A firewall is one of the first lines of defense in preventing cyber attacks.
Naturally, this presents an opportunity for penetration testers and threat actors alike, to attempt exploits that would compromise a network’s security.
There are 13 steps to firewall penetration testing, which include:
- Locating the firewall
- Conducting tracerroute
- Scanning ports
- Nanner grabbing
- Access control enumeration
- Identifying the firewall architecture
- Testing the firewall policy
- Firewalking
- Port redirection
- Internal and external testing
- Testing for covert channels
- HTTP tunneling
- Identifying firewall specific vulnerabilities.
In this article, I’m going to share my methodology for performing a comprehensive firewall penetration test.
By the end, you’ll have a better understanding of how to holistically protect your business from cyber attacks.
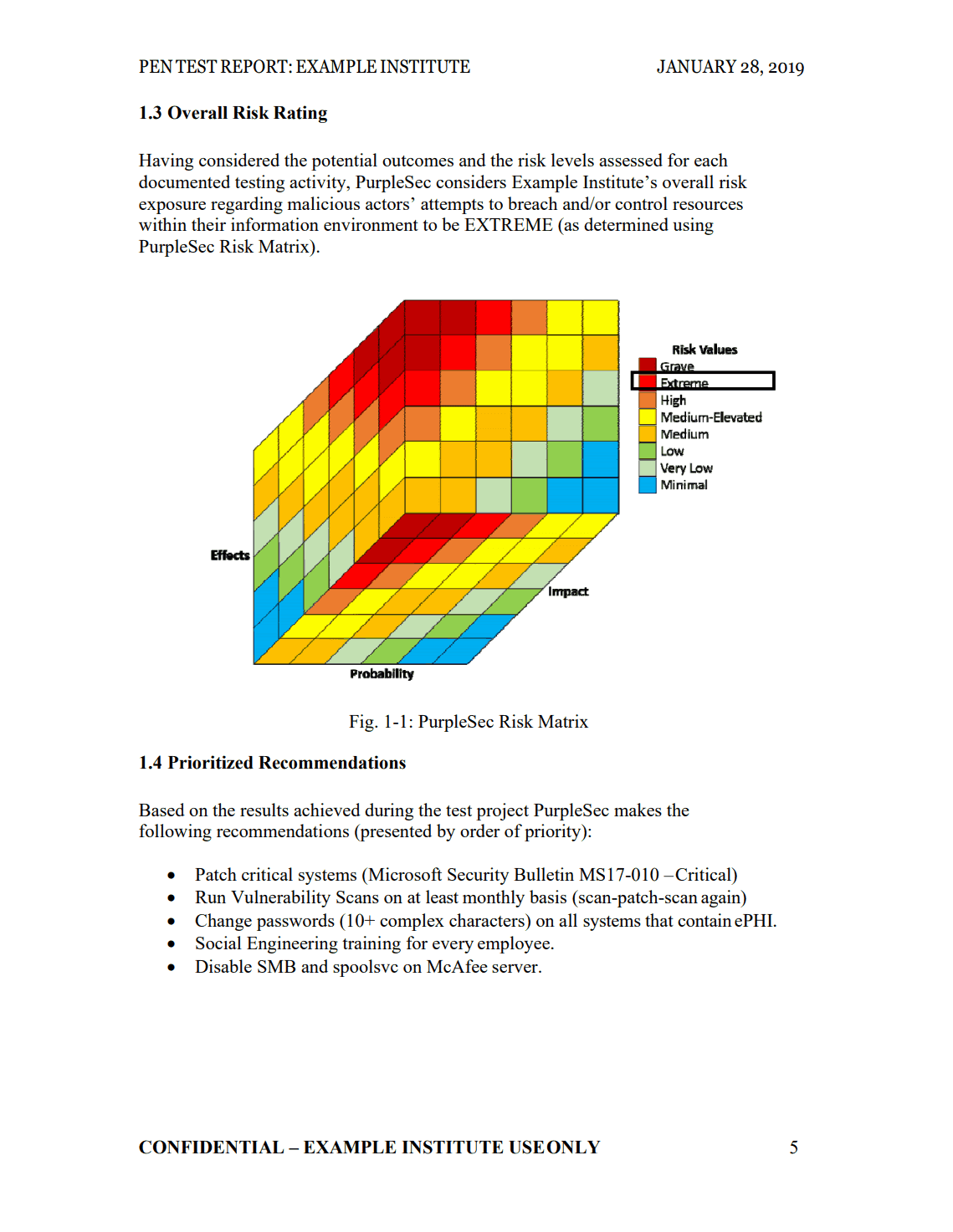
Sample Network Pen Test Report
What should a penetration test report include? Download our sample report to learn.
