Previous
Social Engineering: What Is It
And Why Is It Effective?
Reduce your attack surface with PurpleSec’s social engineering services.
Authors: Josh Allen & Jason Firch, MBA / Last Updated: 7/07/22
Featuring: Darius Burt, CISSP
Reviewed By: Michael Swanagan, CISSP, CISA, CISM
View Our: Editorial Process
Table Of Contents
- What Is A Social Engineering Attack?
- How Does Social Engineering Work?
- Types Of Social Engineering Attacks
- New Social Engineering Tactics & Techniques
- Why Is Social Engineering Such A Successful Form Of Cyber Attack?
- Why Social Media Contributes To The Success Of Social Engineering
- How Do You Prevent Social Engineering Attacks?
- How To Better Educate Staff On The Latest Social Engineering Attacks
- How Technology Will Influence The Evolution Of Social Engineering Attacks
In this section, we interview Darius Burt, CISSP, who is a cyber security leader and a frequent voice in the community on all things social engineering.
During the interview Darius answers our burning question:
Why does social engineering work?
Before we can dive into this topic we need to first understand what social engineering is and why it’s on the rise.
What You’ll Learn
- How human psychology is connected to social engineering.
- What personality types are most vulnerable to social engineering attacks.
- Three newer social engineering tactics in use by threat actors.
- How IT and security professionals can protect their organization from social engineering attacks.
- How businesses can educate employees of the latest attacks beyond computer training.
What Is A Social Engineering Attack?
Social engineering is a type of cyber attack where threat actors attempt to retrieve sensitive information by manipulating people into providing sensitive data, account credentials, or granting access to networks or systems.
Threat actors track our digital footprint to gather as much information as they can about an organization, its employees, and its vendors.
They then craft general or spear phishing campaigns by preying on our emotions or by impersonating authority figures to gain our credentials and personal information.
Social engineering is recognized as one of the greatest security threats facing organizations. It is extremely effective because the attacks are persuasive and very deceptive.
Who Are The Targets Of Social Engineering?
The target of any social engineering attack relies on the threat actors’ goal.
If they’re looking to only gain credentials, then they may generally target anyone in the company.
However, more often you’ll see targeted spear phishing, or whaling attacks against department heads likes the VP of finance or executives like the CEO or CFO.
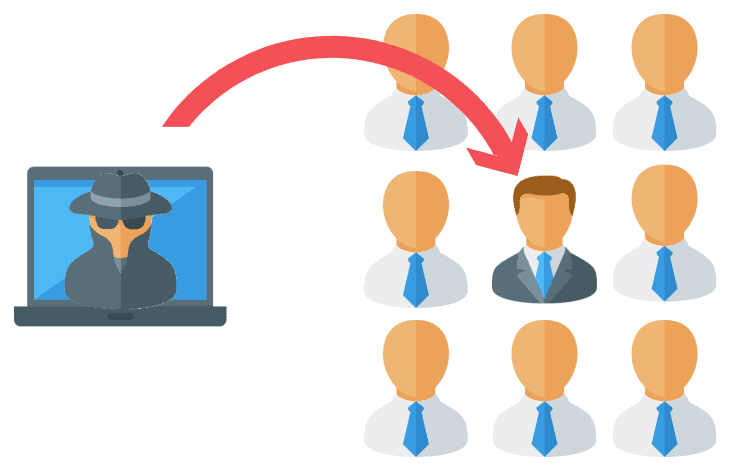
These targeted attackers will develop sophisticated social engineering campaigns by collecting freely available information online.
It may be through a company’s website. Or, a LinkedIn profile page.
This is a typical attack pattern and use case for business email compromise (BCE).
Once an attack is carried out the attacker may phish other employees to see if they can gain access to an account with system admin credentials.
Will Social Engineering Remain A Top Cyber Threat?
The short answer is – yes. Social engineering is here to stay.
Threat actors will continue to do what works. If it’s the easiest way in and the rewards outweigh any potential risk, then the attacks will continue.
In addition, some people just don’t care. They don’t care about the business, the security, or who their reckless actions might impact.
Threat actors will take advantage of this weakness and exploit it by bribing employees and there isn’t much businesses can do.
Having said that, implementing technical controls behind the first line defense of your people is critical for limiting the spread of the attack should an employee click an email.
How Does Social Engineering Work?
