Physical penetration testing simulates a real-world threat scenario where a malicious actor attempts to compromise a business’s physical barriers to gain access to infrastructure, buildings, systems, and employees.
- Common methods used include:
- Mapping The Entrances And Perimeter
- Lock Picking
- Accessing Sensitive Information
- Testing Server Rooms, Wires And Cables
- Testing Fire And Cooling Systems
- Intercepting EM Waves
- Dumpster Diving
- Breaking RFID Tags’ Encryption
- Gaining Physical Access (Tailgating)
- Testing Network Jacks
- Checking Meeting Rooms
- Shoulder Surfing
- Social Engineering Employees
The goal of a physical penetration test is to expose weaknesses in a business’s overall physical defenses. Through identifying these weaknesses proper mitigations can be put in place to strengthen the physical security posture.
In this article, I’m going to share 13 methods that physical penetration testers use to bypass million-dollar physical security controls in seconds.
By the end, you’ll have a better understanding of how to protect your business from a physical breach of your network.
Sample Network Pen Test Report
What should a penetration test report include? Download our sample report to learn.
What Are The Benefits Of Physical Penetration Testing?
The primary benefit of a physical penetration test is to expose weaknesses and vulnerabilities in physical controls (locks, barriers, cameras, or sensors) so that flaws can be quickly addressed.
In addition, physical penetration tests mimic real-world scenarios to demonstrate what impact a malicious actor can have on your systems.
Physical security penetration testing, when performed properly, will strengthen your security defenses and allow you to focus on the digital side of your security.
It makes no sense to throw millions of dollars on security tools if an attacker can get inside your company buildings and slip out unnoticed.
What Methods Are Used In Physical Penetration Testing?
A business cannot have a resilient cybersecurity program in place without ensuring that malicious actors cannot physically bypass its perimeter.
This is why performing physical penetration tests is important, and having a methodology and framework to do so is key in ensuring you do not miss any critical aspects of your physical security.
The following are a series of steps and methods you can take to perform a physical penetration test:
1. Map The Entrances And Perimeter
Start by mapping all the possible entrances into the business to identify unsecured entry points. Attackers often find hidden or unguarded entrances to gain access to buildings.
By mapping doors, windows, and fire exits, you begin to define the premises you need to secure and that are susceptible to attack.
Mapping the perimeter involves conducting an in-depth analysis of your surroundings and buildings, and represents the equivalent of a reconnaissance phase, which is conducted in every other type of penetration test.
Simply put, thoroughly mapping your perimeter will determine the direction of the entire physical penetration testing process and it consists of identifying:
- Doors
- Windows
- Roof type
- Basement access
- Physical access policy
- Lock types
2. Lock Picking
Even today, one of the most effective ways to pass through doors and exits is by using lock-picking techniques. The main reason for this are mechanical locks that haven’t evolved much over time and can be easily picked with a little training.
It’s such a popular method that SANS Institue has a physical penetration testing course that includes lock-picking tools.
Most businesses today use electromagnetic locks to eliminate the risk of lock picking. However, scanning and duplicating ID cards used for electromagnetic locks require an equal amount of effort.
To avoid intrusions, consider using electromagnetic locks with PIN authorization access. This will provide a dual method of authentication. Something you have (a card) and something you know (a PIN).
3. Access Sensitive Information
Telephotography is the act of taking pictures of the inside of a building through windows at a great distance in order to view sensitive information on employee computers.
Even though it seems farfetched, there are many business buildings made almost entirely out of glass windows that increase the risk for this type of attack.
Simply trying to take pictures of employee’s computers from outside the office will be sufficient to test if this attack is successful against your company.
4. Test Server Rooms, Wires And Cables
Servers represent the most critical part of any network and are thus usually given a higher level of attention when it comes to security.
If an attacker gains access to your server room, your entire network is compromised.
With such access, an attacker can infect your system, completely disable it, or steal your most sensitive data.