What Is A Firewall?
A firewall is a software or hardware device that inspects incoming and outgoing traffic on a network.
Based on a predetermined set of policies and rules, or an access control list (ACL), the firewall filters and restricts all connections that do not abide by those rules.
The main purpose of a firewall is to separate trusted networks from the external network or the internet.
In order to accomplish this, a firewall is typically placed in the DMZ (demilitarized zone). Additional firewalls may be placed in front of a business’s internal network, or intranet.
Or, in front of supervisory control and data acquisition (SCADA), which support systems that run industrial organizations such as nuclear power plants.
What Are Next Generation Firewalls?
There are many types of firewalls and each model has different functionalities.
The main progress that was made with regards to firewall capabilities is the introduction of Next Generation Firewalls (NGFW).
Traditional firewalls couldn’t engage in stateful packet inspection but were rather only analyzing network traffic based on the IP address and port number of the packets without taking into consideration previous traffic that passed through the firewall.
With the introduction of NGFW, dynamic packet filtering was a reality and enabled all active connections to be monitored along with the state of the connections.
This additional information is used to aid in the process of determining access.
Firewall Policies
When deploying any firewall, a certain set of policies and rules need to be configured in order to adequately ensure the security of the network perimeter.
Policies and rules allow for certain type of network traffic to be blocked or allowed.
These policies can also be applied later on different firewalls throughout the network.
Additionally, the integration of active directory, role-based access control could be enforced, encompassing each user role and its permissions in the firewall.
Steps To Performing A Firewall Penetration Test
Firewall penetration testing is the process of locating, investigating, and penetrating a certain firewall to reach the internal trusted network of a certain system.
Mostly considered to be a key part in external network penetration testing, firewall testing is one of the most important types of network tests that can be conducted as firewalls represent the first line of defense against outside intrusions.
Below you will find steps that a comprehensive firewall test should include in the penetration testing methodology.
Step 1: Locating The Firewall
Every firewall penetration test will begin with locating the firewall.
Using any packet crafting software, the tester crafts specific IP packets containing UDP, TCP or ICMP payloads.
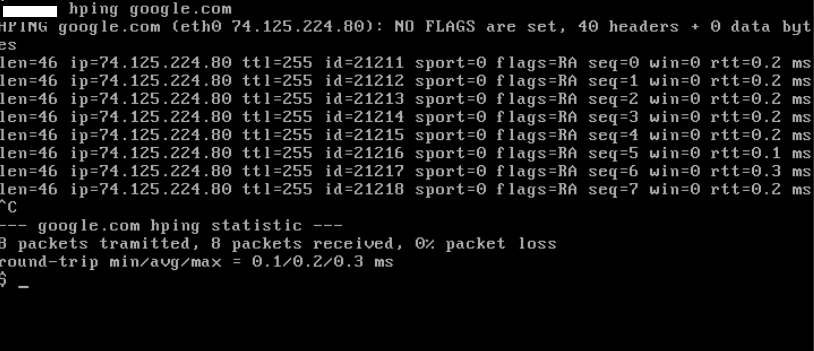
Common firewall pen-testing tools used are Hping and Nmap. Both tools have similar functionality with one small difference. Hping can only scan 1 IP address at a time compared to Nmap, which can scan a range of IP addresses.
Depending on the level of aggressiveness of the scan one wishes to perform, Hping is a better choice to avoid any abnormal activity from being detected.
By repeating the scanning process, one can map the list of allowed services in the firewall.
Step 2: Conducting Traceroute
Network range can be identified by running a tracert command against the firewall located in the previous step.
This step will also provide information regarding the route packets take between systems and determine all routers and devices that are involved in the connection-establishing process.
Additionally, certain information about devices that filter traffic and protocols used can also be obtained.
Free Penetration Testing Policy
Skip the policy-writing hassle with our ready-to-use penetration testing policy template.

