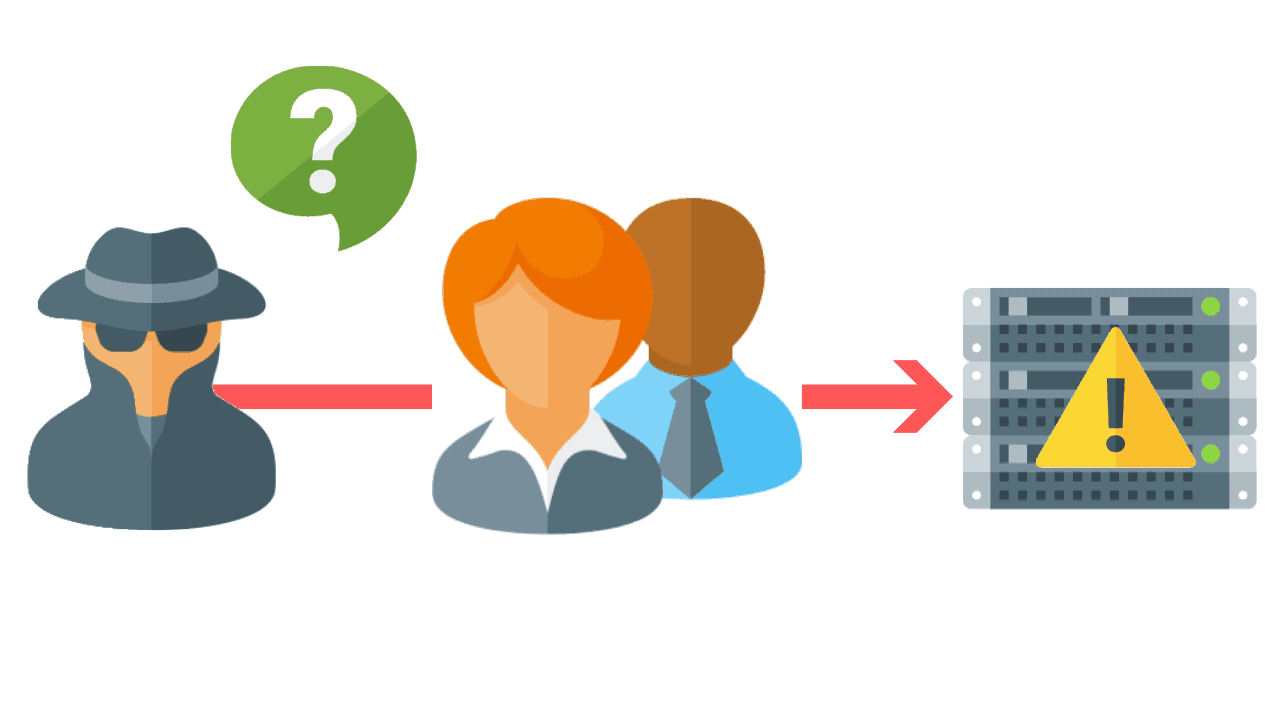 Smishing is a cyber attack that uses SMS text messages to mislead its victims into providing sensitive information to a cybercriminal.
Smishing is a cyber attack that uses SMS text messages to mislead its victims into providing sensitive information to a cybercriminal.
URLs may be embedded in a short link into the text message, inviting the user to click on the link which in most cases is a redirect to a malicious site.
