2024 Cybersecurity Statistics
The Ultimate List Of Cybersecurity Stats Data, & Trends
Hundreds of cyber security statistics including the latest ransomware stats, the cost of cybercrime, the rise of supply chain attacks, and much more!

The Cost Of Cybercrime
- Cybercrime up 600% Due to COVID-19 Pandemic.
- It is estimated that, worldwide, cyber crimes will cost $10.5 trillion annually by 2025.
- The global annual cost of cybercrime is estimated to be $6 trillion per year.
- Cybercrime cost makes up a value worth 1% of the Global GDP.
- On average, a malware attack costs a company over $2.5 million (including the time needed to resolve the attack.
- Ransomware is 57x more destructive in 2021 than it was in 2015.
- There are 30 million SMB in the USA and over 66% of all SMB’s had at least 1 incident between 2018-2020.
- The average cost of a data breach to small business can range from $120,000 to $1.24 million.
- Data breach costs rose from $3.86 million to $4.24 million in 2021, the highest average total cost in the 17-year history of this report.
- The average cost was $1.07 million higher in breaches where remote work was a factor in causing the breach.
- Security Driven AI had best cost mitigation, saving up to $3.81 million (80% cost difference).
- Zero trust security policies saved $1.76 million per breach.
- 10% increase in average total cost of a breach from 2020-2021.
- It costs $180 per record with PII that was breached.
- Over 50% of all cyber attacks are done on SMB’s.
Small Businesses
- There are 30 million SMB in the USA and over 66% of all SMB’s had at least 1 incident between 2018-2020.
- Over 50% of all cyber attacks are done on SMB’s.
Enterprises
- 130 security breaches per year, per organization, on average.
- 22.7% increase in cost of cybersec per year.
- 27.4% increase in annual number of security breaches.
- 50 days – average time needed to resolve an insider’s attack.
- 23 days – how long it takes to recover from a ransomware attack.
- Enterprises experienced 130 security breaches per year, per organization, on average.
- Enterprises saw the annual cost of cyber security increase 22.7% in 2021.
- The annual number of security breaches on enterprise organizations increased by 27.4%.
- On average enterprises needed 50 days to resolve an insider’s attack and 23 days to recover from a ransomware attack.
- 71.1 million people fall victim to cyber crimes yearly.
- Individuals lose $4,476 USD on average.
- Individuals lose $318 billion to cybercrime.
- Individuals of phishing scams lost $225 on average.
- The top 5 cyber crimes in 2021 were:
- Extortion
- Identity theft
- Personal data breach
- Non-payment
- Phishing attacks
- Access to Someone’s entire online identity is worth roughly $1,000.
- PII goes for roughly $200 per record.
- $50 gets you malware + tutorial on how to use it.
- A $34 monthly investment could net a criminal $25,000 a month.
Individuals
- 71.1 million fall victim to cybercrimes yearly.
- Victims lose $4,476 USD on average.
- Victims lose $318 billion to cybercrime.
- Victims of phishing scams lost 225$ on average.

Cyber Attack Statistics
Recent Cyber Attacks
As data breaches become more pervasive in our interconnected world so must our understanding of modern-day cyber attacks. In this video series, we sit down with cyber security experts and get their take on the most recent cyber attacks and data breaches.
- 2022 – The ZLoader botnet responsible for distributing the ZLoader malware was taken down in a joint effort with Microsoft, ESET, Black Lotus Labs, Palo Alto Networks, HealthISAC, and Financial Services-ISAC.
- 2022 – On May 8th, 2022 the a national emergency was declared due to an ongoing Conti ransomware attack against several Costa Rican government entities.
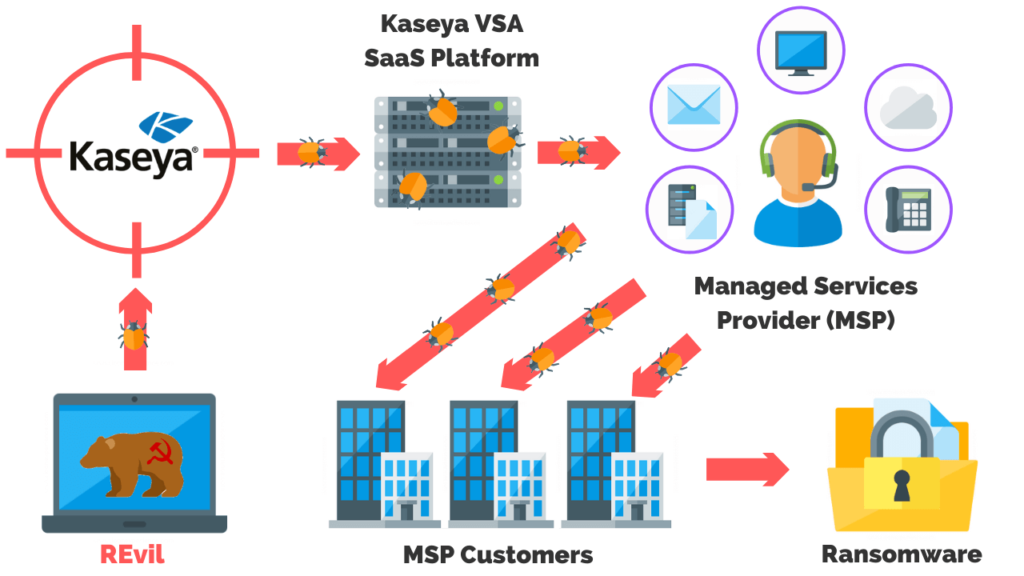
- 2021 – Kaseya suffered a ransomware attack compromising up to 1500 companies with a staggering ransom note of $70 million.
- 2021 – Saudi Aramco experienced a data breach exposing sensitive data on employees and technical specifications of the organization. Threat group ZeroX is demanding a payment of $50 million.
- 2021 – The Accellion file transfer application (FTA) data breach impacted over 100 companies, organizations, universities, and government agencies around the world.
- 2021 – The Pulse Secure VPN zero-day was exploited resulting in the breach of several undisclosed defense firms and government organizations in the United States and Europe.
- 2021 – Solarwinds fell victim to a nation-state supply chain attack impacting government agencies and fortune 500 companies.
- 2020 – Spartanburg County School District was the victim of a ransomware attack on February 26th. As a result, internet connectivity and network access was shut off for three days. Although no data was compromised, the district did lose all online access.
- 2020 – Tillamook County commissioners negotiate for an encryption key to regain control of the government’s computer systems after falling victim to a ransomware attack.
- 2020 – Universal Health Services reports an information technology security incident. Malware, specifically the Ryuk ransomware, which targeted 400 hospitals in the US and the UK. UHS has over 90,000 employees who provide healthcare services to roughly 3.5 million patients every year.
- 2020 – Duesseldorf University Hospital is infected with ransomware, resulting in the first death reported following a ransomware attack.
- 2020 – The hotel chain Marriott disclosed a security breach that impacted the data of more than 5.2 million hotel guests who used their company’s loyalty application.
- 2020 – MGM Resorts suffered a massive data breach resulting in the leak of 142 million personal details of hotel guests.
- 2020 – 500,000 stolen Zoom passwords available for sale in dark web crime forums.
- 2020 – Magellan Health was struck by a ransomware attack and data breach stating that 365,000 patients were affected in the sophisticated cyberattack.
- 2020 – Twitter breach well-coordinated scam made attackers swindle $121,000 in Bitcoin through nearly 300 transactions.
- 2019 – Maryland Department of Labor was breached by hackers who illegally accessed names and social security numbers belonging to 78,000 people.
- 2019 – Captical One recently had over 106 million records stolen containing personal and financial information.
- 2018 – After falling victim to the SamSam malware, the city of Atlanta, Georgia refused to pay the $50,000 ransom and instead spent more than $5 million rebuilding its computer network.
- 2018 – Cyber attackers hacked into Marriot international computer systems and compromised five hundred million accounts.
- 2018 – Cathy pacific was hacked and 9.4 million accounts were compromised.
- 2018 – Facebook code was exploited by attackers and 50 million user accounts were compromised.
- 2018 – Quora was hacked and information belonging to 100million users was compromised.
- 2018 – Under Armor reported that its “My Fitness Pal” was hacked, affecting 150 million users.
- 2017 – Uber network was breached compromising data of fifty million riders, seven million drivers and 600,000 US based driver license details.
- 2017 – Cyber attackers hacked into Equifax servers and exposed over 143 million consumers’ personal information.
- 2017 – 412 million user accounts were stolen from Friendfinder’s sites.
- 2017 – 147.9 million consumers were affected by the Equifax Breach.
- 2016 – Peace cyber-attackers hacked Myspace compromising over 360 million accounts.
- 2016 – Uber reported that hackers stole the information of over 57 million riders and drivers.
- 2015 – Hackers broke into Anthem Inc. servers and stole 37.5 million records consisting of sensitive information.
- 2015 – Peace a Russian based Cyber-attack group infiltrated LinkedIn stealing email and password combinations of over 117 million customers.
- 2014 – Syrian Electronic Army cyber hacking group infiltrated eBay’s network stealing sensitive information of one hundred and forty-five million users.
- 2013 – Cyber criminals hacked Yahoo’s 3 billion email accounts gaining access to sensitive customer information.
- 2013 – Cyber attackers used malware to steal data from Target company point of sale systems compromising information of approximately one hundred and ten million credit/debit carrying customers.
Ransomware Statistics
 Ransomware is malicious software that threatens you with harm, usually by denying you access to your data. Ransomware attacks are often deployed via social engineering tactics. Once a user falls victim to the attack, their data is encrypted.
Ransomware is malicious software that threatens you with harm, usually by denying you access to your data. Ransomware attacks are often deployed via social engineering tactics. Once a user falls victim to the attack, their data is encrypted.
The attacker then demands a ransom from the victim, with the promise to restore access to the data upon payment.
Growth Of Ransomware
- The average ransomware payment in 2021 increased by 82% year over year to $570,000.
- 121 ransomware incidents have been reported in the first half of 2021, up 64% year-over-year.
- The largest ransom demand observed so far in 2021 is $100 million.
- Ransomware has become a popular form of attack in recent years growing 350% in 2018.
- Ransomware detections are on the rise with Ryuk detections increasing by 543% over Q4 2018, and since its introduction in May 2019,
- 81% of cyber security experts believe there will be more ransomware attacks than ever in 2019.
- In 2019 ransomware from phishing emails increased 109% over 2017.
- 21% of ransomware involved social actions, such as phishing.
- New ransomware variants grew 46% in 2019.
- 68,000 new ransomware Trojans for mobile were detected in 2019.
- Ransomware attacks increased 41% in 2019 with 205,000 businesses who lost access to their files.
- It’s estimated that a business will fall victim to a ransomware attack every 14 seconds.
- From 2013 to 2016, the primary ransomware variants reported were CryptoLocker and CryptoWall.
- In 2017 and 2018, that transitioned to WannaCry and SamSam.
- In late 2018 and early 2019, the primary ransomware families have been GandCrab and Ryuk.
