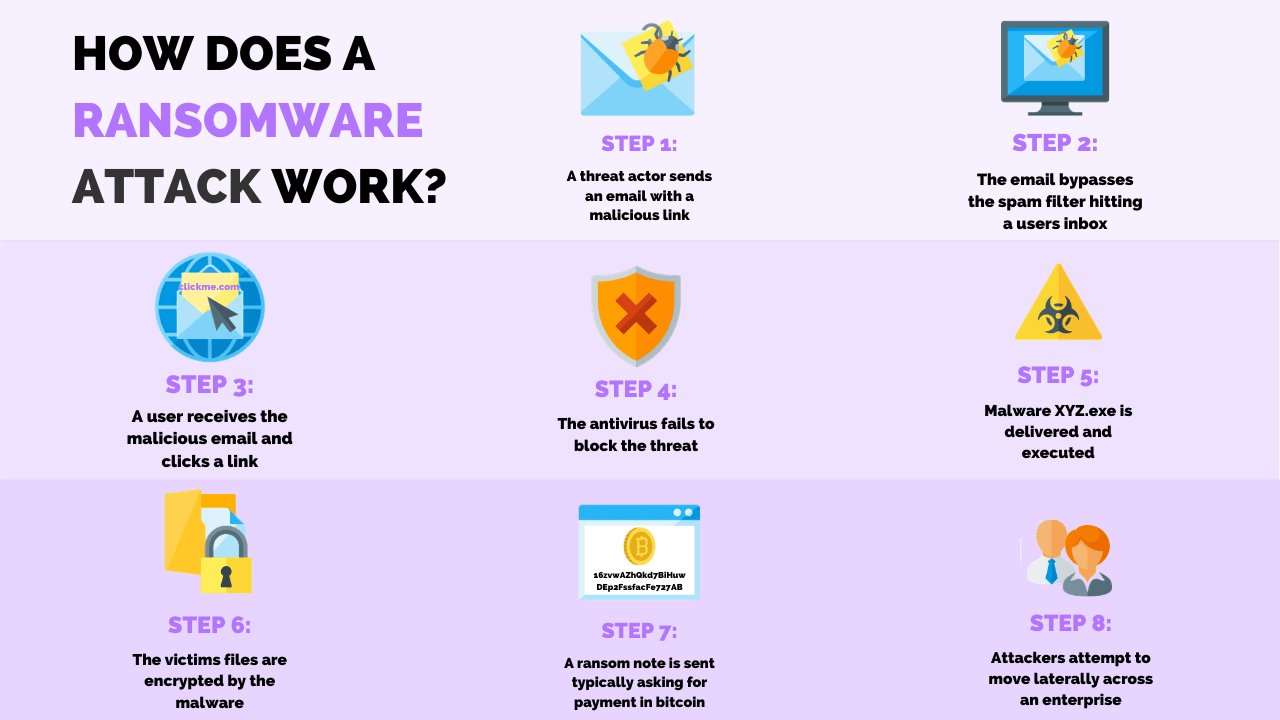
According to the State of Ransomware Report by Malwarebytes, ransomware attacks are at an all-time high with a 75% increase in the average number of monthly attacks.
As a result, a year-on-year increase in ransomware attacks grew 153% in 2023.
However, you can mitigate or prevent ransomware attacks by:
- Providing security awareness training.
- Implementing 3-factor authentication.
- Microsegmentating devices and users.
- Developing a ransomware response plan.
- Keeping systems up to date.
- Regularly backing up data.
- Having a disaster recovery plan.
- Performing red teaming or tabletop exercises.
- Working with a Virtual CISO.
- Using strong password policies and management tools.
Free Security Policy Templates
Get a step ahead of your cybersecurity goals with our comprehensive templates.

What Is Ransomware?
 Ransomware is a type of malicious software designed to deny users access to the files on their computers.
Ransomware is a type of malicious software designed to deny users access to the files on their computers.
It accomplishes this by encrypting these files so that only the malware operator can decrypt them.
A wide range of ransomware variants exists, including Ryuk, LockerGoga, and thousands of others. New variants are developed on a daily basis and used by threat actors against specific targets and for different purposes.
Read More: How Ransomware Spreads: 5 Common Methods
Ransomware attacks are so successful because they are so simple and have a clear psychological impact upon their target.
They can infect any type of computer (laptops/desktops, mobile devices, IoT, routers, cloud storage, etc.) and deny the owner access to the data stored on these systems.
