Organizations today are faced with the tremendous challenge of securing their data as they leverage the internet to conduct business.
Why the challenge?
Along with the old, attackers are continuously developing new threats to exploit vulnerable systems, smartphones, mobile applications, IoT devices, network equipment, and anything that is connected to the internet.
The number of events logged from these multiple data sources can be overwhelming and can lead to poor recognition of a real attack in process or one that is actively damaging systems.
To have an efficient process to support the management of incidents and events produced by multiple data systems, many organizations have implemented a solution known as Security Information and Event Management, commonly referred to as SIEM.
In this article, we will take a closer look at SIEM solutions.
We will define the SIEM, describe how it works, review the benefits and disadvantages of the SIEM, and review the top SIEM products on the market today.
By the end of this article, you will have a better understanding of SIEM and how to develop a successful deployment strategy to align with corporate security objectives.
Free Security Policy Templates
Get a step ahead of your cybersecurity goals with our comprehensive templates.

What Is A SIEM?
A Security Information And Event Management (SIEM) solution supports threat detection, compliance and security incident management through the collection and analysis (both near real-time and historical) of security events, as well as a wide variety of other event and contextual data sources.
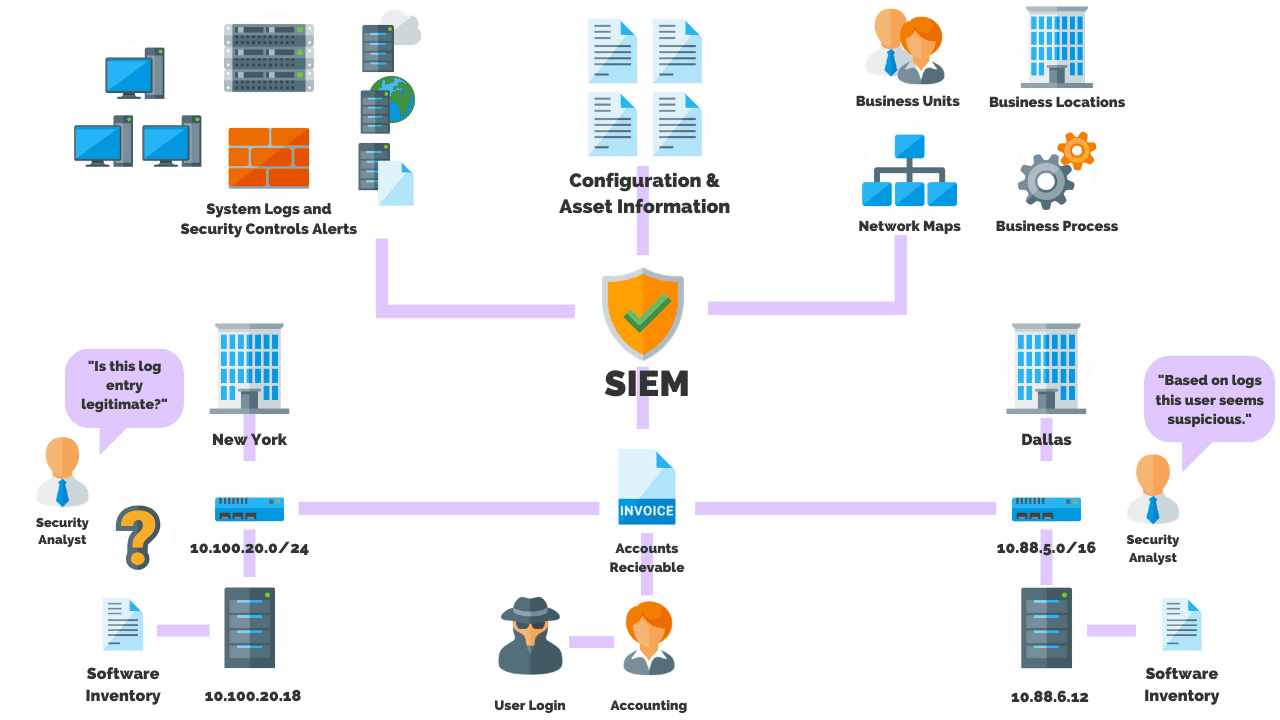
The core capabilities are a broad scope of log event collection and management, the ability to analyze log events and other data across disparate sources, and operational capabilities (such as incident management, dashboards and reporting).
Based on the definition, a SIEM enables IT staff to identify attacks before or as they occur, resulting in faster response times for incident response. SIEM technology is the foundation of an organization’s security strategy, which is critical for the success and continuous monitoring of the cybersecurity program.