Most businesses host their data and systems in cloud environments or own their infrastructure, which is typically stored in data centers.
Because data centers host valuable websites and company data, they often require several layers of authentication including biometric scans, identification badges, and PIN numbers to access.
In addition, servers are stored in rack cages that require a key or PIN to gain physical access to the server.
If the networking equipment is stored at the business’s location, then consider additional layers of authentication or ideally move your systems to a data center or work with a 3rd party hosting provider.
When ensuring the physical security of your servers against damage and attacks, you should focus on three main points concerning the bootability of your servers from:
- A USB drive.
- Type of RAID systems in place.
- Surveillance cameras in server rooms.
Access should also be logged and monitored to maintain awareness and hold employees accountable by letting you know who accessed what and when.
Free Penetration Testing Policy
Skip the policy-writing hassle with our ready-to-use penetration testing policy template.

5. Test Fire And Cooling Systems
Checking your fire and cooling systems is important to ensure the physical safety of your server equipment if a fire or overheating occurs inside the server room.
Without these systems, you run the risk of having your servers becoming unavailable, which is worse than being a victim of a major distributed denial of service (DDoS) attack.
Ensuring these systems run properly will allow you to stay safe in case of a physical hazard.
6. Intercept EM Waves
Electromagnetic waves are often used to transmit an organization’s data and is often vulnerable to interception.
An attacker can use wiretapping bugs to fix the wire and pick up the frequencies later on with the use of an antenna and a receiver. This can cause significant damage to the company due to the theft of sensitive information.
If an attacker intercepts the weakly encrypted traffic, they are then able to take the data offline and attempt brute force attacks to crack the passwords.
By taking the passwords offline, the attacker is able to bypass any account lockout policies.
The only effective countermeasure for this type of attack would be the use of advanced encryption algorithms to secure communications.
7. Dumpster Diving
 As the name suggests, dumpster diving involves looking through the business or its employee’s trash in search of any information that can be used to further penetrate the business’s defenses.
As the name suggests, dumpster diving involves looking through the business or its employee’s trash in search of any information that can be used to further penetrate the business’s defenses.
Paper documents, books, manuals, invoices, and bank statements are some of the things an attacker would look for in order to retrieve useful information.
It is therefore important to use paper shredders for all documents that are being discarded. In some cases, you may wish to consider burning sensitive documents as software exists to reconstruct shredded documents.
8. Break RFID Tags’ Encryption
Radio-frequency ID tags are often used to secure portable resources and are trackable through radio waves.
Often used in case of theft, RFID tags can be identified and information from them retrieved by using RFID tools.
To mitigate this attack, encryption is usually used to secure the RFID tag but can still be susceptible to an attack. If the attacker can break the encryption, the tag can be modified.
9. Gain Physical Access (Tailgating)
Tailgating is a technique used to pass through secure entrances where only authorized personnel are allowed to enter. Attackers achieve this by following the person who is passing through the entrance and entering without credentials.
With this attack, the perpetrator often uses social engineering tactics to put pressure on the employee and enter the building without much questioning. For example, who wouldn’t let a guy whose hands are full of doughnuts into the office? If you look like you belong, then you belong. From that point on, the attacker can try and gain access to restricted areas by pretending to be an authorized person.
To prevent this type of attack, businesses deploy man traps, or checkpoints inside the building, that prevent further access to unauthorized personnel.
One set of authentication may be required for the first checkpoint, like an access card, while a second authentication, like a biometric scan, may be required at the second checkpoint.
Turnstiles and security guards are also effective at deterring tailgating.
In addition, employees should be trained and prepared to ask for the credentials of anyone if they’re not clearly visible.
10. Test Network Jacks
Another important step in the physical penetration testing methodology is to check your active network jacks in meeting rooms and your company lobby.
Often overlooked, unused active network jacks can be exploited by plugging in a wireless access point.
To make sure this doesn’t happen, you should identify all active network jacks in meeting rooms, lobby areas, or any local meeting spaces and monitor them.