Examples Of Phishing Attacks
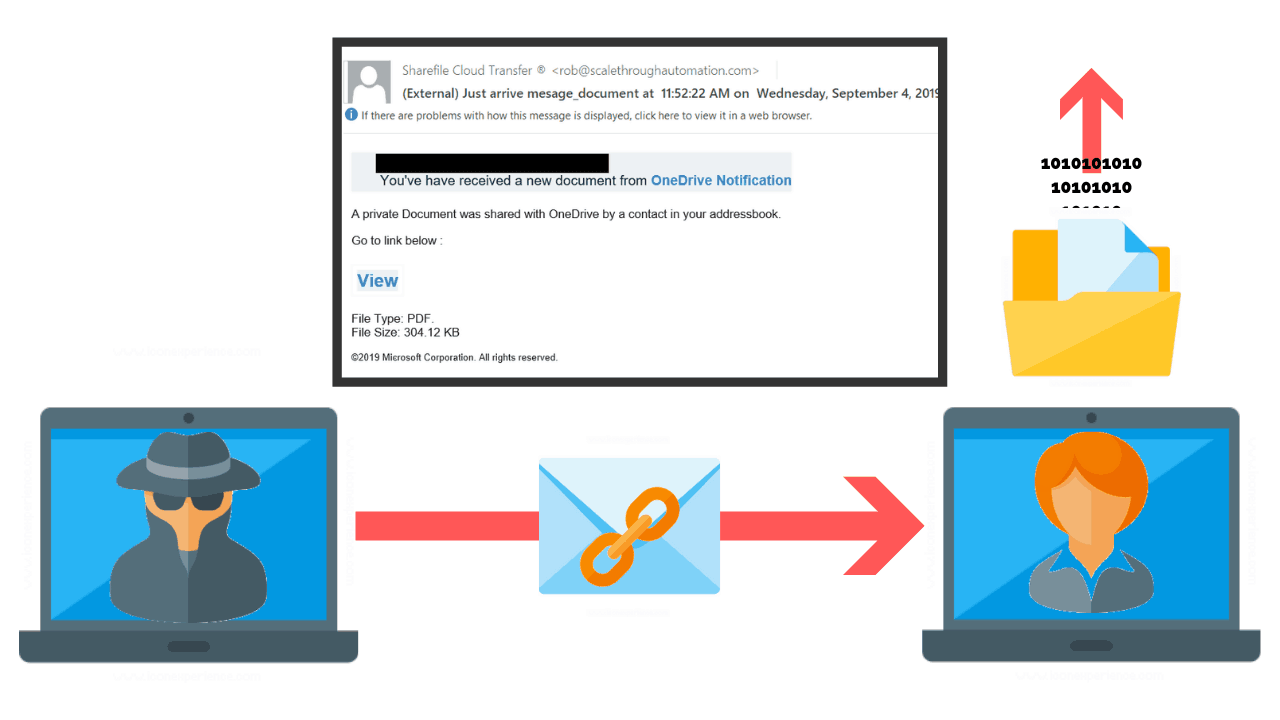
In this example, the phishing email attempts to steal the credentials of a user. Once they have the account credentials, they can attempt to access more network resources such as the VPN, remote desktop services or even online email accounts.
Looking at the email below, you will find that the email is supposedly from Microsoft, however, the sender’s domain name is not Microsoft. This is one indication that this email is phishing. Secondly, hovering over the link of the email identified that the link does not actually take you to Microsoft. This is yet another indicator that the email is phishing.
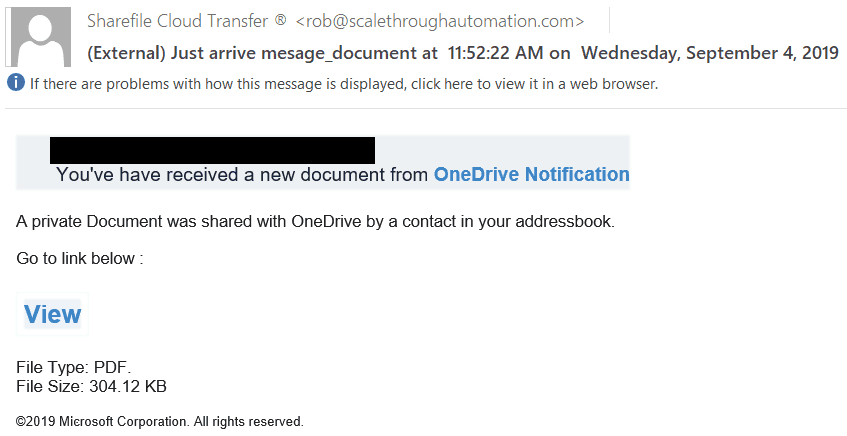
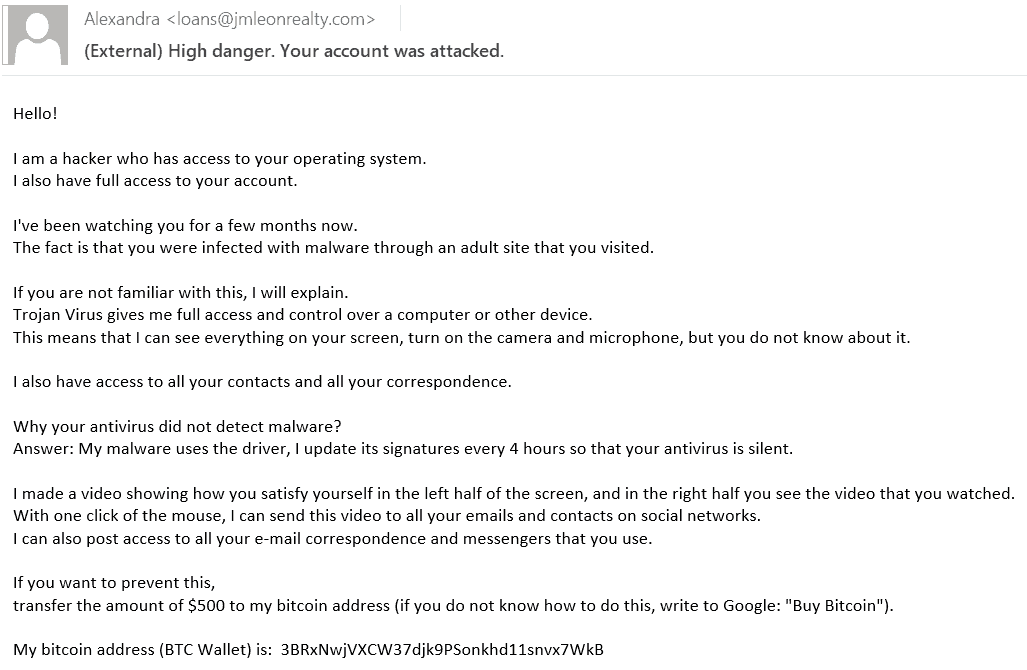
Another common type of phishing that I see is phishing emails that attempt to threaten or scare the recipient. In the example below, the email attempts to blackmail the recipient into paying a sum of money to keep data they have “stolen” from the user from being released to the public. This scare tactic attempts to make the recipient feel embarrassed and violated which in turn may lead to the recipient paying the ransom.
