Previous

What Is Vulnerability Scanning?
A Complete Guide For 2023
Learn about PurpleSec’s fully managed vulnerability management services.
Author: Eryk Waligora / Last Updated: 02/10/2023
Reviewed By: Josh Allen & Jason Firch, MBA
View Our: Editorial Process
Table Of Contents
What You’ll Learn
- What a vulnerability scan is and how the process works.
- The different types of vulnerability scans.
- How to overcome common challenges with vulnerability scanning.
- How PurpleSec is improving the scanning process.
In today’s fast-paced world of technology, the threat of cyber attacks is a growing concern for businesses and organizations of all sizes.
With more and more sensitive data being stored and processed online, the need for a robust security infrastructure is more pressing than ever.
A critical element to secure this infrastructure is vulnerability scanning, but even with the best intentions, many organizations are still falling short in this critical area.
In fact, recent studies show that as much as 80% of all vulnerabilities can go undetected by standard scanning processes.
So, what’s the problem with vulnerability scanning and how can it be solved?
In this article, we’ll dive deep into the issues plaguing the current state of vulnerability scanning and provide concrete solutions for improving your security posture.
What Is Vulnerability Scanning?
Vulnerability scanning is a process of identifying and assessing security weaknesses in a computer system, network, or web application. Vulnerabilities can range from technical flaws in software, hardware or configuration issues to vulnerabilities in policies and procedures.
Learn More: Top 10 Most Exploited Security Vulnerabilities In 2022
The Goal Of A Vulnerability Scan
A vulnerability scan is an important step in the vulnerability management process, which aims to identify and address potential security risks.
By performing regular vulnerability scans, organizations can assess their security posture and proactively manage vulnerabilities before they can be exploited.
Vulnerability scanning plays a crucial role in risk management.
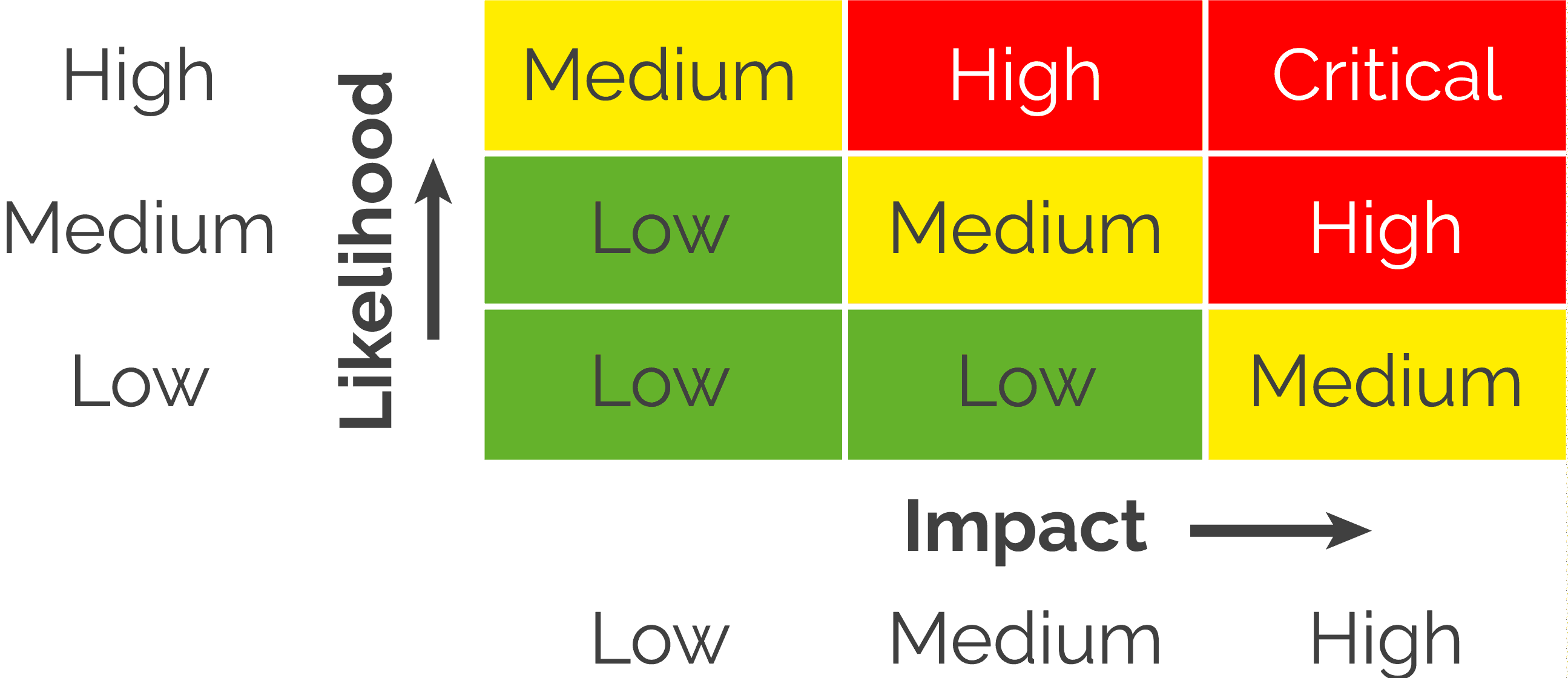
By identifying potential security risks, organizations can prioritize their efforts and allocate resources to address the most critical vulnerabilities first.