Cost Of Ransomware Attacks
- The estimated cost of ransomware attacks:
- 2020 – $20 billion
- 2019 – $11.5 billion
- 2018 – $8 billion
- The average ransom payment amount increased by 104% in Q4 2019 – $84,116, $780,000 for a large enterprise.
- Downtime increased by 200% year over year, and that such costs are “23X greater than the average ransom requested in 2019.
- The top 10 ransomware strains by revenue in 2021 were:
- Conti – $175 million
- DarkSide – $80 million
- Phoenix Cryptolocker – $55 million
- REvil/Sodinokibi – $35 million
- Cuba – $17 million
- Clop – $16 million
- LockBit – $15 million
- Hive – $15 million
- BlackMatter -$14 million
- Ryuk – $13 million
- The NotPeyta ransomware attack losses could exceed $1 billion.
- FedEx lost an estimated $300 million in Q1 2017 from the NotPetya ransomware attack.
- The average cost of a ransomware attack on businesses was $133,000.
- The average cost of ransom per incident is on the rise:
- 2018 – $4,300
- 2019 – $5,900
- 2020 – $8,100
- The average cost of ransomware caused downtime per incident:
- 2018 – $46,800
- 2019 – $141,000
- 2020 – $283,000
- Businesses lost around $8,500 per hour due to ransomware-induced downtime.
- Ransomware attacks cost U.S. healthcare organizations $157 million since 2016
- The individual ransom of 1,400 clinics, hospitals, and other healthcare organizations varied from $1,600 to $14 million per attack.
Mobile Ransomware Statistics
- Threats in the mobile space continue to grow year-over-year, including the number of new mobile malware variants which increased by 54% in 2019.
- There are more than 4,000 mobile threat families and variants in the McAfee sample database today.
- More than 18 million mobile malware instances were detected by Symantec in 2018.
- In 2018, over 8,000 mobile banking ransomware Trojan installations were detected.
- 60,176 new mobile ransomware Trojans were discovered in 2018.
- Less than 20% of mobile malware is delivered via a browser — the remainder of the payloads come through an app.
- More than 4.2 million American mobile users suffered ransomware attacks on their phones.
- Android/LokiBot has targeted more than 100 financial institutions around the world generating close to $2 million in revenue from kit sales on the “dark web.”
Cryptocurrency Ransomware Statistics
- 95% of ransomware profits went through the cryptocurrency trading platform BTC-e.
- 60% of cryptocurrency transactions can be traced back to individuals.
- The number of mobile miners has increased by almost 45% from 2016–2017 to 2017–2018.
Supply Chain Attack Statistics
Not all attacks should be denoted as supply chain attacks, but due to their nature many of them are potential vectors for new supply chain attacks in the future. Organizations need to update their cybersecurity methodology with supply chain attacks in mind and to incorporate all their suppliers in their protection and security verification.
Add this stat to the top (According to a recent survey, over 60% of security leaders) say they plan to deploy supply chain security measures in 2022. 78% reporting that their boards confer on this topic at least once every month.
Growth & Cost Of Supply Chain Attacks
- Supply chain attacks rose by 42% in the first quarter of 2021 in the US, impacting up to seven million people, according to research.
- 84% of IT and security professionals believe that software supply chain attacks will be one of the biggest cyber threats within the next three years.
- 45% of organizations experienced at least one software supply chain attack in the last 12 months, compared to 32% in 2018.
- The average financial impact of a supply chain attack against an enterprise reached $1.4 million in 2021.
- 28% of European enterprises have suffered a supply chain attack in 2021, unchanged from 2020; however, the financial impact was higher.
General Supply Chain Attack Statistics
- 59% of organizations that suffered their first software supply chain attack did not have a response strategy.
- Only 36% have vetted all new and existing suppliers for security purposes in the last 12 months.
- Around 50% of the attacks were attributed to well-known APT groups by the security community.
- Around 42% of the analyzed attacks have not yet been attributed to a particular group.
- Around 62% of the attacks on customers took advantage of their trust in their supplier.
- In 62% of supply chain attacks malware was the attack technique employed.
- When considering targeted assets, in 66% of the incidents attackers focused on the suppliers’ code in order to further compromise targeted customers.
- Around 58% of the supply chain attacks aimed at gaining access to data (predominantly customer data, including personal data and intellectual property) and around 16% at gaining access to people.
- Out of 24 confirmed supply chain attacks, 8 (33%) were reported in 2020 and 16 (66%) from January 2021 to early July 2021. Based on this data, the trend forecasts that 2021 may have 4 times more supply chain attacks than 2020.
- Suppliers’ assets targeted (second column [SA]), most attacks aimed to compromise: Code (66%), Data (20%), and Processes (12%).
- The compromised suppliers’ assets are used as an attack vector to compromise the customers. Those attacks are mostly done (third column [CT]): by Abusing the trust of the customer (62%) in the supplier, or by using Malware (62%)
- Considering that 83% of the suppliers are in the technology sector, the lack of knowledge on how attacks happened could either indicate a poor level of maturity when it comes to cyber defense in suppliers’ infrastructure or unwillingness to share the relevant information.
- In one study of 24 incidents, more than 50% of the supply chain attacks were attributed to well-known cyber crime groups including APT29, APT41, Thallium APT, UNC2546, Lazarus APT, TA413 and TA428.
Social Engineering Statistics
Social engineering is a type of cyber attack where threat actors attempt to retrieve sensitive information by manipulating people into providing sensitive data, account credentials, or granting access to networks or systems.
Threat actors track our digital footprint to gather as much information as they can about an organization, its employees, and its vendors.
Growth Of Phishing
- Phishing was the number one complaint for individuals and businesses in 2020 leading to $1.8 billion in business losses.
- Phishing incidents nearly doubled from 114,702 incidents in 2019 to 241,324 incidents in 2020.
- There were more than11 times as many phishing complaints in 2020 compared to 2016.
- Since 2016, phishing has replaced malware as the leading type of unsafe website.
- There are nearly 75 times as many phishing sites as there are malware sites.
- Google has registered 2.15 million phishing sites as of January 2021, up from 1.7 million on January 2020.
- Incidents involving payment and invoice fraud increased by 112% between Q1 2020 and Q2 2020.
- Attacks on finance employees increased by 87% while attacks on C-Suite decreased by 37%.
- In Q4 2020 scammers requested funds in the form of gift cards in 60% of business email compromise (BEC) attacks, down from 71% in Q3 2020.
- In Q4, BEC attackers requested direct bank transfers 22% of cases, up from 14% in Q3 2020.
- Attacks that requested payroll diversions grew to 13% in Q4 from 6% in Q3 to 13% in Q4 2020.
- The average amount requested in wire transfer BEC attacks increased from $48,000 in Q3 to$75,000 in Q4 2020.
- Phishing domains that contain a compelling catchword designed to fool consumers is up from 58% in Q2 2020, and 33% in 2019.
- 120,500 unique sender addresses were observed in August 2020, nearly 50% higher than the previous record in 2019.
- The number of unique sender TLDs observed in August 2020 was 337, up from a previous high of 259 in late 2019.
- The fourth quarter’s most significant increase in phishing in Brazil was in the e-commerce sector, suffering the most attacks, accounting for45% of the quarterly volume of phishing.
Vishing Statistics
- 99% of Spanish organizations faced vishing attacks in 2019.
- 57% of Australian organizations faced vishing attacks 2019.
- 83% experiencing vishing attacks in 2019.
- In 2016, 64% of the fraudulent phone calls originated in a country different from the victim, while only 6.6% of legitimate calls originate from international locations.
- Peru, Indonesia, Mexico, and India received the most spam calls in 2019, with vishing attacks making up 10-26% of these calls.
- 56 million Americans experienced scam calls that cost a total of US $19.7 billion in 2020.
- Authority was the most commonly used persuasion used in vishing used in 95.3% of cases.
Smishing Statistics
- 44% of users are not aware of the security solution available for mobile devices.
- Mobile phishing attacks have grown at a consistent rate of 85% annually since 2011.
- Mobile phishing attacks have gone up by 37% in Q1 2020.
Advanced Persistent Threat (APT) Statistics
- The global advanced persistent threat (APT) protection market size was over $4.3 billion in 2019 and is projected to reach $20 billion by 2027.
- By 2025 the advanced persistent threat protection market will be worth an estimated $12.5 billion annually.
- The advanced persistent threat (APT) protection market size is expected to register a CAGR of 18.2% during the forecast period and reach the market size of $9.6 billion in 2026.
- The professional services for the advanced persistent threat (APT) protection market shall have notable growth and is projected to register a revenue of $9,387.7 million by 2027, surging from $1,619.5 million in 2019.
- The cloud sub-segment of the global advanced persistent threat (APT) protection market will have the fastest growth and it is projected to surpass $12,184.5 million by 2027, with an increase from $1,957.6 million in 2019.
- The managed services for advanced persistent threat (APT) protection market will have a significant share in the global industry and is further projected to generate a revenue of $10,905.3 million,
- The NGFW software for the advanced persistent threat (APT) protection market will be a rapidly growing segment and is further projected to register a revenue of $3,938.2 million by 2027,
- Security Information and Event Management (SIEM) shall have a dominating market share in the global market and is expected to generate a revenue of $3,811.7 million, during the analysis timeframe.
- The BFSI sub-segment for advanced persistent threat (APT) protection is in extensive demand and is further expected to register a noteworthy revenue of $2,624.3 million by 2027.
- The government and defense sub-segment for the advanced persistent threat (APT) protection market will have a dominating share in 2020 and is expected to generate a revenue of $2,631.1 million by 2027, with a CAGR of 19.3%,
- The Asia-Pacific advanced persistent threat (APT) protection market accounted $1,093.0 million in 2019 and is expected to generate a revenue of $5,275.6 million by 2027.
- North America advanced persistent threat (APT) protection market will have dominating market share and is anticipated to grow at a CAGR of 20.3% by generating revenue of $6,641.1 million by 2027.
- Attacks conducted by APTs on EU institutions, bodies, and agencies increased by 30% in 2021.
- 21% of organizations report having an incident affecting suppliers that they share data with.22% lose access to customer-facing services as a result of a targeted attack.
- 34% of companies experienced damage tot heir reputation as a result of an APT attack.
- 68% of companies experienced a targeted attack on their networks and suffered data loss as a direct result.
- 78% of companies experience downtime as a result of an APT attack.
- 90% of APT groups use spear phishing as an effective way to penetrate a company’s internal network.
- 48% of APT groups use legitimate administration tools and commercial penetration testing tools.
- The cost of the tools needed for a banking attack would start at $55,000. A cyberespionage campaign would be much more expensive, running at least $500,000 to start.
- 14% of APT groups conduct watering hole attacks at the penetration stage. (APT29, APT35, TEMP.Periscope, DarkHydrus).
Zero-Day Attack Statistics
- The total number of zero-days recorded over the last 10 years:
- 2011 – 28
- 2012 – 25
- 2013 -41
- 2014 – 34
- 2015 – 35
- 2016 – 34
- 2017 – 40
- 2018 – 31
- 2019- 29
- 2020 – 38
- 2021 – 66
- Zero-day malware increased to 67.2% in Q3 2021r up 3% in the previous quarter.
