How To Perform A Successful HIPAA Risk Assessment
Cyber security, specifically ransomware, continues to be a concern for healthcare professionals with 69% believing they are at risk for a data breach.
In fact, recent security trends, point to ransomware continuing to be the #1 threat facing healthcare providers in 2021. One step towards good cyber hygiene is by performing a HIPAA risk assessment.
In short, there are 5 main steps in performing a successful HIPAA risk assessment including defining key concepts and information flows, defining threats and vulnerabilities, conducting an initial risk assessment, developing control recommendations, and conducting a residual risk assessment.
In this article, I’m going to go in-depth on each step of the security risk assessment process. By the end, you will have the knowledge you need to guide your organization through a successful HIPAA Risk Assessment.
Article Navigation
- What Is A HIPAA Risk Assessment?
- Steps To Perform A HIPAA Risk Assessment
- HIPAA Risk Assessment FAQS
What Is A HIPAA Risk Assessment?
 Per the brief history of HIPAA noted in the introduction, the HIPAA Security Rule defines the requirement of the Risk Assessment.
Per the brief history of HIPAA noted in the introduction, the HIPAA Security Rule defines the requirement of the Risk Assessment.
It lays out three types of security safeguards required for compliance:
- Administrative
- Physical
- Technical
The HIPAA risk assessment helps an organization ensure that it is compliant with the three security safeguards by providing guidance on how to audit electronic patient health information (ePHI).
The risk assessment includes a thorough audit of potential risks and vulnerabilities that could impact the confidentiality, integrity, and availability of ePHI maintained by a healthcare organization or the covered entity.
Read more: How To Prevent Ransomware Attacks: An Expert Guide
Why Is HIPAA Compliance Important?
The Health Information Portability Accountability Act, commonly referred by its acronym HIPAA, was enacted by Congress in 1996.
One of the key goals of the legislation was to improve the portability of health insurance coverage, that is ensuring employees retained health insurance coverage between jobs.
HIPAA also made healthcare organizations accountable for health data and helped to ensure patient health information remains private and confidential.
After 1996, updates to the HIPAA act gave birth to sub-rules, such as the HIPAA Privacy Rule, HITECH, and the HIPAA Security Rule.
After 10 years of refining, the HIPAA Enforcement Rule became effective in 2006.
In 2013, the HIPAA Security Rule was updated and required a HIPAA risk assessment be performed on applicable entities or Business Associates.
The intent of this article is not to review every historical iteration of the HIPAA rules from its inception, rather we will discuss one of the core components of HIPAA that any organization handling health-related data must perform in order to meet the compliance requirements.
This core component is the HIPAA Risk Assessment.
In the next section, we will examine 5 key steps to successfully perform a HIPAA risk.
Steps To Perform A HIPAA Risk Assessment
There are 5 main steps to performing a HIPAA risk assessment including
- Define Key Concepts and Information Flows
- Define Threats and Vulnerabilities
- Conduct an Initial Risk Assessment
- Develop Control Recommendations
- Conduct a Residual Risk Assessment
Step 1: Define Key Concepts and Information Flows
This initial step sets the tone and overall scope of the assessment. This step identifies the whereabouts and types of assets an organization may use to create, transmit, or store ePHI.
Examples include smartphones, portable storage devices, or technologies such as email that transmit ePHI.
Once the assessor has defined the mediums that transmit ePHI, a determination of who has access to ePHI is also a critical component in this step.
The information obtained in this step will help the assessor establish areas of impact and document how ePHI flows within the organization.
Key concepts and steps listed below:
- Determine where the ePHI is in the organization.
- Determine who has access to ePHI in the organization.
- Document Impact Area
- Define and produce an Information Asset Flow Diagram(s)
- Review security policy
Step 2: Define Threats and Vulnerabilities
As mentioned earlier, the HIPAA Security Rule requires implementing security safeguards to protect ePHI.
In order to successfully determine weaknesses or whether a security safeguard is adequate, the assessor must have a working knowledge of the terms associated with the three security safeguards required for HIPAA compliance – Administrative, Physical, and Technical.
