How To Perform A Successful Network Penetration Test
Test & Validate Your Security Posture
Our penetration testing services deliver immediate ROI with an agile and efficient solution testing resilience against the latest attacks and APT techniques.
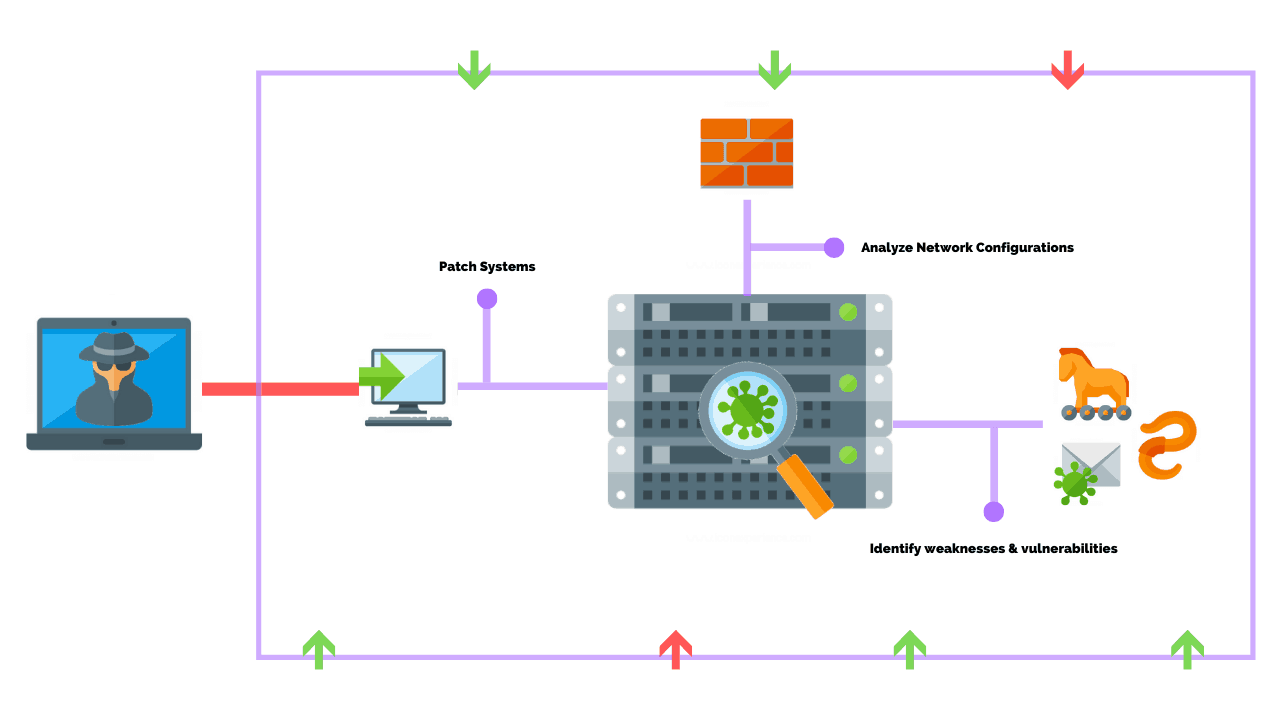
You just completed a vulnerability assessment and you’ve remedied all or most of the identified vulnerabilities. A network penetration test is often the next step to validate the risk assessment with the goal of enhancing a business’s security posture.
There are four main steps to performing a network penetration test which include 1) information gathering and clarifying client expectations, 2) reconnaissance and discovery, 3) performing the penetration test, and 4) reporting on recommendations and remediation.
By the end of this article, you will understand what a network penetration test is and the benefits associated with it. In addition, you will learn how to successfully perform a network penetration test and explain it to future clients or key stakeholders.
Article Navigation
- What Is A Network Penetration Test?
- What Are The Benefits Of Performing A Network Penetration Test?
- What Are The Steps In The Network Penetration Testing Process?
Types Of Penetration Tests |
||
|---|---|---|
 |
 |
 |
Wireless |
External VS Internal |
Social Engineering |
 |
 |
 |
Physical |
Firewall |
Web Application |
What Is A Network Penetration Test?
A network penetration test is the process of identifying security vulnerabilities in applications and systems by intentionally using various malicious techniques to evaluate the network’s security, or lack of, responses.
Similar to vulnerability assessments, a network penetration test, also known as a pen test, aims to identify vulnerabilities in a network.
However, unlike a vulnerability assessment, a penetration test is an exact simulation of a potential attack to identify vulnerabilities that are harder to find in a network.
