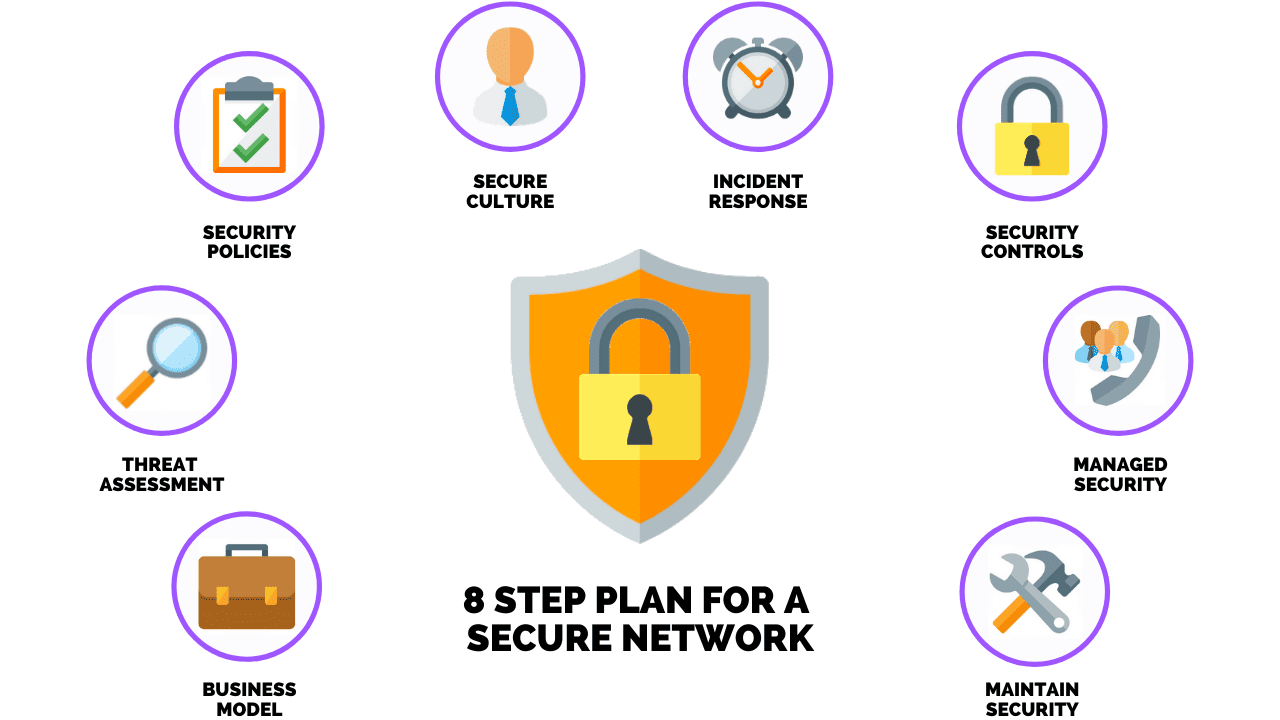
How To Develop & Implement A Network Security Plan
Protecting your business and its data from today’s threats and adversaries is a challenging endeavor requiring expertise and professionally managed resources.
You also need a strategic security plan that outlines how to protect your network from cyber attacks.
The end users in your organization require guidance on the appropriate use of email, mobile devices, the internet, and other aspects of your company’s network.
This plan should support the business model and not be too restrictive, but somewhat painless for your employees to adopt and follow.
In this article, I am going to provide direction on how you can develop and implement a successful network security plan for your organization from start to finish.
In each of the steps, I will explain the purpose and explain how the step can be implemented.
By the end of this article, you will have knowledge of the core components required to establish your own security plan along with the resources and expertise required to maintain the plan.
Article Navigation
- What Is A Network Security Plan?
- Why Is A Network Security Plan Is Important?