How Do You Identify Ransomware On Your Network?
Like any type of malware, some ransomware variants can be detected using traditional signature-based antivirus and antimalware solutions.
However, malware authors are increasingly using zero-day attacks and polymorphic malware to evade these detection systems. As a result, signature-based antivirus only detects about half of malware.
The nature of ransomware also means that it can be detected by other means. To perform bulk encryption of a user’s files, the malware must open a large number of files, encrypt them, and destroy the original versions.
Since these are not actions typically taken by a legitimate user, they can be used to help detect and prevent a ransomware attack.
An organization’s SIEM solution and intrusion prevention systems (IPS) can be configured to include rules to detect these activities and take action.
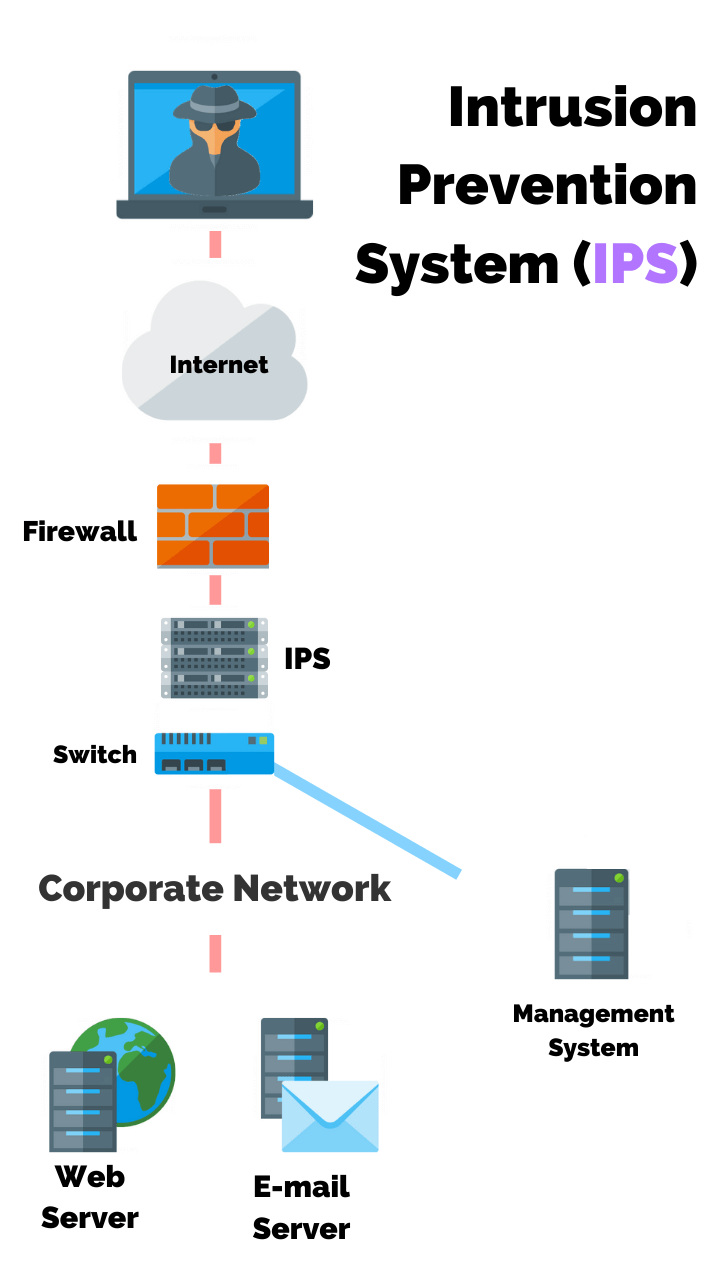
If a program on a computer is exhibiting this behavior, it should be immediately killed to minimize the impact of an attack.
Ransomware can also be detected based on its use of built-in functionality on a target computer. Many malware variants are now designed to “live off the land” by using Microsoft PowerShell to download and run malware.
Similarly, ransomware commonly accesses the operating system’s embedded cryptographic libraries for encryption. Monitoring for the use of these functions can also help to detect and block ransomware on a system.
How To Prevent Ransomware Attacks
A few practical ways to protect your business from ransomware attacks include:
- Provide Security Awareness Training – Give employees continuous security training to equip them with the knowledge to detect and respond to threats, reducing risk from 60% to 10%in the first 12 months.
