Continuous vulnerability management is an ongoing effort that requires vigilance, collaboration, and a proactive mindset. Vulnerability management programs are one of the most critical components of a cybersecurity program. They are considered a requirement for reducing the attack surface and preventing cyber attacks.
While taking a “traditional” approach is better than not implementing any vulnerability management measures at all, periodic scanning still leaves a security gap in between scans that attackers can exploit. Next-generation vulnerability management technologies streamline vulnerability management activities, reduce costs, and increase a cybersecurity program’s return on security investment (ROSI).
Free Security Policy Templates
Get a step ahead of your cybersecurity goals with our comprehensive templates.

What Is Continuous Vulnerability Management?
![]() Continuous vulnerability management is a set of automated processes that support real-time visibility of vulnerabilities and risks across an organization’s entire network.
Continuous vulnerability management is a set of automated processes that support real-time visibility of vulnerabilities and risks across an organization’s entire network.
Automating vulnerability management reduces the mean time to patch vulnerabilities, delivers enriched threat data and remediation advice, and supports risk management by automatically prioritizing vulnerabilities according to the contextual risk to pose to each organization’s operations.
Continuous vulnerability management minimizes the exposure time of vulnerabilities, closes the window of opportunity for attackers, and is a CIS Critical Security Control indicating that it is a requirement for meeting IT security best practices and compliance.
CIS Control 7: Continuous Vulnerability Management
According to CIS Control 7 the recommendations for continuous vulnerability management are to:
Develop a plan to continuously assess and track vulnerabilities on all enterprise assets within the enterprise’s infrastructure. The goal is to remediate these vulnerabilities promptly and minimize the window of opportunity for attackers. Here are the key requirements:
1. Assessment And Tracking
- Continuously acquire, assess, and take action based on new information to identify vulnerabilities.
- Regularly scan endpoints and systems for vulnerabilities.
- Prioritize vulnerabilities based on factors such as likelihood of exploitation and cost.
2. Timely Remediation
- Develop a structured process for addressing vulnerabilities promptly.
- Remediate identified vulnerabilities as soon as possible.
- Minimize the exposure time during which attackers could exploit these vulnerabilities.
3. Monitoring And Threat Intelligence
- Monitor public and private industry sources for new threat and vulnerability information.
- Stay informed about emerging risks and security updates.
- Leverage threat intelligence feeds to enhance vulnerability awareness.
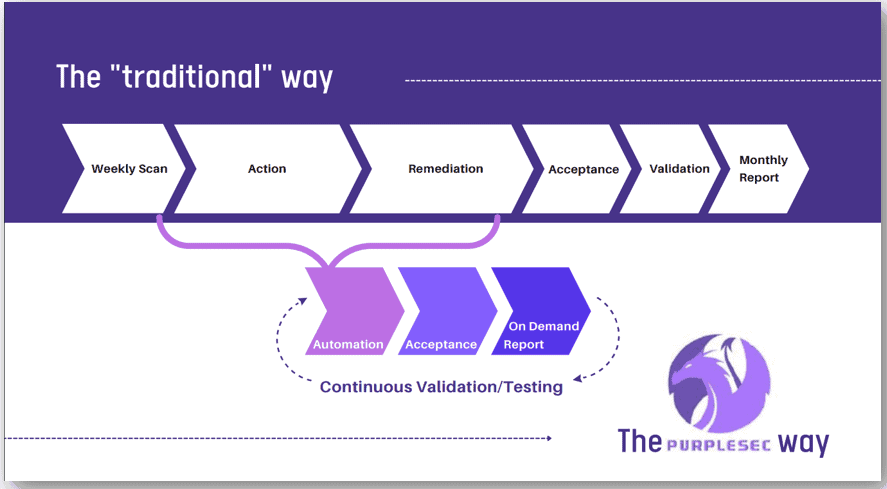
Continuous Vulnerability Management Vs The Traditional Approach
The difference between “traditional” vulnerability management and continuous vulnerability management is that traditional vulnerabilities are periodically scanned and manually remediated.