At times, the assessor may have to communicate with technical teams in the organization who oversees the deployment of security safeguards, therefore, this step is important to the success of the assessment.
See the list below of common terms that should be understood by the assessor:
Technical – Deliberate
- Ransomware
- Insider Threat
- Computer theft
- Keyloggers
- Trojan
- Phishing
Technical – Inadvertent
- Unintended email recipient of sensitive data
- Computer stolen – device left unattended in a public place
- Lost USB storage device containing sensitive data
Technical – Failure
- Lack of encryption
- Weak passwords
- Lack of malware protection
- Unidentified assets
- Unpatched systems
- Lack of file permissions
- Improper disposal of media
Physical Security
- Security Guards
- Building alarms
- Bollards
- Building access controls
- Access badges
- Security cameras
Social Engineering
Disaster Events
- Floods
- Hurricanes
- Tornados
- Typhoons
- Earthquakes
Step 3: Conduct an Initial Risk Assessment
This step is a critical component of the assessment. This step helps the assessor identify all threats to the confidentiality, integrity, and availability of ePHI.
In this step, vulnerable areas within the organization that can potentially be exploited by cyber actors, insider threat, user error, or natural events are identified.
Once the threats are identified, this information can be used to develop a risk management strategy to address the vulnerable areas.
A list of key vulnerable areas that may impact risk to the protection of ePHI:
Human – Deliberate
- Insider threat (disgruntled employee)
- Stealing corporate information
- Divulging corporate information
- Leaving backdoors on systems for later access
Human – Inadvertent
- Clicking a link in a phishing email
- Leaving sensitive information in an unsecured area
- Not locking computer console when away
- Sending sensitive email to incorrect recipient(s)
Technical Failure On Systems
- Lack of encryption
- Weak passwords
- Lack of malware protection
- Unidentified assets
- Unpatched systems
- Lack of file permissions
- Improper disposal of media
- Lack of backups for disaster recovery
Disaster (Natural and Man-Made)
- Office located in a flood zone
- Earthquake
- Tornado
- Hurricane
- Office Fire
- Wildfire
Step 4: Develop Control Recommendations
Understanding and having knowledge of a threat scenario is the foundation of any risk analysis.
By definition, a threat scenario occurs when a threat agent acts on an asset by exploiting vulnerabilities within an information system, person, or building where people are present.
An example of a threat scenario is an organization that allows weak passwords to access their unsecured patient web site on the internet.
A threat agent or hacker locates the site and steals employee passwords and patient data, laying the groundwork for a massive data breach.
Decreasing the impact that can be caused by a threat scenario by implementing controls.
An example is a disgruntled employee who has access to sensitive records. Terminating access to systems immediately is one example of decreasing impact caused by a potential threat scenario. Once the user account of employee is deprovisioned, they can no longer access network resources.
Decreasing the time and privacy available to threat sources at key points within the infrastructure is critical.
An example would be a hacker who sends medical personnel a phony email with a link to a gift card. The link fortunately does not work because the anti-virus software detected it immediately and notifies the support analyst, therefore, decreasing time for the threat source to cause an incident and exposes their covert activity.
Enhancing Incident Response capabilities is a critical control.
Today’s threats are targeted and are designed to hide undetected. Once the attack occurs, it usually spreads laterally and rapidly through an organization.
An effective Incident Response plan when executed properly notifies and alerts the appropriate teams into action to minimize the attack surface.
Enhancing Business Continuity and Disaster Recovery capabilities is key to an organization’s reputation and survival.
A ransomware attack once exploited in a healthcare environment can be damaging to the organization’s reputation.
One control used to reduce risk in this area is to consider investing in a cloud backup solution.
Related Article: What Is Cloud Penetration Testing? (& When Do You Need It?)
Implementing this control will enhance the effectiveness of the Business Continuity and Disaster Recovery plans by minimizing the likelihood of complete data loss.