- Planning for A Secure Network
- Step 1: Understand your Business Model
- Step 2: Perform A Threat Assessment
- Step 3: Develop IT Security Policies & Procedures
- Step 4: Create A “Security-First” Company Culture
- Step 5: Define Incident Response
- Step 6: Implement Security Controls
- Step 7: Hire A Managed Security Company
- Step 8: Maintain Security for The Future
What Is A Network Security Plan?
A network security plan is a strategy that defines the approach and techniques used to protect the network from unauthorized users and guards against events that can jeopardize or compromise a system’s security.
The approach and techniques used by an organization may consist of creating security policies and procedures which describe how an organization intends to meet the security requirements for its systems.
The security plan is a living document, that is, it requires reviews or maintenance at specified intervals to ensure it is current and up to date with regulatory requirements or major changes in the topology of the network.
The governance and maintenance of the network security plan varies from one organization to the next. Many medium to large companies may have a CISO or ISO, Security Manager, Security Director, or Manager of Compliance/Risk. An SMB may have one individual wearing multiple hats at the managerial level.
Regardless of your organization’s Information Technology hierarchy, the oversight of the security plan should be managed by members of the organization who can effectively communicate the policy content to the end users.
Why Is A Network Security Plan Is Important?
Due to the growing threat of hackers continuously probing the Internet for networks to exploit, a Network Security Plan is important to protect the infrastructure from unauthorized access, misuse, destruction, or loss of corporate reputation.
If an organization views a Network Security Plan as a mere checkoff to satisfy a compliance audit requirement, this is a recipe for disaster. This short-sighted approach may lead to long term issue.
For example, a successful phishing attack may install ransomware on an outdated computer on the network. Minutes later, it moves laterally to other machines on the network and onto the email systems.
In a short period of time, the network is crippled, and the business must decide to pay the ransom or figure out methods to stop the attack by hiring an expensive security consulting firm. A well designed and strategic Network Security Plan will have controls in place to proactively prevent attacks and save the organization from this negative experience.
Read more: How To Prevent Ransomware Attacks: An Expert Guide
Planning For A Secure Network
Securing a network requires a complex combination of hardware devices, such as routers, firewalls, intrusion detection/prevention systems, and endpoint software security applications. Deciding which component to purchase, implement, and support requires individuals with a certain level of expertise.
The resources mentioned above along with budgetary limits as set forth by corporate leadership require careful planning and cost analysis to ensure a return on investment.
These factors must be considered as you plan to secure your network. But what is the actual starting point?
In the next section, we will provide the basic steps of how you can create an effective security plan for your organization.
Step 1: Understand Your Business Model
The first step in developing a network security plan is to know what it is you are planning to secure.
You must know what the crown jewels are of your organization, where it resides, and how the business produces revenue.
Your executive leadership will have this information and provide the goals for the business as set forth by the board of directors.
Step 2: Perform A Threat Assessment
Once you understand the business model of your organization, it is now time to understand the assets, systems, and resources that are on active on your network. This information will be used to conduct a threat assessment.
The threat assessment is usually performed by a third party. This assessment may take a few weeks or even longer depending on the breadth of your environment.
The objective of the goal regardless of the timeframe to complete is to provide you with a report of the following information:
- Identify and classify any security holes in the network
- Identify weaknesses and vulnerabilities that could be exploited, such as, weak passwords or default passwords used in critical systems.
- Identify network security vulnerabilities in application, file, and database servers to determine patch levels.
- Audit encryption settings on critical systems
- Test the viability of network defenders to detect and respond to attacks
- Provide evidence to support increased IT investments or network security
The teams involved usually in this stage of the plan will include members from the Network, InfoSec, Database, and Server teams. These teams may be called upon to provide access to systems to perform a comprehensive audit of the environment.
The cost associated with hiring a third-party threat assessor will vary, dependent upon size and scope of your organization.
In general terms, the cost for a threat assessment may start at 10,000 according to one vendor. This cost may cover the third party’s billable hours, number of engineers allotted to project, dedicated project manager, and reporting cost.
