The main difference between an intrusion detection system (IDS) and an intrusion prevention system (IPS) is that an IDS is used to monitor a network, which then sends alerts when suspicious events on a system or network are detected. An IPS reacts to attacks in progress with the goal of preventing them from reaching targeted systems and networks.
While IDS and IPS both have the ability to detect attacks, the main difference is in their responses to an attack.
However, it’s important to note that both IDS and IPS can implement the same monitoring and detection methods.
Free Security Policy Templates
Get a step ahead of your cybersecurity goals with our comprehensive templates.

In this article, we will discuss the characteristics of an intrusion and the various attack methods threat actors employ to compromise a network.
Next, we’ll define IDS and IPS and review the functionality of each system and their respective roles in protecting the network.
By the end of this article, you will have a better understanding of the differences between an IDS and IPS.
Your awareness of the types of IDS and IPS solutions available on the market today will be enhanced, especially when they are combined into a single unit.
What Is An Intrusion Detection System (IDS)?
An Intrusion Detection System or IDS is defined as a computer network security technology originally built for detecting vulnerability exploits against a targeted application.
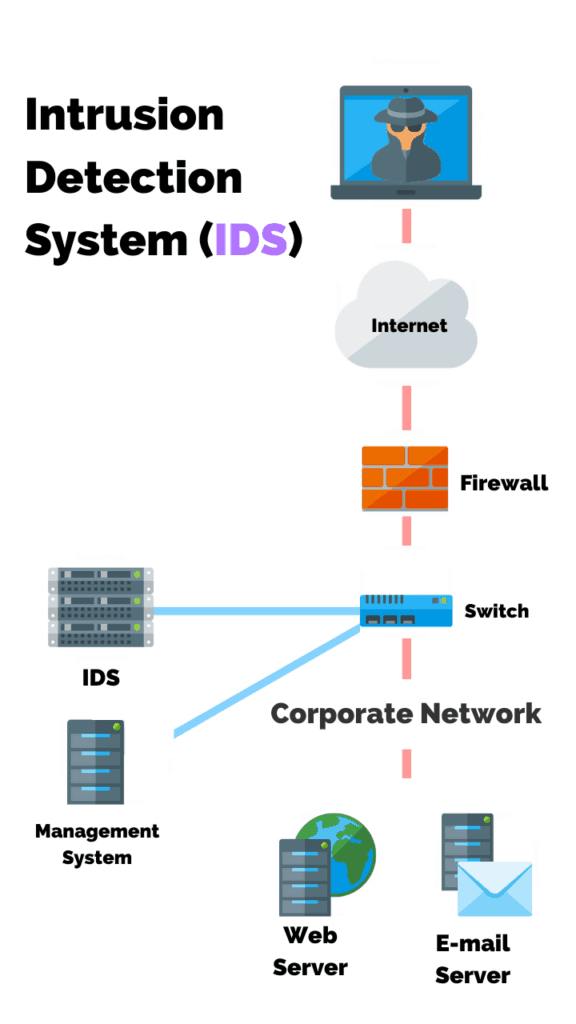
The IDS as the name implies is designed to detect network traffic patterns.
The IDS is not placed directly in line with the network traffic.
It is usually inserted in a tap or span port mirroring device to monitor and notify an administrator of alerts, without impacting the data flow.
This technology is what makes the IDS distinctly different than its counterpart, the IPS, which we will discuss further in this article.
How Does An Intrusion Detection System Work?
As mentioned in the outset of the article, additional layers of security are necessary to counter the intrusion attacks of today.
There are three common detection variants the IDS employs to monitor intrusions including:
- Signature-based
- Anomaly-based
- Reputation-based systems
1. Signature-Based Detection
Signature-based IDS detects possible threats by looking for specific patterns, such as byte sequences in network traffic, or known malicious instruction sequences used by malware.
This terminology originates from antivirus software, which refers to these detected patterns as signatures. Although signature-based IDS can easily detect known attacks, it is impossible to detect new attacks, for which no pattern is available.
2. Heuristic/Behavior Or Anomaly-Based IDS
Heuristic/behavior-based detection, also known as anomaly-based, is a newer technology designed to detect and adapt to unknown attacks, primarily due to the explosion of malware.
