Red and blue teams are more than just Halo references and army techniques.
In fact, these teams play an important role in defending against advanced cyber attacks that threaten business communications, sensitive client data, or trade secrets.
Red teams are offensive security professionals who are experts in attacking systems and breaking into defenses. Blue teams are defensive security professionals responsible for maintaining internal network defenses against all cyber attacks and threats.
Red teams simulate attacks against blue teams to test the effectiveness of the network’s security. These red and blue team exercises provide a holistic security solution ensuring strong defenses while keeping in view evolving threats.
Free IT Security Policies
Get a step ahead of your goals with our comprehensive templates.

What Is A Red Team?
A red team consists of security professionals who act as adversaries to overcome cybersecurity controls. Red teams often consist of independent ethical hackers who evaluate system security in an objective manner.
They utilize all the available techniques (discussed below) to find weaknesses in people, processes, and technology to gain unauthorized access to assets. As a result of these simulated attacks, red teams make recommendations and plans on how to strengthen an organization’s security posture.
How Does A Red Team Work?
You might be surprised to learn (like I was) that red teams spend more time planning an attack then they do performing attacks. In fact, red teams deploy a number of methods to gain access to a network.
Social engineering attacks, for example, rely on reconnaissance and research to deliver targeted spear phishing campaigns. Likewise, prior to performing a penetration test, packet sniffers and protocol analyzers are used to scan the network and gather as much information about the system as possible.
Typical information gathered during this phase includes:
- Uncovering operating systems in use (Windows, macOS, or Linux).
- Identifying the make and model of networking equipment (servers, firewalls, switches, routers, access points, computers, etc.).
- Understanding physical controls (doors, locks, cameras, security personnel).
- Learning what ports are open/closed on a firewall to allow/block specific traffic.
- Creating a map of the network to determine what hosts are running what services along with where traffic is being sent.
Once the red team has a more complete idea of the system they develop a plan of action designed to target vulnerabilities specific to the information they gathered above.
For example, a red team member may know that a server is running Microsoft Windows Server 2016 R2 (a server operating system) and that the default domain policies might still be in use.
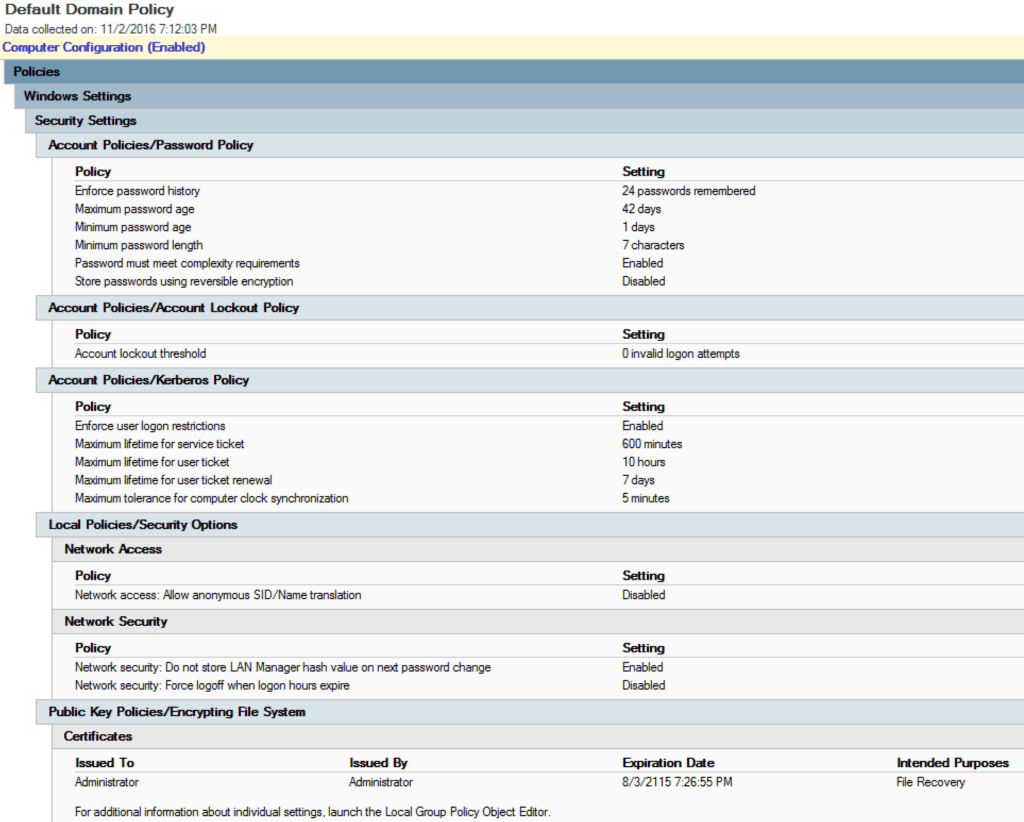
Microsoft “ships” their software in its default state leaving it up to network administrators to update the policies, which Microsoft recommends you do as soon as possible to harden network security.