The internal infrastructure of the organization in most cases provides the access required for the assessor to logon to a resource, such as Active Directory. If the threat assessment involves a vulnerability or penetration test, the assessor will utilize their tool sets of choice.
Once the Threat Assessment is complete, the assessor will create a detailed report specifying vulnerabilities detected and remediation recommendations based on the severity of the findings.
The vulnerability remediation effort may require an update to an existing application or device or recommend the purchase of new equipment.
Whichever the case, the report should provide an overview of the organization’s infrastructure and how well they are protected from insider or external threats.
With this information in hand, the Security leader will undertake a review of the organization’s security policies to determine if they align with best practices and any compliance requirements for the business.
The next step will highlight the characteristics and what to include in a network security policy.
Step 3: Develop IT Security Policies & Procedures
The results of the threat assessment can be used to create or expand the current version of policies and procedures.
From my experience and perhaps at your company, you may have one general Information Security Policy, and other sub or specific policies which support the primary policy.
For example, your organization may have a separate policy for Passwords, Mobile Devices, VPN, Social Media, Internet Usage, or a Clean Desk Policy.
There is not a hard fast rule on the number of policies to create, however, they should be visible and written in terms that the average user in your environment can comprehend.
The link below provides a few samples of security related policies that you can reference for your organization.
The policy templates listed in the above article are short, concise, and easy to understand. The composition of the policy content is generally governed by the Security Leadership (CISO, Information Security Officer, Security Director) in partnership with Compliance and Legal Department approval.
Once the policy content has been thoroughly processed and reviewed, executive leadership will provide the final approval for distribution into the corporate infrastructure.
This high level or ‘top-down’ approach informs the employees that the policies and procedures have been approved at the highest level of the organization and must be adhered to by each employee.
For this reason, new employee orientation and onboarding consist of validating that they have acknowledged and agree to the policies of the organization.
This approach not only creates an atmosphere of accountability for the new employee from day one, but it also results in a ‘Security-First’ culture for the company. Let us expound on this in the next step.
Step 4: Create A “Security-First” Company Culture
To cultivate a strong security first culture at your organization, regular security awareness training is imperative.
The average employee may not recall the exact wording of the core security policy for their organization when they were initially onboarded as a new hire. They also may not recall the location of the security policies.
Security awareness training and periodic phishing campaigns are created with the purpose of reminding the employees of the security policy and how to respond to old and new security threats.
For the past 17 years, October has been Cyber Security Awareness month. This is an ideal time for organizations to send security policy reminders and tips to its employers via email, signs, or posters.
When your organization’s leadership is diligent in creating or improving its security culture, there is great benefit. This proactive approach to security increases security awareness.
It can also assist in identifying persons inside the organization who purposely ignore the policies and desire to damage (theft of sensitive data/intellectual property, disruption to productivity) to the business.
A corporate hotline to anonymously report compliance violations should be included in the organization’s security awareness program.
Despite the efforts in creating and improving the security culture of the organization, there will be events within the organization that challenge the confidentiality, integrity, and availability of the company resources.
Let us learn more about this in the next step.
Step 5: Define Incident Response
Incident Response is a critical component of the Network Security Plan.