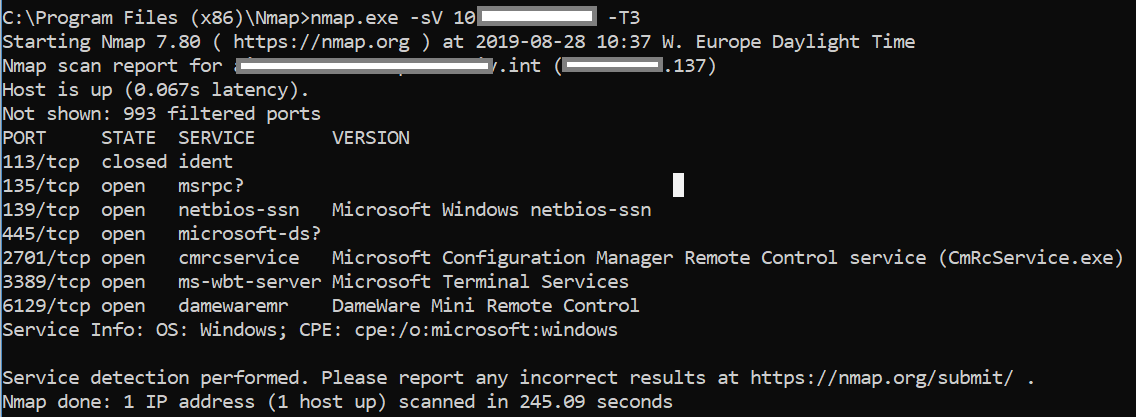
Step 3: Port Scanning
The third step in the firewall penetration testing methodology is port scanning.
The most commonly used tool is Nmap due to the possibility of its wide customization of scans one wishes to perform.
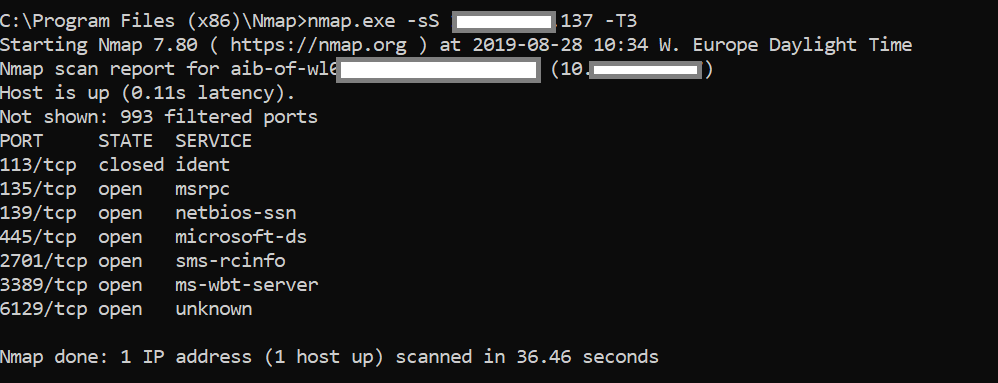
In this step, not only will you identify open ports on the firewall, but also you’ll also identify the corresponding services that are running on those open ports.
Using Nmap, one can craft a scan that encompasses the type of scan wanted, options for that specific scan type, the timing of the scan and much more.
For example, Nmap -sS -p 0-1024 x.x.x.x -T4 will send packets with a SYN flag raised, to the first 1024 ports using aggressive timing.
Depending on the preferences and requirements of the penetration tester, Nmap can export the results of the scan in different formats.
After mapping all necessary ports and determining the ones that are in an open state, the penetration testers can run another Nmap scan on the open ports to determine which services are running.
Running the following Nmap scan will provide that information:
Nmap -sV x.x.x.x -T1.
After crafting and running different Nmap scans, the penetration tester will have a basic overview of the firewall, open ports, and services running on those ports.
Step 4: Banner Grabbing
Performing banner grabbing on the firewall will provide information on the version of the firewall in question.
This information can later be used to find available exploits that can potentially compromise the firewall.
Using Netcat, the penetration tester will craft a connection request which will provide the tester with the right information.
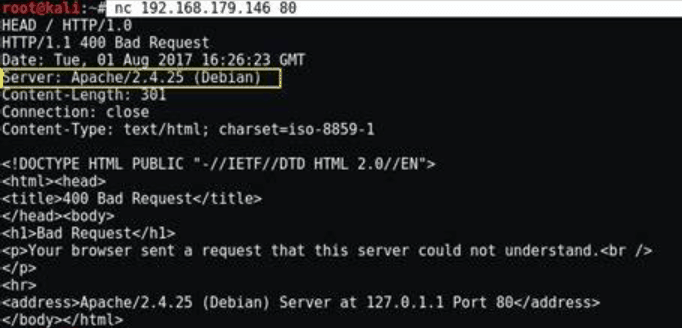
For example, let’s say that we identified port 80 on the firewall as open.
