What Is A Smishing Attack? (And How To Prevent It)
98% of cyber attacks rely on social engineering to collect sensitive data or gain access to system(s) and network(s).
This is because phishing campaigns, like Smishing, are capable of bypassing more sophisticated security controls such as two-factor authentication (2FA).
In this article, I’m going to explain what Smishing attacks are, the common types of smishing scams used by threat actors, how you can identify a Smishing attack, and steps your business can take to prevent an attack.
Article Navigation
- What Is Smishing?
- Why Are Smishing Attacks Performed?
- Example Of A Smishing Attack
- What Are The Most Common Smishing Scams?
- How To Spot A Smishing Attack
- What Steps Can You Take To Prevent A Smishing Attack?
- How Do You Recover From A Smishing Attack?
What Is Smishing?
Smishing is a cyber attack that uses SMS text messages to mislead its victims into providing sensitive information to a cybercriminal.
Sensitive information includes your account name and password, name, banking account or credit card numbers. The cybercriminal may also embed a short url link into the text message, inviting the user to click on the link which in most cases is a redirect to a malicious site.
Smishing is related to two other ‘ishing’ cyber-attacks, phishing and vishing. Let’s examine the key differences and the similarities of the three attacks.
- Vishing utilizes VoIP technology to trick a victim into giving up sensitive information over the phone. The attacker pretends to be from an authoritative or reputable source, such as a bank, technical support, or IRS representative.
- Phishing is a social engineering email attack that usually targets someone in authority or a person who may have access to sensitive information in a corporate environment.
- A Smishing attack utilizes texting technology that is available on mobile devices today. Despite the differences in the attack methods, the end goal of all three ‘ishing’ attacks from the cybercriminals perspective is to illegally profit on the disclosure of sensitive information about you or your employer.
Why Are Smishing Attacks Performed?
Cybercriminals today are primarily motivated by financial gain. They develop code designed to obfuscate your sensitive information for profit. When they obtain this data, they may look to sell your compromised credit card or credentials on the dark web.
They may also use sensitive data to open an account in your name or hold your data ransom in exchange for a large payout.
Motivated cybercriminals utilize smishing due to the enormous volume of mobile devices connected to the Internet today. The attack surface is so vast that an attacker can skillfully craft a text message and broadcast to thousands of addresses in a matter of seconds.
Example Of A Smishing Attack
The message in a smishing attack is similar in content to a phishing or vishing attack. The message is crafted to get you to react and respond immediately. A smishing attack can be difficult to identify.
We are accustomed to receiving brief text messages from people we know, and if there is a URL embedded in the message, how do you tell if it’s fake or not in a text?
Let’s take a look at two examples, and note carefully the methods used to carry out the smish attack.
In the message on the left, the text appears to be from a well-known financial institution, which may be the bank of the victim.
The message on the right claims to be from Apple Support. This of course would be irrelevant to the potential victim if they have an Android, but what if they do possess an iPhone along with their Apple-ID?
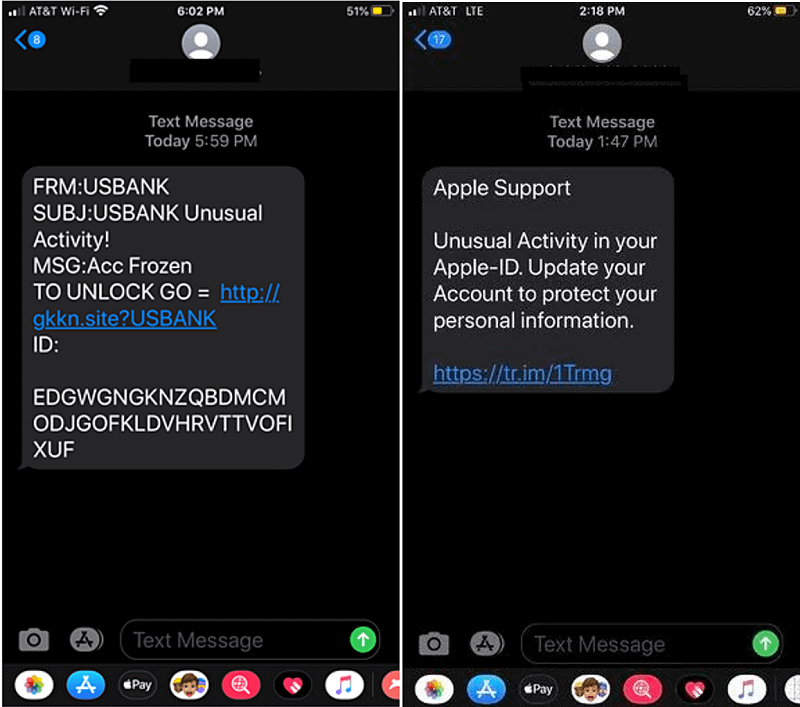
In both of these examples, the end user may be enticed to click on the links.
Why?
One reason may be that they are customers of the bank and they do have an Apple-ID. The attackers are fully aware of how a person may react to a text from their bank or if their prized Apple-ID account has been compromised.
We’ll look at steps to help spot whether this is a smish in the upcoming topics.
What Are The Most Common Smishing Scams?