- Zero-day malware over TLS rose to 47% om Q3 2-21 up from 31.6% in the previous quarter.
- A total of 83 zero-days were recorded in 2021 up 55% from 2020, which recorded 36 zero-days.
- From 2016 through 2020, between 12 and 25 zero-day attacks were identified each year, about 21 per year on average.
- 80% of all successful data breaches in 2019 directly resulted from zero-day attacks.
- It’s estimated that 42% of all attacks in 2021 were zero-day attacks.
- The price of an Android exploit chain increased 1150% over the last 3 years from $200,000 to $2.5 million.
- The price of a full exploit chain for Apple iOS is estimated at $2 million.
- The most common types of zero-day exploits include:
- Memory Corruption (127) – 67.55%
- Logic/Design Flaw (26) – 13.83%
- Information Leak (11) – 5.85%
- User-After-Free (6) – 3.19%
- Other (7) – 3.72%
- The most Zero-days observed in 2021 were:
- Siemens (141) – 23.46%
- Microsoft (118) – 19.63%
- Apple (95) – 15.81%
- Adobe (77) – 12.81%
- Delta Industrial vAutomation (48) – 7.99%
- Oracle (44) – 7.32%
- Trend Micro (38) – 6.32%
- Cisco (17) – 2.83%
- NETGEAR (15) – 2.50%
- Google (8) – 1.33%
Industries Targeted By Ransomware
- Industries in North America reporting ransom attacks in 2021:
- Corporations – 40%
- Municipality – 16%
- Healthcare – 13%
- Education – 13%
- Infrastructure – 11%
- Travel – 4%
- Financial – 3%
Small & Medium Business
- 20% of ransomware victims are small to mid-sized businesses.
- 85% of MSPs report ransomware as a common threat to small to mid-sized businesses.
- 29% of small businesses had experience with ransomware, making them more likely to be unprepared for the threat.
- The average size company of a ransomware attack in 2019 was 645 employees.
City & Local Government
- At least 948 government entities in the United States were attacked by ransomware hackers extorting money in 2019.
- Ransomware attacks against state and local governments were the top cybersecurity industry story in 2019.
- Ransomware attacks against municipalities increased 60% in 2019.
- 48 of the 50 U.S. states, as well as the District of Columbia, experienced at least one ransomware attack from 2013 to 2018.
- Of those municipal victims, communities of fewer than 50,000 residents accounted for 45% of the ransomware activity, while 24% had fewer than 15,000.
- 16% of the municipalities targeted had populations of more than 300,000.
- 17% of state and local government entities that were hit paid the ransom
- While 2018 saw a small resurgence in overall ransomware attacks compared to 2017, there was a sharp jump in ransomware attacks against state and local governments, and that trend appears to continue into 2020 and beyond.
- Ransomware attacks against state and local governments were the top cybersecurity industry story in 2019.
Healthcare
- Ransomware attacks on the healthcare sector will quadruple by 2020.
- More than 700 healthcare providers fell victim to a ransomware attack in 2019.
- Almost half of the ransomware incidents reported in 2018 involved healthcare companies.
- 23% of healthcare organizations paid some form of payment to the attackers.
- On the dark web, an individual healthcare record goes for close to $400, which is 2.5 times the average overall industries.
- Of the 2,600 incidents reported, 36% were malware related followed by accidental disclosure in 26% of the cases.
- 90% of healthcare organizations saw an increase in ransomware infection rates from 2017 to 2018.
- 18% of healthcare devices have been the target of malware.
- A report by CSO online estimates healthcare related malware attacks will likely quadruple by 2020.
- 50% of IT professionals believe their industry simply isn’t ready to handle the threat of ransomware or other cyber security threats.
- 45% of all ransomware attacks in 2017 involved healthcare organizations.
- It’s estimated that in 2019 healthcare organizations fell victim to a ransomware attack every 14 seconds.
- On average, it takes 300 days for a healthcare organization to discover that it had suffered a breach.
- 77% of successful ransomware attacks were from fileless techniques that completely bypassed the victim company’s antivirus.
- 20% of healthcare domain emails were identified as fraudulent in 2017.
- 40 million ransomware attacks were detected using malicious URLs or attachments against healthcare providers in 2017.
Financial
- 90% of all financial institutions have experienced ransomware in the past year.
- More than 204,448 users experienced an attempt to log their banking information.
- Ransomware is a rising threat to small banks and credit unions with less than $35 million in annual revenue.
- Of the 52% of attacks targeting the financial services sector in March 2020, 70.9% of those came from the Kryptik trojan.
Education
- Education organizations were the biggest targets of ransomware attacks in 2019, claiming 61% of reported attacks.
- At least 28 universities, colleges and school districts were impacted in Q1 2019, disrupting operations at up to 422 individual schools.
- In 2019, 89 educational establishments were impacted by ransomware disrupting operations at up to 1,233 individual schools.
Mining & Metals
- 54% of mining and metals companies suffered a significant cyber security incident in 2019.
- 40 percent of mining and metals companies had experienced a rise in external threats over the previous 12 months.
- 96% of attacks on mines are for intelligence gathering.
- Investments into cyber security initiatives by mining and metals companies has increased by 53% in 2019.
- 97% of organizations say their current cuber security function does not fully meet their organization’s needs.
- 38% of email users in the mining industry were hit with a malicious email in the last year.
- The average annual cost of cybercrime to a Canadian company was over $12 million in 2018.
- 48% of industry professionals say that it is unlikely that they would even be able to distinguish and identify a sophisticated attack.
Utilities & Infrastructure
- Ransom demands of $10,000 – $50,000 are more common in 2021 against small businesses, which can have a crippling impact on their operations.
- Early 2020 observes a 32% increase in ransomware attacks against energy/utilities organizations.
- Less than 60% of respondents “believe their organization is in or approaching compliance with government cybersecurity mandates.”
- The global market for energy IT and cybersecurity software and services will surpass $19 billion in 2020 and reach more than $32 billion in 2028.
Malware Statistics
Malware, or malicious software, is any piece of software that was written with the intent of doing harm to data, devices or to people.
Types of malware include computer viruses, trojans, spyware, ransomware, adware, worms, file-less malware, or hybrid attacks. Recent malware attacks have become more sophisticated with the advent of machine learning and targeted spear phishing emails.
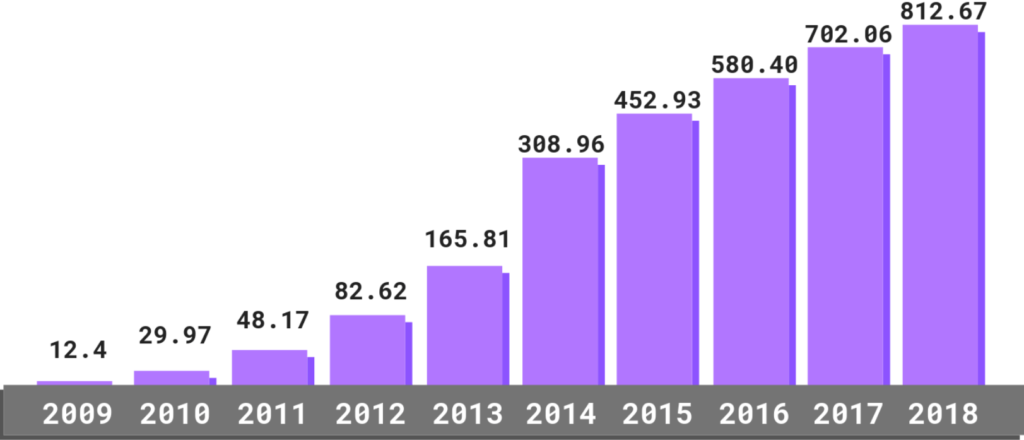
- The total malware infections have been on the rise for the last ten years:
- 2009 – 12.4 million
- 2010 – 29.97 million
- 2011 – 48.17 million
- 2012 – 82.62 million
- 2013 – 165.81 million
- 2014 – 308.96 million
- 2015 – 452.93 million
- 2016 – 580.40 million
- 2017 – 702.06 million
- 2018 – 812.67 million
- 92% of malware is delivered by email.
- Mobile malware on the rise with the number of new malware variants for mobile increased by 54% in 2018.
- Third-party app stores host 99.9% of discovered mobile malware.
- More than 250,000 unique users were attacked by Trojan-Banker.AndroidOS.Asacub malware application.
- 98% of mobile malware target Android devices.
- Over the last year, MacOS malware has increased by 165%.
- Malware development rates for Windows decreased by 11.6% since reaching an all-time high in 2015.
- Malware is still the preferred distribution model, used 71.14% of the time over the last 12 months, while PUAs were only used in 28.86% of instances.
- Gamut spambot was the most frequently used, with over 86% of all spambot cases involving its use.
- The United States continues to host the most botnet control servers in the world. Over the last year, 36% of these servers were hosted in America, while 24% were hosted in undefined countries.
- Trojans make up 51.45% of all malware.
- 7 out of every 10 malware payloads were ransomware.
- 230,000 new malware samples are produced every day — and this is predicted to only keep growing.
- Malware and web-based attacks are the two most costly attack types — companies spent an average of US $2.4 million in defense.
- Overall business detections of malware rose 79% from 2017 due to an increase in backdoors, miners, spyware, and information stealers.
- Over 18 million websites are infected with malware at a given time each week.
- 34% of businesses hit with malware took a week or more to regain access to their data.
- 90% of financial institutions reported being targeted by malware in 2018.
The Cost Of Phishing On Business
- IC3 received a record number of complaints from the American public in 2020: 791,790, with reported losses exceeding $4.1 billion.
- Total phishing complaints reported by the public increased 69% from 2019.
- Business email compromise is the most expensive phishing attack with 19,369 complaints with an adjusted loss of approximately$1.8 billion.
- Phishing scams were also prominent: 241,342 complaints, with adjusted losses of over $54 million.
- Phishing attack statistics show that the average cost of a data breach in 2018 was $3.9 million, or $150 for each record compromised.
General Phishing Statistics
- A total of 146,994 unique phishing sites were discovered in Q2 of 2020.
- During the Q3 of 2020, 40% of phishing websites were hosted on .com domains.
- Threat actors also used other seemingly legitimate domains, such as .org (1.8%) and .net (3%). However, many opted for phishy-looking domains like.xyz (5.84%) and .buzz (2.57%). Other top-level domains used in phishing attacks include .ru (2.93%), .tk (1.47%), and .ml (1.3%).
- 88% of organizations experienced targeted phishing attacks in 2019.
- 86% of organizations had their business email network compromised by threat actors in 2019.
- In 2018, more than 50% of phishing websites used SSL certificates.
- Google and Facebook lost $100 million in 2017 as a result of phishing attacks.