The following Netcat command will retrieve the firewall banner and hopefully expose the webserver version:
nc-nvv 10.0.0.1 80.
One of the most important steps in testing any firewall is crafting and scanning the firewall using custom made packets.
The purpose of this is to elicit different firewall responses and determine which type of firewall you are trying to bypass.
Using Hping or Nmap, a penetration tester should try many different variations of the scan in order to gather as much information as possible.
Each scan should use different flags (SYN, ACK, FIN etc.) and different protocols (TCP, UDP) in order to attempt connection establishment.
Additionally, testing different protocols with different connection attributes will elicit the most useful responses from the firewall.
Step 5: Access Control Enumeration
Every firewall employs access control lists in order to determine which traffic to allow or deny from the internal network.
The only indicator a penetration tester can observe while enumerating the access control list is the state of ports on the firewall.
Nmap can also be used to accomplish this step with the following command; Nmap -sA x.x.x.x.
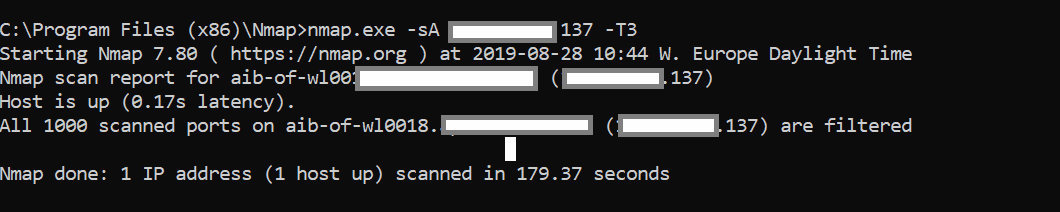
Nmap will send packets to the first 1024 ports with the ACK flag raised.
This will return results indicating if the port is open, filtered or unfiltered.
If the port is in an “Open” state, it is in listening mode. If the state of the port Is “filtered”, it indicates the port is blocked by the firewall.
Finally, if the port is “unfiltered”, the firewall is passing traffic through the port, but the port is not open.
Step 6: Identifying Firewall Architecture
To build on the previous step, sending crafted packets to firewall ports that were already identified will provide a penetration tester with a complete list of port status.
By eliciting responses from the firewall on specific ports, the tester will be able to determine the firewall reaction and aid in mapping open ports.
Additionally, responses from the firewall will let the tester know if the connection was rejected, dropped, or blocked.
Like in the previous steps, Hping, Hping2 or Nmap can be used to accomplish this task.
After initiating the scan, the firewall will send back specific packets indicating the action it took against the scan.
If the firewall returns a SYN/ACK packet, the port is in an “Open” state.
If the firewall returns a RST/ACK packet, it means the firewall rejected the crafted packet from the tester’s scanner.
If no response is received, the firewall drops the crafted packet indicating a filtered port.
Finally, if the firewall returns an ICMP type 3 code 13 packet, the connection attempt is simply blocked.
$35/MO PER DEVICE
Enterprise Security Built For Small Business
Defy your attackers with Defiance XDR™, a fully managed security solution delivered in one affordable subscription plan.
Step 7: Testing The Firewall Policy
Considered to sometimes be a part of the internal network penetration test, testing firewall policies can be done in two ways.
- The penetration tester will compare hard copies of the extracted firewall policy configuration and the expected configuration to identify potential gaps,
- The tester will perform actions on the firewall to confirm the expected configuration.
Step 8: Firewalking
Firewalking is a method of mapping the network devices that sit behind the firewall.
The Firewalk network auditing tool analyzes packets returned by the firewall with the use of traceroute techniques.
It will determine open ports on the firewall by checking devices behind the firewall and thus identify which traffic is able to pass the firewall.
The Firewalk tool is considered to perform advanced network mapping and is able to paint a picture of the network topology.
More specifically, by crafting packets with certain TTL values, the penetration tester can identify open ports if the return message is received with the exceeded TTL.
