Saudi Aramco $50 Million Data Breach Explained
Contents
In this week’s episode of The Breach Report, we cover the Saudi Aramco data breach.
This breach is different from the spate of recent ransomware attacks in that it isn’t really ransomware, and may not even be extortion.
To get more on that, we’ll cover what we know so far about the attack, how it happened, who is responsible, the type of data that has been stolen, and how organizations can avoid becoming victims of the same breach.
Stay Up-To-Date On The Latest Attacks
Be the first to know when our experts release new insights on the top attacks.
You're on the list! Just one more step...
Check your email to confirm your subscription.
How Did The Saudi Aramco Data Breach Happen?
Saudi Aramco didn’t even know about a data breach until 1 terabyte of their data had been leaked online. According to ZDNet, they denied that it was from their systems that they were breached.
Aramco recently became aware of the indirect release of a limited amount of company data which was held by third-party contractors,” the spokesperson said. “We confirm that the release of data was not due to a breach of our systems, has no impact on our operations, and the company continues to maintain a robust cybersecurity posture.
Saudi Aramco said third parties were scrapped for data or possibly breached. That’s where the data was taken from and put up for sale.
Is This A Proof Of Concept?
It’s possible that these threat actors were only trying to find what data was publicly available. Alternatively, the threat actors may be advertising their skill sets to show off their capabilities.
When you go to certain hacking conferences, you see some showcasing their zero-day exploits. You might wonder why they’re showing off an exploit that they could sell for $100,000.
However, it’s not about selling that particular exploit. It’s about creating relationships.
Once credibility is established, these threat actors are contacted by paying parties to run campaigns against other organizations.
Free Security Policy Templates
Get a step ahead of your cybersecurity goals with our comprehensive templates.

What Data Was Breached?
Full personal identifiable information on 14,254 employees was exposed including:
- Employee Names
- Phone Numbers
- Photos
- Passport Copies
- Email Addresses
- Job Titles
- Residence Permits
Technical data that was exposed includes:
- Project Specification For Systems
- Architectural Engineering
- Construction management
- Machinery
- Vessels
- Telecom
- Internal Reports
- Agreements
- Memos and Letters
- Pricing Sheets
- Network Maps
This means threat actors have access to IP addresses, scatter points, WiFi access points, IP cameras, and IoT devices.
In addition, the network location map has precise coordinates of where all these data systems are. Finally, the threat actors have access to Saudi Aramco’s clients along with invoices and contracts.
Who Is Responsible For The Saudi Aramco Data Breach?
ZeroX is the threat group claiming responsibility for this attack. Despite reaching out to internal sources, PurpleSec was unable to uncover further information about this group, their origins, or other attacks they’ve been involved in.
What Are The Extortion Payment Terms?
ZeroX is posting the information for sale online for $50 million. Little else is known about whether Saudi Aramco has paid the demand. ZeroX did post a screenshot sent to Bleepingcomputer of a timer counting down from 662 hours, or approximately 28 days.
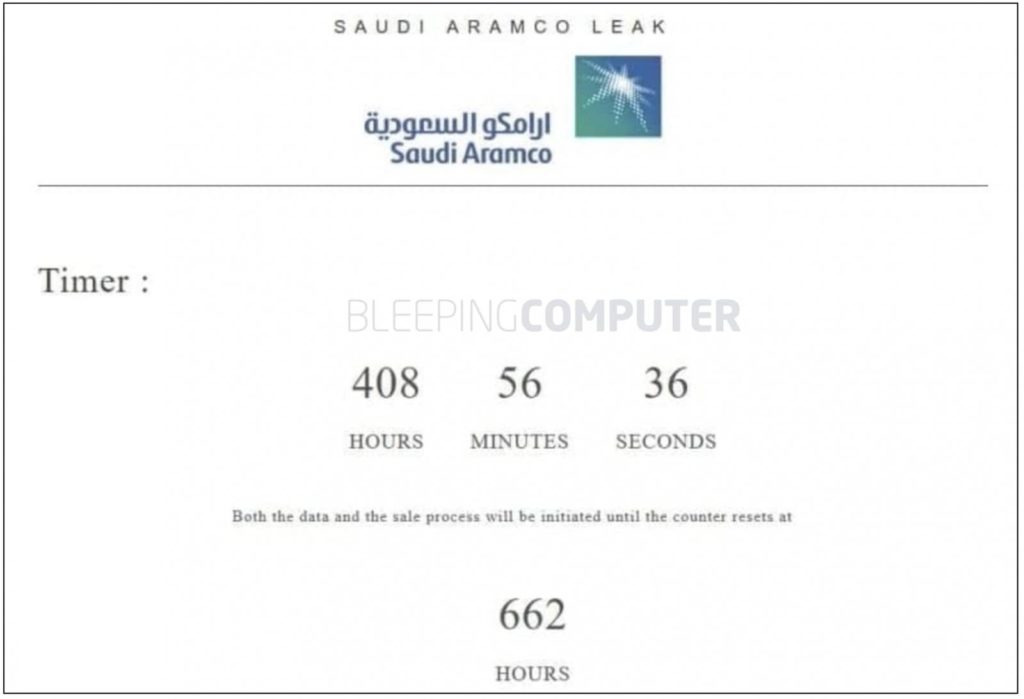
When questioned about the meaning of this screenshot all the threat group said is that it’s a puzzle for Saudi Aramco to figure out.