If still set to its default state, an attacker can work to compromise the relaxed security measures in place.
After vulnerabilities are identified, a red team tries to exploit those weaknesses to gain access into your network.
Once an attacker is in your system the typical course of action is to use privilege escalation techniques, whereby the attacker attempts to steal the credentials of an administrator who has greater/full access to the highest levels of critical information.
The Tiger Team
In the early days of network security, a tiger team carried out many of the same functions as a red team.
The term has evolved over the years now referring to tiger teams as an elite and highly specialized group hired to take on a particular challenge against the security posture of an organization.
Examples Of Red Team Exercises
Red teams use a variety of methods and tools to exploit weaknesses and vulnerabilities in a network. It’s important to note that red teams will use any means necessary, per the terms of engagement, to break into your system.
Depending on the vulnerability they may deploy malware to infect hosts or even bypass physical security controls by cloning access cards.
Examples of red team exercises include:
- Penetration testing, also known as ethical hacking, is where the tester tries to gain access to a system, often using software tools. For example, ‘John the Ripper’ is a password-cracking program. It can detect what type of encryption is used, and try to bypass it.
- Social engineering is where the Red Team attempts to persuade or trick members of staff into disclosing their credentials or allowing access to a restricted area.
- Phishing entails sending apparently-authentic emails that entice staff members to take certain actions, such as logging into the hacker’s website and entering credentials.
- Intercepting communication software tools such as packet sniffers and protocol analyzers can be used to map a network, or read messages sent in clear text. The purpose of these tools is to gain information on the system. For example, if an attacker knows a server is running on a Microsoft operating system then they would focus their attacks to exploit Microsoft vulnerabilities.
- Card cloning of an employee’s security card to grant access into unrestricted areas, such as a server room.
What Is A Blue Team?
A blue team consists of security professionals who have an inside out view of the organization. Their task is to protect the organization’s critical assets against any kind of threat.
They are well aware of the business objectives and the organization’s cybersecurity strategy. Therefore, their task is to strengthen the castle walls so no intruder can compromise the defenses.
How Does A Blue Team Work?
The blue team first gathers data, documents exactly what needs to be protected and carries out a risk assessment.
They then tighten up access to the system in many ways, including introducing stronger password policies and educating staff to ensure they understand and conform to security procedures.
Monitoring tools are often put in place, allowing information regarding access to the systems to be logged and checked for unusual activity.
Blue teams will perform regular checks on the system, for example, DNS audits, internal or external network vulnerability scans and capturing sample network traffic for analysis.
Blue teams have to establish security measures around key assets of an organization.
They start their defensive plan by identifying the critical assets, document the importance of these assets to the business and what impact the absence of these assets will have.
Blue teams then perform risk assessments by identifying threats against each asset and the weaknesses these threats can exploit.
By evaluating the risks and prioritizing it, the blue team develops an action plan to implement controls that can lower the impact or likelihood of threats materializing against assets.
Senior management involvement is crucial at this stage as only they can decide to accept a risk or implement mitigating controls against it.
The selection of controls is often based on a cost-benefit analysis to ensure security controls deliver maximum value to the business.
For example, a blue team may identify that the company’s network is vulnerable to a DDoS (distributed denial of service) attack.
This attack reduces the availability of the network to legitimate users by sending incomplete traffic requests to a server.
Each of these requests requires resources to perform an action, which is why the attack severely cripples a network.
The team then calculates the loss in case the threat occurs.
Based on cost-benefit analysis and aligning with business objectives, a blue team would consider installing an intrusion detection and prevention system to minimize the risk of DDoS attacks.
Examples Of Blue Team Exercises
Blue teams use a variety of methods and tools as countermeasures to protect a network from cyber attacks.
Depending on the situation a blue team may determine that additional firewalls need to be installed to block access to an internal network.
Or, the risk to social engineering attacks is so critical that it warrants the cost of implementing security awareness training company-wide.
Examples of blue team exercises include:
- Performing DNS audits (domain name server) to prevent phishing attacks, avoid stale DNS issues, avoid downtime from DNS record deletions, and prevent/reduce DNS and web attacks.