The Evolution Of SIEM Technology
The actual term SIEM was coined by two Gartner analysts. In a 2005 Gartner report named Improve IT Security with Vulnerability Management, the analysts proposed a new security information system based on two previous-generation technologies known as Security Information Management (SIM) and Security Event Management (SEM).
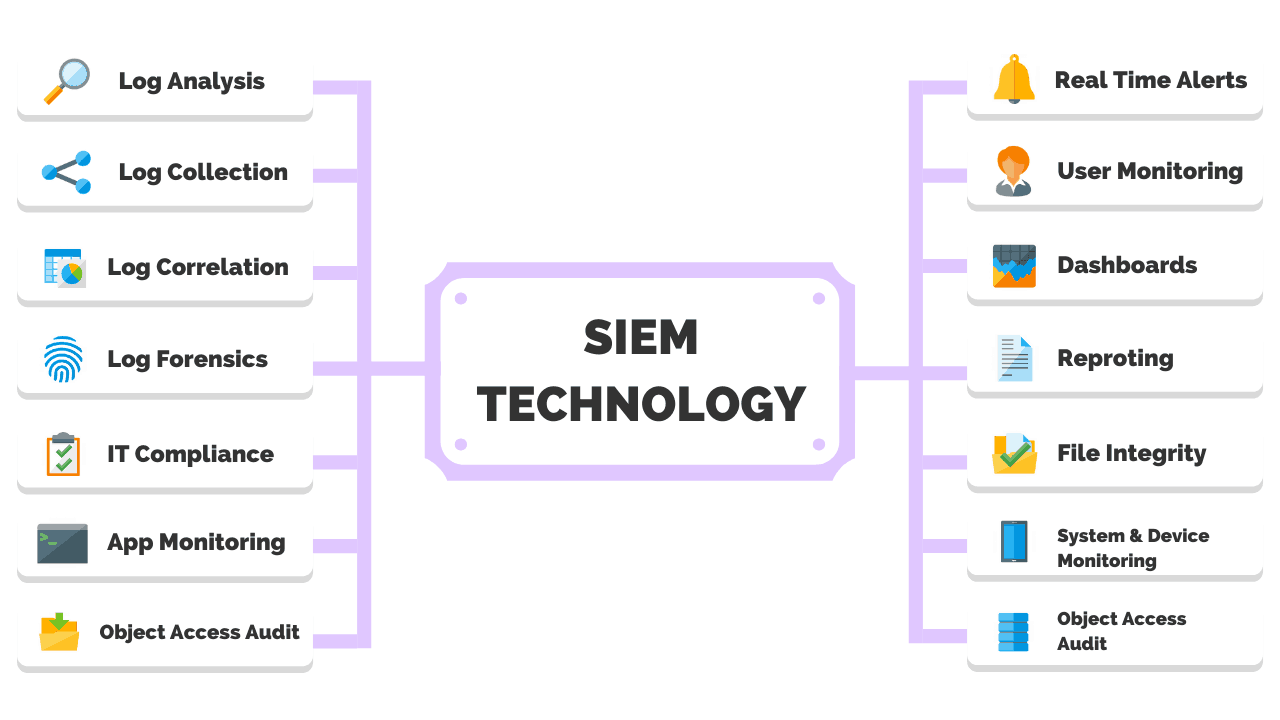
The first-generation SIM technology was built on top of traditional log collection management systems. SIM introduced long-term storage analysis, and reporting on log data, and combined logs with threat intelligence.
The second-generation SEM technology addressed security events, aggregation, correlation, and notification for events from security systems such as antivirus, firewalls, and Intrusion Detection Systems (IDS), as well as events reported directly by authentication, SNMP traps, servers, and databases.
A few years following, vendors introduced a combination of the SIM and SEM to create the SIEM, hence a new definition per Gartner’s research.
How Does A SIEM Work?
A SIEM solution works by collecting data from various sources such as computers, network devices, servers, and more.
The data is then normalized and aggregated. Next, security professionals analyze the data to discover and detect threats.
As a result, businesses can pinpoint security breaches and enable organizations to investigate alerts.
To best understand how the SIEM works, let’s first take a closer look at two key security concepts: incidents and events.
Security Incidents
A security incident is an occurrence that actually or potentially jeopardizes the confidentiality, integrity, or availability (CIA) of an information system or the information the system processes, stores, or transmits or that constitutes a violation or imminent threat of violation of security policies, security procedures, or acceptable use policies.
