You can reduce the mean time to patch vulnerabilities by implementing a continuous and automated vulnerability management solution.
This drastically cuts down on the time required to prioritize and remediate vulnerabilities while enabling your security or IT teams to focus on more valuable projects.
Free Security Policy Templates
Get a step ahead of your cybersecurity goals with our comprehensive templates.

Many organizations struggle with aggregating the results from their vulnerability scanner and correlating this data into useful metrics that can help drive their patching and remediation process.
Based on publicly available statistics for data breaches over the last decade, failure to patch vulnerable systems promptly can potentially result in loss of revenue, damage to an organization’s brand, and in some cases complete shutdown of the business.
In this article, we will explore in detail the factors that determine the average time to patch, and review how PurpleSec’s vulnerability management solution can help reduce the average time to patch your vulnerabilities.
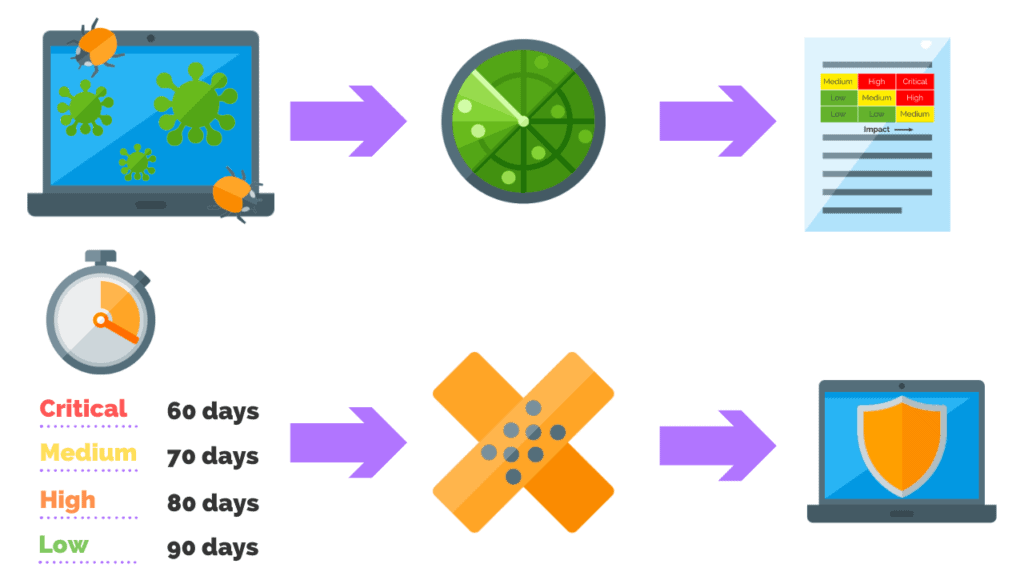
What Is The Average Time To Remediate A Vulnerability?
According to Infosec Institute, the average number of days to remediate a vulnerability is between 60 to 150 days.
Vulnerability scanning tools perform the same function for enterprise and SMB environments. You provide a list or a range of IP addresses of your network for the scanner.
The scanner runs at a specified time and produces a vulnerability report for all assets it can touch. The report breaks down what it finds in various severity levels, such as:
- Critical
- High
- Medium
- Low
- Informational
For example, if you are a SMB with less than 5 IP addresses, with only a single Critical vulnerability, your average time to patch should be considerably lower than a larger organization that has 1,000 IP addresses with 500 Critical vulnerabilities.
So where do we start in understanding how these figures can help your organization reduce patching times and achieve the benefits of vulnerability management?
Vulnerability Metrics Defined
Let’s first consider a few terms related to the metrics used to calculate the average patching time:
- Mean Time to Patch (MTTP) – Average time it takes to patch a vulnerability. Generally calculated by subtracting the difference in time between the official release date of a patch and the time it takes to install the patch on the average of supported assets. The MTTP time should not exceed the number of days between the next maintenance period.
- Median Time To Respond/Remediate (MTTR) – Measurement of time elapsed between the occurrence of a security incident, time of discovery, when it was investigated, and contained.
- Median Time To Detect (MTTR) – The average length of time it takes a cybersecurity team to discover incidents in their environment.
- Maintenance Window/Period – The period set aside by IT to remediate vulnerabilities within the environment. This time in most cases is pre-approved and continuous by Change Management.
We will reference these metrics throughout the remainder of the article.
Risks Of Not Patching Vulnerabilities
When gathered and measured properly, vulnerability metrics can help your IT teams identify areas of risk within your organization.
In this section, we will examine the dangers of not reporting key metrics and how it can potentially put your organization at risk for the next data breach.
New Vulnerabilities Are Emerging Daily
A consistent and high MTTP value will elevate the risk of exposing your critical systems to zero-day attacks.
Once hackers compromise your systems, they can harvest your data in a matter of days or even load malware onto your systems that could lay dormant indefinitely.
This is dangerous and increases the risk of the software infecting other systems on the network.