It’s likely that ZeroX is either messing with Saudi Aramco or they’re attempting to put pressure on Saudi Aramco to pay the demand before that information is released online.
What Is The Current Status Of This Attack?
As of July 27, 2021 Saudi Aramco’s data is still up pending sale.
ZeroX has mentioned at least five interested buyers but did not provide details of who those buyers were or provide evidence that those buyers exist.
It is possible that one of those buyers is Iran, as they were suspected in the Shamoon attack back in 2012, which impacted up to 30,000 systems and caused disruption to Saudi Aramco’s services for several weeks.
Regardless of who the buyer is, this is a treasure trove of data on Saudi Aramco, which keeps the buyer’s hands cleaner as they’re not the ones breaching the systems.
This information could also be used to sell future malicious campaigns against Saudi Aramco.
This may include phishing or other forms of social engineering, or a targeted penetration test against the network and its employees.
What Can Companies Do To Prevent This Type Of Breach?
There are a couple of layers and steps that companies can take to prevent a data breach like the one impacting Saudi Aramco.
Third Party Security Risk Assessments
The first step is to conduct a security risk assessment provided by a third-party vendor. A risk assessment will not necessarily prevent this type of breach. However, it will help you better understand your risk through third parties.
This is considered best practice when it comes to identifying security gaps and guiding the direction of your cyber security program.
A risk assessment also answers questions such as:
- Where is your data going on a third parties networks?
- How is a third party protecting that data?
And do they protect that, which brings in the next step, which should be done, and really should all be done in tandem, but you kind of have to build a program, right?
Data Segregation
After assessing your third parties, the next questions to answer are:
- What kind of data are you sending to your third parties?
- Are you sure third parties don’t have access to data they shouldn’t have?
Data inventory and data segregation on your network will help you to better understand how data flows in and out of your systems.
If one of these third parties does get breached, you won’t be in the position that Saudi Aramco is in where everything from passport photos to IP addresses to geo-coordinates of SCADA systems is exposed.
As a result, you can limit the type of data threat actors can pull out of your third
Zero Trust Security
From a security perspective, a defense in-depth approach plus zero trust is the future of security maturity. Zero trust takes things a step further by limiting the actual splash damage caused by threat actors.
There are a few considerations when assessing the potential splash damage from a third-party breach:
- If one system is infected then do threat actors have the means to infect more?
- If more than one system can be infected then how many in total can be accessed?
- How many of those systems can threat actors collect data from?
With zero trust, your organization effectively turns every system and point of access into its own environment and perimeter. Each environment has its own rules per perimeter thereby limiting access only to users who have permission.
To implement zero trust it requires you to understand your network inside and out and requires eliminating technical debt in the organization.
While there are significant upfront costs and resources required, zero trust does control the splash damage, which prevents these types of attacks from happening.
Or, at the very least limits the impact.
Ultimately, implementing zero trust reduces maintenance of security and enables organizations to offload many third party security solutions.
Article by
Share This Article
Our Editorial Process
Our content goes through a rigorous approval process which is reviewed by cybersecurity experts – ensuring the quality and accuracy of information published.
Categories