This detection method uses machine learning to create a defined model of trustworthy activity, and then compare new behavior against this trust model.
While this approach enables the detection of previously unknown attacks, it can suffer from false positives, which are previously unknown legitimate activities that can accidentally be classified as malicious.
However, it is still needed to monitor and analyze user and system activity, and audit system configurations, and vulnerabilities.
3. Reputation-Based
Reputation-based IDS track a file’s reputation so it can identify suspicious files.
What Are The Types Of Intrusion Detection Systems?
There are two main types of IDS including:
- A network intrusion detection system or NIDS.
- A host-based intrusion detection system (HIDS).
Network-Based Intrusion Detection System (NIDS)
Since the IDS is not in line with the network traffic, it can be placed strategically wherever the tap or span devices are located.
This feature allows the IDS to monitor and report on traffic flow in various areas of the network.
This type of intrusion protection is referred to as a Network Intrusion Detection System or NIDS.
As illustrated in the example below, the NIDS does not sit directly in line with the network traffic.
It reads a copy or mirror of the traffic per the network TAP device.
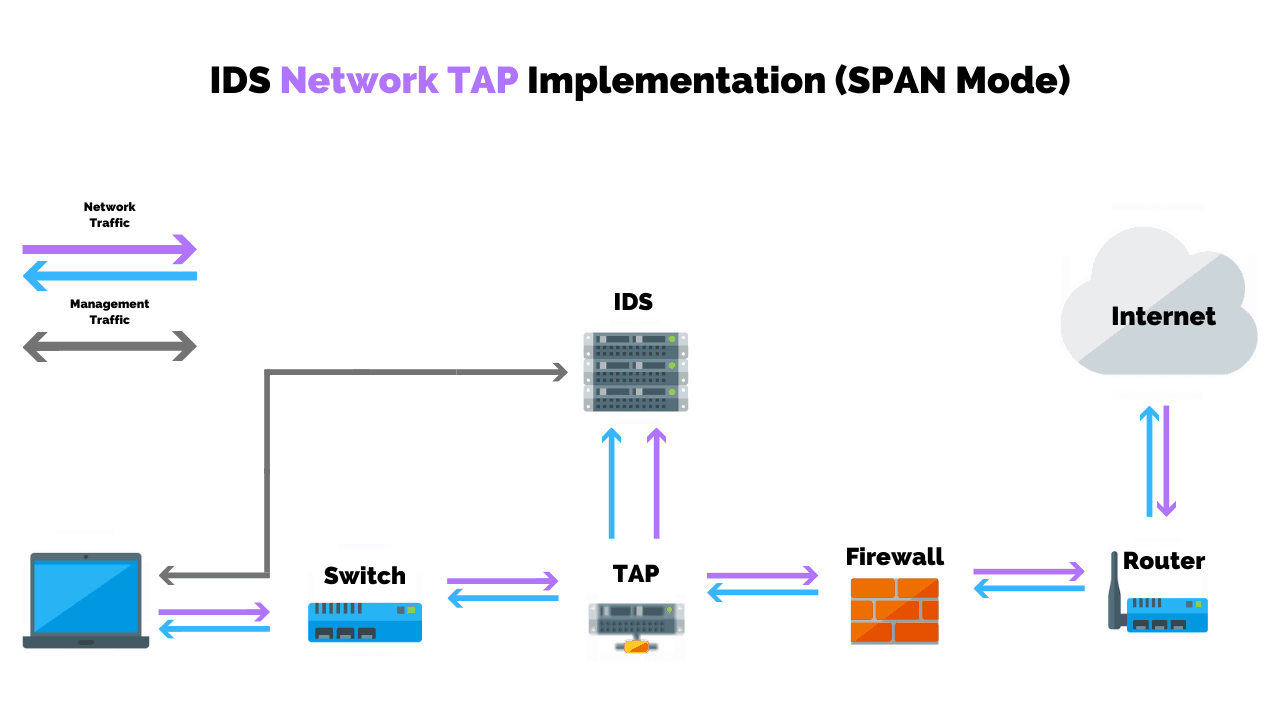
The admin or management console receives the alerts, however, network traffic flow is not altered or impeded.
