You can create a successful phishing campaign by following these steps:
- Send A Social Engineering Questionnaire
- Crafting Your Phishing Emails
- Vishing Scenario
- The Smishing Scenario
- Getting Stakeholder Buy In
- Performing The Phishing Test
- Reporting
- Security Awareness Training
Free Security Policy Templates
Get a step ahead of your cybersecurity goals with our comprehensive templates.

Knowing how threat actors think is fundamental to preventing cyber attacks from compromising systems and networks.
This is especially true since 21% of ransomware attacks are delivered through social engineering.
In this article, I’m going to explain the steps for creating a phishing campaign and the role security awareness training plays in helping to secure your data.
By the end, you will have the knowledge you need to build a successful phishing campaign for your organization.
Why Are Phishing Campaigns Performed?
When performed regularly, phishing campaigns ensure that employees remain vigilant of their security responsibilities and are aware of the recent attack vectors and popular trends used by threat actors.
You can deploy all of the security controls in the world – a SIEM solution, IDS/IPS, and EDR, among others.
However, all it takes is one click of a link by an employee to give access to an unauthorized user.
Social engineering is one of the most successful types of cyber attacks because it plays on human emotions and triggers an impulse to react.
They often use phrases that demand our attention and incite urgency.
With the outbreak of Coronavirus, attackers have exploited these human vulnerabilities resulting in a 600% increase in cybercrime.
Compliance Requirements
Many compliance frameworks and audits such as CMMC, ISO 27001, SOC 2, HIPAA, and HITRUST require periodic security awareness training for employees.
The ideal way to perform this training is to include it in the new-hire orientation security training module and make it a mandatory requirement before granting access to critical systems.
Security awareness training should be completed at least on an annual basis and train employees not only on identifying phishing attacks but also to respond appropriately and report to the incident response team for proactive action.
Organizations such as healthcare providers should perform more frequent phishing campaigns and ideally hire an outside consultant to perform phishing exercises.
This is because a single data breach has the potential to put these organizations out of business because of the immense fines from HIPAA and GDPR.
Steps To Creating A Phishing Campaign
Considering the mentioned risks of a successful social engineering attack, the security team must do its part and educate employees so that they can identify a phishing attack.
They do this by running an organizational-wide phishing campaign to test and gauge employee awareness.
Step 1: Send A Social Engineering Questionnaire
The first step to performing any social engineering engagement is to obtain buy in and approval from key stakeholders.
Stakeholders might refer to:
- Executive management
- IT directors and managers
- Compliance and auditing teams
- Project management and operations teams
This is done by sending an informal questionnaire designed to better understand the business, its environment, and how employees interact with the environment or with one another.
Here are a few questions to consider asking as a baseline before crafting the phishing campaign:
- What level of employee information will be provided to the campaign team? Would it include personal information such as first name, last name, payroll bank, etc.?
- What common websites or applications do internal users utilize daily?
- What are the most common file types users work with? (PDFS, Word, Excel, etc).
- What organizations does the company work with? (Vendors, IT support, business partners, charities).
- What is a major internal company product or service that employees prioritize the most?
- Is there a group of employees who routinely fall for the Phishing emails?
- Are there any blacklisted websites such as Gambling, Porn, etc. that employees are suspected to visit?
- Is there segregation between the employees who handle sensitive information v/s employees handling public information? Do they use different systems?
- How often is the security awareness training performed?
- Do employees in different countries use different email domains and username format?
- Is it a targeted Phishing campaign (i.e. Spear Phishing) or a generic Phishing campaign?
- Are employees allowed to use social media sites such as Facebook, Twitter, etc. using their workstations and work emails?
Review The Questionnaire Answers With Stakeholders
Schedule a follow-up call with stakeholders once the questions have been answered.
The purpose of this call is to probe for further information that may not have been included in the questionnaire.
For example, you could share preliminary ideas on the approach of the campaign to assess whether or not users would be likely to fall victim to an attack.
This feedback is invaluable to ensuring the phishing campaign is testing a realistic scenario.
There are few learning opportunities gained for employees if the campaign is too easy or too difficult.
The end goal isn’t to see how many people you can trick, but instead how many you can help educate or reinforce their knowledge of social engineering threats.
Once you’ve gathered this information the next step is to build the campaign.
Step 2: Crafting Your Phishing Emails
Creating emails for a phishing campaign is an art.
Armed with information collected from the questionnaire the testing team will begin to craft email templates.
Your approach will depend on the scope of work of the engagement.
