There are 5 best practices for implementing a risk-based approach to vulnerability management including:
- Having complete visibility of your environments.
- Having a complete inventory.
- Conducting a risk assessment.
- Calculating risk weighting.
- Aligning processes to mitigate risk.
Free Security Policy Templates
Get a step ahead of your cybersecurity goals with our comprehensive templates.

What Is Risk-Based Vulnerability Management?

Risk-based Vulnerability Management is an improvement on traditional vulnerability management because it prioritizes each vulnerability’s risk score using combined inputs that consider the location of each vulnerability enriched vulnerability score metrics.
Risk-based vulnerability management optimizes remediation activities based on the risks that each vulnerability poses to an organization.
Best Practices For Risk-Based Vulnerability Management
The modern threat environment has evolved and attackers are not prepared with automated tools that can help them identify vulnerabilities and exploit targets much faster.
This requires a vulnerability management program that has more accurate methods for categorizing vulnerabilities according to the actual risk they pose to an organization to keep pace with the evolving threat environment.
1. Have Complete Visibility Of Your Environments
You can’t protect what you can’t see, so creating digital visibility is an important step in developing a vulnerability management program and reliably managing risk.
With a full inventory of systems and data, hardware and software, and a network topography in hand, ensure your scanning and other security tools have visibility of all critical assets in the environment.
2. Have A Complete Inventory
 Having complete visibility into an IT environment is crucial for mitigating vulnerabilities and reducing risk.
Having complete visibility into an IT environment is crucial for mitigating vulnerabilities and reducing risk.
This complete inventory of all systems and data is a prerequisite for conducting a risk assessment and a risk-based vulnerability management program capable of:
- Prioritizing vulnerabilities
- Optimizing vulnerability management activities
- Reducing the exposure time of critical vulnerabilities.
3. Conduct A Security Risk Assessment
A full and proper risk assessment of an organization’s IT infrastructure includes the critical consideration of how each asset impacts an organization’s overall business operations.
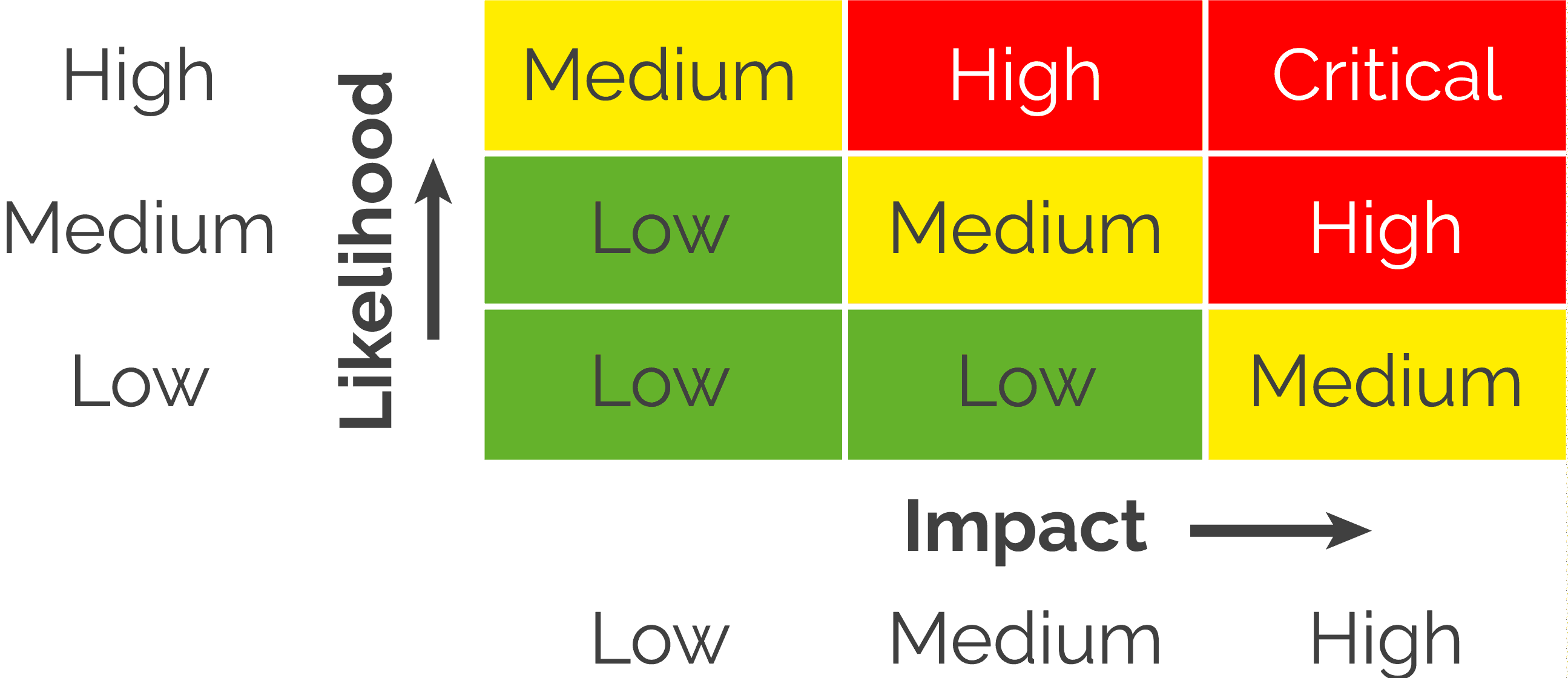
A security risk assessment should identify which assets are critical for revenue-generating activities, and identify sensitivity labels for all data, especially data that is protected by regulations or is a component in a cyber-insurance or compliance requirement.
