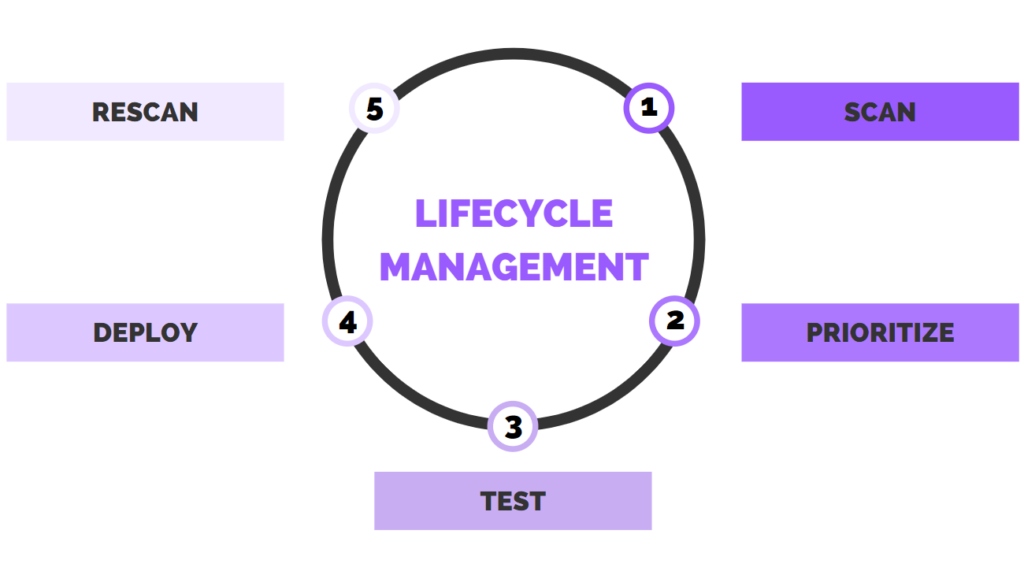
There are five main steps in the vulnerability management lifecycle:
- Assess
- Prioritize
- Action
- Reassess
- Improve
Free Security Policy Templates
Get a step ahead of your cybersecurity goals with our comprehensive templates.

What Is The Vulnerability Management Lifecycle?
The vulnerability management lifecycle is a process intended for organizations to effectively identify, remediate, and confirm the elimination of network vulnerabilities in a computer system.
This cyclical structure is not only designed for security professionals to address a vulnerability from start to finish but can be applied to any vulnerability instance.
For reliable, continuous vulnerability management, following a lifecycle process is key to any organization’s security program.
Step 1: Assess
The most straightforward way to find a vulnerability is to scan your network and to conduct a vulnerability assessment.
These will help to discover misconfigurations or coding flaws that can be used to compromise or exploit an application or system.
With these vulnerabilities now known, you can move on to the next step.
Step 2: Prioritize
Not every vulnerability is the same, meaning not every vulnerability requires the same treatment.
The most critical vulnerabilities could include ones that are backlogged, not just newly discovered ones.
To map out the severity levels facing your organization you can assign a risk scoring card or matrix to prioritize which vulnerabilities to remediate.
Step 3: Action
Once you have prioritized your vulnerabilities you can begin addressing the ones at the top of your list.
By implementing a patch management procedure, your security infrastructure or engineering team will repair and test each vulnerability at a time.
These could be short-term or long-term fixes.
Step 4: Reassess
To ensure the reliability of patches and to keep updated on any irregularities or changes to the vulnerability, it’s important to maintain continuous monitoring.
This monitoring phase of the vulnerability management lifecycle can be done either manually with the aid of a security analyst, or more commonly now with the use of automated tools.
Once a reassessment has been made, teams can capture this information into a vulnerability management report to document and leverage for continued use, as Step 5 explains.
Step 5: Improve
After all assessments and actions have been taken to eliminate a vulnerability, one of the most important steps to impact the effectiveness of a vulnerability management program is to perform a lookback or “lessons learned” exercise.
This approach helps management define what worked, and what did not, during the lifecycle process.
Evaluating these results can determine long-term improvements and can be leveraged for budgetary needs.
Frameworks For Vulnerability Management
Selecting a framework for your vulnerability management plan can provide a reference for designing and implementing security mechanisms to help ensure vulnerabilities to your organization are eliminated properly.
This assurance allows managers and leadership to intelligently manage their organization’s security posture using risk-based vulnerability management.
Abiding by a vulnerability management framework also instills confidence in the organization’s industry and establishes a strong reputation of proactive compliance, which can lead to increased business.
NIST Vulnerability Management Framework
The National Institute of Standards and Technology (NIST) is within the U.S. Department of Commerce is the gold standard when developing a vulnerability management program.
If you are looking to develop a well-structured patch management program look no further than NIST SP 800-40 Rev. 4.
Related Article: Patch Management VS Vulnerability Management
As one of the key features of any vulnerability management lifecycle, patch management supports a security team’s ability to effectively eliminate the vulnerabilities identified in their systems.
With this detailed framework in hand, an organization can quickly and professionally take action on remediation to continue the vulnerability management life cycle process.
Top Challenges With The Vulnerability Management Lifecycle
There are several challenges to implementing a vulnerability management lifecycle.
Many organizations simply don’t know where to start, let alone how to include the right features to make a program operational and to ultimately bring value to the organization.
Understanding these challenges will help you to avoid them.
Resource Intensive
Traditional vulnerability management is accomplished by throwing bodies at the problem, but quantity doesn’t mean quality.
It is far better that you have fewer employees that can perform at a higher capacity. To offset the number of employees, organizations will typically attempt to supplement labor by purchasing software and tools to take on more of the manual tasks.