If no response is received, it can be concluded that the firewall filtered the packet and blocked the connection.
Step 9: Port Redirection
Testing for port redirection is an important step that can allow further compromise of a given network.
If a desired port is not accessible directly, port redirection techniques can be used to circumvent the denial of access.
If the tester manages to compromise a target system and wants to bypass the firewall, he or she can install a port redirecting tools such as Fpipe or Datapipe and listen to certain port numbers.
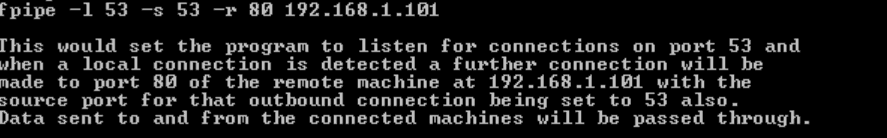
Once the traffic to the ports is sniffed, it can be redirected to the compromised machine.
Step 10: External And Internal Testing
Performing external and internal penetration tests is not always required when testing the firewall, however, it does provide a more realistic approach to how a malicious actor may attack your systems.
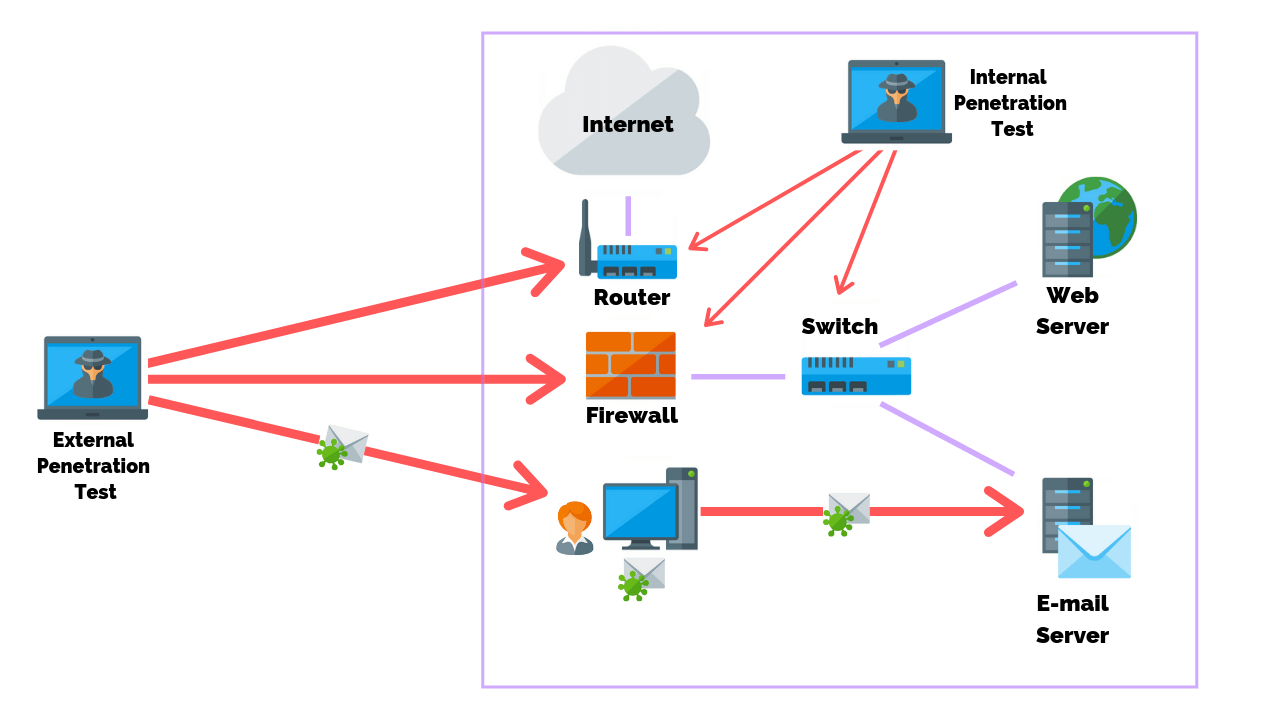
An external penetration test researches and attempts to exploit vulnerabilities that could be performed by an external user without proper access and permissions.
An internal penetration test is similar to a vulnerability assessment, however, it takes a scan one step further by attempting to exploit the vulnerabilities and determine what information is actually exposed.