4. Calculate Risk Weighting
Prioritizing vulnerabilities essentially means calculating a relative risk score for each vulnerability that is more detailed than simply relying on a CVE’s CVSS score.
A contextual risk-based score takes account for each vulnerability’s locality within the IT environment and the criticality of the affected asset to business operations, as well as regulatory and compliance requirements, which assets are potentially impacted by the vulnerability and how those assets are related to an organization’s business operations, and critical assets.
How To Calculate Risk
This approach takes the basic risk equation (Risk = Threat * Probability) and uses enriched inputs to calculate the real contextual risk a vulnerability poses to an organization.
Inputs such as CVSS score and vector, [], and the location of a vulnerability within an organization’s IT environment have a big impact on the potential damage that an attacker could do by exploiting it.
Calculating a threat-based risk score allows decision-makers to apply limited IT security resources more efficiently and effectively.
5. Align Processes To Mitigate Risk
Considering how a traditional vulnerability management program addresses risk in an arbitrary way rather than contextually according to real risk.
Real protection depends on improving vulnerability management programs by taking a more strategic approach.
By conducting a risk assessment and categorizing systems by their business impact, new vulnerability data can be enriched to better visualize the potential impact and vulnerabilities can be assigned a prioritized risk score; delivering a more effective and efficient risk mitigation process.
Why Traditional Vulnerability Management Fails
Traditional Vulnerability Management is a broken system that does not effectively reduce the risk for most organizations.
There isn’t just one problem with the traditional approach either; there are multiple.
Firstly, patching on a monthly cycle such as Microsoft’s infamous patch Tuesday leaves a prolonged exposure time when true risk is not visible.
During this time, organizations can only hope that new vulnerabilities are not offering an easy foothold into the network.
Secondly, the traditional approach does not address the contextual risk that each vulnerability represents.
So IT security team members are not prioritizing vulnerabilities effectively or efficiently; potentially overlooking the most critical vulnerabilities, maybe picking the low-hanging fruit first.
The traditional process of prioritizing cyber risks was developed at a time when both the number of disclosed vulnerabilities and the number of software applications that an organization depends on were far fewer in number.