Examples of an incident include but are not limited to:
- Attempts (either failed or successful) to gain unauthorized access to a system or its data.
- Unwanted disruption or denial of service.
- The unauthorized use of a system for the processing or storage of data.
- Changes to system hardware, firmware, or software characteristics without the owner’s knowledge, instruction, or consent.
Security Events
A security event is any observable occurrence in an information system including:
- Operating systems
- Applications
- Devices
- Databases
How is the IT staff informed or made aware that they need to investigate a security event or incident? This is usually communicated via an alert.
The alert is a notification that a specific attack has been directed at an organization’s information systems. Alerts are brief in content and are usually directed to a specific individual or response team.
The notification is usually sent via an email, console pop-up message, or by text or phone call to a smartphone.
Depending on the number of events produced for each platform to be monitored, you can imagine the number of events logged can reach in hundreds to thousands per hour rather quickly.
Careful and precise tuning of the SIEM is required to detect and alert on events that pose the greatest risk.
It is this capability that sets the SIEM apart from other monitoring and detection tools on a network, such as an IPS or IDS. The SIEM doesn’t replace the logging functionality of these devices.
It simply works alongside these tools by ingesting and aggregating their log data to identify events that may lead to the potential exploit of a system.
Understanding The SIEM Process
The process of how the SIEM collects and alerts on detected events includes:
- Collecting data from various sources
- Normalizing and aggregating collected data
- Analyzing the data to discover and detect threats
- Pinpointing security breaches and enabling organizations to investigate alerts

What Are The Benefits Of A SIEM?
The benefits of an organization possessing a SIEM far outweigh the consequences of not having a SIEM. That is so long as the implementation of the security control is protecting something of greater value.
Without a SIEM, IT staff will lack a centralized view of all logs and events. With limited visibility, IT staff will more than likely miss critical events from their systems, leading to a high number of backlogged events that may contain incidents that require immediate investigation.
On the other hand, having a SIEM increases efficiencies and enhances the incident response program.
In addition to a centralized dashboard common to most SIEM products today, a well-tuned SIEM can notify on several pre-defined categories and event thresholds, as noted in the following scenarios:
- A firewall has logged five consecutive incorrect login attempts and has locked out the admin account.
- A web filter software has logged that a computer is connecting to a malicious website 100 times within one hour.
As mentioned, most modern SIEMs today have built-in intelligence that can detect configurable threshold limits and events per a certain period, along with summaries and customizable reporting.
More advanced SIEMs are now incorporating AI (Artificial Intelligence) to alert behavioral and pattern analysis.
The reporting and notification features enable the IT staff to react and respond quickly to potential incidents.
This intelligence reinforces the SIEM’s capability of detecting malicious attacks before they happen, such as detecting event patterns that resemble the early stages of a ransomware attack.
The SIEM’s presence on the network can reduce the cost of a full-blown security breach, saving an organization an untold amount of revenue and loss of reputation.
Today many regulated organizations, such as those in the Banking, Financial, Insurance, and Healthcare markets are required to attest that they have a managed SIEM on-premise or in the cloud.
The SIEM responds to security assessment control questions. They provide evidence that systems are monitored and logged, reviewed, and have log retention policies in place to satisfy compliance standards including ISO and HIPAA.
What Are The Disadvantages Of A SIEM?
The investment in a complete SIEM solution can be expensive. It’s not a ‘set it and forget it’ type of tool. It’s a complex technology that requires skilled IT engineers and analysts to manage and support.
The IT staff supporting the SIEM should be capable of tuning the system for relevant events, interpreting malicious attack patterns, and having demonstrated knowledge of the incident response process.
If the SIEM is not monitored 24x7x365 around the clock by the appropriate staff, it will add little or no business value to the security program and can leave the organization vulnerable to an attack.
Managed Solutions Service Providers (MSSP) are also an option if the technical expertise to manage the SIEM is not present within the organization.
If managed services are considered a viable option, prepare for a monthly premium for this level of expertise and support.
As noted in the cost table, a SIEM can be quite a substantial investment if the organization has multiple data sources that produce a large number of logged events.
Many SIEM vendors charge based on the number of alerts triggered and the amount of storage required to retain the events. Careful research is required to estimate the total cost of SIEM ownership.
Why Do SIEM Projects Fail?
To have a successful SIEM implementation, it’s imperative to understand the pain points and failures of other deployments.
There are several reasons why SIEM deployments fail including:
- Lack of Planning – Failure point: Lack of strategy for SIEM – capacity planning, limited proof of concept exercises with multiple vendors, understanding scalability, and having the right internal staff ask the right questions to the vendor.