Today’s attackers are required to circumvent a number of security controls as businesses continue to invest into security including:
- Endpoint Detection & Response
- Antivirus
- Antimalware
- IPS and IDS
- Firewalls
- Security Information Event Management
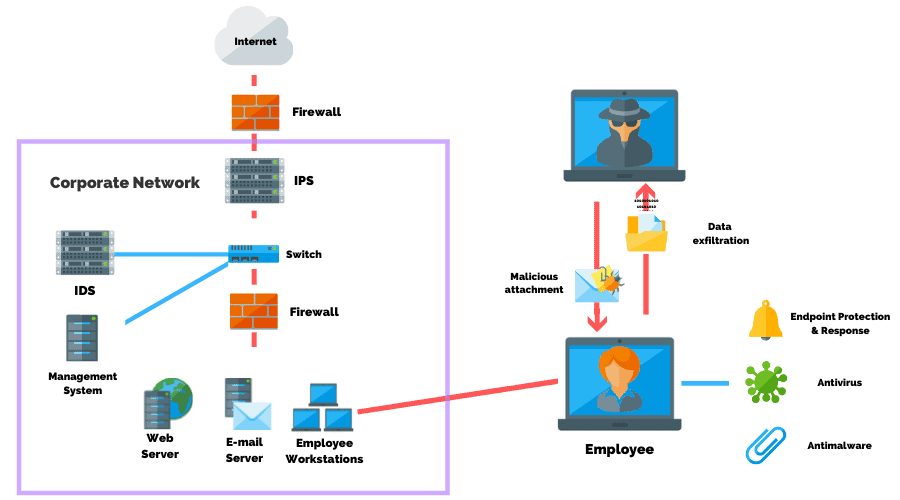
Social engineering is a common method used by threat actors, red teams, and penetration testing services, to bypass these controls in order to gain initial access to an organization’s systems.
Threat actors are not shy about sending millions of emails to people at one time.
All that’s needed for a successful campaign is for one or two of those emails to be clicked on.
You can consider your business breached as soon as a user clicks a malicious link – regardless of how much money was invested into tools.
Types Of Social Engineering Attacks
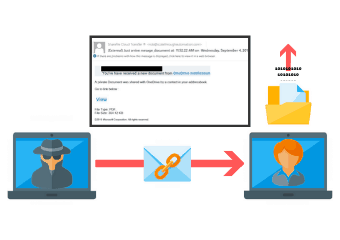
Phishing Attacks
Phishing refers to an attack that is usually sent in the form of a link embedded within an email. The email is disguised and looks like an email from a reliable source, but in reality, it’s a link to a malicious site.
Vishing (Voice Phishing)
![]()
Vishing attempts to trick victims into giving up sensitive information over the phone. In most cases, the attacker strategically manipulates human emotions, such as fear, sympathy, and greed in order to accomplish their goals.
This form of attack has been around since the early 2000’s, but has become increasingly prevalent in part due to the upward trend in the number of people working remotely today.
Smishing (SMS Phishing)
![]()
Smishing is a cyber attack that uses SMS text messages to mislead its victims into providing sensitive information to a cybercriminal.
URLs may be embedded in a short link into the text message, inviting the user to click on the link which in most cases is a redirect to a malicious site.
Watering Hole Attack
A watering hole attack consists of injecting malicious code into the public Web pages of a site that the targets used to visit. The method of injection is not new, and it is commonly used by cyber criminals and hackers.
The attackers compromise websites within a specific sector that are ordinarily visited by specific individuals of interest for the attacks.
Pretexting
An attacker can impersonate an external IT services operator to ask internal staff for information that could allow accessing the system within the organization.
Whaling Attacks

Whaling adopts the same methods of spear phishing attacks, but the scam email is designed to masquerade as a critical business email sent from a legitimate authority, typically from relevant executives of important organizations.
The word whaling is used, indicating that the target is a big fish to capture.
Tailgating
The tailgating attack, also known as “piggybacking,” involves an attacker seeking entry to a restricted area that lacks the proper authentication.
The attacker can simply walk in behind a person who is authorized to access the area.
In a typical attack scenario, a person impersonates a delivery driver or a caretaker who is packed with parcels and waits when an employee opens their door.
New Social Engineering Tactics & Techniques
Phishing, Vishing, and Smishing are all common social engineering techniques used today.
However, newer tactics are emerging with some of the worst offenders being:
Malicious QR Code Attacks
A malicious QR code attack is where a threat actor will replace a QR code with their own which when scanned redirects the user to a malicious site.
For example, visit almost any restaurant these days and you see the signs on the table with a QR code that you scan in order to get to the menu.