Urgent text messaging from your bank are common smishing scams, as noted in the previous example.
Back in May 2018, Fifth 3rd Bank customers were the targets of a smishing attack. The attackers pretended to represent Fifth 3rd Bank. They devised a scheme to warn customers that their accounts were locked.
Within the body of the text message, they provided a link for the customers to unlock their account. As you probably guessed, the scheme worked.
Let’s explain why.
The link took the unsuspecting customer to a fake site that looked similar to Fifth 3rd’s real web site. The phishing site prompted the visitors to enter their user name and password, one-time code and PIN codes to unlock their account.
The cybercriminals then used the stolen account information to expunge nearly 68,000 from 17 ATM’s across three states.
Another common attack used by cybercriminals is to pretend to be your friend or co-worker.
The attackers will send a text informing the would-be victim that a gift card is available. In order to claim the card, you must read the security code on the back. Once that is done, the attacker owns the card and your account information.
How To Spot A Smishing Attack
Be mindful of unsolicited text messages from unknown sources. If you don’t recognize the number or name of the text sender, delete it. Google is a powerful tool, research the source of the text to determine if they are legitimate.
Most companies that conduct business in the US are registered with the Better Business Bureau. Don’t hesitate to reach out to the company directly to find out if they send text messages to prospective merchants.
On the other hand, what if you receive a text message from a company that you do have an account with, such as your bank or your mobile provider?
Recall the two examples in the screenshots listed earlier in the article. If this was your account, what are the clues to help identify if the SMS text was from a legitimate source or an attempt to smish?
- Is the message urgent and requiring me to click on a link immediately?
- Have I previously setup this type of notification on my account?
- Does the short URL in the message look like it’s a message from my bank or Apple support?
- In the URL, should the bank be requesting me to logon to an unsecured web link – http compared to https?
- I’ve already registered my account and my bank knows my identity, why would they text me to update my account?
If you answered Yes or No to any of these questions, this may be a targeted smish attack. Both earlier examples fit the description of a smish and will help you identify this attack.
What Steps Can You Take To Prevent A Smishing Attack?
Prevention of smishing attacks will require attention to detail. One major prevention tip is to avoid clicking links within text messages, especially if they are sent from someone you don’t know or have not confirmed as a method of notification.
This is worth repeating.
Similar to the examples provided earlier in this article, be mindful that attack messages can appear to come from someone you conduct business with, so avoid clicking and logon to the website or call their support to confirm the text message.
Here’s a few tips you can use to prevent smishing attacks:
- Don’t respond to text messages that request private or financial information from you.
- If you get a message that appears to be from your bank, financial institution, or other entity that you do business with, contact that business directly to determine if they sent you a legitimate request. Review this entity’s policy on sending text messages to customers.
- Beware of messages that have a number that says it is from “5000” or some other number that is not a cell number. Scammers often mask their identity by using email-to-text services to avoid revealing their actual phone number.
- If a text message is urging you to act or respond quickly, stop and think about it. Remember that criminals use this as a tactic to get you to do what they want.
- Never reply to a suspicious text message without doing your research and verifying the source. If your bank is really going to cancel your credit card, you should be able to call the number on the back of your card to discuss this matter with them.
- Never call a phone number from an unknown texter.
Interestingly, this list was published back in 2013.
This goes to show how long smishing has been around and will continue to be a major tactic of cybercriminals.
The only difference since the article was written is the volume of mobile phones available around the globe today, which has increased the attack surface for the cybercriminal.
Mobile phones operating systems also change frequently. Apply and update to the latest applicable Android or iOs patches as they are released.
How Do You Recover From A Smishing Attack?
If you become a victim of a smishing attack, there are a few steps to help you recover and prevent future attacks.
- If you’re phone is a corporate phone issued by your employer, immediately notify your IT Support team of the incident. Most corporate IT teams have tools to remotely wipe the phone and may have a backup of the corporate data. They can also advise on additional recovery options as needed.
- Blocking the number is a best practice to prevent the attacker from resurfacing. The FTC (Federal Trade Commission) has a complaint online site that allows you to report unsolicited text messages.
- If you suspect your credit information has been compromised, immediately contact the credit bureaus to freeze your credit or request their guidance on recovery steps.
Conclusion
Mobile technology provides an instant and efficient means to communicate with business partners, workmates, friends and family.
As long as the cybercriminals have the motivation to disrupt and profit from weaknesses in mobile communications and lack of social awareness, the threat of smishing attacks is something all owners of mobile devices will have to contend with on a daily basis.
The best defense in protecting your personal and corporate information is to be constantly on the offensive. This includes being knowledgeable of the various schemes cybercriminals employ in smishing attacks, as well as incorporating the prevention recommendations highlighted in this article.
Be vigilant and cautious as you conduct business and communications with your mobile devices. By following sound prevention steps outlined in this article, you will be in a position to identify and prevent becoming the next victim of a smishing attack.
Related Articles
- Social Engineering Penetration Testing: Attacks, Methods, & Steps
- How To Identify, Prevent, & Remove Ransomware Attacks
- What’s The Difference Between Phishing & Whaling Attacks?
- Vulnerability Scanning VS Penetration Testing: What’s The Main Difference?
- What Is A Social Engineering Attack And How Does It Work?