What Is Spear Phishing?
The main difference between phishing and spear phishing is that spear phishing targets specific users or groups of users such as a billing department or HR department, while phishing emails are sent to a broad audience. Targeted emails sent to these users are typically well crafted and designed to fit the normal business correspondence the user may be used to seeing on a regular basis.
Spear phishing is one of the fastest-growing threats in cyber security. This is because the information that is freely available on the web, such as social profiles, company about us pages, and much more is also available to threat actors.
Threat actors take this information to build a unique profile of their victims. The end result is a highly personalized and targeted email that entices you to click and install malicious software.
Examples Of Spear Phishing Attacks
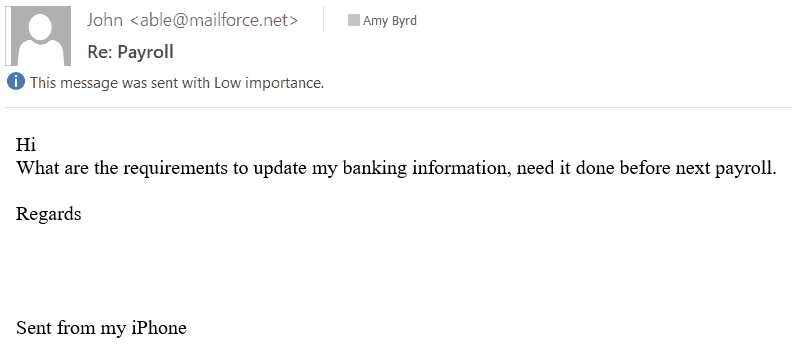
In this example, you see that the attacker has sent an email to a member of a payroll department in an attempt to change their direct deposit information. From what I have seen, these emails typically come from poorly chosen email addresses that are easily identifiable.