A legitimate QR code will take you to the website of that organization and the menu will be presented to you.
But because it’s just sitting there on the table anyone can replace it with their own QR code.
It may look exactly like the organization’s menu, however, as soon as you go to it, malware is dropped on your phone, and then the attacker has access to your phone.
Website & Mobile Push Notifications
The use of push notifications on websites has increased in use as an effective way for businesses to communicate with their visitors or customers.
You’ll find these notifications on websites or banners at the top that ask if you want to receive notifications from the website either by email or SMS.
Threat actors have begun to hack website push notifications and are replacing them with their own.
Once clicked, threat actors will spam you with email or attempt a drive-by malware attack.
Collaboration Scams
A collaboration scam is where a threat actor will send an email to someone who conducts security research asking them to collaborate on a project.
If the target responds to the email then they’ll receive an email with a link to the project document.
Once the document is opened it will infect the system and they’ll have access to whatever the security researcher was working on.
How PurpleSec Prevents Social Engineering
Our penetration testing services validate your organization’s security and test resilience against the latest attacks and APT techniques following MITRE’s ATT&CK framework.
Why Is Social Engineering Such A
Successful Form Of Cyber Attack?
Social engineering is involved in over 90% of all cyber attacks.
One answer for its growing popularity is that social engineering is easier and less expensive for threat actors.
Instead of developing or purchasing a zero day exploit threat actors simply trick a company’s employees into providing credentials.
This is why social engineering attacks are so successful and a crowd favorite as it doesn’t require nearly as much effort or technical skillset to penetrate into an environment.
Ultimately, social engineering attacks work because they prey on human vulnerabilities including:
- Reciprocity – People tend to return a favor, hence the pervasiveness of free samples in marketing.
- Commitment and consistency – If people commit to an idea or goal (orally or in writing), they are more likely to honor that commitment because it’s now congruent with their self-image. Even if the original incentive or motivation is removed after they have already committed, people will continue to honor the agreement.
- Social proof – People will do things that they see others doing.
- Authority – People will tend to obey authority figures, even if they’re asked by those figures to perform objectionable acts.
- Likability – People are easily persuaded by others that they like.
- Scarcity – Perceived scarcity will generate demand. For example, by saying offers are available for a “limited time only,” retailers encourage sales.
The good news is that we have an understanding of the problem, but at the same malicious actors have already created systems in place to exploit the above principles of human behavior.
How Social Engineering Is Related To Psychology
According to the American Psychological Association, psychology is the scientific study of the mind and behavior.
Social engineering relies on human behavior and the way humans think.
It takes advantage of our tendencies and decision making and is a direct correlation between psychology and susceptibility to social engineering attacks.
If you think about it, marketing is a non-malicious version of social engineering.
Data driven marketers analyze every interaction that a prospect has with their brand to update their messaging, fine tune their processes, and optimize for sales.
This is done by leveraging data insights into marketing campaigns that appeal to our desires and what we think we like in order to get us to buy a product or service.
The military has a similar established practice called information operations.
The Psychology Of Social Engineering
Psychology is all about what makes people tick while social engineering is the deliberate targeting of that human behavior and influencing someone to make a decision that they wouldn’t normally make under different circumstances.
Politicians, for example, thoroughly study their constituents to formulate the right messaging.
They know exactly what they want to say and who they want to say it to in order to keep that vote.
In an attack scenario, a social engineering campaign will involve a plan to influence you or an employee to:
- Click a malicious link
- Download a file or enable macros
- Open the building door
- Wire funds to the attacker’s account
- Provide account credentials
- Take some other action
What Personality Types Are Most Vulnerable To Social Engineering?
Agreeableness and Extraversion are the two most vulnerable personality types to social engineering.
This is according to Dr. Margaret Cunningham, the principal research scientist for human behavior with Forcepoint X-Labs in a recent interview with Myers-Briggs.
Agreeable people tend to be more willing to share information.
Meanwhile, extroverts tend to be more transparent when they start talking.
They are very open about what they do and who they are, thus making them more susceptible to social engineering.
What Personality Types Are Most Resilient To Social Engineering?
Conscientious people are less susceptible to social engineering attacks.
This personality trait tends to be more thorough and thinks through the actions they take or the decisions they make.
Why Social Media Contributes To The Success Of
Social Engineering Campaigns
Social media plays a large factor in the success of social engineering because it provides threat actors with a treasure trove of intelligence gathering.
As a threat actor, my first step will be to follow you on social media and maybe attempt to be your friend.