Host-Based Intrusion Detection System (HIDS)
Another type of Intrusion Detection System is a software package that is installed on the endpoint or host device.
This type of system is referred to as a host intrusion detection system (HIDS).
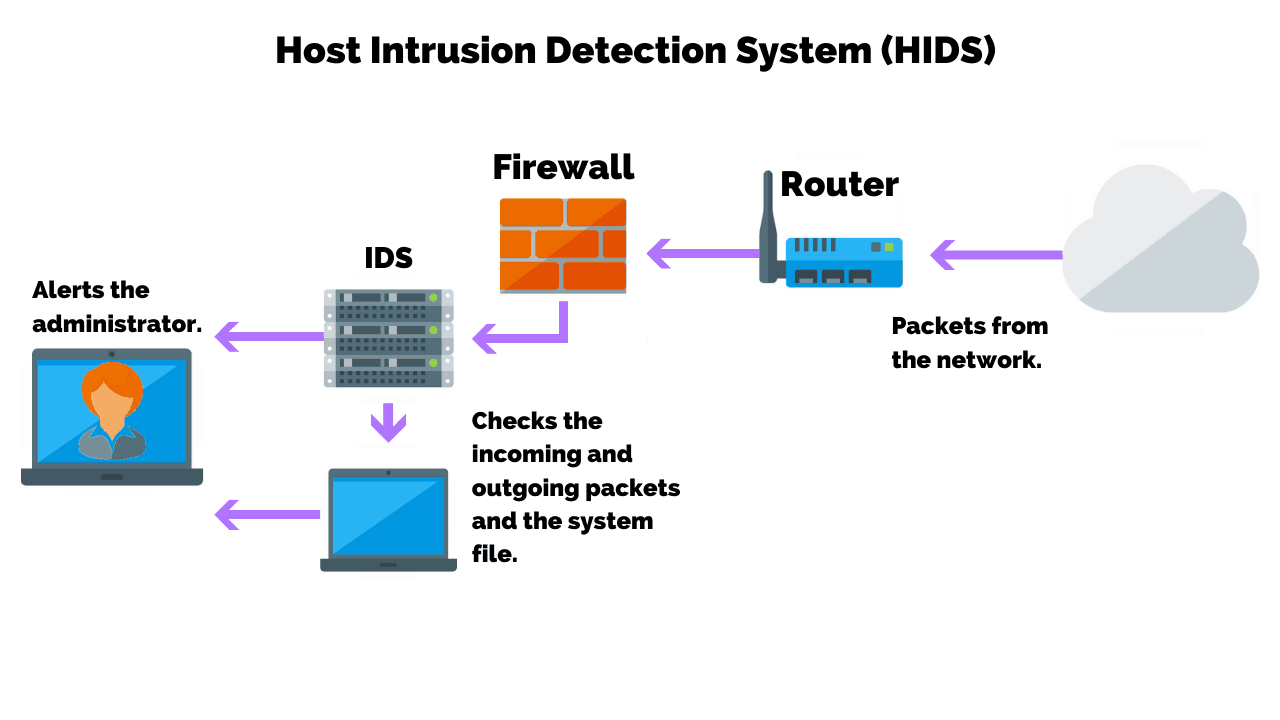
What Does A Host-Based IDS Monitor?
Popular anti-virus vendors include HIDS as part of their endpoint protection suite.
Instead of relying on mirrored traffic from a TAP device, HIDS software will examine events on a computer on your network.
This type of intrusion detection system mainly operates by looking at data in system files on the computer that it protects. Those files include log and configuration files.
What Is An Intrusion Prevention System (IPS)?
An Intrusion Prevention System or IPS is a network security and threat prevention technology that examines network traffic flows to detect and prevent vulnerability exploits.
The IPS often sits directly behind the firewall.