Learn More: How To Implement Risk-Based Vulnerability Management
This helps to reduce the impact of security incidents, minimize the risk of data breaches, and protect sensitive information.

A Step In the Vulnerability Management Process
It is important to note that vulnerability scanning is just one aspect of a larger vulnerability management program.
To effectively manage vulnerabilities, organizations should implement a comprehensive approach that includes:
What Is A Vulnerability Scanner?
Vulnerability scanners are software programs designed to identify security weaknesses within a computer system or network. A vulnerability scanner can help organizations assess their risk by identifying potential threats, such as outdated software or unpatched systems.
Open Source Vulnerability Scanners
Open-source vulnerability scanners are free to use and are typically developed and maintained by a community of volunteers.
These scanners offer a good starting point for organizations with limited resources or those who are new to vulnerability scanning.
Examples of popular open source vulnerability scanners include OpenVAS and OpenSCAP.
Paid Vulnerability Scanning Tools
Paid vulnerability scanning tools often offer more advanced features, such as real-time scanning and prioritization of vulnerabilities based on severity.
These tools are maintained and updated by the vendor, which can provide additional security and stability to organizations.
Examples of paid vulnerability scanning tools include Nessus, Qualys, and Rapid7.
While both open source and paid tools can be effective, the right choice for an organization will depend on the organization’s specific needs, resources, and goals.
Types of Vulnerability Scans
As we’ve discussed so far, vulnerability scanning allows organizations to identify and remediate vulnerabilities in their systems and applications before they can be exploited by attackers.
There are various types of vulnerability scans, each with its own specific focus and approach including:
- Credentialed VS Uncredentialed Scans
- Network Vulnerability Scans
- Web Application Scans
Credentialed VS Uncredentialed Scans
One key distinction in vulnerability scans is between credentialed and uncredentialed scans.
Credentialed scans, also known as authenticated scans, utilize the access privileges of a user with the system being scanned in order to more accurately identify vulnerabilities.
This type of scan is best for identifying vulnerabilities that can only be exploited by an authenticated user.
In contrast, uncredentialed scans, also known as unauthenticated scans, perform the scan from the perspective of an attacker, who does not have access privileges to the system.
Uncredentialed scans are best for identifying vulnerabilities that can be exploited by attackers who have not yet gained access to the system.
Depending on the specific needs of an organization, either type of scan can be useful, but it is important to understand the differences and when each is best used.
Network Vulnerability Scans
Another type of vulnerability scan is a network vulnerability scan.
This type of scan focuses on identifying vulnerabilities in an organization’s network infrastructure, including:
- Routers
- Firewalls
- Servers
- Workstations
- Printers
- Other network-connected devices.
Network vulnerability scans can help organizations identify and remediate vulnerabilities in their network before they can be exploited by attackers, leading to data theft or other security incidents.
Learn More: Vulnerability Scanning VS Penetration Testing
Web Application Vulnerability Scans
Finally, there are web application scans, which focus specifically on identifying vulnerabilities in an organization’s website or applications.
Security engineers often refer to the OWASP Top Ten when identifying, evaluating, and remediating vulnerabilities such as SQL injections or cross-site scripting (XSS).
By performing regular web application scans, organizations can ensure that their web applications remain secure and protected from attackers.
The Vulnerability Scanning Process Explained
- Step 1: Preparation – The first step of the vulnerability scanning process is preparation. This involves gathering information about the network or system to be scanned, including the IP addresses, subnets, and any other relevant information. This information is then used to configure the vulnerability scanner and ensure that it will be able to properly scan the network or system.
- Step 2: Scanning– The second step of the vulnerability scanning process is the actual scan. This is where the vulnerability scanner is run and begins to identify potential vulnerabilities in the network or system. The scanner may use various methods to identify vulnerabilities, including port scanning, protocol analysis, and application testing.
- Step 3: Analysis – Once the scan has been completed, the third step of the vulnerability scanning process is to analyze the results. The vulnerability scanner will generate a report of its findings, which must be reviewed and analyzed to determine the severity of each vulnerability and what steps should be taken to address them.
- Step 4: Mitigation – The final step of the vulnerability scanning process is to address and mitigate the vulnerabilities that have been identified. This may involve patching software, reconfiguring systems, or implementing other security measures to prevent the vulnerabilities from being exploited. It’s important to follow through with these steps in a timely manner, as ignoring vulnerabilities can leave the network or system exposed to potential attacks.
Benefits Of Vulnerability Scans
Vulnerability scans play an important role in securing an organization’s infrastructure.
There are several benefits to performing regular vulnerability scans including:
- Identifying security threats: Vulnerability scans can help organizations identify potential security threats in their infrastructure, including unpatched software, misconfigured systems, and weak passwords. This information can be used to prioritize remediation efforts and reduce the risk of a successful attack.