In order to cover both sides, the tester will send packets from outside of the network and analyze the received packets inside the network.
Step 11: Test For Covert Channels
A covert channel is a hidden communication connection that allows hackers to remain stealthy.
Mostly used for concealing activities and extracting valuable or sensitive data from a company, covert channels are created by installing a backdoor on a compromised machine inside the network.
Once installed, a reverse shell can be created to establish a connection with the outside machine belonging to the hacker.
One way of doing this is with the use of the popular hacking platform Metasploit.
To test whether establishing a covert channel is doable, the penetration tester will:
- Identify firewall rules with the help of Firewalk.
- Attempt to reach systems behind the firewall.
- Examine the response of the arriving packets.
Step 12: HTTP Tunneling
HTTP tunneling method consists of encapsulating traffic with HTTP protocol and is often used when there is restricted access to a device that sits behind a firewall or a proxy.
In this scenario, HTTPort tool can be used to send POST requests to the HTTP server by specifying the hostname, port number, and path.
As the nature of HTTPort’s functionality can bypass HTTP proxies, the only obstacle left is the enabled connect methods on the proxy itself.
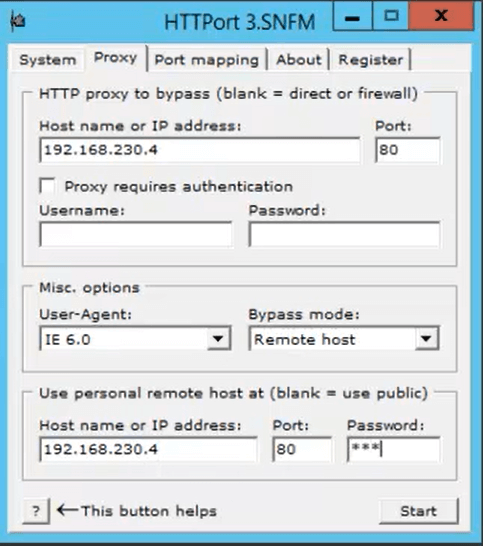
If the CONNECT HTTP method is enabled, creating a HTTP tunnel is easy.
However, if the CONNECT method is disabled, a remote host mode must be used but requires a significant amount of effort to accomplish.
Step 13: Identify Firewall Specific Vulnerabilities
If you were wondering how to ensure there are no vulnerabilities in your firewall, the answer is making sure no misconfigurations are present.
As this is the main reason hackers manage to penetrate the network, configuring your firewall properly is the most important step you can take.
In some cases, printing or file-sharing services are left enabled on certain open ports and allow hackers to bypass the firewall through that vector.
Disabling services that are not needed and checking firewall configuration is the only way to ensure safety.
Documenting Penetration Testing Findings
Like with any other type of penetration test, firewall testing also needs to be documented.
It is important to include all the findings from the test, especially the methods of attack that worked on the target firewall.
In addition, focusing on the methods that worked and on the misconfigurations that were potentially found, the penetration tester will narrow down the focus on the most important findings.
Firewall Penetration Testing Tools
Most important tools needed for firewall penetration testing are scanners including:
- Nmap
- Hping
- Hping2
- Netcat
- Firewalk Network Auditing tool
These scanners allow the tester to customize packets and elicit a response from the firewall.
By interpreting the responses from the firewall, the tester can determine state of ports, services running and their version, perform banner grabbing and find vulnerabilities.
Finally, Fpipeand Datapipe tools can be used when attempting port redirection and HTTPort tool can be used when attempting HTTP tunneling.
Conclusion
The main purpose of performing firewall penetration testing is to prevent unauthorized access to the internal network from the internet.
Depending on the type of firewall, most represent a traditional stateless firewall or a next-generation firewall, which remembers the state of all connections.
The success of any firewall penetration test depends on multiple factors.
Making sure firewall policies and rules are configured properly will greatly reduce the attack success and prevent most unauthorized connection attempts.
Using security scanners such as Nmap, Hping and Netcat to enumerate and fingerprint the firewall will provide various information about the firewall, its access control lists and the state of its ports.
Most decisions and actions a penetration tester will take will depend on these firewall responses.
Last but not least, documenting everything is just as important as the test itself.
Make sure to include all relevant findings and tools as you work through the process, instead of waiting to the end of the test.
This will save a lot of time, headaches, and confusion once you’re ready to deliver the report.
Article by