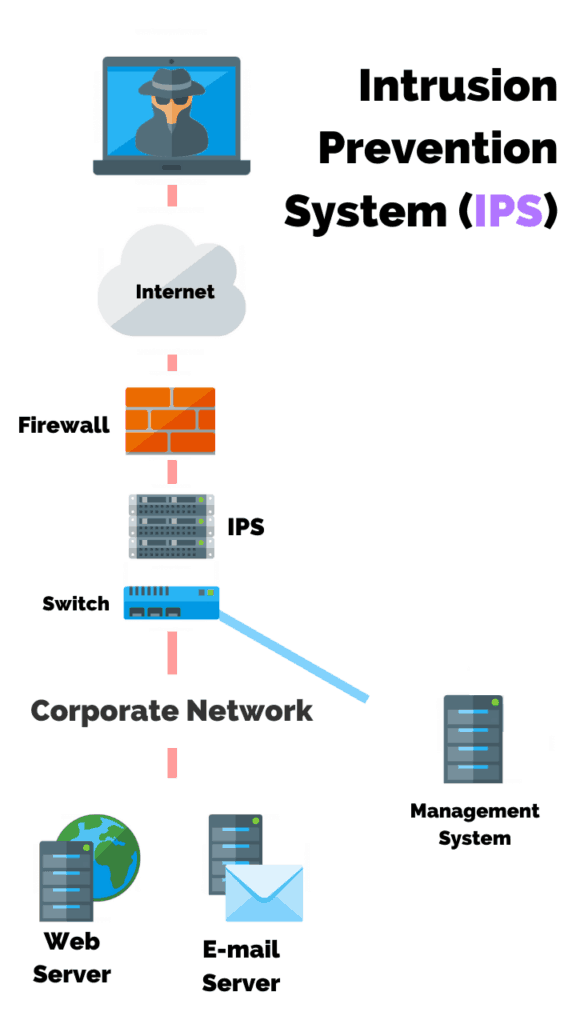
Unlike the IDS, the IPS is placed inline (in the direct communication path between source and destination), actively analyzing and taking automated actions on all traffic flows that enter the network.
This key feature is what distinguishes the IPS from the IDS.
How Does An Intrusion Prevention System Work?
Intrusion prevention systems work by scanning all network traffic. There are a number of different threats that an IPS is designed to prevent, including, but not limited to the following:
- Denial of Service (DoS) attack
- Various types of exploits
- Worms
- Viruses
When deployed correctly, an IPS prevents severe damage from being caused by malicious or unwanted packets, and brute force attacks.
The IPS performs real-time packet inspection, deeply inspecting every packet that travels across the network. If any malicious or suspicious packets are detected, the IPS will carry out one of the following actions:
- Terminate the TCP session that has been exploited.
- Block the offending source IP address or user account from accessing any application, target hosts or other network resources unethically.
- Reprogram or reconfigure the firewall to prevent a similar attack from occurring in the future.
- Remove or replace any malicious content that remains on the network following an attack. This is done by repackaging payloads, removing header information and removing any infected attachments from file or email servers.
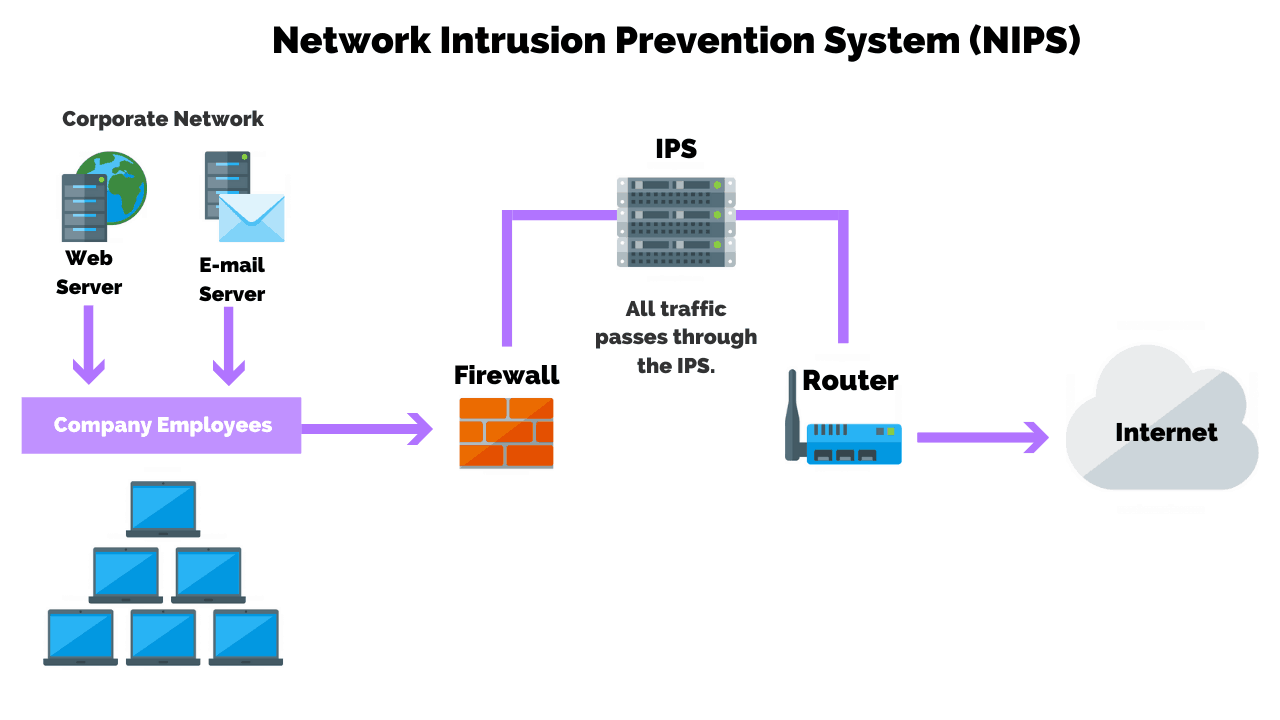
Similar to the IDS, an IPS is typically configured to use a number of different approaches to protect the network from unauthorized access. These include:
Signature-Based
The signature-based approach uses predefined signatures of well-known network threats. When an attack is initiated that matches one of these signatures or patterns, the system takes necessary action.
Anomaly-Based
The anomaly-based approach monitors for any abnormal or unexpected behavior on the network. If an anomaly is detected, the system blocks access to the target host immediately.
Policy-Based
This approach requires administrators to configure security policies according to organizational security policies and the network infrastructure.
When an activity occurs that violates a security policy, an alert is triggered and sent to the system administrators.
What Are The Types Of Intrusion Prevention Systems?
There are four main types of Intrusion Prevention Systems including:
- Network-based
- Wireless
- Network behavior
- Host-based
Network-Based IPS (NIPS)