- Companies phishing attacks targeted worldwide in 2020:
- Software-as-a-Service (SaaS) companies and webmail providers (34.7%)
- Financial institutions (18%)
- Payment platforms (11.8%)
- Social media websites (10.8%)
- e-commerce businesses (7.5%)
- US organizations were the main targets of threat actors, having been on the receiving end of 84% of all phishing attacks in 2018.
- Canada was in second place with just 4% of attacks, while China and France tied for third place with 2%.
- Gmail’s built-in filters block more than 100 million phishing emails daily. 68% of cases blocked emails as part of a previously unknown phishing scam.
- In one study, 61% of participants couldn’t tell the difference between a genuine and a fake Amazon login page.
- Almost half of all malicious email attachments came in the form of Microsoft Office documents:
- Microsoft Word (39.3%)
- Microsoft Excel (8.7%)
- Executable (19.5%)
- Rich text (14%)
- Java archive files (5.6%)
- The most common words used in phishing emails that target businesses are:
- Urgent (8%)
- Important (5.4%)
- Important update (3.1%)
- Attn (2.3%)
- More than 1,506 data breaches occurred due to data phishing attacks, compromising 164.68 million records – an increase of 19.8% from 1,258 breaches in 2018.
- The most impersonated brands to carry out phishing attacks include:
- Google (13%)
- Amazon (13%)
- Facebook & WhatsApp (9%)
- Microsoft (7%)
- Apple (2%)
- Netflix (2%)
- PayPal (2%)
- 96% of threat actors use spear-phishing to gather intelligence.
- Threat actors cite disruption (10%) and financial gain (6%) as their main motivators for launching a spear-phishing attack.
- The number of known spear-phishing groups has grown from 116 in 2016 to over 250 in 2018.
- The top countries with these groups include:
- Japan (69)
- China (44)
- Turkey (43)
- Saudi Arabia (42)
- South Korea (40)
- Taiwan (37)
- United Arab Emirates (30)
- 1 out of 10 spear-phishing emails is part of a sextortion scam
- Phishing was the second most commonly used infection vector, employed in 33% of attacks—slightly up 31% from 2019 —suggesting that attackers’ changing techniques and defensive mechanisms against phishing are keeping pace.
Types Of Cyberecurity
Cloud Security Statistics
- The global cloud security market size was $578 million in 2019 and is projected to reach $1.5 billion by 2027, at a CAGR of 13.2% during the forecast period.
- 79% of companies have experienced at least one cloud data breach in the past 18 months.
- 80% of CISO’s surveyed were not able to identify excessive access to sensitive data in cloud production environments.
- 92% of organization’s IT environment is at least somewhat in the cloud today.
- More than half (55%) of organizations currently use multiple public clouds, with 21% saying they use three or more.
- Close to half (46%) of organization’s cloud-based applications were purpose built for the cloud and 54% moved from an on-premise environment.
- Cloud computing budgets are on the rise, as 32% of IT budget is expected to be allocated to cloud computing within the next 12 months.
- In one survey, the top challenges with public clouds were found to be:
- Controlling cloud costs (40%)
- Data privacy and security challenges (38%)
- Securing/protecting cloud resources (31%)
- Governance/compliance (30%)
- Lack of cloud security skills/expertise (30%)
- Enterprises struggle the most with data privacy and security (42%), governance and compliance (39%) and controlling costs (37%).
- SMBs say controlling costs is their greatest challenge (43%), then data privacy and security (36%), migrating data to the cloud, securing cloud resources, and finally a lack of cloud security skills (all 28%).
- 74% of companies use more than one IaaS provider.
- 32% of companies experienced the wrong users having privileged access, and 25% experiencing problems with unauthorized users.
- The top cloud security concerns in a 2020 survey were:
- Data loss and leakage (69%)
- Data privacy/confidentiality (66%)
- Accidental exposure of credentials (44%)
- Only 20% of organizations assess their overall cloud security posture in real time.
- Approximately 20% of organizations conduct weekly evaluations of their cloud security posture.
- 58% of organizations evaluate their posture once a month, or even less frequently.
- 22% of organizations still assess their cloud security posture manually.
- 75% of security professionals say they are concerned about public cloud security.
- The biggest security threats against public clouds were ranked as:
- Misconfiguration of the cloud platform (68%)
- Unauthorized access (58%)
- Insecure interfaces (52%) Hijacking of accounts (50%)
- 37% of security professionals say lack of qualified staff is the biggest road block to faster adoption.
- When selecting a cloud security provider organizations say they look for:
- Cost effectiveness (63%)
- Ease of deployment (53%)
- Security tools are cloud native (52%)
- Most organizations deploy more than three cloud solutions in their environment.
- 50% of web application attacks that lead to a data breach involve mail server compromises with 96% of those cases targeting cloud-based mail servers.
- 28% of enterprises consider security to be the most important criterion when picking a cloud vendor.
- External attacks on cloud accounts grew 630% from January to April 2020.
- 90% of cloud identities are using less than 5% of the permissions they’ve been granted.
- Breaches caused by cloud misconfiguration by industry:
- Technology (41%)
- Healthcare (20%)
- Government (10%)
- Hospitality (6%)
- Finance (6%)
- Other (17%)
- Hybrid cloud breaches were the least expensive, costing an average of 3.61 million US dollars—28.3% less than public cloud breaches.
- 79% of enterprises want better integrated security and governance for their data in the cloud. Cloud Access Security Brokers, or CASBs, can help businesses to achieve this goal.
- Organizations struggled to implement proper cloud security, resulting in more than 33 billion records exposed in 2018 and 2019 alone.
- In one report, organizations were asked what they feel was the most important in 2019 to improve security visibility for use of public cloud services:
- Identifying software vulnerabilities and remediation (29%)
- Identifying workload configurations that were out of compliance (28%)
- Identifying misconfigured security groups (25%)
- Discovering public cloud-resident sensitive data (24%)
- Third-party access to public cloud-resident data (23%)
- In 2020, the cloud security software market was valued at 29.5 billion U.S. dollars and is expected to exceed 37 billion U.S. dollars in 2026.
- 52% of organizations say cloud based services are a factor in PKI growth followed by zero-trust (50%), remote workforce needs (43%), IoT devices (43%).
- Out of 196 data breaches caused by cloud misconfigurations, Elasticsearch misconfigurations accounted for 44% of all records exposed in 2018 and 2019 and was also the most common database breached across all platforms (20%).
- 68% of organizations say cloud account takeovers present a significant security risk.
- 51% stated that phishing is the most frequent method that attackers use to acquire legitimate cloud credentials.
- When asked who is most responsible for ensuring the security of SaaS applications respondents stated:
- End-users (30%)
- Company + Cloud Service Provider (24%)
- Security Team (20%)
- 30% of respondents stated that their company’s end-users are most responsible for ensuring the security of SaaS applications.
- Compromised cloud accounts cost organizations on average $6.2 million per year.
- 86% of the surveyed organizations said cloud account compromises cost them at least $500,000.
- 50% of companies used NIST as their security framework for securing public cloud environments. 46% used CIS top 18 controls while 19% didn’t follow any framework.
- 72% of organizations say that cloud migration is the top digital transformation priority that will impact the security of their organization.
- Cloud services brought the following security benefits to organizations in 2019:
- High availability (58%)
- Fear of data loss/leaks (51%)
- Loss of control (36%)
- Integration with the current IT environment (36%)
- Insufficient cloud environment isolation (16%)
- In 2019, organizations cited the top security threats relevant to cloud services:
- Compliance (50%)
- Integration with the current IT environment (38%)
- Fear of too high dependency on the provider (32%)
- Insufficient transparency (21%)
- In 2019, organizations followed these compliance standards for security cloud environments:
- ISO 27017 (15%)
- ISO 27018 (9%)
- SOC 1,2,3 (9%)
- NIST SP 800 family (7%)
- 58% of companies rely on their cloud provider’s native security tools, and 34% were looking to hire more staff dedicated to cloud security in 2020.
- 57% of companies with smaller security teams turn to the cloud to implement security technologies.
- 98% of organizations surveyed experienced a cloud security breach in the past 18 months, up 20% from the previous 2020 study.
- 83% of cloud breaches occurred due to an exploited vulnerability.
- 60% of businesses with 10,000 or more employees cite access as their leading factor for causing cloud breaches
- 66% of companies use PKI automation or are in the midst of deploying it within their organizations.
- 49% list a cloud-first PKI deployment approach as their third-highest priority (behind certificate lifecycle automation (56%) and PKI visibility (71%).
- The average total costs of cloud based breaches in 2021 were:
- Public cloud – $4.8 million
- Private cloud – $4.5 million
- Hybrid cloud – $3.6 million
- Cloud misconfigurations represent 15% of initial attack vectors in data breaches.
- 65% of cloud network security incidents are related to user error.
- It’s estimated that 99% of cloud security failures through 2025 will be the customers’ fault.
- 30% of organizations don’t use adequate cloud security controls.
- The cloud security software market size in 2020 reached $29 billion.
Web Application Statistics
- 50% of all sites were vulnerable to at least one serious exploitable vulnerability throughout 2021.
- Between 2020 and 2021, the number of malicious web application requests climbed 88%, more than double the year-over-year growth rate.
- DDoS attacks were up 37% over 2020.
- 42% of respondents reported a lack of resources (including budget and headcount) as the factor that most impacted their compliance.
- Web application attack campaigns are 44% longer than they were during the time period covered by the previous report.
- There is a 24% increase in RFI (remote file inclusion) attacks since the previous report.
- Retail web apps were targeted by 48.1% of all attack campaigns.
- PHP apps suffer 3x more Cross Site Scripting attacks than .Net apps.
- WordPress CMS is attacked 24% more than all other CMS systems combined.
- Whilst web application requisitions grew 88%, broken access control and injection attacks represented more than 75% of web application attacks.
- SaaS providers together accounted for more than 28% of web application attacks.
- Moving to cloud-ready security solutions.
- 25% of surveyors shared that they have more than 50% of their application workloads in the cloud..
- Average Security Operations Center receives approximately 10,000 alerts per day for security alone.
- 9 out of 10 web applications, user can be attacked by hackers.
- In 39% of the sites, Unauthorized access to the application is possible.
- Breaches of sensitive data were a threat in 68% of web applications. Some reports state there is a 47% chance of breaches for personal data and around 31% for Credentials.
- 82% of issues were found in the application code itself.
- On average, the number of vulnerabilities per web application reached one third as compared to 2018.
- On average each system had 22 vulnerabilities and out of those 22, 4 were highly risky.
- In 2019 1 out of 5 vulnerabilities were highly vulnerable.
- High-risk vulnerable code dropped 17% compared to the previous year.
- On average the number of high-risk vulnerabilities on a single website has also dropped significantly in 2019. With every year showing consistent growth.
- 71% increase in security threats or attacks since the beginning of the Coronavirus outbreak, these attacks include fraudulent web pages, Email phishing, malware, and ransomware.
- When looking at global threats, these are the top mitigation measures that were used from January 2022 to March 2022 to keep customers sites and applications online, as well as secure.
- 38% of HTTP traffic is automated by bot traffic.
- 2019 report stated that security breaches had increased by 67% over the last five years.