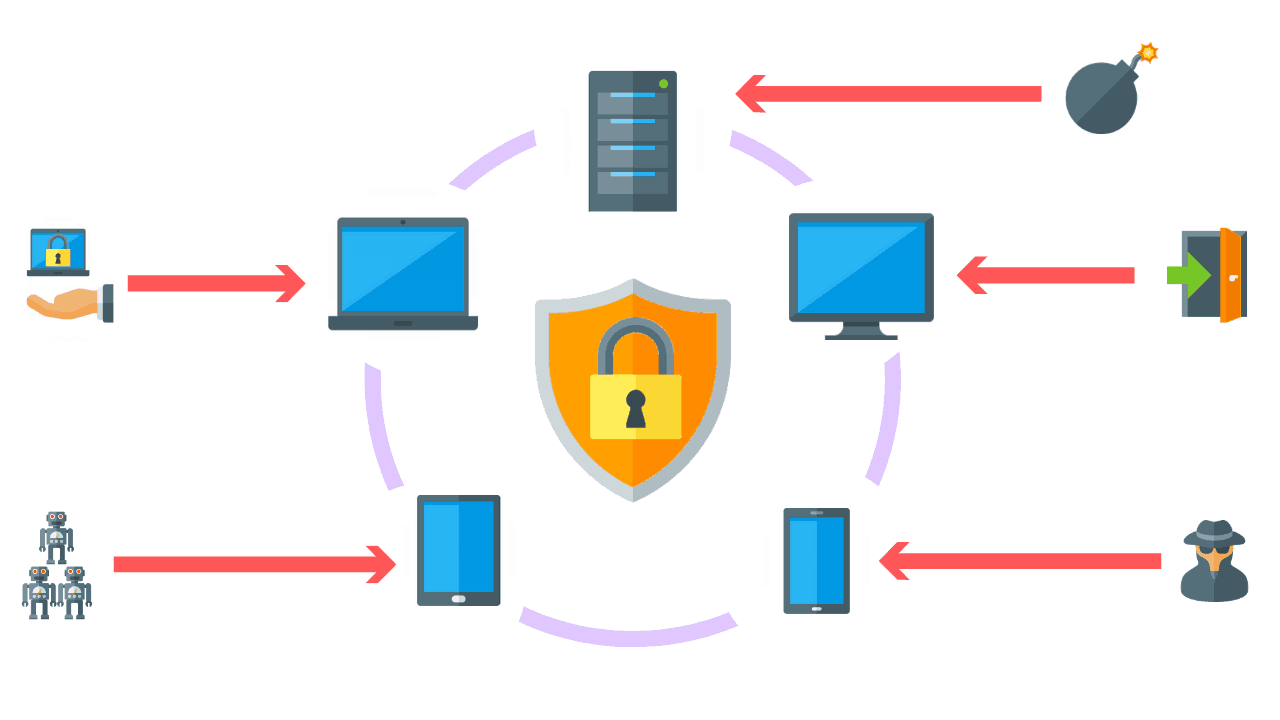
Threat actors have the goal of disrupting the operation of businesses around the world including your organization. Around the clock, these characters are searching for methods to infiltrate your network with the intent of installing ransomware, by way of phishing, and other social engineering techniques.
On top of the threats from unknown actors in the wild, there is the risk of insider threat. A disgruntled employee may have a grievance and may attempt to expose sensitive data, or an employee may perform an unintended action that results in data loss.
The good news is that there is technology available to thwart these attacks. There are firewalls, network segmentation, endpoint malware protection, and security awareness programs.
Regardless of how well a corporation has developed and matures its security strategy, this does not remove the probability of an incident from occurring.
A simple click on a link from an email can be disastrous – it only takes one bad decision to impact the network. Who should be contacted when an incident occurs?
What if the IT managers are on vacation? Our building was destroyed, where is the Incident response plan? A hacker gained access to our accounting database, what should we do?
Incident Response answers these questions. Incident response is an organized approach to addressing and managing the aftermath of a security breach or cyber attack. The goal of Incident Response is to handle the situation in a way that limits damage and reduces recovery time and costs.
To reduce the lifecycle of a discovered incident, the Incident Response plan facilitates rapid handling. The plan provides information of who the members of the Incident Response Team are and their assigned duties.
Within the plan, there is a call tree that helps the incident handler facilitate the process – document the incident timeline, assemble the relevant team members, and provide the proper notification of the event and status to senior leadership.
At the conclusion of the incident, the plan outlines lessons learned from the attack which helps the team understand how the incident occurred and methods to prevent repeating of the incident in the future.
If your organization is contemplating the creation of an Incident Response Plan, the link below provides templates for various types of incident plans.