- Compliance with regulations: In many industries, organizations are required to adhere to specific regulations, such as PCI DSS, that require regular vulnerability scans. By conducting these scans, organizations can ensure they are in compliance and avoid costly penalties.
- Continuous improvement: Regular vulnerability scans allow organizations to track their progress in addressing security vulnerabilities over time. This information can be used to identify areas where the organization needs to improve its security posture and make proactive changes to reduce the risk of attacks.
By incorporating vulnerability scans into their security program, organizations can better protect their systems, data, and reputation.
Importance Of Having A Vulnerability Scanning Policy
A vulnerability scanning policy is a set of guidelines that outline the procedures and standards for conducting regular vulnerability scans. It is important for organizations to have a vulnerability scanning policy for several reasons.
First, the policy helps ensure that scans are conducted in a consistent and controlled manner. This helps to ensure that all vulnerabilities are discovered and addressed, reducing the risk of a potential security breach.
Second, the policy helps organizations prioritize their scanning efforts by specifying the frequency and scope of scans. This helps to ensure that critical systems and assets are scanned on a regular basis, while also reducing the amount of time and resources spent on unnecessary scans.
Finally, the policy provides a clear chain of command for who is responsible for conducting scans, analyzing results, and taking corrective action. This helps to ensure that vulnerabilities are addressed in a timely manner and that responsibility is clearly defined.
Common Challenges When Performing A Vulnerability Scan
Performing vulnerability scans is a critical aspect of a comprehensive security program, but it’s not without its challenges. Here are three common challenges organizations face when it comes to vulnerability scanning.
Keeping Up With the Frequency of Scanning
One of the most common challenges organizations face is keeping up with the frequency of scanning. The reality is that vulnerabilities are discovered on a regular basis, and it’s essential to scan for them as frequently as possible.
It’s easy to fall behind and let scanning slip from your priority list, which can leave your organization vulnerable to attack.
Learn More: How To Reduce Your Mean Time To Remediate A Vulnerability
False Positives & Negatives
Another challenge organizations face is dealing with false positives and negatives, which can lead to a false sense of security or cause teams to burn through resources chasing non-existent vulnerabilities.
- False positives occur when a vulnerability scan identifies a potential vulnerability that does not actually exist.
- False negatives occur when a vulnerability scan fails to identify a real vulnerability.
Keeping Scan Results Up-to-Date
Finally, keeping scan results up-to-date is common challenge organizations face.
As new vulnerabilities are discovered and patches are released, it’s essential to re-scan to ensure the results are accurate.
Failing to do so can result in missed vulnerabilities, leaving your organization vulnerable to attack.
How PurpleSec Is Improving Vulnerability Scanning
PurpleSec’s vulnerability management services offer a comprehensive solution to organizations struggling with the complexity and resource constraints of their vulnerability scans.
Case Study: How We Reduced Vulnerability Risk By 86%
The program includes regular scans, vulnerability assessments, and remediation support, ensuring organizations stay ahead of potential threats and maintain a secure environment.
This results in an efficient and cost-effective solution, increasing the accuracy and efficiency of processes.
With PurpleSec, organizations can eliminate manual effort and have peace of mind knowing that their systems are being monitored by experts and have a comprehensive view of their security risk.
Wrapping Up
In conclusion, vulnerability scanning plays a crucial role in a comprehensive vulnerability management program.
With the rapid evolution of cyber threats, it’s more important than ever to have a continuously evolving approach to vulnerability management.
A vulnerability scan helps identify and prioritize the most critical vulnerabilities, so they can be remediated before they can be exploited by attackers.
However, performing a vulnerability scan can be challenging, especially for organizations with limited resources. This is where PurpleSec comes in, providing a managed vulnerability management platform that streamlines the process and provides a more comprehensive and effective solution.
By partnering with PurpleSec, organizations can take their security to the next level without adding more resources to their team.
Schedule a demo today to see how our platform can help you achieve your security goals while freeing up your team to focus on other critical tasks.
Frequently Asked Questions
How Do You Perform A Vulnerability Scan?
A vulnerability scan is typically performed using specialized software, known as a vulnerability scanner, that scans a target system for potential security weaknesses. The scan identifies and reports any known vulnerabilities in the software, operating system, and other applications running on the system. A vulnerability scanner typically checks for issues such as missing patches, misconfigured systems, and outdated software.
Which Is The Most Popular Vulnerability Scanner Used By Companies?
It is difficult to determine the most popular vulnerability scanner used in companies as it largely depends on the size and type of organization, as well as specific security needs. Some popular vulnerability scanners include Nessus, Rapid7, Qualys, and Tenable. Each of these tools has its own strengths and weaknesses, and the best option for a specific organization may vary.

Eryk Waligora
Eryk has a multi-perspective experience from his over 10 years of professional work in the media/entertainment, technology, and cyber security industries. He is currently serving as a cyber threat intelligence manager as well as a technical writer for PurpleSec.
Recent Articles
Categories
Policy Templates
Most Popular