This increase has overwhelmed IT security teams by flooding them with more vulnerabilities than they have time to remediate.
Because of this, a traditional vulnerability management approach – to remediate all vulnerabilities in an IT environment – has become impossible and it fails at achieving its ultimate goal; reducing risk.
Contrastingly, vulnerability prioritization is the process of deciding which vulnerabilities pose the biggest risk to an organization by calculating a risk score for each one and offers a significant improvement to the traditional approach.
Let’s examine some of the limitations of the traditional approach to vulnerability management that fail to effectively address an organization’s cyber risk objectives:
- Focuses On CVSS Scores.
- Places Less Weight On Internal Vulnerabilities Vs External.
- Accept Longer Time Frames To Mitigate Vulnerabilities.
Focuses On CVSS Scores
The most important metric in a traditional vulnerability management program is the CVSS score and string. The CVSS score quantifies the ultimate severity of a disclosed CVE vulnerability.
The CVSS string relays the contextual information about a vulnerabilities exploitability that was used to calculate the CVSS score and includes:
- Whether the vulnerability can be exploited remotely
- Whether the vulnerability requires user interaction
- Whether the vulnerability is easy or difficult to exploit
- Whether proof-of-concept (POC) exploit code has been published for the vulnerability
- Whether a vulnerability’s exploitation can impact confidentiality, integrity, or availability
Places Less Weight On Internal Vulnerabilities Vs External
Another mistake of a traditional vulnerability management approach is that it over-emphasizes the risk of external attack surface and tends to neglect internal network vulnerabilities.
Although this approach may seem to make sense since it seems logical that attackers must first breach an outer attack surface to enter an organization’s internal IT environment, a more careful analysis of this strategy shows its limitations.
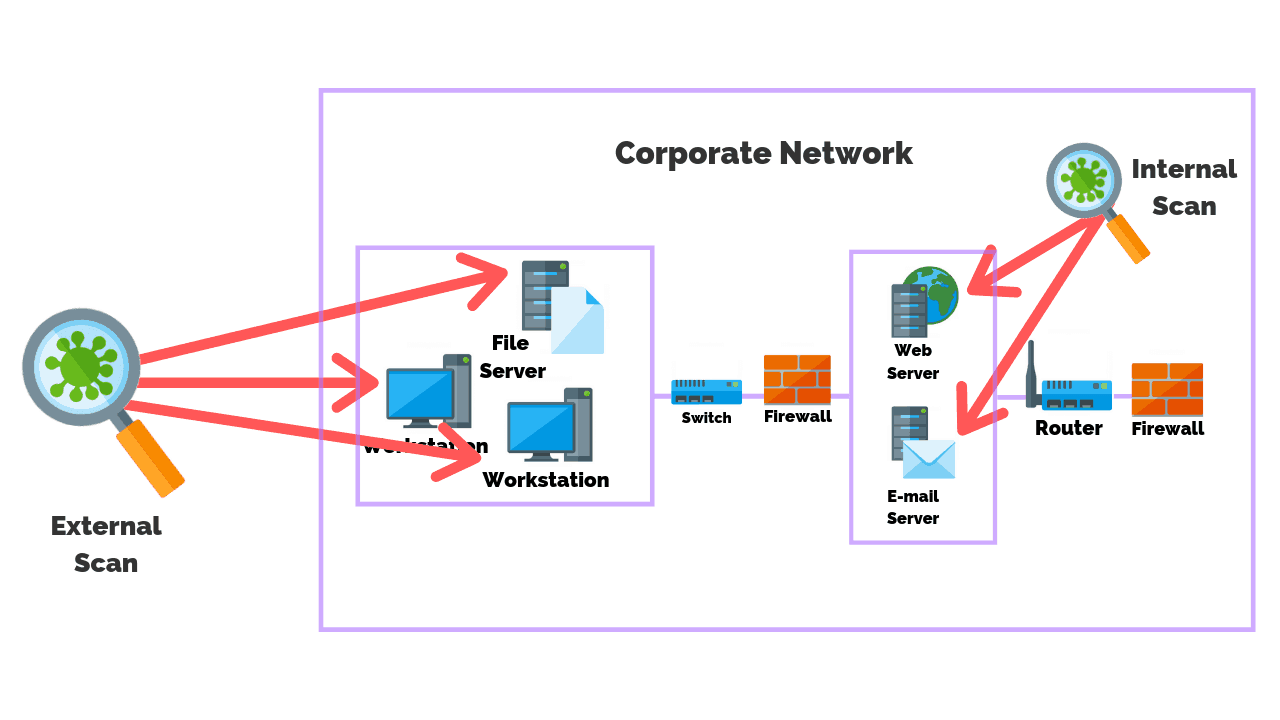
The external attack surface is only one step away from having access to an internal network, so one misconfiguration or zero-day could give an attacker direct internal access.