Step 5: Conduct A Residual Risk Assessment
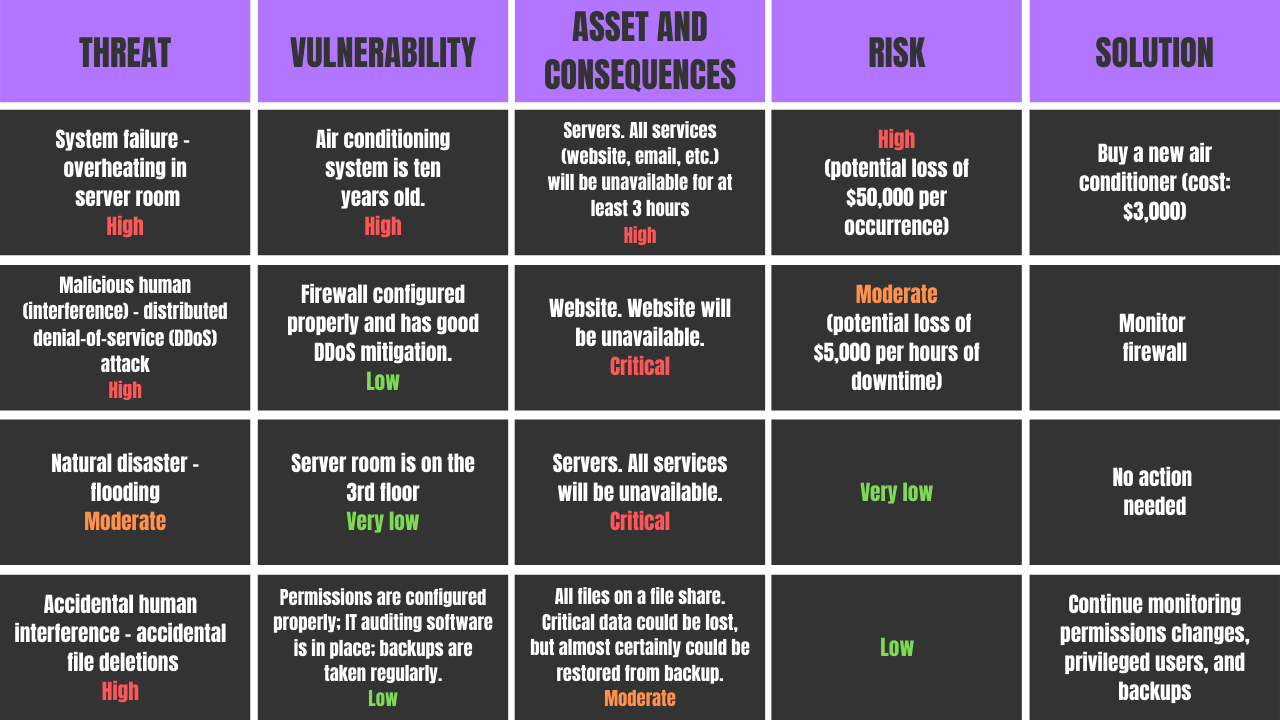
A useful tool in illustrating the relationship between assessment risk categories paired with various threats and vulnerabilities is to create a threat map.
This chart enables the assessor to visually demonstrate the level of risks currently in the environment and demonstrate how existing controls are reducing risk across identified assets.
The chart below illustrates a sample of threats, associated vulnerabilities, types of assets, risk, and the recommended solution to reduce the exploitation of the threat.
You will notice some of the terms listed in the chart are comparable to list of key terms documented in Step 2.
The above chart also enables the assessor to identify gaps and risks that are left over after a control has been implemented. This left-over risk after a control is applied is defined as residual risk.
An understanding of a residual risk is critical to the assessment.
Why is this the case?
Total elimination of risks in practical terms is highly unlikely, however, the goal of the risk assessment is to identify gaps in systems and helps determine the actions to bring risk to the lowest tolerable level an organization will accept.