The following scenarios are examples of email campaigns based on difficulty:
- Basic
- Intermediate
- Advanced
Scenario 1: Basic
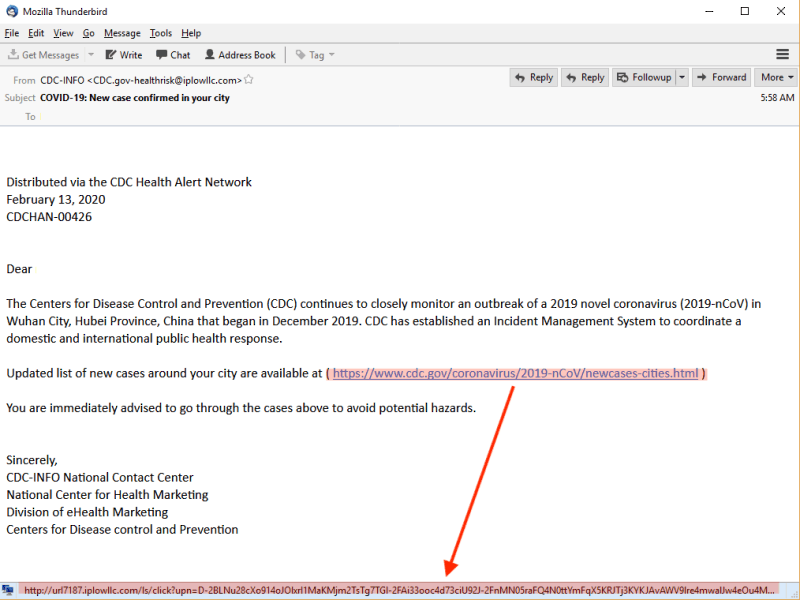
In the easy phishing email, the campaign team will make obvious errors and ask the user to perform a basic task like changing a password.
The link to change the password will redirect the user to a malicious page.
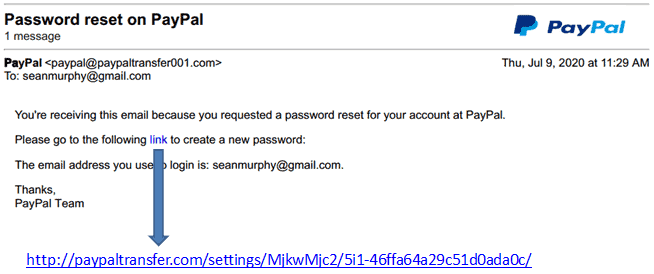
These types of emails are typically sent in mass with no specific target in mind.
Scenario 2: Intermediate
The intermediate phishing email will look more familiar and would ideally come from a variant of a trusted source like the employee’s workplace, a vendor, or a friend.
In this example, the email is posing as a member of the IT team who needs information from an employee for an upcoming audit.
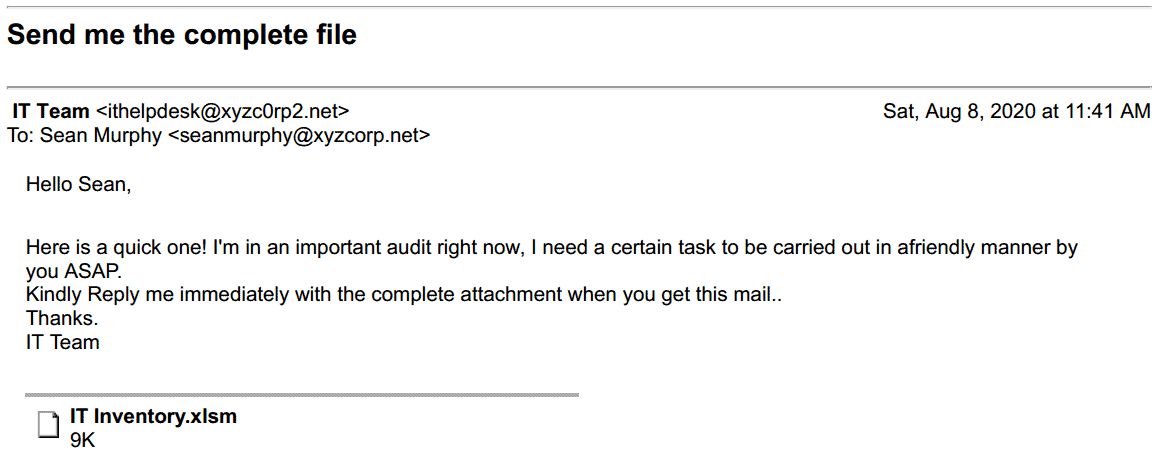
If done correctly, the email will look like any one of the dozens of requests that bombard someone’s inbox daily.
If the employee isn’t vigilant, they may mistake the phishing email as a legitimate request.
Scenario 3: Advanced
Of all the above, emails asking for immediate action from the executive team member or a colleague are the most effective.
These types of emails have an attachment to them and ask for an action to be performed right away.
These phishing emails typically mention the name of the leadership team either in the sender or the action required field and contain an attachment which when opened could cause the workstation and the network to be infected with malicious code.