My goal would be to get to know as much information as I can about who you are, what you do, your interests, the types of food you eat, the car you drive, how much money you make.
Anything that would give me a foot into the door of your life.
People share too much information on social media – what they’re eating, where they’re going, or pet names.
This is the same information that we, unfortunately, use to create passwords.
From there all I would need is the nickname of your pet.
Since I also know your name I can blast a bunch of usernames that I think are associated with you.
Finally, I’d attempt passwords that I think might also be associated with the things that you post on social media.
How Do You Prevent Social Engineering Attacks?
There are a variety of ways you can prevent social engineering attacks whether in the office, working remotely, or surfing the web at home.
As a user, you can prevent falling victim to a social engineering attack by:
- Being Suspicious
- Not Providing Personal Information
- Not Providing Financial Information
- Not Sending Sensitive Data
- Paying Attention To URLs
- Verifying Company Contact Information
- Installing Attack Mitigations
Businesses will often invest in annual security awareness training or continuous simulated phishing campaigns as an additional layer of security.
It’s also common to install attack mitigations such as firewalls, antimalware, and email spam filters.
Implementing multifactor authentication is another useful security control that reduces 99.9% of automated malware attacks on Windows systems.
Be Suspicious
Be suspicious of unsolicited phone calls, visits, or email messages from individuals asking about employees or other internal information.
If an unknown individual claims to be from a legitimate organization, try to verify his or her identity directly with the company.
Do Not Provide Personal Information
Do not provide personal information or information about your organization, including its structure or networks, unless you are certain of a person’s authority to have the information.
Do Not Provide Financial Information
Do not reveal personal or financial information in email, and do not respond to email solicitations for this information. This includes following links sent in email.
Do Not Send Sensitive Information
Don’t send sensitive information over the Internet before checking a website’s security. (See Protecting Your Privacy for more information.)
Pay Attention To URLs
Pay attention to the Uniform Resource Locator (URL) of a website. Malicious websites may look identical to a legitimate site, but the URL may use a variation in spelling or a different domain (e.g., .com vs. .net).
Verify The Company Contacting You
If you are unsure whether an email request is legitimate, try to verify it by contacting the company directly.
Do not use contact information provided on a website connected to the request; instead, check previous statements for contact information.
Information about known phishing attacks is also available online from groups such as the Anti-Phishing Working Group.
Install Attack Mitigations
Install and maintain anti-virus software, firewalls, and email filters to reduce some of this traffic. (See Understanding Firewalls, Understanding Anti-Virus Software, and Reducing Spam for more information.)
Finally, take advantage of any anti-phishing features offered by your email client and web browser.
How To Better Educate Staff On The Latest Social Engineering Attacks
The best thing a business or employee can do to prevent social engineering is to be aware and establishing a security awareness program is a good goal to work towards.
Unfortunately, what tends to happen is people will do security awareness training as an annual requirement to satisfy compliance.
However, that can’t be the only time you’re educating staff.
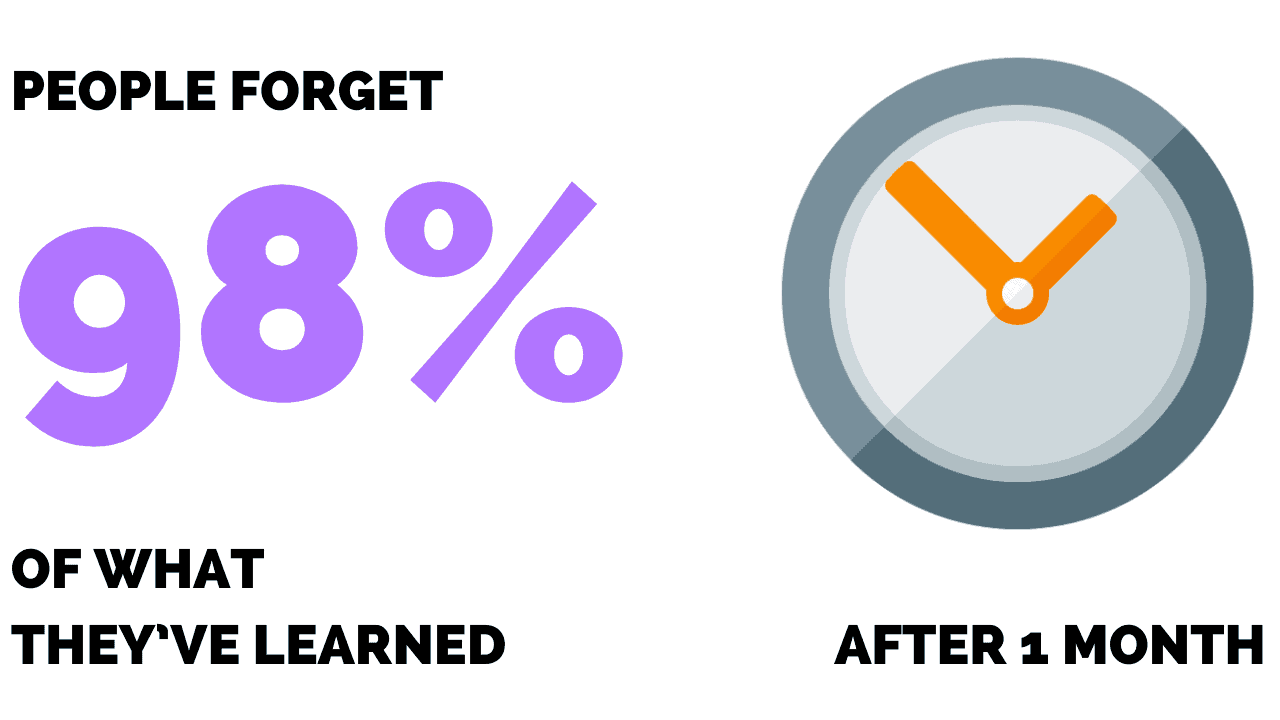