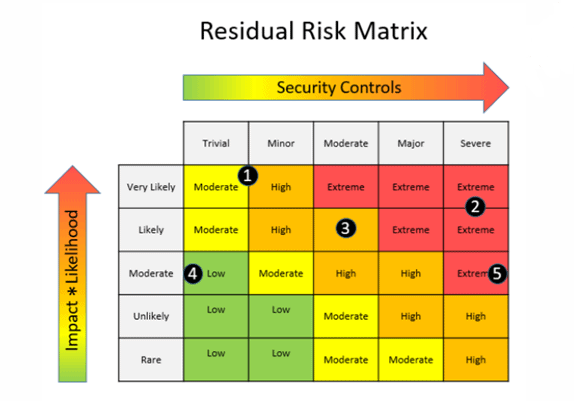
The chart below illustrates the residual risk and how it is measured once security controls are applied.
The arrow on the left measures the likelihood of a threat impacting an organization.
The security controls on the Y axis illustrates the prioritization of risk at certain level, as noted by the Risk ID values 1 to 5.
Note in the chart, that all the Risk ID’s are not lumped together in one area. Risk ID 4 has a low priority, and the other ID’s are spread out.
HIPAA Risk Assessment FAQs
What Is the Difference Between a HIPAA Risk Assessment and Risk Analysis?
A risk assessment involves many steps and forms the backbone of your overall risk management plan. A risk analysis is one of those steps—the one in which you determine the defining characteristics of each risk and assign each a score based on your findings.
Who Is Required to Perform A HIPAA Risk Assessment?
The HIPAA Security Rule and its standards apply to covered entities (CEs) and their business associates (BAs). A description of each entity is listed below.
Covered Entities
Covered entities deal directly and touch ePHI (electronic Patient Health Information. The covered entity includes hospitals, healthcare providers, insurance companies, and clearinghouses.
Business Associates
Business associates are non-healthcare industry professionals with access to ePHI. These professionals may serve CEs as third-party vendors. BAs include technology vendors, consultants, accounting firms, and attorneys.
How Much Does A HIPAA Risk Assessment Cost?
The cost of a security assessment can range from $10,000 for simple tests to over $50,000, depending on the size of the business, number of devices connected to the network, complexity of operations, and scope of the assessment.
Before you factor in an annual review and paying to address your vulnerabilities, the minimum you can expect to pay for a security risk assessment is approximately $15,000 USD.
Is A Risk Assessment Mandatory for HIPAA Compliance?
Yes. The Health Insurance Portability and Accountability Act (HIPAA) Security Rule requires that the CE (Covered Entity) and its BA (Business associate) conduct a risk assessment of their healthcare organization.
How Often Does A HIPAA Risk Assessment Need to Be Performed?
HIPAA does not specify how often risk assessments need to be performed. The law requires “regular” analysis of safeguards, although organizations can interpret this in many ways. At minimum, best practices dictate conducting an annual risk assessment; the threat landscape changes often enough to warrant a yearly review.
HIPAA recommends that CEs perform at least one risk assessment per year. Still, there are instances where additional yearly risk assessments are necessary. For example, you should run a new security risk assessment any time there is a new healthcare regulation.
BAs are also required to conduct annual security risk assessments under HIPAA’s Security Rule. Again, more than one yearly risk analysis may be necessary. For example, if the BA failed a previous risk assessment or has recently undergone a merger or acquisition, a second risk analysis may be proper.
What Should Be Included in A HIPAA Security Risk Assessment Report?
Regardless of whether the HIPAA security assessment is performed internally or externally, it should include evaluation of:
- Administrative, physical and technical safeguards
- Facility and workstation security
- Encryption protocols for email, devices, data storage, wireless connections and more
- Hardware and software that stores PHI
- Change management policies and procedures
- Monitoring downstream BAs
- Appropriate destruction and disposition of data
- Liability insurance
- ePHI vulnerability, which evaluates various areas where PHI resides
- Threat actions, which evaluates risk associated with power outages, weather-related threats, personnel-related threats and the like
Related Articles