Secondly, the human element is an important factor – phishing attacks are cited as the most common way that attacks gain access to an internal network.
Finally, an organization’s insiders also pose a significant risk and have direct access to critical internal resources.
These facts all indicate that the simple black-and-white approach to prioritizing vulnerabilities by their internal/external locality is not an effective way to mitigate cyber risk.
Accept Longer Time Frames To Mitigate Vulnerabilities
Traditional vulnerability management programs only periodically scan an IT environment for vulnerabilities, perhaps once a month, or even as infrequently as once every 6 months or once per year.
This means that vulnerabilities in a traditional approach are afforded a long exposure time when attackers can take advantage of them.
Also, traditional vulnerability management programs are not supported by automated processes that provide IT security teams with enriched context.
Instead they are forced to manually collect their own data and parse it into a rough decision making process that results in a delayed response time to the remediation and a somewhat arbitrary prioritization that is clouded by human error.
Why Should You Switch To Risk-Based Vulnerability Management?
If you aren’t doing a risk-based approach you are taking an arbitrary approach to reducing risk. Attackers aren’t stupid.
On the other hand, attackers approach their target’s strategically, attacking vulnerabilities that are more likely to provide access to an organization’s critical system and data.
Focus On Risk
Cyber risk poses a threat to organizations because cyber attacks can have a large impact on:
- Financial stability
- Brand image
- Competitive advantage
- Intellectual property (IP) and trade secrets
When implementing a vulnerability management program, businesses need to be able to quantify and qualify where cyber risk exists in their organization and tend to the risk hotspots first and with the most resources.
Risk Reduction Is The Ultimate Goal Of Cybersecurity
Cybersecurity policies, security controls, and activities are ultimately put in place to protect an organization, its business operations, its competitive advantage, growth, and its finances.
However, just as businesses need to approach their revenue-generating activities strategically, they also need to be strategic in their approach to cybersecurity.
Just as strategic placement of an advertisement will increase sales, strategic remediation of vulnerabilities will offer better cyber security, close critical attack surfaces sooner, and ultimately reduce an organization’s risk of suffering a critical cyber breach.
Better Vulnerability Reporting
A risk-based approach to vulnerability management delivers more actionable vulnerability reports rather than a simple list of tasks containing virtually no useful data.
Risk-based vulnerability management also gives an enriched context to each vulnerability to optimize their deployment of Infosec personnel, saving time while having a bigger impact on defensive security, and delivering a better return on security investment (ROSI).
Wrapping Up
Next-generation risk-based solutions offer more efficient and effective vulnerability management capabilities above and beyond traditional approaches.
Going forward, organizations should look towards a risk-based approach to vulnerability management for prioritized and actionable vulnerability reports and better risk visibility across the entire IT environment.
The additional benefits of a next-gen vulnerability management solution include automated continuous scanning and threat intelligence aggregation that saves time, reduces the chance of human error, and alleviates the burden on IT security teams.
Article by