What Are The Benefits Of Performing A Network Penetration Test?
There are numerous benefits to performing network penetration tests on your systems including:
- Understanding the network baseline
- Testing your security posture and controls
- Preventing network and data breaches
- Ensuring network and system security
Acting as an in-depth test of the network, the network penetration test will allow businesses to better understand their network baseline, to test their network and system security controls, prevent attacks and breaches, and ensure network security in the future.
A network penetration test is typically performed when a business has a mature security posture, or they believe they have strong security measures in place.
Understand The Network Baseline
Most of the time, the network’s baseline is identified through the use of scanning tools like port scanners, network scanners, and vulnerability scanners. Understanding a network’s baseline allows the business owner to understand what security controls are working, identify existing vulnerabilities, and provide them additional information about their network.
Test Your Security Posture And Controls
Unlike a vulnerability assessment, a network penetration test will put your security controls to the ultimate test. A network penetration test’s goal is to breach your network and exploit those vulnerabilities to understand the areas that need improvement.
Prevent Network And Data Breaches
When a successful penetration test is performed, the results assist a business owner in designing or adjusting their risk analysis and mitigation strategies.
This helps the business prevent future breaches because the network penetration test simulates a real-world attacker attempting to break into your systems.
Ensure Network And System Security
A network penetration test helps to ensure system security in a variety of ways.
For example, a business may have a mature security strategy with strong external defenses but their internal defenses, such as a host-based Intrusion Prevention System (IDS) that prevent attacks from trusted hosts on the network, have been neglected.
Now, we have an idea about what a network penetration test is and the benefits that it has for businesses – let’s go through the process of performing a successful network penetration test.
What Are The Steps In The Network Penetration Testing Process?
Network penetration testing and vulnerability assessments are often used interchangeably.
However, there are some notable differences, most security practitioners view network penetration testing as a step that follows your vulnerability assessment.
Particularly, after the vulnerabilities identified in the vulnerability assessment have been remedied and the business owner would like to further test the security of their network.
To perform a successful penetration test, there are 4 steps that must be completed:
Step 1: Information Gathering And Client Expectations
When you are discussing the goals of the network penetration test, there are a few important things to consider.
Penetration tests fall into three main categories:
- Black box testing
- Gray box testing
- White box testing
Black Box Testing
A network penetration test that is performed from the position of an average hacker, with minimal internal knowledge of the system or the network, is known as black box testing.
This type of test is typically the quickest as it employs tools to identify and exploit vulnerabilities in the outward-facing network.
It is important to note that if the perimeter cannot be breached in this type of penetration test, any internal vulnerabilities will remain undiscovered.
Gray Box Testing
A network penetration test that is performed from the position of a user, that has access to the system, potentially including elevated privileges, is known as gray box testing.
This type of test aims to provide a more focused assessment of the network’s security, with insights into the external and internal vulnerabilities.
White Box Testing
A network penetration test that is performed from the position of an IT or IS user, that has access to the source code and architecture documentation, is known as white box testing.
This type of penetration test typically takes the longest, with the most challenging aspects being the large amounts of data that must be scrutinized to identify vulnerabilities.
It is important to know the types of network penetration tests that can be performed, whether you are a penetration tester or a business owner because they all provide specific benefits to the businesses.
Understanding Client Expectations
On top of deciding on the type of penetration test for your network, you must also discuss and set a date and time for the penetration test to occur, whether the test will be performed on a production or staging/testing environment, and if the client wishes for vulnerabilities to be exploited or simply identified and reported on.
It may seem inconsequential, however, if there are security measures currently in place on a network, it could shut down mission-critical systems on a network.
Finally, a network penetration test could be performed in a “live” setting, which would be during normal business operation hours, or performed after normal operating hours, which may occur during the night or over the weekend, depending on the business’s schedule.
At this stage, you should have documentation that records the information that will be used during the penetration test.
Step 2: Reconnaissance And Discovery
Now, it is time for you to put your penetration tester hat on.
After you have discussed the goal of the network penetration test, including the information that will be used during the test and the time and date in which it will occur, the reconnaissance and discovery step begins.
Reconnaissance
During your reconnaissance, you will begin by employing port and network scanners on the network and systems to get a view of the network, the devices on the network, and existing vulnerabilities.
Your goal will be to see where the vulnerabilities are located in order to begin your exploitation of those vulnerabilities.
Social engineering, the use of deception to manipulate individuals into divulging confidential or personal information that may be used for fraudulent purposes, could be used as a tactic to identify vulnerabilities in the network that will allow you to gain access more easily.