In most desirable cases, the network jacks will be inaccessible due to the network access controls in place that prevent the proper functioning of rogue devices in your environment.
For example, a port can be configured to only allow access with a device using a specific MAC address.
11. Check Meeting Rooms
Employees often leave sensitive documents, unlocked computers, or passwords written on notepads after meetings, presenting a serious security risk.
To mitigate this risk, businesses should establish and enforce employee policies to check for unattended electronic media and/or sensitive papers employees leave behind in meeting rooms. It’s important to also check for notes that employees leave behind that can provide attackers with an overview of some of the more important business decisions in the company.
$35/MO PER DEVICE
Enterprise Security Built For Small Business
Defy your attackers with Defiance XDR™, a fully managed security solution delivered in one affordable subscription plan.
12. Shoulder Surfing
As the name implies, this attack involves simple observation of employee’s computer to pick up on their usernames, passwords, intellectual property, sensitive data, and more.
To test this attack, penetration testers should simply observe if they can pick up on login credentials that employees type.
Attackers won’t be as obvious as to hover around your workstation. This would draw too much attention. Instead, they may pose as a handyman, delivery person, or friendly “co-worker.”
If successful, screen protection can be used to significantly decrease an observer’s ability to pick up on employee’s typing actions.
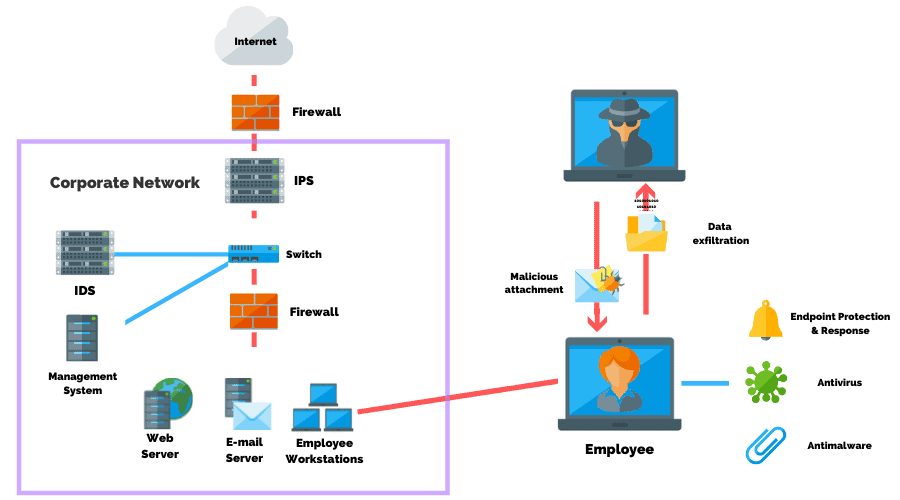
13. Social Engineer Employees
Social engineering is the practice of extracting sensitive information from employees at a given company through the use of deceptive practices which an employee is unaware of.
These attacks require strong social skills to be successful and are often very effective when executed correctly.
It’s been reported that 98% of cyber attacks rely on social engineering as an entry point into a business’s systems.
Attackers often deploy several tactics in order to succeed in social engineering their targets. One of the main tactics used is authority and urgency.
For example, an attacker may pose as a manager requesting $10,000 be wired for an emergency “expense.” At which point most employees would ask why that much money needed to be transferred immediately.
The attacker can then pressure the employee by saying they’re on a tight deadline and that the Vice President isn’t happy. They may even threaten the employee’s job if the request isn’t granted.
Attackers also often exploit a person’s natural desire to help by making the employee abandon best practices and perform a task that they are not allowed to do.
Victims are often completely unaware that they have been manipulated and the attacker manages to successfully achieve their main goal.
To test your employees, try hiring a professional social engineer to gain access to your business’s premises through the use of various techniques involving:
- Disguises.
- Fake phone calls to the reception.
- The manipulation of security guards with fake IDs.