A network-based IPS monitors the network for malicious activity or suspicious traffic by analyzing the protocol activity.
Network-based intrusion prevention systems or NIPS detect and prevent malicious activity by analyzing protocol packets throughout the entire network.
They are often referred to as IDS/IPS or Intrusion Detection and Prevention systems.
Once installed, NIPS gathers information from a host console and network to identify permitted hosts, applications, and operating systems commonly used throughout the network.
They also log information on characteristics of normal network traffic to identify any suspicious changes to a network.
NIPS can prevent attacks in a variety of ways, such as:
- By sending a TCP connection to prevent an attack.
- Limiting bandwidth usage.
- Rejecting suspicious network activity.
Today’s NIPS are even capable of commanding firewalls and routers to block suspicious activity.
A downside to NIPS is that it does not typically analyze encrypted network traffic, handle high traffic loads, or handle direct attacks against IDS/IPS.
NIPS primarily uses signature-based detection to identify threats.
Signature-based detection looks for patterns or signatures of previously recognized threats in order to identify potential new threats.
Wireless Intrusion Prevention System (WIPS)
A wireless intrusion prevention system (WIPS) operates at the Layer 2 (data link layer) level of the Open Systems Interconnection model.
WIPS can detect the presence of rogue or misconfigured devices and can prevent them from operating on wireless enterprise networks by scanning the network’s RFs for denial of service and other forms of attack.
Network Behavior IPS
This method primarily involves anomaly-based detection, which looks for deviations from what is known as “normal” behavior in system or network activity.
Upon initiation, anomaly-based detection requires a training period in which a profile for what is considered normal behavior is constructed over some time.
Inconsistencies with that profile are flagged as malicious.
Anomaly-based detection is outstanding for identifying new threats, but issues can arise if the network is compromised during the training period, as malicious behavior might be logged as normal while a profile is being generated.
Additionally, anomaly-based detection also produces many false positives due to benign activity that wasn’t recognized during the initial training period.
Stateful protocol analysis detection is similar to anomaly-based detection in that it looks for deviations from normal network or system behavior.