- On average 30,000 websites get hacked every day.
- In 2020 the average time to detect a web application hack took 228 days.
- The average time to fix a web app breach is 80 days.
- WordPress is the tech powering 43.2% of websites on the web in 2021, this is up from 39.5% at the end of 2020.
- WordPress is heavily prone to breaches due to their extensive user database that tracks over 30 million websites.
- 29% of WordPress plugins with critical vulnerabilities were not patched.
- In 2021, WordPress added nearly 1.500 new vulnerabilities to the database.
- In 2020 96.22% of vulnerabilities originate from plugins and themes. In 2021, we see that number rise to 99.42%.
- In 2021, 6 out 18 components were outdated on a single website.
- Web Applications have become the #1 target for the exploitation of vulnerabilities.
- In a 2018 survey researchers found around 70 types of weaknesses in web applications.In 2019, a study found that hackers can attack 9 out 10 web applications.
- A 2019 study proved that 46% of web applications have critical vulnerabilities.
- 87% had medium security vulnerabilities.
- 30% of web applications are vulnerable to XSS.
- 81% of surveyors said they were increasingly worried about website security.
- Over 70% of digital agencies and freelancers are worried about website security.
- WordPress websites are #1 hacked web apps.
- 96% of web apps have some known defects.
- Half of internal-facing web application vulnerabilities are considered high risk.
- 50% of internal application vulnerabilities are considered high or critical risks.
- 32% of vulnerabilities in internet-facing applications are considered high or critical.
Crypto And Blockchain Security Statistics
Crypto is a form of digital currency that you can use to purchase services and goods. However, it uses an online ledger with strong cryptography for securing your online transactions called Blockchain. Blockchain is among the most secure technologies with data integrity, a decentralized system, and verifiability.
Blockchain has incredible potential to help companies verify the sources of their products and track supply chain movement, minimizing fraud and contamination issues.
- Worldwide spending on blockchain solutions hit $6.6 billion in 2021.
- By 2022, worldwide spending on blockchain solutions is estimated to reach $11.7 billion.
- Blockchain will grow at rate of 85.9% from 2022 to 2030.
- 68% of executives believe data security and privacy are the areas in greatest need of modification to help boost blockchain adoption.
- The global blockchain technologies market is expected to grow from $5.49 billion in 2021 to $8.61 billion in 2022.
- The global blockchain technology market is estimated to accumulate $20 billion in revenue by 2024.
- Blockchain tech is predicted to generate an annual business value of over $175 billion by 2025.
- Blockchain could add $407 billion in GDP in the USA alone.
- The UK stands to achieve a $72 billion boost to the economy, and Germany could see a $95 billion increase.
- 60% of CIOs were on the verge of integrating blockchain into their infrastructure by the end of 2020.
- Blockchain will boost global GDP by $1.76 trillion by 2030.
- 51% of attacks, in which hackers acquire more than half of the network’s computational power, are an issue that has plagued many blockchain systems.
- Hackers steal $46 million worth of cryptocurrency every month.
- Several of the top ten blockchain attacks are:
- Exchange hacks
- Decentralized finance hacks
- Phishing
- Rug pull
- Exit scams and others
- Six of the top ten most expensive crypto breaches occurred in 2021.
- Cryptocurrency theft grew even more, with roughly $3.2 billion worth of cryptocurrency stolen in 2021 — a 516% increase compared to 2020.
- IRS Criminal Investigations announced that it had seized over $3.5 billion worth of cryptocurrency in 2021 — all from non-tax investigations.
- Crypto investment funds manage over $59.6 billion in assets.
- Exploiting decentralized finance (DeFi) protocols was the fastest-growing way to steal crypto in 2021.
- DeFi is responsible for $1.4 billion of the overall crypto money lost alone in the previous year.
- DeFi protocols saw the most growth by far in usage for money laundering at 1,964%.
- A 2021 survey found around 52% of respondents believe there will be strong potential for blockchain in verifying customer billing instructions and reducing fraudulent activities.
- By the end of 2022, the number of US adults who own at least one cryptocurrency will climb 19.0% to 33.7 million.* That equates to 12.8% of the population.
- This year, 3.6 million US adults will use cryptocurrency.
- Crypto payment transaction value globally will surge 70.5% in 2022 to reach $10.40 billion. By the end of 2023, transaction value will grow another 55.4% to exceed $16 billion.
- 53% of the global organizations view blockchain as one of their top 5 strategic priorities.
- 90% of banks in the US and Europe introduced blockchain-related projects prior to 2018.
- The finance sector accounts for around 30% of the market value for blockchain.
- Blockchain can reduce as much as 30% of banking infrastructure costs.
- Implementing blockchain could save banks $12 billion annually.
- Blockchain has resulted in a reduction of transaction costs by up to 20% for consumer ticket bookings.
- Blockchain could increase the construction industries productivity up to 9%
- In 2019, the retail industry lost $62 billion to just one issue, fraud. With a blockchain receipt from every manufacturer, retailers could verify their deals and dramatically reduce that number.
- 90% of government organizations worldwide have investigated the potential of investing in blockchain technology, an IBM study found in 2017.
- Blockchain in healthcare industry are estimated to reach a total cost of $6.61 billion by 2025.
- Total spending on integrating blockchain into healthcare will rise to $5.61 billion by 2025.
- 55% of healthcare applications will have adopted blockchain for commercial deployment by 2025.
- Blockchain in healthcare will reach value of $1189.8 million by 2028.
- Blockchain market in manufacturing size grew to $85.64 billion in 2022.
Zero Trust Security Statistics
Just like the name implies, the zero-trust framework follows an implicit trust philosophy and commands us to “trust no one.” This is a significant departure from traditional security models that followed a “trust but verify” approach.
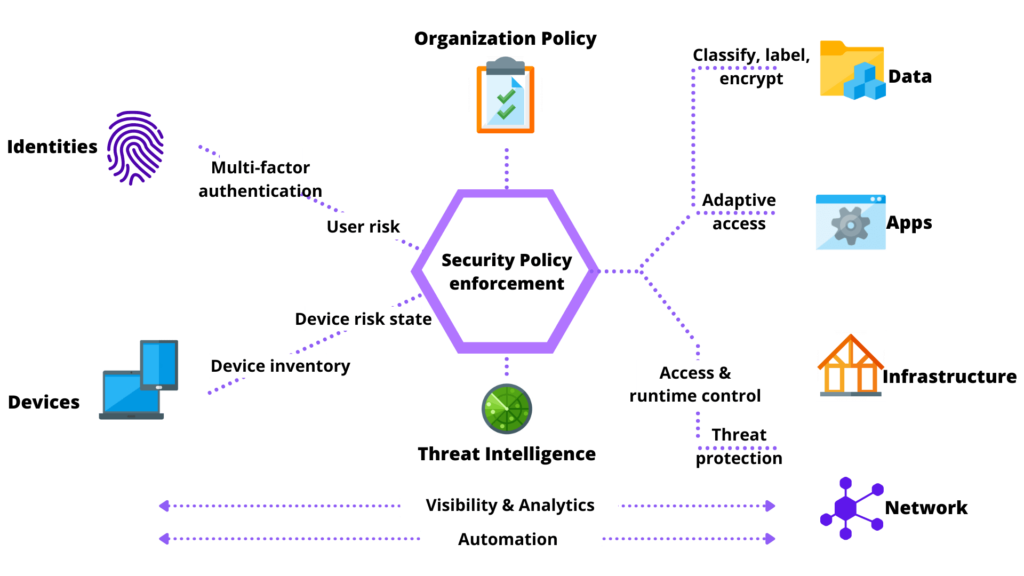
In contrast, the zero-trust security model requires continuous authentication, authorization, and validation of all internal and external users to gain and maintain secure zero-trust network access to apps and data on an enterprise network.
- 72% of respondents have plans of adopting Zero Trust in the future or have already adopted it.
- 15.2% Compound annual growth rate expected from 2021 to 2028 for the global zero trust security market.
- In 2022, 34 of global respondents indicated that zero trust security had a great impact in shaping cloud security strategy.
- Only 19% of respondents stated that zero trust did not affect their company’s cloud security strategy.
- As of January 2022, one third of respondents stated that their company already had a formal strategy in place and were actively embracing Zero Trust.
- Only 20% of respondents had no Zero Trust strategy as of 2022.
- Gartner estimates 47% of knowledge workers will work remotely in 2022.
- Microsoft’s Zero Trust Adoption Report highlighted the barriers to Zero Trust implementation. 53% mentioned leadership alignment such as C-suite and stakeholders as the biggest barrier.
- IBM rated average total cost of a breach of 1 to 10 million records at $52 million and a mega breach of 50 to 65 million records cost more than $400 million.
- A survey of nearly 1,300 network security professionals reported: 43% identified “identity and Access Management” as the first task to address as they begin to move into zero trust, “Network Security” placed second, at 20.8%.
- Advanced Zero Trust programs pose clear organizational benefits, including:
- Increased organizational agility (52%).
- Safer cloud migrations (50%).
- Support of digital transformation (48%).
- Zero Trust adoption will continue to mature.
- 78% of firms planning to bolster Zero Trust security operations in the new year.
- Implementing Zero Trust technologies can address emerging security gaps, but most enterprises are still in early stages of adoption.
- 36% of organizations have started to deploy Zero Trust solutions.
- A merely 6% of them have fully implemented their Zero Trust projects to date.
- Lack of expertise and stakeholder buy-in compounds implementation challenges.
- Business leaders consider micro-segmentation and Zero Trust Network Architecture (ZTNA) to be a critical technical foundation for their Zero Trust strategy (73%).
- 44% of business leaders report their organization needs help identifying and designing the most appropriate Zero Trust pilot.
- 62% of organizations attempted to use data center firewalls and software-defined networking(SDN), but they took to long to deploy.
- 53% found them to be too expensive and 50% said these approaches did not scale.
- 66% of those surveyed say they are planning to expand their Zero Trust budgets in 2022 – allocating 36% of their total spend to micro-segmentation projects.
- 68% of security leaders surveyed are counting on micro-segmentation to help in a variety of areas.
- Zero Trust Network Architecture (ZTNA) spending will grow from $820 million this year to $1.674 billion in 2025.
- 26% Compound Annual Growth Rate (CAGR).
- Worldwide spending is projected to reach $170 billion this year, increasing to $233 million by 2025, achieving an 11% CAGR.
- Security Services, infrastructure protection, and IAM will drive $122 billion in spending this year alone.
- Zero Trust becomes the foundation of more hybrid cloud integrations:
- 92% of enterprises have a multi-cloud strategy
- 82% have a hybrid cloud strategy
- IT leaders are keen to invest in Zero-trust but face issues around lack of expertise, and selling the concept into the C-suite.
- 66% percent of organizations plan to increase their zero trust spending, particularly around micro-segmentation initiatives.
- 60% are saying they had been unprepared for the rapid pace of cloud migration.