- Lack of Goals & Objectives for SIEM Solution – Failure point: Senior Leadership is not engaged and board with the SIEM deployment and outcome
- Lack of Training – Failure point: The right knowledge is required to tune and configure SIEM. May require some scripting knowledge for advanced SIEM products
- Lack of Security Resources to Manage the SIEM Tool – Failure point: The tool is useless if there are not enough trained resources to support the SIEM
- SIEM Complexity – Failure point: A SIEM can generate thousands of events per hour. Support staff will need to know how to eliminate the ‘alert noise’ and correlate real events to maximize the value of the SIEM.
- Using SIEM Solely for Compliance – Failure point: Not realizing the full potential of SIEM value, such as malware detection, brute force attack handling, and user behavior monitoring.
- Not Speeding Up the Value with SIEM – Failure point: Not incorporating threat intelligence feeds with SIEM to help improve threat detection and response.
How To Avoid SIEM Deployment Pitfalls
When evaluating a new SIEM solution for an organization or considering making improvements to an existing one, be mindful that a SIEM is not the silver bullet to eliminate all security attacks and incidents.
Although it is a necessary component in an organization’s overall security program, a SIEM’s true value is achieved when it is combined with other threat response tools, such as SOAR – Security Orchestration, Automation, and Response.
What Is The Best SIEM Tool?
Since Gartner is responsible for the SIEM acronym, I would say they would be a good resource to identify the best and top SIEM’s. The top vendors in the market per Gartner research are listed in the LEADERS pane below:
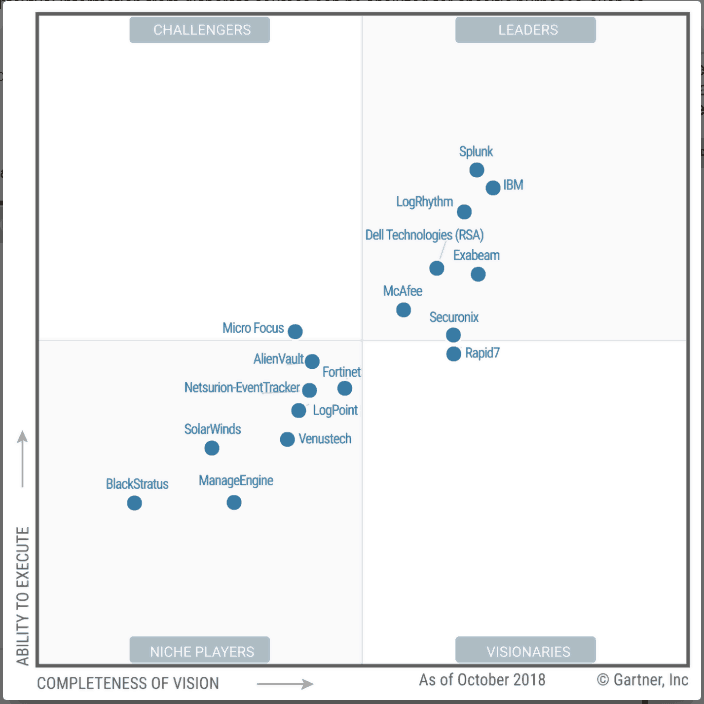
The seven SIEM vendors listed in the Gartner LEADER quadrant are listed below. Select each one to learn more about their differences and capabilities.
- Splunk Enterprise Security
- LogRhythm NextGen SIEM
- IBM QRadar
- Exabeam
- Securonix
- RSA NetWitness Suite
- McAfee Enterprise Security Manager
Splunk
Although a SIEM by definition has a primary function, each vendor (as listed in the Garter quadrant) has unique features that separate it from its competitors.
Splunk, for example, is capable of accepting hundreds of apps and add-ons which are designed to extend the capabilities across hundreds of various devices and applications.
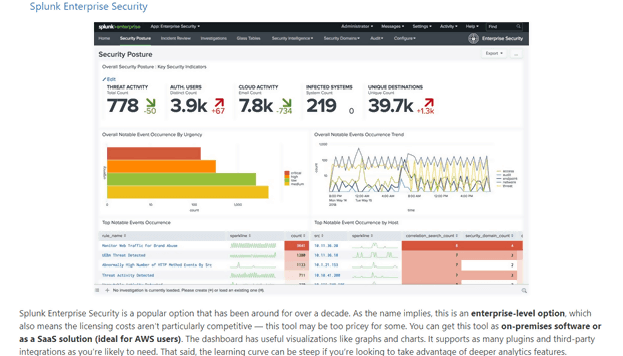
IBM QRadar Advisor
The IBM QRadar Advisor with Watson app is designed to complement the IBM QRadar Intelligence platform by helping analysts triage and investigate incidents.