Ransomware & Extortionware Remain A Top Threat
A high MTTP or MTTR metric also puts your organization at risk of becoming the next victim of a ransomware or an extortionware attack.
SMBs are at the highest risk since they may not have cyber insurance to recover from this type of attack or have the means to restore their company from a data breach.
Related Article: How To Prevent Ransomware Attacks
End-of-life operating systems or legacy applications running on production servers are especially at risk.
If exploited, these systems can shut down production or prevent users from accessing them altogether.
Delaying Time To Patch
Delayed patching increases your MTTP which can lead to a backlog of vulnerabilities, which in turn increases technical debt.
Instead of proactively patching to reduce risk, reactive patching after the systems have been exploited is not the best practice.
By understanding the role metrics play in the patching process, your organization can determine risk and make plans to reduce the MTTP and MTTR values.
So, how can your organization go about planning and meeting the challenge of timely patching?
Common Challenges With Patch Management
Implementing a solution to remediate vulnerabilities can be challenging and requires careful planning. Several factors need to be considered as you plan to develop this important component of your vulnerability management program.
Supporting Legacy Systems
Organizations should have plans in place to replace legacy systems.
For example, Microsoft notifies its customers well in advance of systems that are approaching the end of life and provides a date when patches will no longer be available.
If unable to patch legacy systems, isolate the environment into a private VLAN to reduce the impact of infecting other devices on the network.
Lack Of A Vulnerability Remediation Process
Creating a process to track and measure the vulnerability remediation process is a common problem many organizations face today.
If policies are not enforced to report metrics continuously, it will be difficult to develop remediation plans and reduce technical debt.
No Testing Environment
Lack of lower environments (Test or User Acceptance Test/UAT) that simulate your production systems for testing.
If no lower environment is available to test patches, this may introduce unintended results if applied directly without testing first in a lower environment.
A good test process can alleviate fears by infrastructure teams of adopting the new remediation process and alignment with Change Management.
How PurpleSec Improves The Vulnerability Management Process
PurpleSec’s vulnerability management services are designed to help organizations lower their average time to patch vulnerabilities whether it be a large enterprise or SMB network. It utilizes automation technology to replace manual tasks, allowing your analysts to focus on prioritizing systems that are at the most risk for exploitation.
Are services are also designed to integrate with tools you already have to deliver a full, robust vulnerability management lifecycle process.
Reduces Your Mean Time To Patch (MTTP)
In a recent case study, PurpleSec’s security experts were able to reduce remediation times from an average of 180 days down to 9-12 days while driving significant cost savings for our client.
Vulnerability automation speeds up the entire lifecycle contributing to a significant reduction in remediation timelines.
This is accomplished by dynamic orchestration and intuitive playbooks, which in turn automate tasks that were formerly manually intensive.
The solution integrates with your existing security tools to deliver a centralized platform for analysis along with a streamlined remediation process to increase mitigation time.
Internal audit teams, compliance, and executives can visibly view the state of the vulnerability program by viewing the comprehensive reporting and analytics provided by the solution.
Provides Continuous Validation
The platform is flexible and allows you to manage the scanning frequency, validation, and remediation effort at any time.
This ability to continuously scan and validate your vulnerabilities compresses the remediation ‘time to remediate’ window, which in turn reduces the risk of attack from external threat actors.
Continuous validation also allows you to proactively mitigate vulnerabilities instead of allowing them to remain unpatched and grow uncontrollably over time.
If staffing is not available, no need to worry.
The platform can provide automation software and tools along with support from our security analyst to perform continuous validation.
Impact to production systems is low, due to the agentless technology used by the platform.
Automates Tedious Tasks
The platform is built on software that incorporates both AI (Artificial Intelligence) and ML (Machine Learning) technology. This technology works in the background by modeling the context of assets to create a pattern or baseline.
The data can then be used to identify critical assets.
Over time, the output of this data allows the analyst to focus on the reports from the important assets instead of manually clicking through a spreadsheet to locate information.
The reduction in time to repair can contribute to your bottom line by freeing up your analyst to focus on other important areas or critical projects in the business that require attention.
Although AI/ML has been around for several years, utilizing this technology within a vulnerability management platform greatly decreases the risk of human error and drives the automation features of the platform.
Detects Zero-Day Vulnerabilities
Equipped with an expert-defined remediation library that is constantly updated with the most current threat intelligence, zero-day vulnerabilities are now quickly identified.
Once reported, the platform can automatically send a notification to your cyber threat teams via a ticketing system or direct alerts to a mailbox.
The approval process can be further streamlined by automating the approvals beforehand, as well as having a predefined playbook available to assist in patching the zero-day vulnerability, per approval from your organization’s change management procedures.
Wrapping Up
In this article, we have reviewed the key metrics that directly impact the average time to patch your vulnerabilities.
With an understanding of the key metrics and how they relate to risk, your business can identify the right metrics to quickly measure gaps within your current vulnerability patching process.
By coupling this information with PurpleSec’s automated vulnerability management solution, your organization can begin to prioritize and streamline the process of patch remediation by replacing time-consuming processes with a more efficient and agile system.
Article by