You may need to conduct a black box penetration test if you want to evaluate your application security, wireless security, infrastructure, network security, or physical security in a scenario closest to a real-life attack.
Free Security Policy Templates
Get a step ahead of your cybersecurity goals with our comprehensive templates.

What Is A Black Box Penetration Test?
A black box penetration test is a security test performed by an external party that is completely unfamiliar with the target. The security assessor (penetration tester) is provided with no information of the system specifics and no credentials except for the target URL.
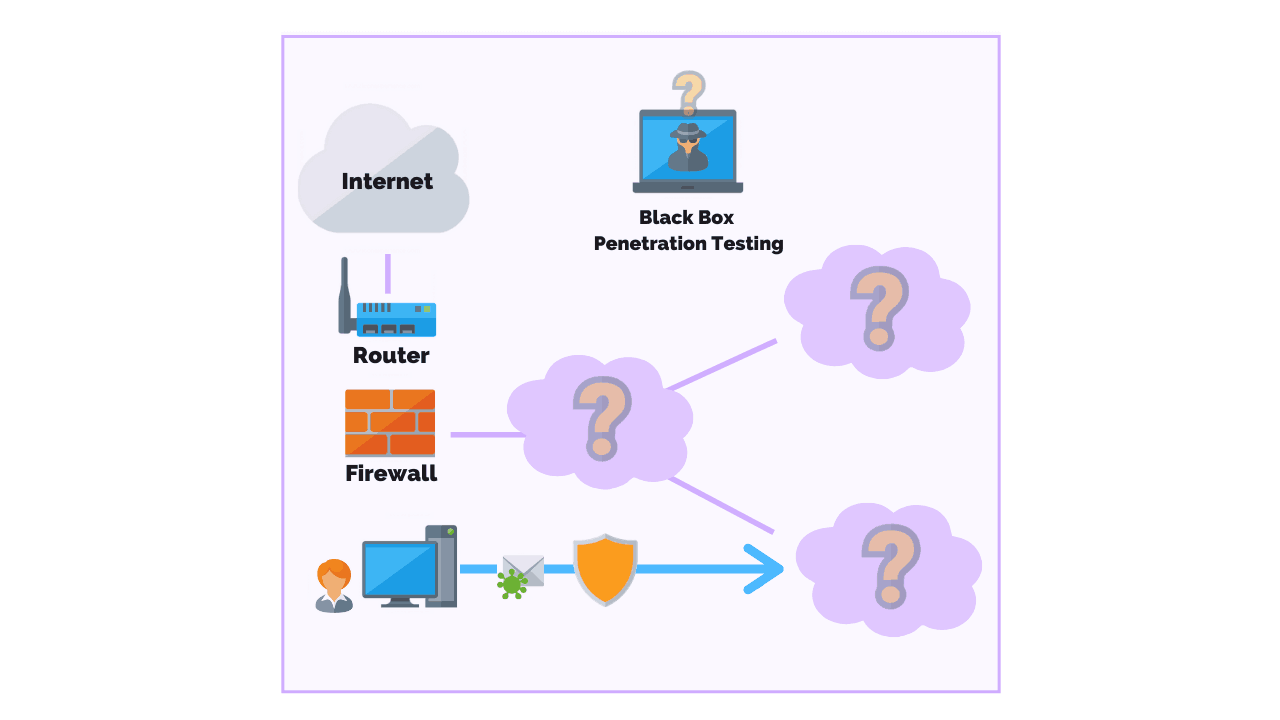
During the penetration test, the security assessor has the goal to imitate the behavior of a malicious, unprivileged user and try and perform a real attack by detecting security vulnerabilities within the application.
Related Article: External Vs Internal Penetration Testing
A black box approach is conducted to answer the question:
Can an external attacker that doesn’t have any sort of access different than what an end user should have, compromise our systems and make the application act differently than how it was designed to act?
Do I Need A Black Box Pen Test?