The most effective defense against social engineering attacks is implementing security awareness training policies and training programs.
Platforms like KnowBe4 provide businesses with simulated email phishing tests. When employees fall for a simulated attack, their actions are recorded and they’re prompted to take remediation training.
Document All Findings
The final step in the physical security penetration testing methodology is documenting all findings. The security specialist who performed the penetration test writes a technical report detailing all vulnerabilities and weaknesses found in the above steps.
The report should include the findings regarding:
- The type of locks on doors and gates.
- Server room specifications
- Fire and cooling systems specification
- Valuable documents were found.
- Employee access to facilities.
- Social engineering results.
This information will then be used to create an action plan to mitigate future exposure to physical security weaknesses.
What Tools Are Used In Physical Penetration Testing?
There are several tools penetration testers use when performing physical security penetration tests.
Most of these tools are used to enhance the vision of the penetration tester, but there are also more complex tools used for lockpicking and communication interception.
The following is the most common list of tools used in physical penetration testing:
- High-Quality Cameras – A must in every physical security penetration test is a high-quality camera. A camera assists the tester by getting a better picture of the perimeter, entrances, and additional insight into the insides of the building. The reconnaissance and information-gathering phase is critical to planning a successful test.
- Binoculars – Simple but effective, penetration testers often use binoculars to gather information from afar that will later be used in social engineering efforts. Penetration testers will watch the behavior of employees and other activities to create a plan of attack.
- Night Vision Goggles – Sometimes penetration testers try to gather information during the night. This is often the case due to decreased activity around the business’s premises and the simple fact that penetration testers are less identifiable.
- Radio Device – Often more than one penetration tester is hired to breach a business’s physical security defenses. For this reason, having communication with a colleague is important for coordination and radio devices are used to achieve this goal.
- Tension Wrench – The preferred choice of most penetration testers for lockpicking is the wrench. These tools can lockpick most mechanical locks and hold any picked pins in place.
- Wireless Access Point– If the penetration tester plans to access a building then testing an unsecured network jack may be one of the primary goals. Wireless access points can be plugged into the network jacks and test whether it is functional. From there, attack vectors can be planned to gain access to the system.
- Antenna and Receiver – If the penetration tester wants to wiretap a wire in the company to intercept employee communication, an antenna would be used to intercept the EM waves and pass the current to the receiver. Once the signal is passed, the receiver can extract the desired information.
How Long Does It Take To Perform A Physical Penetration Test?
Most physical penetration tests take two to six weeks to complete from the initial discovery call to delivering the final report.
However, several factors impact the time to complete the test and report including:
- The level of effort required to break through physical barriers.
- The number of locations.
- Distance between those locations.
How Much Does A Physical Penetration Test Cost?
A physical penetration test can cost between $8,000 to $20,000 depending on the number of locations, travel between locations, the size of the facilities, and the complexity of the project scope.
Cost also varies depending on the type of penetration test being performed.
For example, what level of access or knowledge will the penetration tester have of the environment?
What specific goals or outcomes are you hoping the test will achieve?
Ultimately, physical penetration tests are unique to each business and often require a discovery call to determine the exact specifications of the project before an accurate proposal can be prepared.
While fixed-priced proposals are standard, it’s not uncommon for cybersecurity companies to bill set hours for active testing (the step where the physical test takes place), travel costs, in addition to delivering a written report and remediation plan.
Conclusion
Most businesses are happy to justify spending money or allocating resources to protect their network from cyber attacks.
However, physical security is often overlooked as an entry point for malicious actors.
By performing physical penetration testing, businesses can reveal physical security weaknesses in their environment while demonstrating how easy it could be for an attacker to gain physical access to systems.
Special attention should be given to social engineering, as this is the most used and most successful method of attack because it tests your employee’s ability to follow standard operating procedures.
Finally, documenting findings will address weaknesses that can be exploited and lay the foundation for preparing a remediation plan whether that be through adding physical security controls or implementing employee awareness training.
Article by