- Implement 3 Factor Authentication– Add an extra layer of security with 3 factors – something you know, something you have, and something you are – to prevent 99.9% of password compromises.
- Microsegment Devices And Users – Break the network into isolated segments with restricted access to limit ransomware’s ability to spread throughout the system.
- Develop A Ransomware Response Plan – Create a plan outlining immediate steps to isolate infections and restore systems to minimize disruption from an attack.
- Keep Systems Up To Date – Adopt daily scanning and patching of vulnerabilities to significantly reduce the window of opportunity for exploitation.
- Regularly Back Up Data – Use a multifaceted backup strategy across cloud, physical, local, and offsite formats to ensure malware-free recovery options.
- Have A Disaster Recovery Plan – Define downtime tolerance, recovery procedures, and comprehensive testing strategies to mitigate ransomware impacts.
- Perform Red Team Or Table Top Exercises – Test incident response plans and leadership reactions to identify security gaps and improve readiness.
- Work With A Virtual CISO– Collaborate with an experienced advisor to design response plans and enable data-driven security decisions.
- Use Strong Password Policies And Management Tools – Enforce complex passwords, frequent rotation, and centralized control to prevent unauthorized access.
What Do You Do If You Fall Victim To A Ransomware Attack?
If a system has been infected by ransomware, a quick response is essential.
Ransomware rapidly encrypts files and attempts to spread itself to other systems, meaning that the impact of an attack grows rapidly if a response is delayed.
If a ransomware attack is detected, take the following actions:
- Quarantine the affected system: Ransomware variants will often try to spread themselves through the network. This can be done simply by unplugging the network cable.
- Notify the IT/security team: The team should have recovery procedures in place.
- Do not restart the computer: Some ransomware variants accidentally encrypt critical system files. A computer may not power back on after infection.
- Make a copy of the infected drive: Some ransomware decryptors, like Ryuk, will accidentally destroy files, even with the correct key.
- Attempt disk decryption with ransomware decryption tools: Decryptors have been released for flawed ransomware variants and may be able to perform decryption.
- Restore infected systems from clean versions: Ransomware may have persistence mechanisms that make them difficult to remove without a full wipe.
- Restore systems from clean backups: If possible, restore systems from backups that predate the ransomware infection. Always restore from a copy to protect the original.
- Sanitize removable media, connected drives, etc.: Ransomware commonly tries to spread by infecting other connected drives. These should be quarantined and sanitized to remove the infection.
The Ransom Dilemma - Should You Pay?
Best practice says that organizations should never pay a ransom after an attack. However, in some cases, business drivers force organizations to pay in order to regain access to critical data.
For example, if the value of the data is significant enough to force companies into making a payment, such as proprietary intellectual property.
The FBI recently released documentation outlining what to consider before paying a ransom:
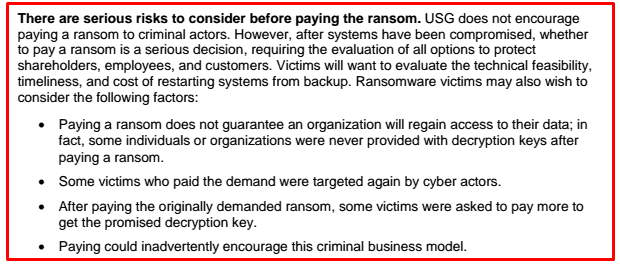
In practice, no real consensus exists on the topic of whether or not to pay a ransom. Additional factors mean that the choice is not always as simple as whether or not to pay.
On the one hand, paying a ransom theoretically gives an organization access to its encrypted data. However, this is not always the case. In fact, the decryptor for the Ryuk variant of ransomware has a programming bug that accidentally drops the last byte of a decrypted file.
In many files, this byte is unneeded padding, but, in others, it is essential to opening and parsing the file.
On the other hand, failing to pay a ransom means that the attacker gets nothing for their attack. Since the goal of a ransomware attack is to make a profit, some cybercriminals are taking action to prevent this. Some ransomware variants now steal sensitive data before encrypting it.
If the victim refuses to pay the ransom, the attacker threatens to sell this data to a competitor or publicly release it. If this data contains sensitive customer data, it would be considered a data breach under the General Data Protection Regulation (GDPR) and similar data privacy laws.
Conclusion
Ransomware is a significant security threat to any organization, but it’s entirely preventable. Taking action to minimize the probability of infection and ensuring that clean backups are available for system restoration can dramatically decrease the cost associated with a ransomware attack.
Article by