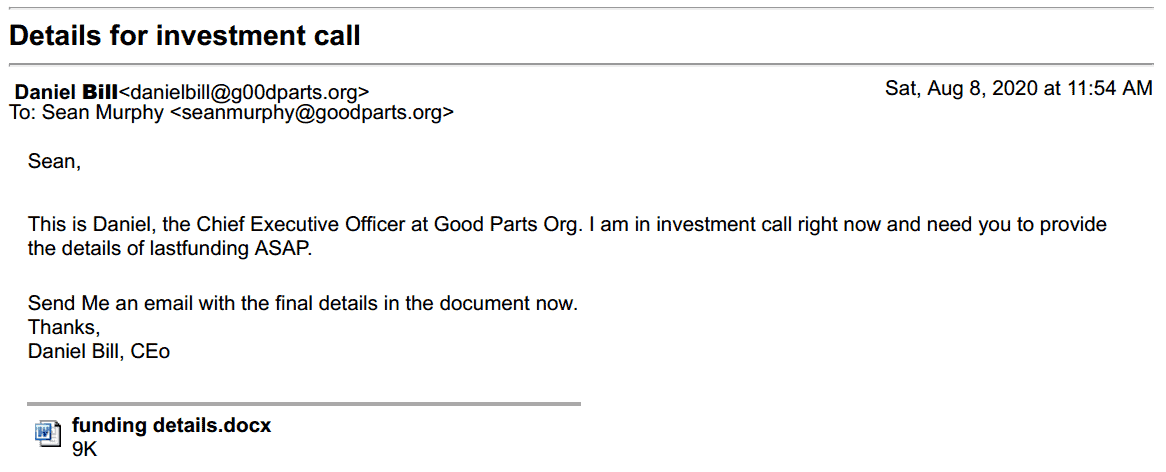
It’s not uncommon for threat actors to purchase a lookalike domain to enhance the quality of the phishing email.
One precaution a company can take to prevent this is to purchase variations of the company’s domain name.
This can be relatively inexpensive for most organizations costing $5 – $20 per year to hold the domain.
Step 3: The Vishing Scenario
The demand for instant collaboration coupled with the accessibility of mobile phones domestically and globally, has created a prime target for threat actors to carry out vishing attacks.
Payrolls are the number one scam used to reach employees.
An employee may receive a phone call from someone posing to be from the payroll department and will ask for confidential information like the employee’s bank account details or SSN.
Another popular scam used is pretending to be the financial institution where the employee maintains their payroll account.
Finally, employees, especially immigrants and old people, are targeted often pointing out discrepancies in a tax return or an irreversible action such as deportation or warrant for arrest.
With the fear of deportation or a huge tax penalty, victims either pass confidential account information or fall prey to the vishing attack and transfer a huge sum through direct deposit or gift cards.
Step 4: The Smishing Scenario
Smishing attacks are performed using text messages enticing to be from legitimate sources.
These messages usually contain a link and will ask the victim for immediate action to either claim an offer or money.
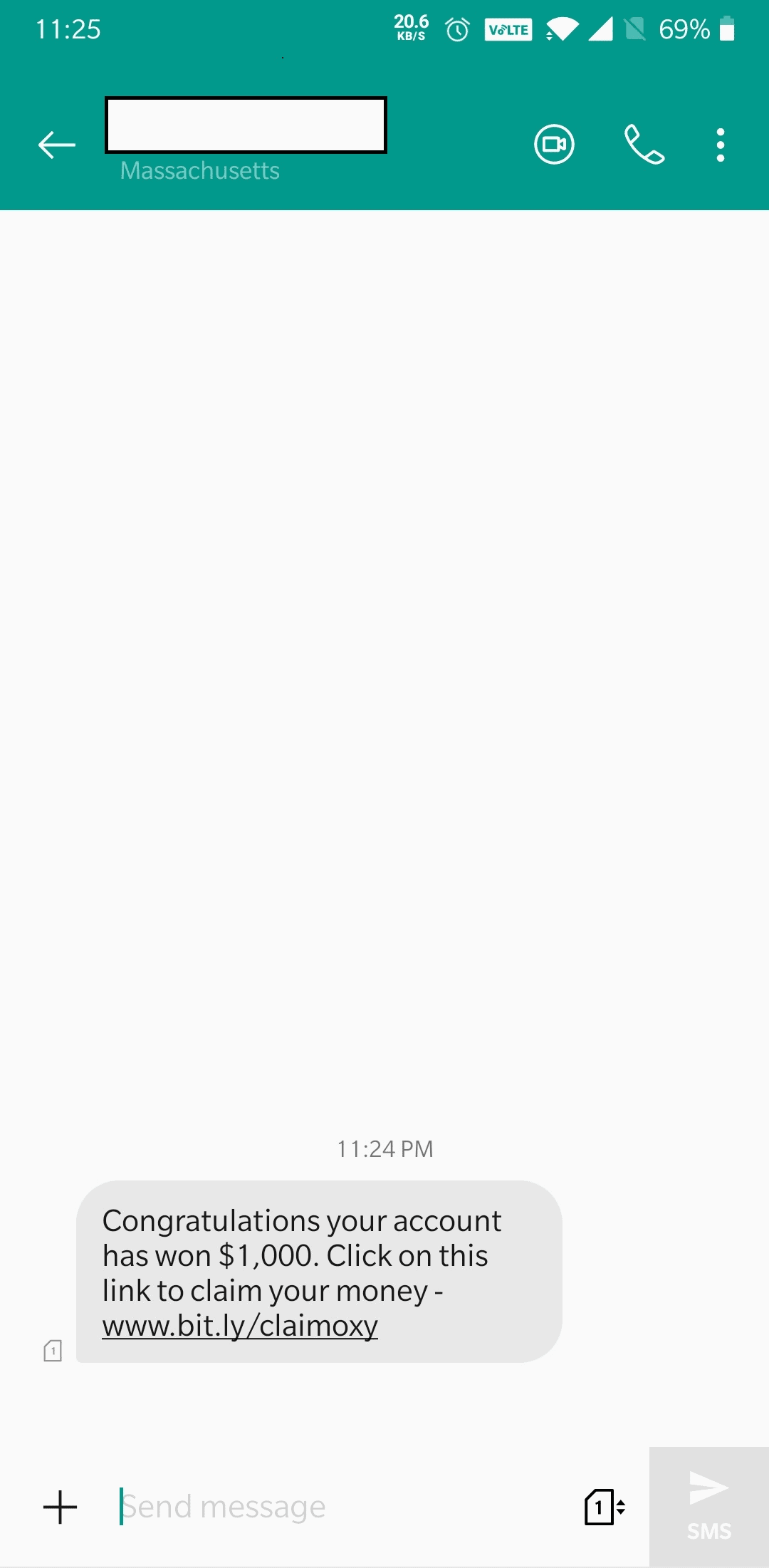
More often than not, the link in the message is a malicious code which upon clicked will enable the scammer to monitor all the SMS received on the phone.
This will also include any multi-factor authentication codes required for authorized or privileged access to systems.
Step 5: Getting Stakeholder Buy In
With all being said, the most important component of a successful phishing campaign is executive sponsorship.
The executive team is expected to review the phishing campaign and provide approval.
The executive team may choose to group the employees and agree to allocate a certain percentage of general phishing emails to one group, a certain percentage for spear phishing (ideally employees who hold confidential information), and both types of emails to the rest of the employees.
Employers may also choose to perform a vishing or smishing campaign to understand the effectiveness and applicability of security awareness training.
It’s also important to understand the terms of the engagement.