- 78% of IT Security teams are looking to embrace zero trust network access in the future. 19% are actively implementing zero trust, and 15% already have zero trust in place. At the same time, about half of the enterprise IT security teams (47%) lack confidence in their ability to provide zero trust with their current security technology.
- 62% of organizations say their biggest application security challenge is securing access to private apps that are distributed across datacenter and cloud environments. This is followed by minimizing exposure of private apps to the internet (50%), tied with gaining visibility into user activity (50%).
- When asked about the benefits of zero trust, two-thirds of IT security professionals (66%)say they are most excited about zero trust’s ability to deliver least privileged access to protect private apps.
- Organizations are considering implementing Zero Trust architecture more than any other cybersecurity solution.
- Zero Trust architecture is built on the philosophy of removing implicit trust from every level of an organization’s IT structure.
- Only 29% of security teams said they’d implement a zero-trust architecture when asked how they would protect against ransomware.
- Fully deployed Zero Trust saves companies 43% on average on data breach costs.
- Organizations without Zero Trust suffered upwards of $5.04 million in damages.
- With those using a fully deployed Zero Trust system saved $1.76 million per breach.
- Organizations can potentially see savings in the tens of millions of dollars over a five year period if it migrated to a zero trust security infrastructure.
- Companies with partially deployed zero trust saved $660,00 per breach.
- A full deployment takes time, the cost saving effect of zero trust is seen almost immediately.
- Another key component of Zero Trust is the use of AI and security automation.
- Organizations using AI and security automation detected & contained breaches 27% faster.
- AI automation alone in the architecture of zero trust saw savings on data breach cost.
- Organizations without AI and automation saw breach lifecycles – the time it takes to detect and contain – 324 days.
- Those that use AI and security automation in their security architecture experienced a lifecycle of 247 days. Saving two and a half months of remediation and decrease in loss of customers.
- By 2022 80% of new digital business applications opened up to ecosystem partners will be accessed through zero trust network access (ZTNA).
- By 2023 60% of enterprises wil phase out their remote access virtual private networks (VPN) in favor of Zero Trust.
- 30% of enterprises will adopt cloud-delivered Secure Web Gateway (SWG), Cloud Access Security Brokers (CASB), Zero Trust Network Access (ZTNA) and Firewall As A Service (FWaaS) capabilities from the same vendor.
- Along with implementation gaps, enterprises report several challenges in building a Zero Trust Strategy, starting with lack of qualified vendors with a complete solution.
- 80% of respondents reported that implementing a Zero Trust strategy across an extended network was not going to be easy – 60% said it would be moderately or very difficult or very difficult, and another 21% said it would be extremely difficult.
- In a survey of 1,009 IT security professionals, Zero Trust is a main security priority for most organizations, but comprehensive understanding and adoption of the Forrester-founded framework remains inconsistent,” One Identity said.
- 1,000 IT security Professional survey concluded:
- 99% of respondents say Zero Trust is important, including 75% who characterize it as “Critically” or “Very” important.
- Just 21% say they are ‘very confident’ in their organization’s understanding of Zero Trust.
- Barriers to adoption include a lack of clarity (32%), other priorities (31%) and lack of resources (29%).
- IT Security teams getting started with Zero Trust in a variety of ways.
- Top recommendations for getting started with Zero Trust include continuously verifying access (49%) and betting monitoring user access and privilege (48%).
- 61% of companies are reconfiguring access policies and 51% are implementing new technology as part of their Zero Trust implementation.
- Only 21% say they are “very confident” in their organization’s understanding of Zero Trust
- Only 24% report challenges with implementing Zero Trust
- Challenges include lack of clarity (32%), other priorities (31%), and lack of resources (29%)
- Zero Trust reduces an attackers ability to move laterally (44%).
- Enforcing least-privilege access to critical resources (44%).
- Reducing an enterprise’s attack surface (41%).
- Cyber security leaders named the following as the biggest cultural and environmental factors that hamper their ability to implement.
- Too many internal silos and stakeholders for different components of Zero Trust (47%).
- Too many legacy technologies that do not “support” zero trust (44%).
- Lack of internal expertise to develop a zero trust roadmap and policies (39%).
- 93% stated Zero trust benefits have matched or exceeded their expectations.
- Security breach costs surged 10% from last year.
- 30% of breaches involve internal factor.
- 82% of executives rely on Zero Trust concepts to enable digital transformative initiatives.
- Why Zero Trust is needed:
- 70% of breaches are from external sources.
- 67% of data breaches are the result of stolen credentials or human error.
- 37% of attacks use stolen or weak credentials.
- 41% of people would stop using a company that suffered a security breach.
- 30% of data breaches involved authenticated users.
Mobile Security Statistics
A mobile device is a general term for any type of handheld computer. These devices are designed to be extremely portable, and they can often fit in your hand. Some mobile devices—like tablets, e-readers, and smartphones—are powerful enough to do many of the same things you can do with a desktop or laptop computer.
- 42% of organizations report that vulnerabilities in mobile devices and web applications have led to a security incident
- Based on a study of more than 1.3 million Android and iOS apps, 14% of the apps using public cloud backends had misconfigurations that exposed users’ personal information.
- 30% of the known, zero-day vulnerabilities discovered in 2021 targeted mobile devices.
- The same year, there was a 466% increase in exploited, zero-day vulnerabilities used in active attacks against mobile endpoints.
- Further, 75% of the phishing sites analyzed specifically targeted mobile devices.
- 97% of companies have faced cyberattacks involving mobile threats
- Most organizations have experienced a mobile malware attack last year, and 93% of them began in a device network.
- The most common types of Malicious network traffic from devices include:
- Phishing messages designed to steal credentials (52%)
- Command and control traffic from malware on a device (25%)
- Browsing to infected websites or URLs (23%)
- Research has found that at least 40% of mobile devices contain hardware vulnerabilities.
IoT Security Statistics
The Internet of Things, or IoT, refers to the billions of physical devices around the world that are now connected to the internet, all collecting and sharing data. This network of physical objects—“things”— are embedded with sensors, software, and other technologies for the purpose of connecting and exchanging data with other devices and people across the globe.
- Companies could invest a total of up to $15 trillion in IoT by 2025.
- Forbes estimated 646 million IoT devices were used for healthcare in 2020.
- 44% of companies in the US have adopted IoT.
- In 2025, as many as 152,000 IoT devices will be connecting to the internet every minute.
- It’s estimated that 646 million IoT devices were used for healthcare in 2020.
- From $91 million in 2016, annual global spending on security measures for IoT networks is set to jump to $631 million in 2021, with a CAGR of 21.38%.
- IoT devices are typically attacked within five minutes of connecting to the internet.
- In 75% of cases, routers act as a gateway for IoT attacks.
- 48% of businesses admit they are unable to detect IoT security breaches on their network.
- Only 42% of US municipalities have turned to IoT devices, while nearly half of government IT departments have issues with IoT tech.
- 93% of executives believe the benefits of IoT outweigh the risks.
- More than 25% of all cyber attacks against businesses will involve IoT.
- 63% of companies say IT security is a critical skill for IoT.
- 98% of IoT traffic isn’t encrypted.
- 63% of consumers find connected devices “Creepy” concerning data collection.
- 55% of companies don’t require third-party IoT provider security and privacy compliance.
- Globally, 32% of the companies that have already adopted IoT consider data security issues related to the lack of skilled personnel to be the most critical concern for their IoT ecosystem.
- 33% of these companies consider attacks on devices to be the primary concern.
- From January to June 2021, there have been more than 1.5 billion IoT breaches, most of them using the telnet remote access protocol. The Internet of Things hacking statistics is on the rise due to the pandemic.
- Nearly 58% of the attacks occurred with the intent of mining cryptocurrency.
- An average smart home could be a target of more than 12,000 hacker attacks in a single week.
Working From Home Security Statistics
WFH means an employee is working from their house, apartment, or place of residence, rather than working from the office. Many companies have a WFH policy, or remote work policy, that allows their employees to work from home either full-time or when it’s most convenient for them.
- Remote work has increased the average cost of a data breach by $137,000.
- Only 9% of organizations use all the 5 must-have protections in place against internet-based attacks.
- 54% of IT professionals consider remote workers to pose a greater security risk than traditional workers.
- 12% of respondents that allow corporate access from mobile devices use a Mobile Threat Defense solution to protect their corporate assets and users.
- 31% don’t use any of the mentioned methods to prevent sensitive business data from leaking outside the organization.
- Employees are a vulnerable target as 48% of malicious email attachments are office files.
- 82% of employers report a shortage in cyber security skills.
- 66% of security breaches are a result of employee negligence or malicious acts.
- Home workers are the primary target of criminals as cyber attacks have risen 238% since the beginning of the pandemic.
- 44% of those surveyed said they didn’t provide cyber security training to their staff on the threats of working from home.
- 68% of the organizations surveyed did not deploy antivirus software for work-issued devices.
- 47% of employees cited distraction as the reason for falling for a phishing scam while working from home.
- 24% of respondents had to spend money unexpectedly to resolve a security breach or malware attack following the WFH shift.
- 20% of respondents reported that they don’t use any of the methods mentioned to protect remote users while browsing the internet, and only 9% use all the methods mentioned to protect against internet-based attacks.
- 26% don’t have an endpoint solution that can automatically detect and stop ransomware attacks.
- Based on a 1200 security professionals survey on what their endpoint security can do in case of a ransomware attack.
- only 16% reported it can do all of the mentioned capabilities, and 26% reported their endpoint security solution can’t do any of the mentioned capabilities.
- Only 12% of organizations that allow corporate access from mobile devices use a Mobile Threat Defense solution.
- 26% of people interviewed reported being tempted to keep copies of valuable company data in case “the worst comes to the worst” (the company becomes insolvent or they lose their job).
- Remote workers have caused a security breach in 20% of organizations.
- Email phishing attacks were the most common source of data breaches while working from home.
- One quarter of all employees have noticed an increase in fraudulent emails, spam and phishing attempts in their corporate email since the beginning of the COVID-19 crisis.
- Whether the benefits of remote work outweigh the risks, 92% said they believe they do.
- 90% of respondents believe remote workers pose a security risk in general.
- 54% believe that remote employees pose a greater security risk than onsite employees.
- 73% of VP and C-suite IT leaders believe remote workers pose a greater risk than onsite employees compared to 48% of IT managers and 45% of IT directors.
- 25% of employees use the same password for everything.
- 24% haven’t updated their remote work security policy in more than a year.
- 49% of IT leaders say they only somewhat agree that remote employees adhere to remote work policies.
- 44% of organizations do not let IT teams take the lead role in developing the remote work security policy.
- 5% of the data breaches involved remote workers.
- The average cost of a breach was $1.07 million higher in breaches where remote work was a factor in causing it.
- Organizations with more than 50% of their workforce working remotely took 58 days longer to identify and contain breaches (and it should be noted that the average number of days is 287, making this nearly a year’s time!).
- 57% report that more than half of their workforce works remotely at least 2 days a week.
- 94% of organizations allow remote access to corporate apps and assets from unmanaged and managed devices,
- 17% reported they allow remote access only from company-managed laptops.