The baseline of normal behavior is outlined in universal vendor-created profiles.
Stateful protocol analysis is designed to differentiate between benign and suspicious activity in authenticated and unauthenticated states.
Host-Based IPS
Host-based intrusion prevention systems, or HIPS, analyze activity within a single host to detect and prevent malicious activity.
HIPS primarily analyzes code behavior, using both signature and anomaly-based detection methods to detect suspicious activity.
They are often lauded for preventing attacks that leverage encryption.
Similar to HIDS, many anti-malware solutions provide HIPS as part of their product suite.
HIPS can also prevent access to sensitive information located on the host, thus preventing any potential damage caused by rootkits or Trojan horses.
HIPS can also prevent the host machine from processing malicious activity on a network.
Since HIPS provides security only to a single host machine or server, it’s best used alongside IDS/IPS and WIPS to provide complete threat management throughout a network, providing a comprehensive program for prevention.
By now, you’ve probably noticed that the definitions and mode of operations of an IPS and IDS are different, yet close in their objective, which is to protect the network from intruders and their methods of attack.
So, what happens if you put the two technologies together?
Can IDS And IPS Work Together?
In short, yes an IDS and IPS can work together.
Around 2005, vendors combined the two technologies together to take advantage of their functionality.
In order for the IPS to even block any traffic, it has to first detect and inspect the traffic, which describes the functionality of the IDS.
Instead of two separate appliances performing two separate functions, it made perfect sense for firewall and other network product vendors to combine the two systems into one appliance.
This opened up an opportunity for a new term that is commonly used today, Next Generation, specifically, the Next Generation Firewall/NGFW and Unified Threat Management/UTM systems.
Although Gartner coined the term “next-generation firewall” in 2003 and predicted they would include IPS features and would be offered in 2006, NGFWs were not widely adopted until 2013.
At that time, they began including IDS/IPS functionality, such as using signatures to identify known attacks and looking for anomalies and protocol deviations in the packet flow.
When the technologies are combined into a single appliance, the administrator has options to deploy as an inline IPS, or detection only with sensors strategically placed to passively monitor network traffic.
This configuration model provides options for the administrator to utilize the device in prevent or detect mode.
Next-generation IDS/IPS have evolved in response to advanced targeted threats that can evade first-generation IDS/IPS.
A business may also wish to implement a SIEM solution alongside the IPS/IDS to ingest and aggregate log data to identify events that may lead to the potential exploit of a system.
What Is A Network Intrusion?
A network intrusion is any unauthorized activity on a digital network.
An intrusion compromises a computer system by breaking the security of such a system or causing it to enter into an insecure state.
Network intrusions often involve stealing valuable network resources and usually jeopardize the security of networks and their data.
Networks and endpoints are susceptible to intrusions from unintended sources named threat actors. A threat actor can reside anywhere in the world.
All they need is access to the internet, a motive, and a method or route of attack, which is commonly referred to as the threat vector.

Common types of network vulnerabilities that threaten the cyber security of a company include:
- Malware – Malware, or malicious software, is typically installed on a user’s machine or a host server. Types of malware include trojans, viruses, and worms.
- Social engineering attacks – Social engineering attempts to fool users into giving up personal information. These types of attacks include email phishing and whaling, vishing, waterhole attacks, and tailgating.
- Outdated or unpatched software – Software applications that are left unpatched which exposes systems running the application and potentially the entire network.
- Web Server Exploits – Smartphones, tablets, and other mobile devices can be used as devices to pass malware and other attacks on to the corporate network. Additionally, mobile malware may be used to steal useful data from the mobile device.
- Data Storage Devices – Portable storage devices such as unencrypted USB or Flash drives.
Your network security team must address these factors when assessing the overall security posture of your systems.
One way to do this is by performing routine security vulnerability assessments.
Wrapping Up
When evaluating a security solution for your corporate infrastructure or home, keep in mind that internet security threats are becoming more silent and dangerous.
A layered security system that merges signature and behavior-based technologies with other tools will enable you to level the playing field against threat actors and their attack methods.
The combined functionality of the intrusion prevention system, whether network or host-based, is one tool worthy of consideration and has its critical place in the securing of corporate network infrastructures and personal computers.
Article by