While full-time employees (FTE) are usually the main cost to an organization, purchasing unnecessary and difficult-to-use tools can also be very expensive.
This is not a sustainable or cost-effective solution.
Managed Security Service Providers (MSSPs) can help alleviate the challenge of Labor and associated costs by outsourcing for precision and expert solutions.
Inefficient
Many IT and security teams are not always in sync.
Whether due to underfunding of budget, overstretched team capacity, or general lack of vision, a vulnerability management program can suffer exponentially.
When processes and ownership of responsibilities are not always clear and become neglected, a vulnerability can slip through the cracks and open an organization to exposure.
Likewise, a poorly run vulnerability management program can show stakeholders a failed return on investment and may cause a further decrease in staff and budget.
Another critical challenge facing organizations today includes Managed Service Providers (MSPs) who own an organization’s vulnerability management.
Many of these providers are not experts and will often leave companies more vulnerable and for longer periods.
Time Consuming
One of the most stressful aspects of an ineffective vulnerability management program is the amount of time it takes to remediate a vulnerability and to carry out other vulnerability management processes.
From identification to prioritization, and then remediation, the mean time to patch high or critical vulnerabilities is estimated to be 60 days on average.
This of course not only takes away from other work but adds to an increase in labor, additional tooling, and an overall increase in costs.
With so much time spent focused on manual tasks this also leads to greater chances of human error and potential points of exposure that can result in damage to the organization.
How PurpleSec Streamlines The Vulnerability Lifecycle
PurpleSec’s approach to vulnerability management is constantly looking to the future, not only at the evolving threat landscape but to how people and teams function best within an organization.
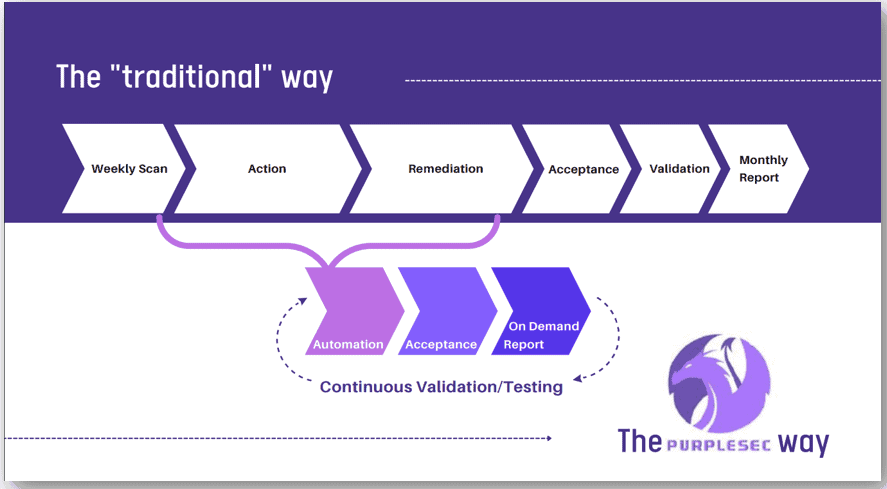
To keep up with the fast pace of response, secure critical assets, and reduce the high price tags of tools on the market today, there are several ways to improve your organization’s security posture without a heavy lift.
Automated Vulnerability Management
As systems become increasingly complex and integrated, it’s desirable to move away from manual processes where possible.
This is especially true for vulnerability patch management, Step 3 in the Vulnerability Management Lifecycle.
It can help turn weeks of coordinating these processes into days.
You’ll want to use various tools and methods for automated vulnerability management.
However, it’s recommended you do so in a controlled fashion that limits disruptions to business systems. To do this you can automate your testing workflows and triage process.
Instead of hiring employees to manually scan or patch a system, it makes more sense for them to be analyzing the results and providing to management for decision-making.
This relieves the burden of time-consuming tactical work and allows for better planning and strategy.
Extremely Cost Effective
Of course, one of the top benefits to any organization is cost-effectiveness, and PurpleSec’s vulnerability management lifecycle possesses multiple cost-saving advantages.
With a fully managed solution, it doesn’t require nearly as many people to run, saving 1,000s of labor hours per year.
And with no expensive, complicated, or intrusive software stacks to purchase an organization can function at ease with 100% agentless deployment.
It eliminates ad hoc patching which can lead to missed patches and compound costs.
It also reduces technical debt by helping the organization set focus and prioritization around assets that present the highest risk if exploited.
Plain and simple, vulnerability management helps to bring structure and precision to an organization’s security posture, bolstering its justification to stakeholders who will then be more likely to support vulnerability initiatives.
Continuous Remediation
Vulnerability management helps to move organizations from a reactive response to a proactive one.
Having a continuous patch management process in place ensures immediate identification and prioritization and has the resources for critical vulnerability remediation.
In doing so it lays the groundwork for a quicker and more effective response to threats that emerge.
Scanning just once per month means you’re vulnerable the other 29 days of the month.
It’s not just a one-and-done task – it must be continuous to truly reduce risk, especially against zero-day attacks and ransomware.
Deploying continuous remediation goes beyond point-in-time scans or assessments to significantly reduce risk exposure.
This approach is also relevant for compliance purposes, as it is a requirement when following NIST and CMMC frameworks.
Having a set structure to compare to and perform self-audits to improve the remediation process will save time, and money, and align to actionable goals.
Continuous vulnerability management will harden cyber defenses and ensure the best return on security investment (ROSI).
Wrapping Up
This article explained the need to cut down on manual processes, align to a well-structured framework for compliance purposes, and follow the five main steps of the vulnerability management lifecycle.
Now that you understand what a vulnerability management life cycle is and how it can benefit your organization you can move forward to implement the right methods and services required to build a mature vulnerability management program.
Article by