Research shows people forget 97-98% of what they’ve learned after one month.
This means if you’re not engaging employees on a quarterly basis then you’re not effectively educating them on emerging threats.
As a baseline, you should know how your organization compares against others.
We recommend reviewing the SANS Institute Security Awareness Mautirty Model™.
Next, it’s time to rethink how we deliver the training to employees.
Going Beyond Mundane Computer Based Training
Let’s face it – people don’t want to go through the same mundane computer based training, or PowerPoint slides year after year.
Self assessments, while cost effective, are creating a breed of employees who click through without paying attention to any of the information.
The employer may require the training as part of a PCI audit, however, the employee is more concerned about keeping up with their own workload.
Here are a few ways you can improve your employee’s engagement beyond the basics:
Create Engaging Content
The most important aspect of any security awareness training platform are its training modules.
The struggle here is balancing information with entertainment.
On one hand, we don’t want to bore employees. On the other hand, we need the message to resonate.
We recommend finding a platform that uses short form video and scenario based learning.
If you’re in a specific industry, such as healthcare, then you may wish to find a platform that has scenarios that speak to that audience or address HIPAA.
Conduct Phishing Simulations
Phishing simulations should be a regular exercise that’s conducted throughout the year.
The goal is to familiarize staff with what it’s like to be phished, while also benchmarking your businesses’ overall risk to social engineering.
If you really want to test your employees then try including vishing into your campaign.
According to some security professionals Voice Phishing (Vishing), has a success rate of 37%,
Recent research suggests that vishing alone has a success rate of 37%, but this increases to 75% when combined with email phishing.
Report Suspicious Emails
Employees should not only be trained on the signs of a suspicious email or phone call but also when and how to report these potential threats.
This is because employees play a valuable role in preventing the spread of a phishing campaign by reporting suspicious emails.
By reporting threats early, security and IT teams are able to quickly respond to and block malicious activity before a breach can occur.
Bring Awareness To Security Controls
You don’t know what you don’t know and in security, where the same acronym can mean two different things, it’s no wonder people get overwhelmed.
However, like most things, explaining the why behind the operations is a good remedy.
It’s important that employees are aware of the security controls that the business has in place and why they’re there.
Host A Learning Session
Learning sessions are a great way to share high-level and actionable information on topics that can be disseminated across your entire organization.
The objective is to bring employees into a room or virtual hangout and treat it like a conference.
You may also consider hiring guest speakers or a local expert to demonstrate how easy it might be to crack a password.
People will remember what they go through, which is why we recommend hosting these sessions at least annually.
How Technology Will Influence The Evolution Of
Social Engineering Attacks
Technology will make it easier maybe to bypass technical security controls.
Just as we automate all the mundane tasks that we do daily, so will threat actors who are looking to automate their attacks.
Tools already exist out there that can clone websites and create targeted emails with a spoofed email address.
As technology evolves, there is a need to be creative, as defenders, to figure out how to keep attackers out.
Especially when they come up with ways to bypass the technical controls in place.