If you need to evaluate your application, infrastructure, or network in a scenario closest to a real-life attack then a black box approach might be a good fit.
If the scope is smaller, and you want to test just a certain component or some small changes black box might be the right approach. The upside is that this type of pen test can be very cost-effective.
However, the results are not likely to be as actionable as a white box penetration test.
This is because a true black box engagement is not often sufficiently funded. In addition, assessors are given little time, sometimes only a few weeks, to complete months’ worth of work.
Advantages Of Black Box Testing
The advantage of the black box approach is that this technique mirrors a real-life attack providing information on:
- What vulnerabilities can be exploited?
- What is the potential business impact?
The main benefit is that the penetration tester approaches and attacks the application with the same amount of knowledge as an external hacker would also have when it decides to attack the application.
Disadvantages Of Black Box Testing
However, some disadvantages should be taken into consideration.
A white-box penetration test or a gray-box penetration test provides a more comprehensive review of the source code and internal processes.
However, a black box approach does not include internal testing making it more difficult for the penetration tester to find any vulnerabilities.
This may result in giving a false image that the system in question is secure and follows solid security standards.
But, that might not be the full picture and a lot of vulnerabilities might exist beneath the surface.
The main issue is that when an external attacker decides to put an application in its scope, attack it, and attempt to find anything that might compromise it, the attacker can dedicate months or maybe more time to discovering security holes.
Many engagements today do not provide the time and budget required for a penetration tester to conduct such a thorough test.
The test is usually defined within a certain timeframe that the penetration tester has to follow and it would have a clearly defined start date and end date, which generally is no longer than two weeks.
Steps To Performing A Black Box Penetration Test
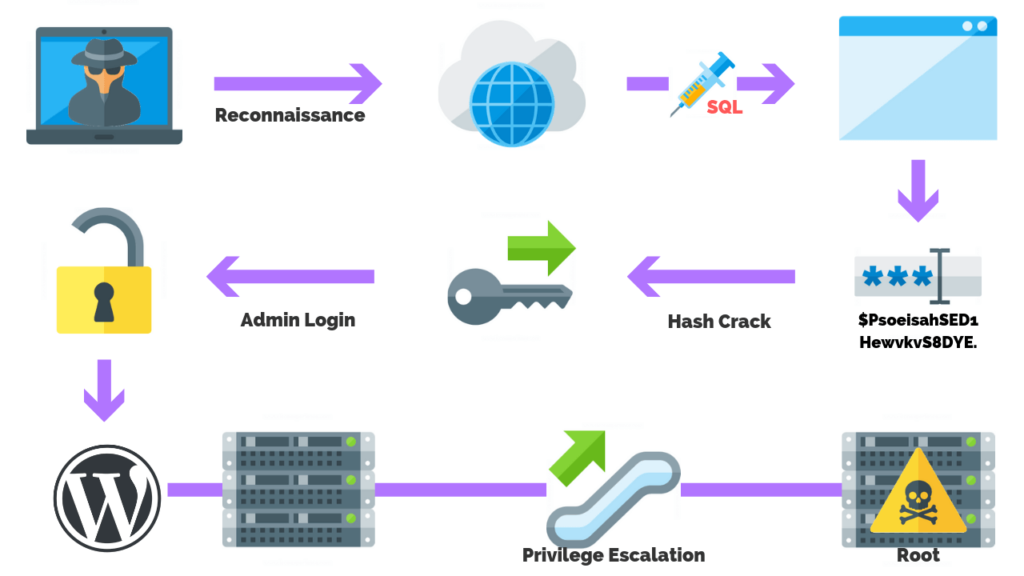
The steps of performing a black box pen test include:
- Reconnaissance
- Scanning & Enumeration
- Vulnerability Discovery
- Exploitation
- Privilege Escalation
Reconnaissance
Reconnaissance is the process of gathering information about the target system.
Usually, this is publicly known information that can be found by googling and inspecting the social media of the company and its website(s).