Incident Response Plan 101: How to Build One, Templates and Examples
Step 6: Implement Security Controls
 It is great for your organization to have solid, professionally written policies describing what should be done.
It is great for your organization to have solid, professionally written policies describing what should be done.
This is a serious must have, however, there should be tools and controls implemented in the environment to support the policy statements, or else, the policies are just words.
There are several security control frameworks available that can be used as a reference to establish your security controls.
These frameworks provide direction on how to secure firewalls, implement secure Operating System best practices, Password best practices, and other security initiatives.
Common Frameworks available in the industry are:
- NIST National Institute of Standards and Technology
- ISO/IEC 27001 International Organization for Standardization/International Electrotechnical Commission
- CIS Center for Internet Security
- PCI DSS Payment Card Industry Data Security Standard
- CMCC Cybersecurity Maturity Model Certification
The common theme in the listed frameworks is to build secure networks. I highly encourage you to review each framework to determine if it aligns with your current business model.
If there is not a requirement to adopt the full set of controls in each framework, at a minimum utilize the framework control recommendations to meet best practices for specific areas that align with your network, such as the firewall requirements listed in the NIST framework as an example.
Achieving the requirements listed in any of the frameworks requires resources and expertise. If your organization is lacking in this area, help is available.
Step 7: Hire A Managed Security Company
Hiring an outsource company to augment your security staff is a great option. These outsourced companies are referred to as a Managed Security Service Provider (MSSP).
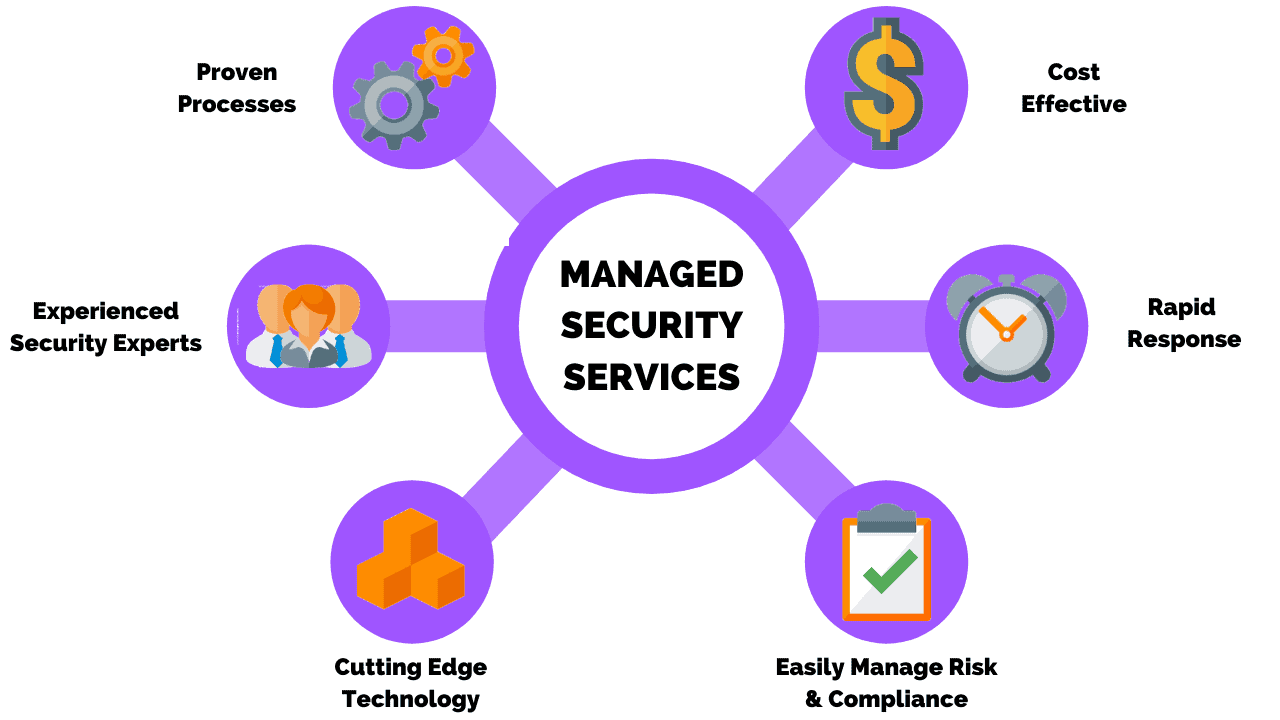
The advantages of hiring an MSSP are that they can be retained as needed or contracted for a set period. MSSP’s are staffed with SME (Subject Matter Experts) in various technologies.