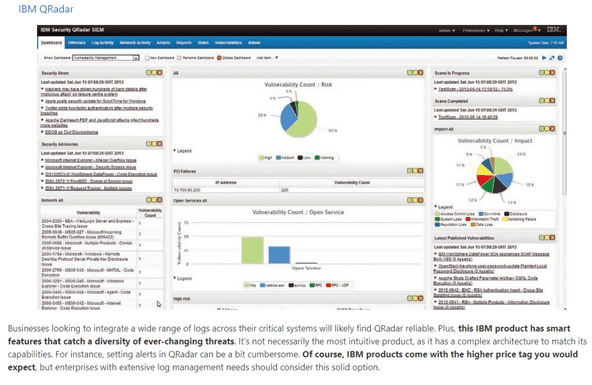
AlienVault
AlienVault is open-source and is a popular inexpensive cloud SIEM solution.
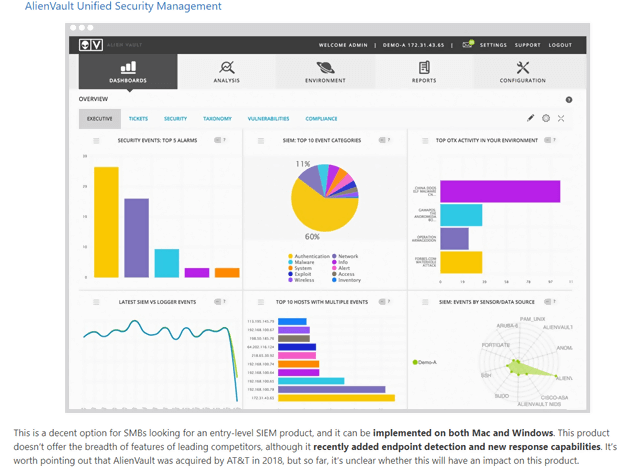
Splunk Enterprise Free
For a small business, there are free versions available that do the job such as Splunk Free, however, the feature set is reduced and the dashboard is lacking a few of the bells and whistles of the purchased version.
How Much Does A SIEM Solution Cost?
The cost of a SIEM varies across vendors. Each vendor utilizes different factors to arrive at the rate they charge for their services.
Depending on these factors you can expect to pay between $1,800 to $40,000 per year for a SIEM solution.
However, this does not include the cost of a security professional to analyze and interpret the logs. These positions have a salary that ranges from $60,000 to $100,000 per year.
| Vendor | Pricing Solution | Starting Annual Cost |
|---|---|---|
| Splunk Enterprise | $150 per Gigabyte of storage. | $1,800 |
| IBM Qradar | On Premise – based on events per second. | $10,400 |
| McAfee ESM | Cloud based VM. | $40,794 |
| AlienVault USM | User based – $640 up to 4TB of data. | $5,595 |
| SolarWinds | Based on nodes starting at 30 nodes. | $4,585 |
The table above provides an estimate of the projected cost based on variables such as storage used, events per second, number of users, and the number of devices or nodes.
Based on the sample above, Splunk Enterprise Free, SolarWinds, or AlienVault are possible choices for smaller businesses if they have lower storage requirements and/or a limited number of devices to manage.
It is also common today for vendors to partner with 3rd party resellers to sell their products. To receive the best pricing, contact the vendor directly and they will point you to a list of their preferred resellers for price quotes and annual maintenance cost.
Conclusion
One of the most important steps required to achieve a successful SIEM deployment is support from senior leadership, along with proper planning. It is critical to perform an audit and assessment of your internal environment before purchasing a SIEM.
This step will help determine storage requirements based on the volume of data and logs forwarded to the SIEM from various systems.
Another factor for success involves the research of multiple SIEM vendors. It is advisable to conduct multiple proofs of concept exercises as needed to observe the various features and scalability options offered by the vendor.
This will help determine the best solution that aligns with corporate security objectives.
The SIEM, as we have learned is a necessary tool designed to protect the organization from attacks that may cause harm to the business.
By avoiding the common pitfalls associated with SIEM deployments and leveraging its features alongside other security solutions, the SIEM will be an essential value add to a comprehensive cybersecurity strategy.
Article by