- The data showed that since organizations moved to a work from home (WFH) model, the potential for cyberattacks and breaches has increased:
- 20% of respondents said they faced a security breaches as a result of a remote worker.
- 24% of respondents saying they paid unexpected expenses to address a cybersecurity breach or malware attack following shelter-in-place orders.
- 28% of respondents admitted they’re using personal devices for work-related activities more than their work-issued devices.
- 61% of respondents’ organizations did not urge employees to use antivirus solutions on their personal devices.
- 18% of respondents admitted that, for their employees, cyber security was not a priority, while 5 percent said their employees were a security risk and oblivious to security best practices.
- 44% of respondents’ organizations did not provide cybersecurity training that focused on potential threats of working from home (like ensuring home networks had strong passwords, or devices were not left within reach of non-authorized users).
- 61% of respondents’ organizations provided work-issued devices to employees as needed, 65% did not deploy a new antivirus (AV) solution for those same devices.
- The statistics below convey how many organizations allow remote access to corporate applications:
- 51% from personal mobile devices.
- 52% from personal laptops.
- 32% by third-parties.
- 6% do not allow any remote access.
- Below are more statistics pertaining to how organizations secure remote access to corporate applications:
- 73% use VPN connections.
- 46% use multi-factor authentication.
- 18% use Device risk posture check.
- 16% use Zero Trust Network Access.
- For the 9% of organizations that do protect remote users who are browsing the internet, here are the methods they use:
- 55% use URL filtering.
- 49% use URL reputation.
- 41% use content disarm & reconstruction (CDR).
- 31% use zero phishing.
- 17% use credentials protection.
- 43% of remote employees use disk encryption on endpoint devices.
- 42% of remote employees scan to email and office apps for sensitive data.
- 30% of remote employees scan files for sensitive content.
- 20% of organizations don’t use any methods to protect remote users who are browsing the internet, and only 9% use methods to protect against internet-based threats.

Cybersecurity Statistics By Industry
Cybersecurity Statistics For Healthcare
 Patient data is particularly valuable to the criminal community. Electronic Health Records (EHR) contain a wealth of information about each patient: name, social security number, financial information, current and previous addresses, medical history and names of next of kin.
Patient data is particularly valuable to the criminal community. Electronic Health Records (EHR) contain a wealth of information about each patient: name, social security number, financial information, current and previous addresses, medical history and names of next of kin.
Threat actors may also target medical devices such as patient monitoring equipment. This equipment is often linked to a computer and therefore potentially to the whole network.
- 16% of healthcare providers report having a “fully functional” cybersecurity program.
- 43% say that they are either still developing security programs or have not developed one.
- 82% of surveyed healthcare organizations say that security is a top concern.
- 69% of those in the healthcare industry believe they are at risk for a data breach.
- 94% are now using some form of advanced DLP software to protect sensitive data.
- 89% of healthcare organization had patient data lost or stolen in the past two years.
- Patient health records can be sold for as much as $363 on the black market, which is more than any piece of information from other industries.
- 93% of healthcare organizations are currently using some form of cloud services.
- 63% plan to use multiple cloud vendors.
- 25% of healthcare organizations using the public cloud report that they are not encrypting patient data.
- Healthcare has the highest number of attacks by ransomware over any other industry.
- The healthcare industry was the victim of 88% of all ransomware attacks in US industries in 2016.
- 20% of healthcare domain emails were fraudulent in 2017.
- Healthcare organizations were targeted 473% more often in Q4 2018 vs Q1 2017.
- 54% of healthcare business associates say their top vulnerability is tied to employee negligence in handling patient information.
- 81% of healthcare cyber security incidents are rooted in employee negligence.
- 69% of healthcare organizations cite negligent or careless employees as their top worry for security incidents, followed by cyber attacks (45%) and insecure mobile devices (30%).
- The average cost of a cyber attack in healthcare is $3.62 million.
- Data breaches are costing the US healthcare industry about $6.2 billion per year.
Cybersecurity Statistics For Financial Services
- 67% of financial institutions reported an increase in cyber attacks over the past year.
- 26% of financial enterprises faced a destructive attack.
- 79% of financial CISOs said threat actors are deploying more sophisticated attacks.
- 21% suffered a watering-hole attack in the last year.
- 32% of financial institutions encountered island hopping, is leveraging one compromised organization to gain entry into another.
- 25% of all malware attacks hit banks and other financial industries, more than any other industry.
- Credit card compromised increased by 212% year over year, credential leaks experienced a similar increase of 129%, and malicious apps increased by 102%.
- 47% of financial institutions reported an increase in wire transfer fraud.
- 31% of financial institutions reported an increase in home equity loan fraud.
- 79% of financial institutions said cybercriminals have become more sophisticated, leveraging highly targeted social engineering attacks.
- 32% of financial institutions reported experiencing counter-incident response.
- 21% of financial institutions reported experiencing C2 on a sleep cycle.
- 70% of financial institutions said they are most concerned about financially motivated attackers.
- 30% of financial institutions said they are most concerned with nation-state activity.
- Global attack types and sources on financial sectors:
- Web attacks – 46%
- Service-specific attacks – 28%
- DoS/DDoS 8%
- 69% of financial institution CISOs are planning to increase cyber security spending by 10% or more in 2019.
- 47% of financial institution CISOs said their organizations are operating threat hunt teams.
- 32% of financial institution CISOs said they conduct threat hunts on a monthly basis.
- 70% of cyber crimes targeting surveyed financial institutions involve lateral movement.
Cybersecurity Statistics For Federal And Local Government
- Over 70,000 Department of Defense contractors are required to meet CMMC compliance by 2021.
- Nearly 60 million Americans have been affected by identity theft.
- U.S. government to spend $15 billion on cyber security-related activities in 2019 up 4% over the previous year.
- The United States is the number one target for targeted cyber attacks.
- United States: 38%.
- India: 17%.
- Japan: 11%.
- Taiwan: 7%.
- Ukraine: 6%.
- South Korea: 6%.
- Brunei: 4%.
- Russia: 4%.
- Vietnam: 4%.
- Pakistan: 3%.
Cybersecurity Statistics For Small Business
While it’s true that enterprise companies are targeted by cyber attacks daily it’s actually small businesses that face the most risk of loss.
This is because threat actors view small businesses as easier targets having less money to invest into security like financial institutions or technology companies may.
- 43% of cyber attacks target small businesses.
- 47% of small businesses had at lease on cyber attack in the past year, 44% of those had two to four attacks.
- 70% of small businesses are unprepared to deal with a cyber attack.
- 3 out of 4 small businesses say they don’t have sufficient personnel to address IT security.
- 66% of small business are very concerned about cyber security risk.
- 85% of small businesses plan to increase spending on managed security services.
- 51% of small businesses say they are not allocating any budget to cyber security.
- 58% of malware attack victims are categorized as small businesses.
- In 2018, cyber attacks cost small businesses an average of $34,604.
- Ransomware damage costs alone are on track to hit $11.5 billion in 2019, at which point it’s estimated that small businesses will fall victim to a ransomware attack every 14 seconds.
- 4% of malware sent to small businesses is delivered via email.
- The most common malicious email disguises are:
- 7% bill / invoice
- 3% email delivery failure notice
- 4% package delivery
- 1.1% legal/law enforcement message
- 0.3% scanned document
- 60% of small businesses say attacks are becoming more severe and more sophisticated.
- Only 14% of small businesses rate their ability to mitigate cyber risks, vulnerabilities and attacks as highly effective.
- 60% of small companies go out of business within six months of a cyber attack.
- 48% of data security breaches are caused by acts of malicious intent. Human error or system failure account for the rest.
- Small businesses are most concerned about the security of customer data:
- Consumer records 66%
- Intellectual property 49%
- Customer credit or debit card information 46%
- Financial information 26%
- Employee records 8%
- Business correspondence 5%
- Other 1%
- The types of cyber attacks on small businesses broke out as following:
- Web-based attack 49%
- Phishing / social engineering 43%
- General malware 35%
- SQL injection 26%
- Compromised / stole devices 25%
- Denial of services 21%
- Advance malware / zero day attacks 14%
- Malicious insider 13%
- Cross-site scripting 11%
- Ransomware 2%
- Other 1%
- Percentage of small businesses that store valuable data
- 68% store email addresses
- 64% store phone numbers
- 54% store billing addresses
- Small businesses are not investing in cyber security
- 38% regularly upgrade software solutions
- 31% monitor business credit reports
- 22% encrypt databases
- 69% of small businesses do not strictly enforce password policies.
- 16% of small businesses say they had only reviewed their cyber security posture after they were hit by an attack.
- Only 16% of small business are very confident in their cyber security readiness. These areas are lacking:
- Strategy – 52% of small business have a clearly defined strategy around cyber security.
- Accountability – 23% of small businesses have a leadership role dedicated to cyber, whereas 46% have no defined role at all.
- Willingness to respond – 65% of small businesses have failed to act following a cyber security incident.
- Training – 32% of small businesses have conducted phishing experiments to assess employee behavior and readiness in the event of an attack.
- Insurance – 21% of small businesses have a standalone cyber insurance policy, compared to 58% of large companies.
- 4 out of 5 small businesses report malware has evaded their antivirus.
Cybersecurity Statistics For Higher Education And School Districts
- The education industry is ranked last in cyber security preparedness out of 17 major industries.
- 41% of higher education cyber security incidents and breaches were caused by social engineering attacks.
- There were 455 cyber security incidents in the educational sector last year.
- Educational records can fetch up to $265 on the black market.
- 43% have had student data attacked, including dissertation materials and exam results.
- 25% have experienced critical intellectual property theft.
- 28% have had grant holder research data attacked.
- 87% have experienced at least one successful cyber attack.
- 83% believe cyber attacks are increasing in frequency and sophistication.
- 79% universities have experienced damage to reputation and almost 74% have had to halt a valuable research project as a result of a cyber attack.
- 77% also say a cyber breach has the potential to impact national security, due to the potentially sensitive nature of the information which could been compromised.
- 64% don’t believe their existing IT infrastructure will protect them against cyber attacks in next 12-18 months.
- 27% see the current security of their data center as ‘inadequate’ and in urgent need of updating.
- 85% of universities agree that more funding must be given to IT security to protect critical research IP.
- On average, 30% of users in the education industry have fallen for phishing emails.
- The education sector accounted for 13% of all data security breaches during the first half of 2017, resulting in the compromise of some 32 million personal records.
- In March 2018, over 300 universities worldwide suffered from a giant cyber attack organized by nine Iranian hackers. According to the official information, 31 terabytes of “valuable intellectual property and data” was exposed.
Cybersecurity Statistics By Solution
Endpoint Detection And Response Statistics
Endpoints are network-connected computing devices, capable of communicating with other points and devices across the network. Such devices come in many forms, from PCs, tablets, and mobile phones to smart vehicles and light bulbs.
While these devices form endpoints on a network they are often the starting point of a cyber attack, which is why a focus on endpoint security is essential. This is especially relevant in a corporate environment, where sensitive business data is at stake.