Discovery
Discovery is when you find the information that you were seeking during reconnaissance. By aggregating the information found a path can be identified to breach the network.
Now, let’s put this step into action.
During a gray box penetration test on a client’s network, tools like a port scanner, a tool that identifies open ports on a system, and a vulnerability scanner, a tool that identifies vulnerabilities on a system, are used to begin to identify ways to gain access to the network.
Step 3: Performing The Network Penetration Test
During step 3, the pen tester will perform the network penetration test based on the vulnerabilities that you identified in step 2.
This step often uses tools that include exploit scripts or custom scripts you may code yourself.
In many cases, the pen tester will choose the vulnerability they deem the easiest or most critical to exploit and begin the process of exploiting it.
However, this approach is not foolproof, requiring multiple vulnerabilities to be tested to successfully gain access to the network.
This information is important when relaying the results to the client as it will be beneficial for them to know the strong and weak points in their network security.
Take a look at the example below on how a successful penetration test could be performed.
Technical Approach
During reconnaissance and discovery, a pen tester runs a port scanner and vulnerability scanner tools on the network.
You saw that there was a client system that has an open port on Port 80, which is unusual for that system as it typically doesn’t need to connect to the internet, which is on Port 80.
You deduce that this system may not have the proper defenses for an attack that originates from Port 80. You run an SQL Injection or Buffer Overflow attack to attempt to gain access to that system.
You then use the pivot method, using the compromised system to attack other systems on the network, and a Brute Force attack, as you believe that the internal security defenses are not prepared for an attack from a trusted host on the network.
Human Approach
During your reconnaissance and discovery, your scanning tools revealed that there no technical vulnerabilities existing in the systems.
However, you noticed that social engineering and the use of phishing attacks may be the best approach in this penetration test as you easily identified key employees and their contact information in the company through the social media search.
You then craft a phishing email that looks like a company email from Human Resources, asking them to download the file and fill out for HR purposes, and embed Key Logger or Rootkit malware in the attachment.
You then send it to the key employees in the Accounting Department that you identified on social media and wait for them to take the bait.
Once you are notified that an Accounting employee downloaded the malware, you are able to breach the network and gather sensitive financial information and possibly escalate account privileges to gain administrator-level access.
When you have successfully gained access to the sensitive data or critical systems that you were targeting, you have successfully breached the network.
If you are unable to gain unauthorized access to the target systems, your network penetration test is not necessarily unsuccessful. Knowing the strengths and weaknesses of a network is just as important to the client, and if this were the case, you could recommend a more in-depth test, like a white box test, in the future.
It is important to remember that to perform a complete network penetration test for a client, you will need to provide them the results and recommendations from your test.
Step 4: Reporting, Recommendations, And Remediation
Following a penetration test, a report is written specific to the type of network penetration test performed for the client, that details the process, the vulnerabilities and evidence collected, and recommendations for remediation.
It is vital to a data owner to understand the risk to their business that the vulnerabilities pose, and it is the job of the pen tester to provide them with a risk analysis that assists them in making the appropriate decision.
Remediation may include implementing patches and updates.
However, it can also include the implementation of specific policies like Employee Use policies and IT Security policies if internal vulnerabilities.
Remember, a successful network penetration test is not just one in which a successful breach occurs. If the tester is unable to breach the network, then it validates that the existing security posture of the organization is sufficient in deterring, detecting, or preventing attacks.
Conclusion
Network penetration testing is a crucial part to a business’s security plan. In this article, you learned how to perform a successful penetration test and provide the results to your client.
Network penetration tests are important to enhance a business’s cyber security posture and it is your job to identify their vulnerabilities before the real attackers do.
Are you ready to work together? Get a no-obligation consultation to meet your penetration testing needs.
Related Articles
- How To Perform A Successful Network Vulnerability Assessment
- What Is A Red Team VS A Blue Team In Cyber Security?
- 13 Physical Penetration Testing Methods (That Actually Work)
- What Are The Most Common Types Of Network Vulnerabilities?
- Vulnerability Scans VS Penetration Tests: What’s The Main Difference?


Laurie Kusmaul
Great information! I cited this article for a paper in my Network Security course. Thank you! Just wanted to point out one thing. In this web article you state “host-based Intrusion Detection System (IDS) that prevent attacks from trusted hosts on the network…” I was under the impression that an IDS does not prevent attacks, that only an IPS can do that. Do you agree?
Jason Firch, MBA
Hi Laurie! Thank you for your comment. I’m thrilled to hear you found value in this article and thank you for pointing out this mistake. You’re 100% correct it should have been an IPS not an IDS. We’ve updated the article accordingly.