- Conducting digital footprint analysis to tracks users’ activity and identify any known signatures that might indicate a breach of security.
- Installing endpoint security software on external devices such as laptops and smartphones.
- Ensuring firewall access controls are properly configured and that antivirus software are kept up to date
- Deploying IDS and IPS software as a detective and preventive security control.
- Implementing SIEM solutions to log and ingest network activity.
- Analyzing logs and memory to pick up unusual activity on the system, and identify and pinpoint an attack.
- Segregating networks and ensure they are configured correctly.
- Performing routine vulnerability scans.
- Securing systems by using antivirus or anti-malware software.
- Embedding security in processes.
How Do Red And Blue Team Exercises Help An Organization?
Implementing a red and blue team strategy allows an organization to benefit from two totally different approaches and skillsets.
It also brings a certain amount of competitiveness into the task, which encourages high performance on part of both teams.
The red team is valuable, in that it identifies vulnerabilities, but it can only highlight the current status of the system.
Benefits Of Red Teams
- Identify vulnerabilities: Red teams can help organizations identify vulnerabilities in their systems and networks. By highlighting these weaknesses in the organization’s defenses and a red team can help organizations take proactive measures to address them.
- Test defenses and response capabilities: By simulating a real attack scenario, organizations can evaluate their response capabilities and identify areas where they need to improve. Compensating controls can then be implemented to ensure these types of attacks cannot compromise the organization.
- Foster a culture of cyber security: Red team exercises also help to foster a culture of cyber security within an organization. By showing employees how attacks happen and the impact they can have, organizations can improve their employee’s awareness of cyber security risks.
On the other hand, the blue team is valuable in that it gives long term protection by ensuring defenses remain strong, and by constant monitoring of the system.
Benefits of Blue Teams
- Improve cyber security readiness: Blue teams can help organizations identify gaps in their cybersecurity defenses. By practicing response scenarios in a controlled environment, organizations can develop their incident response plans and ensure that they have the appropriate tools and processes in place to mitigate or deter cyber attacks.
- Enhance collaboration and communication: Blue team exercises can foster collaboration and communication between different teams within an organization, such as IT, security, and business units. Teams can better understand each other’s roles and responsibilities with the objective of improving their ability to work together in the event of a real attack.
- Train staff: Blue teams also help organizations train their staff in cyber security best practices. The aim is to help teams develop the skills and knowledge they need to respond to cyber incidents. As a result, staff gain hands-on experience in identifying and responding to cyber threats.
Learn More: How To Implement Social Engineering Awareness Training
While there is some overlap in both teams and their benefits the key advantage is the continual improvement in the security posture of the organization by finding gaps and then filling those gaps with appropriate controls.
How Do Red And Blue Teams Work Together?
Communication between the two teams is the most important factor in successful red and blue team exercises.
The blue team should stay up to date on the new technologies for improving security and should share these findings with the red team. Likewise, the red team should always be aware of new threats and penetration techniques used by hackers and advise the blue team on prevention techniques.
Depending on the goal of your test will depend on whether or not the red team informs the blue team of a planned test. For example, if the goal is to simulate a real response scenario to a “legitimate” threat, then you wouldn’t want to tell the blue team about the test.
The caveat is that someone in management should be aware of the test, typically the blue team lead. This ensures the response scenario is still tested, but with tighter control when/if the situation is escalated.
When the test is complete both teams gather information and report on their findings. The red team advises the blue team if they manage to penetrate defenses, and provide advice on how to block similar attempts in a real scenario. Likewise, the blue team should let the red team know whether or not their monitoring procedures picked up an attempted attack.
Both teams should then work together to plan, develop, and implement stronger security controls as needed.
What Is A Purple Team?
 While red teams and blue teams share common goals, they’re often not politically aligned.
While red teams and blue teams share common goals, they’re often not politically aligned.
For example, red teams who report on vulnerabilities are praised for a job well done. Therefore, they’re not incentivized to help the blue team strengthen their security by sharing information on how they bypassed their security.
There’s also no point in “winning” red team tests if you’re not sharing that information with the blue team. Remember, the main purpose of red and blue team exercises is to strengthen the overall security posture of the organization.
That’s where the concept of a purple team comes into place. A purple team isn’t necessarily a stand alone team, although it could be.
The goal of a purple team is to bring both red and blue teams together while encouraging them to work as a team to share insights and create a strong feedback loop.
Management should ensure that the red and blue teams work together and keep each other informed.
Enhanced cooperation between both teams through proper resource sharing, reporting and knowledge share is essential for the continual improvement of the cyber security program.