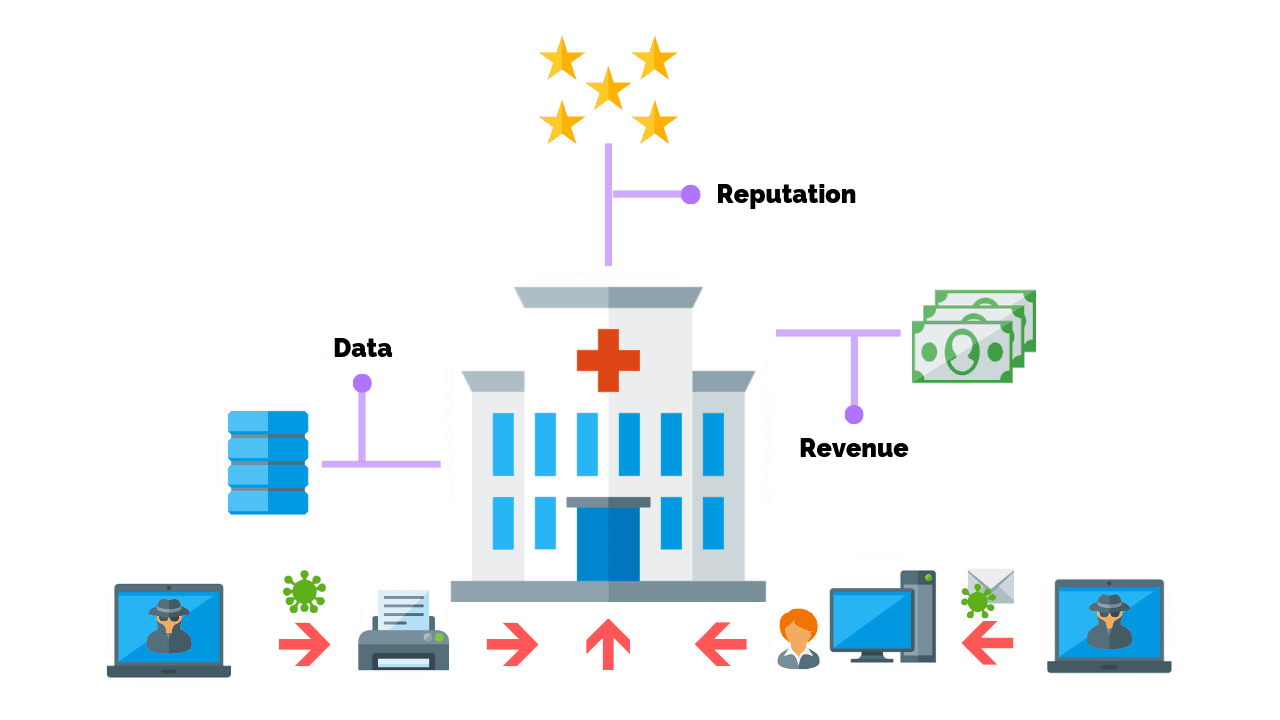
Our experts help healthcare providers identify risks to protected health information (PHI) and reduce the risk of fines and legal action
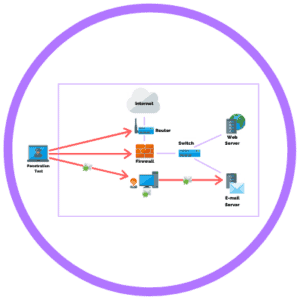
HIPAA Penetration Testing
NIST has issued a special recommendation for HIPAA that says, “Conduct trusted penetration testing of the effectiveness of security controls in place, if reasonable and appropriate. This validates your exposure to actual vulnerabilities.”
It also says to document any deficiencies that are identified in a technically detailed report and include effective, efficient, and clear methods for remediation. That is a NIST recommendation specifically for HIPAA.
All information that is created and/or stored on the tested systems will be removed from these systems. If this is for some reason not possible from a remote system, all these files (with their location) will be detailed in the technical report so that your technical staff will be able to remove these after the report has been received.
Incident Response Planning
Incident Response Plans are not a one-size-fits-all document. Each organization must adapt to encompass its unique requirements. That being said, certain best practices can help ensure that any entity’s IRP satisfies legal requirements, serves patients and customers, and protects its reputation.