For example, is the objective only to prove that an employee can be phished?
Or, is the objective to steal credentials and prove the ability to compromise a system or network as a result of the phishing?
Step 6: Performing The Phishing Test
After gaining executive buy-in, the next step would be to simulate an actual phishing attack.
The employer may choose any of the phishing templates mentioned above.
Phishing attacks are often timed by the press coverage of the company.
For example, a company undergoing a round of funding may get phishing emails mentioning some public information about funding.
These emails are usually sent in the second half of the day as employees wrapping up the day may not ponder much towards the end of a long workday and click on the link easily.
The security team will likely collect multiple metrics on the phishing campaign, however, the users who opened the email, users who clicked on the malicious link, and the users who sent the emails to the security team for inspection should be reviewed first.
The security team may choose the employees falling victim to the campaign to complete additional security awareness training to strengthen their knowledge around the effective countermeasures for phishing.
Step 7: Reporting
The final executive report for a successful Phishing campaign should include the:
- Type of phishing performed
- Most and the least successful phishing schemes
- Total number of users for each category of phishing
- Number of users who clicked on the link or revealed confidential information during the vishing campaign
- List of employees needing additional training
The security team should ensure that the employees falling for the phishing campaign have action items like completing additional phishing training or spending time with the security team to understand the nuances of the phishing emails.
Step 8: Security Awareness Training
A redundant theme across the entire campaign should be to embed and drive the culture of security within teams.
Regardless of the effectiveness of the phishing campaign, they will become rudimentary.
Putting the entire onus of securing the organization will never be a good cybersecurity strategy and all employees must participate in enabling the security of the organization.
For these reasons, it should be made mandatory for all employees to complete security awareness training with a fundamental module for good cyber security practices such as:
- How to identify a phishing email
- Creating a strong password
- Maintaining a clean desk policy
- Using multi-factor authentication
Article by