Continuous vulnerability management provides 24/7 monitoring of an IT environment and automation to reduce the burden on IT security teams which reduces mean time to resolution and improves return on security investment.
The benefits of vulnerability management are obvious – networks simply cannot be protected without vulnerability remediation processes.
However, “traditional” vulnerability management is an old paradigm that does not efficiently or effectively reduce exposure time or attack surface.
Because threat actors deploy tools that can continuously monitor their target’s attack surface for new security gaps, defenders need to match those efforts with next-generation vulnerability management technologies.
Monthly Scans & Vulnerability Assessments Aren’t Sufficient
Enterprise IT infrastructure is in constant flux as companies deploy new technologies to increase their productivity and widen their scope of capabilities. This constant change also ensures that new vulnerabilities are constantly added to the IT environment.
Quarterly and even monthly vulnerability assessments are not good enough to provide a high degree of risk assurance because the exposure between scans is an open opportunity for attacks to stay ahead of the network defenders.
Threat researchers find and disclose new vulnerabilities daily and even one of these in a network could offer an attacker a foothold and put your organization at risk.
You Can’t Visualize & Report On True Risk
Traditional vulnerability management only creates a “point in time” risk assessment within an environment. This creates an “exposure time” – a blind spot when true risk across an organization’s IT environment is invisible.
Continuous automated vulnerability management aggregates and analyzes vulnerability data across the entire IT environment in real-time and combines it with cyber threat intelligence (CTI).
This next-generation vulnerability management processes flow provides the IT security teams with a set of risk-prioritized vulnerabilities and remediation advice allowing them to take immediate action.
Time Consuming For Personnel
Cyber threat intelligence is a constant stream of new information, security advisories, and remediation processes.
This continuous nature and the sheer amount of data make traditional vulnerability management a time-intensive process that can lead to alert fatigue in IT security team members.
Continuous automated vulnerability management solutions make the processes faster and more efficient than traditional vulnerability scanning but also make a vulnerability management program more effective by reducing the potential for human error.
Next-generation cyber security tools allow IT staff to spend less time trying to analyze the threat environment and more time improving network security by remediating vulnerabilities.
When Should You Consider A Continuous Vulnerability Management?
If you are unsure about your organization’s ability to manage a cyber attack or don’t have an in-house IT security team, continuous vulnerability management is an opportunity to streamline security operations, strengthen operational resiliency, and gain strong cyber risk assurances.
Here are some scenarios that indicate your organization will benefit from continuous vulnerability management technologies:
- You Want To Improve Your Return On Security Investment (ROSI).
- You Want To Streamline Your Vulnerability Management Program.
- If You’re In A High Targeted Industry.
- You’re Rapidly Growing.
You Want To Improve Your Return On Security Investment (ROSI)
ROSI assesses how much potential financial loss security investment can prevent by calculating the monetary value of the risk reduction.
Continuous vulnerability management programs reduce the risk and potential costs of a cyber-attack by identifying vulnerabilities immediately as they appear within an organization’s environment.
The automated technologies that support continuous vulnerability activities also provide IT security team members with industry-leading enriched threat data and risk priority scores that are calculated according to each organization’s unique business operations.
This combination reduces the potential for human error and allows IT staff to spend more of their time closing security gaps and less time researching what to do.
You Want To Streamline Your Vulnerability Management
Organizations of all sizes are rushing to increase their cyber security protections in response to:
- New regulations and compliance requirements,
- A threat environment that is exponentially increasing in frequency and costs of a breach.
Continuous vulnerability management is a standard control requirement for:
CIS compliance, and advised by NIST in its standards Information Security Continuous Monitoring (ISCM) for Federal Information Systems and Organizations (SP 800-137) and Technical Guide to Information Security Testing and Assessment (SP 800-115) because:
“The use of automated support tools can make the process of continuous monitoring more cost-effective, consistent, and efficient“.