The MSSP’s the organizations I have had the experience of working alongside are expert in the following technologies:
- Network Security (Firewalls, Routers, Switches, and WAN)
- Vulnerability Management
- Penetration Testing
- Forensics
- SIEM (Security Information Event Management)
- Endpoint Support (Endpoint Security Management – Malware/Antivirus Support)
- Data Loss Prevention
Partnering with a MSSP can help your organization implement your Network Security Plan.
They can also manage certain areas of your infrastructure where expertise is lacking. This partnership can help your team focus on operational tasks and other synergies with the relationship.
Partnering with a MSSP can be a cost-effective solution. The terms of the contract are set at the start of the engagement.
They usually provide a project manager who is the go-to person for issues and is available to ensure that the terms of the Service Level Agreement are satisfactory as agreed upon in the contract.
Selecting a Managed Service Provider is a critical decision for your organization. Partnering with the right provider can make a positive impact on your teams’ efficiency and bottom line.
Selecting the wrong partner can have the opposite effect and can quickly sour and be a burden to your budget and to your staff.
Therefore, it is imperative to carefully establish service level agreements upfront, letters of attestation, insurance, and other legalities within the contract.
If managed and supported properly, partnering with a MSSP can help you in meeting the goals of your Network Security plan.
Step 8: Maintain Security for The Future
Once the Network Security Plan has been documented, communicated to executive leadership, and security controls have been implemented to support the plan, your organization is heading in the right direction of laying the groundwork for an effective and sustainable security culture.
There may be pain points along the way, since adopting a change in corporate culture may not be well received by all members of the organization.
It is essential for executive leadership to support the culture, which in turn will set the tone for the rest of the organization.
To ensure the entire organization is in tune with the security culture, various roles and resources are required to orderly move the culture along.
Most medium to large organizations have various roles in place to oversee the Information Technology and cyber security program of the organization and help sustain the culture.
A sample list of roles is listed here:
- Chief Information Security Officer (CISO)
- Information Security Officer (ISO)
- Chief Information Officer (CIO)
- Director of Security
- Security Manager
- Compliance Risk Manager
The individuals assigned to these roles should make it a practice to engage with other non-technical business leaders representing Finance, Legal, Human Resources, and Marketing.
Regular communication with these teams will help the organization understand that security is an integral part of the business culture that all employees should support.
Security leaders should meet quarterly to review the state of the security program to assess gaps in processes, tools, or review security awareness training.
An overall review of the network security plan should also be conducted on an annual basis as well.
Conclusion
A Network Security Plan provides the roadmap for your organization to operate safely and securely.
Development of the plan requires a thorough understanding of the business and support from executive leadership.
The plan should be deliberate, enforceable, understandable, educating all employers to want to do the right thing for security.
By following the suggestions provided in this article, you can create a successful network security plan and develop a sustainable security culture that will provide lasting benefits for your organization.
Related Articles
- Network Security Types: Expert Explains The Basics Of Cyber Security
- 9 Common Types Of Malware (And How To Prevent Them)
- Vulnerability Scanning VS Penetration Testing: What’s The Difference?
- How Often Should You Perform A Network Vulnerability Scan?
- Internal VS External Vulnerability Scans: What’s The Main Difference?