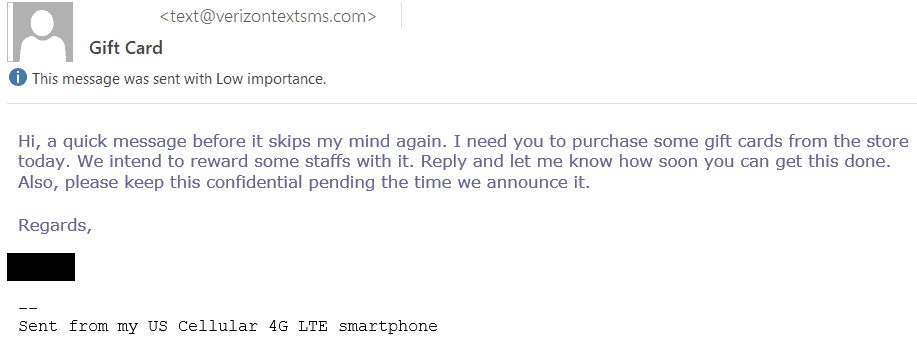
This next example is slightly different than the first in that instead of trying to change someone’s direct deposit information they are trying to trick the recipient into purchasing gift cards. Again, this is typically targeted to a specific group of people that would have access to perform this request. In my experience, these emails most commonly target executive assistants.
What Is A Whaling Attack?
Whaling is a form of phishing that targets high-level executives such as the CEO or CFO of a company, or attempts to impersonate them. Like spear phishing, these emails are specially crafted for the intended recipient. When these emails are specially crafted they become harder and harder to identify.
One common example I have seen involve a CEO being spoofed in an attempt to trick someone in the finance department to make a payment to a “vendor”.
A recent upswing of whaling attacks have been identified in the shipping industry. These attacks have been noted to attempt to spread malware and transfer payments to suspicious accounts. The emails that have been collected so far show the attackers are attempting to make the email look as if it is an internal email by changing the letter “I” to a number “1”.
Example Of A Whaling Attack
In 2016, Snapchat fell victim to a whaling attack and released the following statement:
“It’s with real remorse–and embarrassment–that one of our employees fell for a phishing scam and revealed some payroll information about our employees.”
The email was sent to a Snapchat employee and had appeared to come from the CEO. The attacker had requested payroll information, and since payroll was part of their duty and the “CEO” was asking for it, the employee handed over the information. Shortly after the incident, the attacker released the payroll information.
How Do You Prevent Phishing Attacks?
With users being the weakest link in the chain, end-user training is one of the most effective ways to protect against phishing attacks. There are many ways to train users but some of the most effective I have seen revolve around annual and remedial training courses as well as simulating phishing attempts.
Other common methods used to prevent phishing and whaling attacks include:
- Never provide personally identifiable information.
- Verify email addresses are authentic.
- Never click unknown links or download attachments.
- Avoid emails that insist you act now – fake urgency is meant to intimidate you.
- Check for spelling and grammatical mistakes within the email.
- Create additional authentication policies before wiring money, such as requiring a phone call to authorize payment.
Security Awareness Training
Annual security awareness training is a great way to refresh users on current trends and new methods taken by attackers. However, training should not stop there. Simulated phishing attacks performed by either your company or a third-party company is an excellent way to test your users and validate the effectiveness of your training.
In the event a user fails a phishing test, or even falls victim to a phishing attack, remedial training should be used to train the user in the areas they were found to be deficient.
A few other things you can add to your security awareness training program are:
- A button, available in your end-users mail client, that can report an email as suspicious has proven to increase reporting of suspicious email and thus increase the detection rate of phishing attacks,
- If you are using a simulated phishing approach, track metrics so you can measure the effectiveness of your training and can adjust accordingly,
Other things that can be done to defend against phishing attacks include:
- Perform routine phishing campaigns to test the awareness of employees and to determine how they respond to an incident.
- Encourage your executives to make their social media platforms private in an attempt to prevent whaling attacks.
- Use mail filtering technologies that can proactively block known malicious senders and spam mail while also providing the ability to blacklist known malicious senders.
- Use multi-factor authentication for access into any service that allows entry into your network externally (VPN, Remote Desktop, Outlook).
Related Articles