Next-generation vulnerability management technologies go above and beyond traditional methods.
It provides access to the skills and knowledge of leading IT security professionals, delivers quantitative analytics for data-driven prioritization and risk visibility, and most importantly reduces mean time to remediate.
If You’re In A High Targeted Industry
Professional services, IT, manufacturing, healthcare, and finance industries have been hit the hardest by cyber attacks.
These industries represent high financial value and are the most difficult to defend because they are competitive, fast-paced, and continuously adopt new technologies to increase productivity.
For companies in these industries, the challenge of defending an IT network is not a question of “if” you will be attacked, or even “when” because cyber attacks are evolving on a daily.
For strong risk assurances, cyber-defenses need to match the pace of attackers’ activities and close security gaps across an organization’s entire IT environment.
You're Rapidly Growing
Every company hopes to grow and most of its attention is focused directly on growing its customer base, revenues, and profit margins.
However, growth comes with increased risk. As companies scale their services they handle a larger amount of sensitive data and become more attractive to attackers.
Fortunately growing an IT security department to match overall growth is necessarily a requirement. Continuous vulnerability management stretches existing IT and Infosec staff further, enabling them to mitigate a higher number of vulnerabilities in a lower amount of time.
IT security team members can spend more time remediating vulnerabilities and less time manually aggregating, researching, and analyzing vulnerability information.
Challenges With Implementing A Continuous Vulnerability Management Program
While continuous vulnerability management can improve the effectiveness and efficiency of traditional vulnerability management, the implementation of this program also includes unique challenges.
Requires A Mature Inventory
Risk is defined as the probability that a security incident will happen and the potential damage that one could cause. Risk is not distributed evenly throughout an organization, but rather it is highly contextual to each organization’s business operations.
Therefore, each organization has its own set of critical systems and data, and each asset’s potential attack surface is different.
An effective vulnerability management program depends on the identification of risk within an organization’s business operations and IT infrastructure and therefore relies on having a complete risk assessment.
This requires an organization to thoroughly inventory and apply detailed classifications to its IT infrastructure before vulnerability management processes can begin.
Setup Can Be A Significant Technical Lift
Having the correct principles for your continuous vulnerability management program is one thing, but technical implementation still offers a significant challenge and can lead to program failure.
Installing and correctly configuring the technologies required for a continuous program can be a significant technical lift, especially for IT teams that are not deeply experienced in container deployment and management
Other challenges include integrating continuous vulnerability management tools with the existing network and ensuring that the scanners have full visibility of the entire network environment.
Supporting Legacy Systems
Legacy systems are highly vulnerable to cyber-attacks. Sometimes systems cannot be updated because they have reached their end-of-life cycle and no longer receive security updates.
Legacy systems present another problem as well; as systems grow older, the knowledge and skills for defending them become harder to find as most IT workers specialize their skills for the next generation of technologies.
These facts don’t necessarily mean that legacy systems cannot be defended, but it does mean that defensive cybersecurity strategy must be more vigilant, and policies and security controls must be carefully selected and implemented to keep attackers out.
Wrapping Up
The cyber threat environment never sleeps.
That means reducing the attack surface within an organization’s IT environment requires closing new security gaps as soon as they appear. Traditional vulnerability management practices do not meet the challenges posed by today’s threat environment.
Not only because they lack compliance with industry-standard best practices to be continuous but also because they are efficient and introduce the potential for alert fatigue and human error.
A traditional approach to vulnerability management requires IT security team members to manually aggregate vulnerability data and prioritize vulnerabilities and does not minimize exposure time.
A continuous vulnerability management standard leads the way and is now a requirement for meeting industry best practices.
Next-generation technologies that support continuous automated vulnerability management aggregate, analyze, and deliver risk-prioritized vulnerability data that reduces response times, and human error; ultimately leading to a significant increase in network security by closing the window of opportunity for attackers.
When it comes to closing the cyber security gaps that attackers seek to exploit, sooner is better than later but continuous is the gold standard.
Article by