The kind of information that may be gathered are IP addresses, employee information, websites, email addresses, and so on.
Scanning & Enumeration
 In this stage of the penetration test, more information is gathered through different techniques.
In this stage of the penetration test, more information is gathered through different techniques.
The penetration tester looks for more information by scanning the target’s IP address utilizing tools like Nmap.
The scan would usually produce information like the version of the operating system, and the type of running software and check for vulnerable versions of software that is running.
Through enumeration, usually user roles, and user accounts are expected to be gathered.
Vulnerability Discovery
![]() Having in mind the information gathered so far through the different techniques, the penetration tester should now look for publicly known vulnerabilities and attack entry vectors that would be a possible way into the target.
Having in mind the information gathered so far through the different techniques, the penetration tester should now look for publicly known vulnerabilities and attack entry vectors that would be a possible way into the target.
This may include but is not limited to known CVEs in the system, vulnerable versions, or third-party applications used by the target.
Exploitation
In this phase of the penetration testing engagement, the penetration tester already noted several possible exploitable vulnerabilities gathered through automated scanning and manual research.
Now different methods are used to exploit the found security vulnerabilities.
Each one requires different knowledge and most likely different tools that the penetration tester would use to penetrate the system and obtain initial access or gather sensitive information from the system that is being exploited.
Privilege Escalation
The final phase of the exploitation is conducted if the penetration tester successfully enters the system and can gain initial access.
Privilege escalation means that now the penetration tester tries to escalate the privileges to a higher system role.
For example, an admin, and tries to access systems that the admin has access to, like database access or Active Directory access.
Examples Of Black Box Techniques
Some common black box techniques during a penetration testing engagement could be the following:
- Open Intelligence Information Gathering
- Vulnerability Scanning
- Full Port Scanning
- Exploratory Testing
- Fuzzing
- Password Attacks
Related Article: Types Of Penetration Tests Explained
Open Intelligence Information Gathering
This technique gives the penetration tester the possibility to create a better map of the target that they are working on.
The assessor uses public resources to collect as much information as possible about the application or network system that is being tested – resulting in insights into the system they are against.
Vulnerability Scanning
Vulnerability scanning usually means running the target’s IP address against a vulnerability scanner.
The scanner runs the application through a database of vulnerabilities and checks whether the application in question is vulnerable to any of those vulnerabilities.
Many findings from the vulnerability scanners do turn out to be false positives meaning the penetration tester has to do a manual confirmation.
The findings from vulnerability scanners usually give initial information on something that should be looked into further.
Full Port Scanning
A full port scan of the target is usually part of the penetration tester methodology.
This is because identifying open ports might expose and lead to information that could lead to different vulnerabilities or exploitation vectors.
The scan covers 1000 of the most popular UDP ports and the entire 65,535 TCP ports.
Exploratory Testing
Exploratory testing is when you perform a test without any plan in advance and without an expectation or specific outcome.
It is usually just playing around with the target and allowing different outcomes, results or vulnerabilities, and security issues that appear from one test to be a guide for another one.
This type of exploratory testing is especially useful in black box penetration testing where one big find might be the ground for the whole penetration test.
Fuzzing
Fuzzing sometimes referred to as fuzz tests is a process of automatically testing applications, specifically input fields for missing input checks.
The fuzzer provides a lot of invalid or random inputs in the program that the application might not expect or is not designed to handle.
The test usually tries to detect crashes, errors, memory leaks, and different behavior than expected.
Password Attacks
Password attacks test the target for password vulnerabilities since brute-force attacks on login forms are a very common attack vector amongst malicious attackers.
Usually, automated tools are used and a dictionary of common passwords is created to guess and gain access to a system.
There are different forms of password attacks, some faster, some particularly slower methods, however, all with a common goal to detect an account with a weak password and use that as an entry vector into the system.
Of course, there are many other types of techniques and attacks used, but these are usually a standard in a black box penetration testing engagement.
Article by