- EDR has been adopted by more than a third of security teams as of 2020 (35%).
- The number of organizations using an EDR tool is expected to double (2x) over the next 5 years.
- Reducing incidents and breaches is the second leading factor for security spending.
- The percentage of organizations that will use Managed EDR services will grow to 25% by 2024.
- 68% of organizations have experienced one or more endpoint attacks that successfully compromised data and/or their IT infrastructure.
- Gartner’s latest EDR Forecast predicts that global enterprises’ spending will reach $13.3 billion in 2021, growing tp $26.4 billion in 2025.
- 82% of CISOs have reevaluated their security policies in response to the support needed for work-from-home (WFH) and virtual teams, endpoints often lack needed patches to stay secure or are overloaded with conflicting software agents.
- 76% of IT security decision-makers say their enterprise EDR has increased in 2021.
- Global Market Outlook (2017-2026), sales of EDR solutions—both on-premises and cloud-based—are expected to reach $7.27 billion by 2026, with an annual growth rate of nearly 26%.
- 39% of businesses reported cyber security breaches or attacks in the last 12 months.
- 31% of businesses experience breaches or attacks at least once a week.
- 1 in 5 of the businesses reporting cyber-attacks lost money, data, or other assets.
- 70% of successful breaches begin on endpoint devices.
- 44% of IT departments manage somewhere between 5,000 and 500,000 endpoints.
- 68% of organizations suffered one or more endpoint attacks that successfully compromised their data and/or IT infrastructure.
- At least 87% of organizations permit employees to use personal mobile devices in the workplace. Thus, managing and securing mobile devices is one of the most vital EDR use cases for companies today.
- Additional research revealed that endpoints are among the most targeted, with 81% of companies reporting malware having infected their devices.
AI Cybersecurity Statistics
AI/ML—short for artificial intelligence (AI) and machine learning (ML)—represents an important evolution in computer science and data processing.
The goal is to simulate natural intelligence to solve complex problems. The goal is to learn from data on certain tasks to maximize the performance of that task. AI is decision-making. ML allows systems to learn new things from data.
- 61% of enterprises claim that they are unable to perform intrusion detection without using AI and ML.
- 50% of organizations that deployed AI cybersecurity solutions used it to aim detection
- 69% of organizations surveyed in a Capgemini study said AI security is urgent, and this number is likely to grow as more are hit by AI-driven attacks
- 48% of the executives surveyed say they make extensive use of AI in cyber threat detection, 34% use it extensively for prediction, and 18% use it for a response.
- AI reduces the time taken to remediate a breach or implement patches in response to an attack by 12%.
- 28% of respondents are using security products with AI embedded, with 30% using proprietary AI algorithms, and 42%, currently either use (or plan to use by next year).
- 73% of respondents said they were testing use cases for AI for cyber security in some way.
- 43% of executives see an increase in machine-speed attacks.
- Implementing machine learning into a company’s sales and marketing efforts shows a 47% increase.
- Recent machine learning statistics tell us that 80% of companies are planning to use A.I. at some point in the near future
- Machine learning statistics show that this kind of technology increases business productivity by up to 54%.
- 92% of top companies are currently investing in artificial intelligence.
- 48% of businesses are using machine learning, deep learning, data analysis, and natural language processing to effectively make use of large data sets.
- AI and machine learning reduce the effort required to detect and respond to cyber threats, making them cost-effective technologies.
- The average cost reduction is 12%, with some organizations lowering their costs by more than 15%.
- 61% of organizations say they will not be able to identify critical threats without AI, while 69% believe AI will be necessary to respond to cyber attacks.
- Security automation and AI can save businesses more than 80% of the cost of manual security by reducing tech time and improving threat detection thanks to machine learning.
- 51% of enterprises have plans to implement AI for automated processes.
- 3 in 5 firms said AI improves the accuracy and efficiency of their analysts.
- Nearly 75% of executives said AI increases the accuracy of detecting a breach.
- AI reduces overall detection time, on average, by 12%.
- By 2025 over 50% of the revenue of the major consultancies will be derived from service delivery that leverages automation and AI instead of just human resources.
- 3 out of 4 surveyed executives say that AI allows their organization to respond faster to breaches.
- 69% of organizations think AI is necessary to respond to cyber attacks.
SIEM Statistics
Lorem ipsum dolor sit amet, consectetur adipiscing elit. Ut elit tellus, luctus nec ullamcorper mattis, pulvinar dapibus leo.A Security Information and Event Monitoring solution (SIEM) aggregates log and event data from an exponentially-growing number of data sources across the infrastructure (applications, network and endpoint security tools, cloud monitoring tools, identity providers, etc.).
This data is then analyzed using predefined threat detection rules and queries to identify suspicious or unauthorized behavior.
- Costly to maintain: 75% of SIEM costs are operational after purchase.
- With a compound annual growth rate (CAGR) of 5.5%, it’s anticipated to grow to $5.5 billion by 2025.
- Industry-wise, the retail and software industries combined make up 27% of the demand in the SIEM industry.
- Enterprise SIEMS are missing detections for 80% of all MITRE ATT&CK techniques.
- 15% of SIEM rules are broken and will never fire due to common issues such as misconfigured data sources and missing fields.
- Only 25% of organizations that forward identity logs such as Active Directory and Okta to their SIEM, actually use them in their detection rules.
- On average, SIEMs only cover 20% of the 190+ adversary techniques described in MITRE ATT&CK v10.1.
- On average, SIEMs cover fewer than 5 of the top 14 techniques used by adversaries in the wild, based on 2021 threat intelligence data from Recorded Future, Red Canary, and Picus Security.
- On average, 75% of default out-of-the box (OOB) rules provided by SIEM vendors are disabled, due to the difficulty of adapting generic rules to each organization’s unique infrastructure, log sources, naming conventions, and more.
- The total cost of deploying a SIEM solution is:
- SIEM Software – $20,000 – $1 million
- Implementation – $50,000
- Training – $0 – $10,000
- Resources – $74,000 – $500,000
- Hardware – $25,000 – $75,000
- Infrastructure – $10,00
- Among 300 IT and security leaders, the top outcomes respondents expect by switching to cloud-based SIEM include:
- 40% —lower staffing costs.
- 40% —lower operational expenses (OpEx).
- 34% —lower capital expenses (CapEx).
- Cloud-based SIEM users spend, on average, $541,000 per year to support their solution, while on-premises companies are averaging $607,000.
- On-premises SIEM users are 11 percent more likely than cloud-based implementers to cite total cost of ownership as an existing challenge.
- Organizations are averaging 27 full-time employees to carry out SIEM-related infrastructure, maintenance, and training tasks.
- Among the cloud SIEM deployments, the majority (57%) made the migration in the past two years. It appears that a primary reason for this migration is cost.
- Despite 81% saying their security operations centers (SOCs) are adequately staffed, respondents admit their security personnel are spending far more time (60%) on routine IT operations tasks versus security-related functions (27%).
- If SIEM costs $1 million to purchase, operating expenses might easily reach $3–4 million annually.
Virtual Private Network Statistics
VPN stands for “Virtual Private Network” and describes the opportunity to establish a protected network connection when using public networks. VPNs encrypt your internet traffic and disguise your online identity. This makes it more difficult for third parties to track your activities online and steal data.
- A study found that 85% of free VPNs have permissions or functions that could compromise a user’s privacy, while 35% of VPNs expose a user’s traffic, and 18% contain potential malware or viruses.
- 31% of internet users worldwide have used a VPN service.
- VPN usage increased by 27.1% in 2020 alone.
- 88% of companies migrated employees to remote work in 2020, raising demand for VPNs.
- The top market for VPN usage in 2021 was Indonesia, with 44% of people using a VPN.
- By 2027, the VPN marketplace is projected to reach a value of $107.5 billion.
- Due to the coronavirus pandemic, VPN usage grew even more, and the market for VPNs is now expected to exceed $92 billion in 2027.
- 49% of users choose VPNs for general security, whereas 31% of users connect to public WiFi through VPNs.
- A separate study of VPN apps with free plans available for Android devices found that 75% of the apps used third-party tracking, and more than 38% contained some type of malware.
- 57% of mobile users used VPNs to access better TV, movies, and games, compared to 54 percent of PC or laptop users.
- VPN usage survey, nearly half of people that use VPNs did so for general security, while another (40%) did so for general privacy.
- Research has shown that VPNs increase data usage by anywhere between 4% and 20%, depending on which VPN protocol you’re using.
Managed Detection & Response Statistics
Managed Detection and Response (MDR) is a cybersecurity strategy focused on detecting cyber-attacks before they reach a critical stage. MDR relies on cloud computing, which provides important information about a threat and how it was detected. MDR takes this information and creates defensive measures to combat the attack.
- By 2025 50% of organizations will be using MDR services.
- 94% of organizations are evaluating MDR services.
- 79% of organizations are considering adopting MDR soon.
- 68% of the MDR market is occupied by large businesses.
- By 2024 more than 90% of organizations looking to outsource security will focus on detection and response services.
- 30% of organizations leveraging Open Systems MDR saw a reduction in overall risk.
- Organizations investing in MDR services saw a:
- 50% reduction in the delta of Mean time to detect (MTTD) and Mean time to respond (MTTR).
- Up to 50% cost savings in Cyber security operations.
- 60-75%+ attainment on first-to-know and first-to-report threats.
Frequently Asked Questions
Where do most cyber attacks come from?
It is reported by the Center for Strategic and International Studies (CSIS) that China and Russia are the biggest cyber offenders and have been since 2006. From 2006 to 2018, China was involved in 108 cyber incidents with losses of more than $1 million each. Russia has been responsible for 98 major cyber incidents since 2006 with losses of more than $1 million each. The study named the rest of the world as the third-worst offender, with 67 incidents. Next in the ranking came Iran with 44 incidents, and North Korea with 38. India was listed as guilty of 16 important cyber incidents from 2006 to 2018, while the U.S. was accused of nine.
What percentage of malware is distributed by email?
Nearly 98% of all cyber attacks rely on some form of social engineering to deliver a payload such as malware. The most popular method of initiating a social engineering attack is through phishing emails. Therefore, threat actors distribute malware via email approximately 92% of the time.
How many businesses are targeted by spear-phishing attacks each day?
62% of businesses experienced phishing and social engineering attacks in 2018 with a new organization falling victim to ransomware every 14 seconds in 2019.
What percentage of successful cyber attacks were caused by someone falling for a phishing attack?
The total number of spear-phishing campaigns targeting employees increased by 55%, which makes up 71% of all targeted attack on businesses. Given the rise in phishing attacks it is estimated that 90% of incidences and breaches included a phishing element in 2019.
AI Vs AI: The Biggest Threat To Cybersecurity
AI-Powered Cyber Attacks: The Future Of Cybercrime
The Average Cost Of Ransomware Attacks (Updated 2025)
AI In Cybersecurity: Defending Against The Latest Cyber Threats
Our Services Work Better Together
Ready To Get Secure?
Reach Your Security Goals With Affordable Solutions Built For Small Business




